Today, we are excited to announce the launch of
Sysdig Secure 2.4! With this release, Sysdig adds runtime profiling to enhance anomaly detection and introduces brand new interfaces that improve
runtime security policy creation and vulnerability reporting.
These features are focused on upgrading the experience of creating your security policy to detect security threats and attacks to your infrastructure and apps.
Back in April, we
announced the industry’s first unified
Cloud-Native Visibility and Security Platform, which provides both monitoring (via
Sysdig Monitor) and security (via
Sysdig Secure) at massive enterprise scale, across both multi and hybrid cloud environments.
Alright, let’s dig deeper into Sysdig Secure 2.4, which focuses on runtime detection and vulnerability management!
I. Runtime profiling
Sysdig’s approach to runtime defense in large-scale environments is to automatically model runtime behavior by analyzing the activity inside the containers. Analyzing syscalls, traversing the kernel leveraging
eBPF technology and enriching them with various metadata including Kubernetes and Cloud provider labels, allows Sysdig to create a truly comprehensive container runtime profile. This
reduces the effort required to manually create and update profiles.
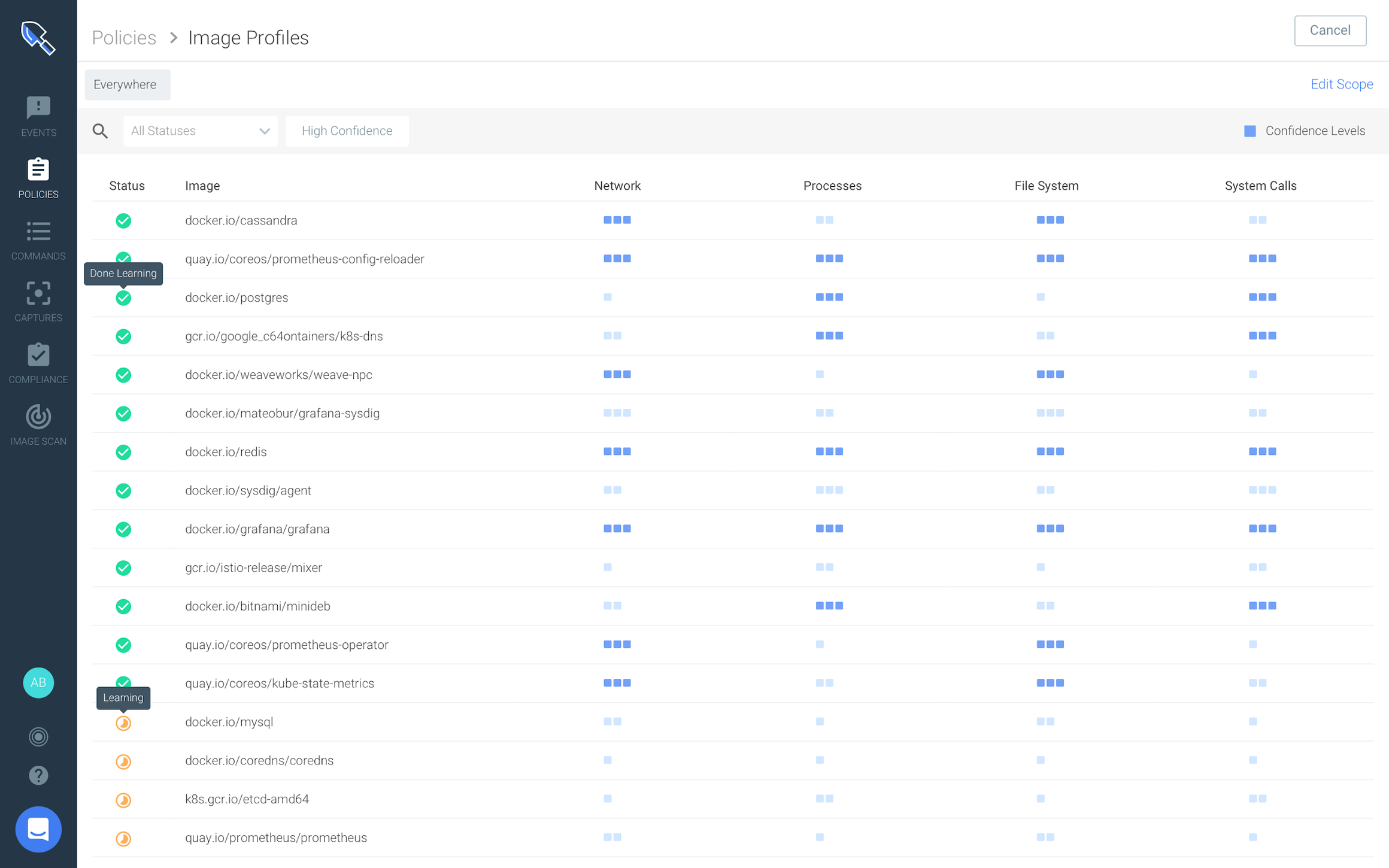
Sysdig uses its syscall-level understanding to gain deep insights into container runtime behavior such as:
- Spawned process – which process and binaries are running?
- Network traffic – what TCP/UDP ports does this application communicate on?
- File system activity – what files are being read? And written?
- System calls – what system calls are executed?
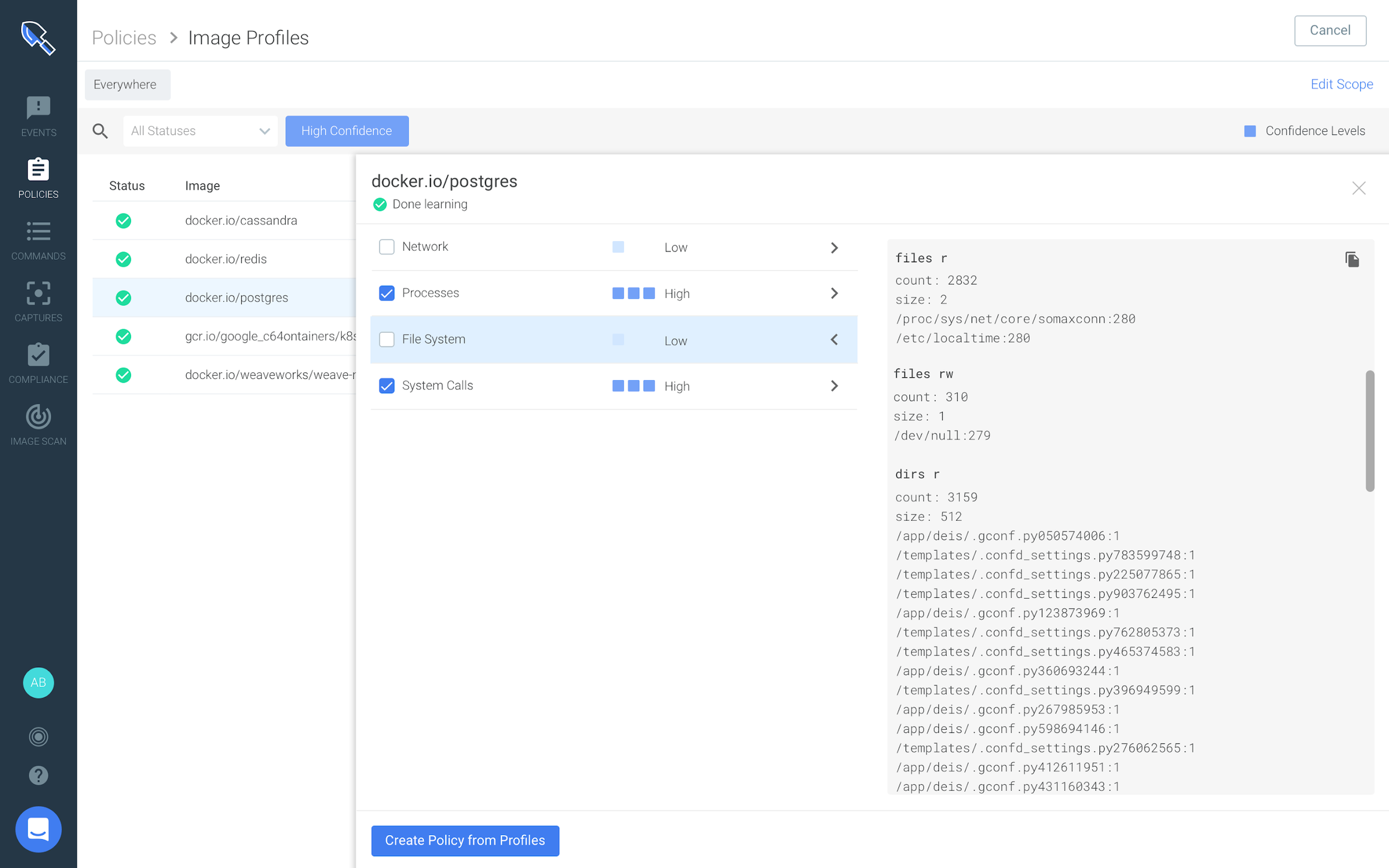
After the learning is complete, Sysdig Secure provides visibility into auto generated runtime profiles through confidence levels. These three confidence levels (low, medium, high) reflect how much we know about the specific container runtime behavior. Security teams gain more transparency and assurance into their policy when they have full control of what’s inside a runtime profile rather than applying black box auto generated profiles.
After the profile is built, a user can simply snapshot it into a runtime policy that can be directly applied to different scopes using metadata: containers, hosts or Kubernetes resources.
II. Falco Rule Builder
Our goal with this release is to** ease the burden on security teams to create their container security policy**. In addition to auto generating runtime profiles, creating, editing and managing your
Kubernetes security policy is now much easier.
Create and customize advanced security policies
Sysdig Secure also provides the simplicity and flexibility to create custom runtime rules based on
open-source Falco. The new security policies contain a mix and match of runtime profiles, UI built rules and advanced Falco rules.
Sysdig Secure has developed a new interface called *Falco Rule Builder *that lets you visually interact with the Falco engine under the hood and create powerful rules via a flexible UI. Runtime rules can be scoped and filtered to any aspect of your environment (such as a particular Kubernetes namespace, deployment, pod, etc.) and managed at scale across multiple clusters, cloud providers and data centers.
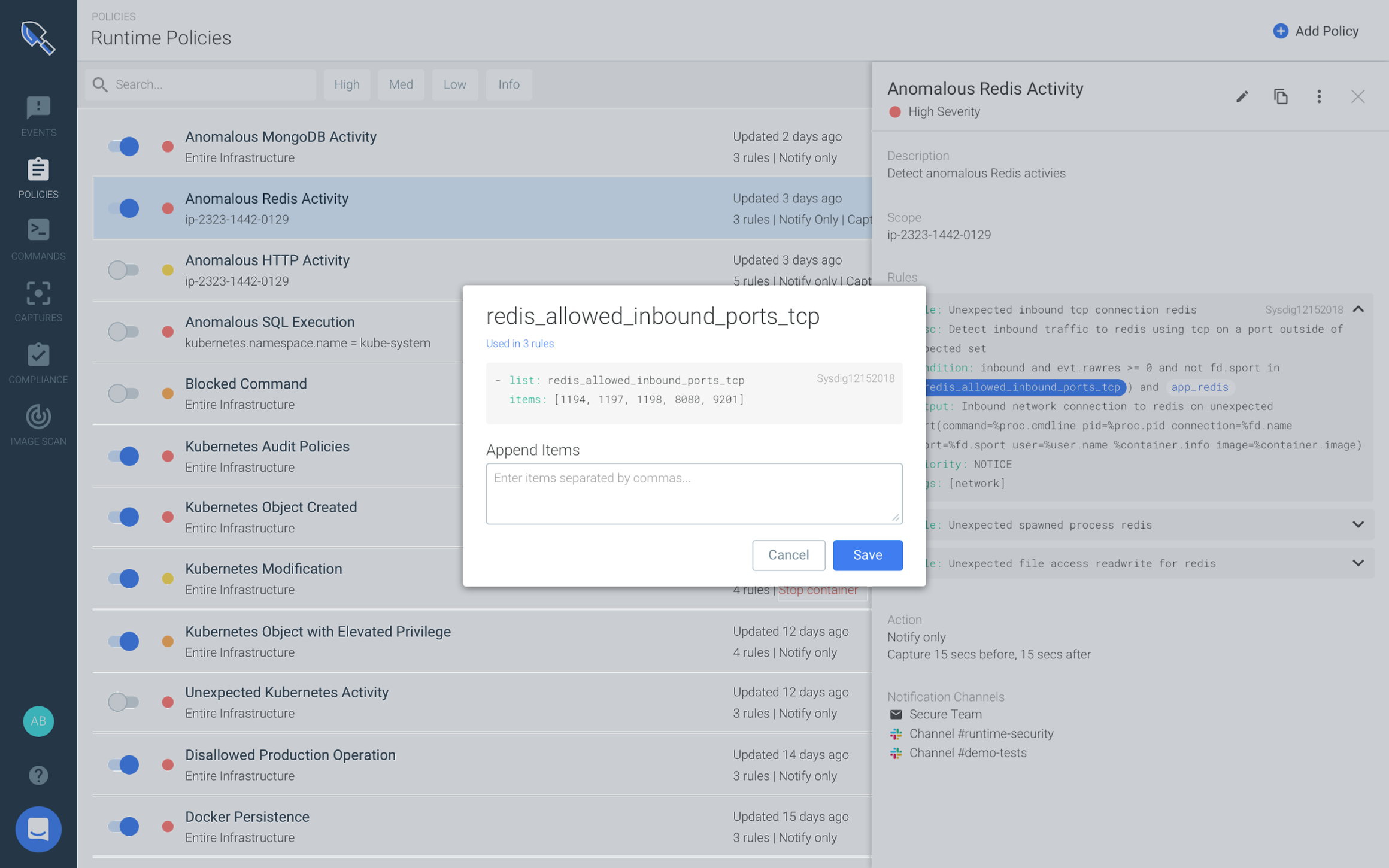
Users can also create new policies without needing to know in-depth Falco expressions and filtering commands.
Although Sysdig Secure focuses on containers, these custom rules can be applied to bare metal and virtual instance hosts as well.
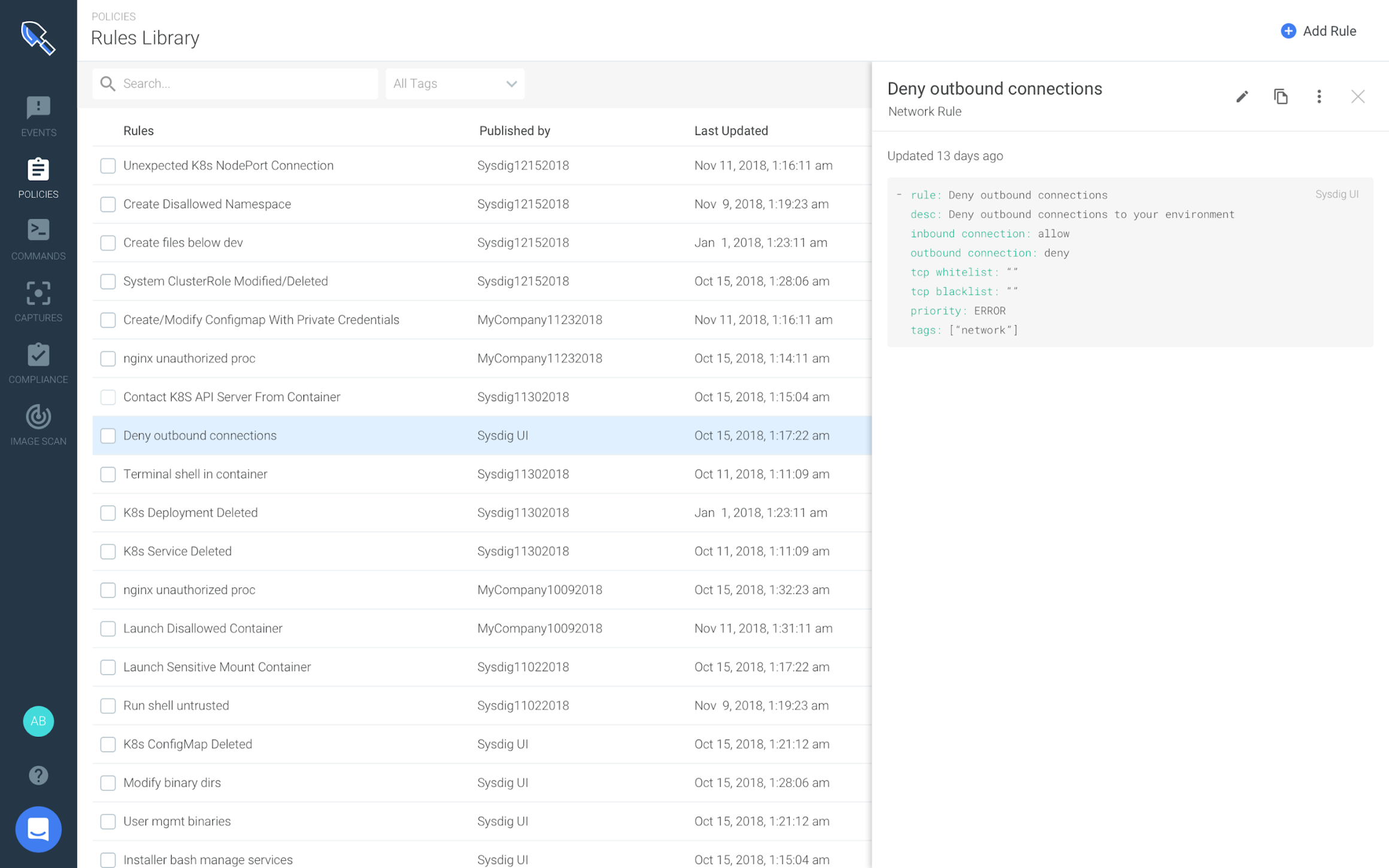
Leveraging community and framework-driven policies via Rules Library
Taking it a step further, users can easily leverage existing
security compliance frameworks such as
MITRE ATT&CK, and utilize container runtime security rules that adhere to eight key MITRE categories. Now, they can be easily implemented via the
Rules Library to be part of the container security profile.
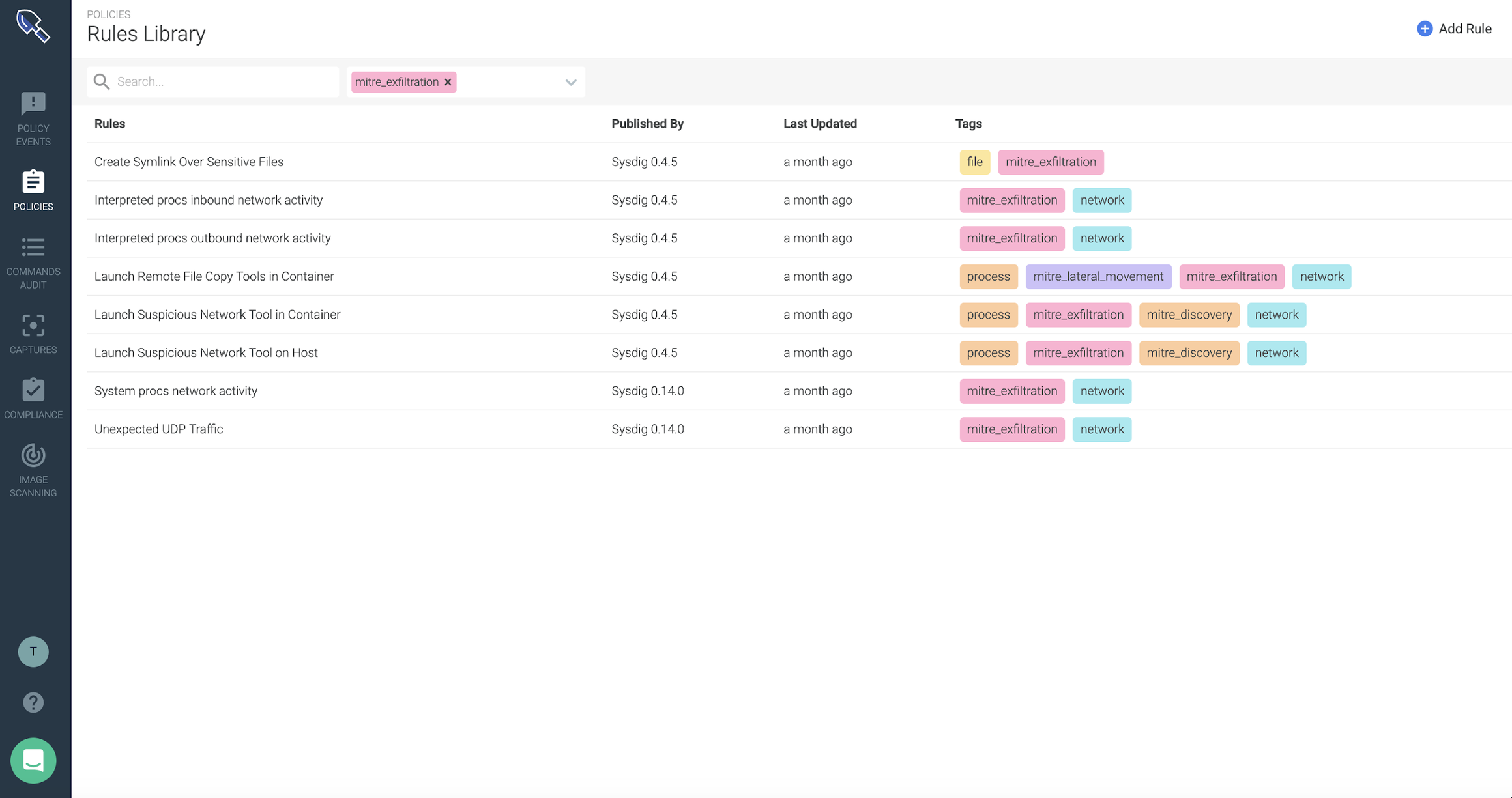
Because of the open source contribution, a wide variety of community sourced rules are available to enhance the rules repository and allow other users to benefit from a community-driven security approach. For example, FIM rules can be easily leveraged via the
Rules Library in the Sysdig Secure platform.
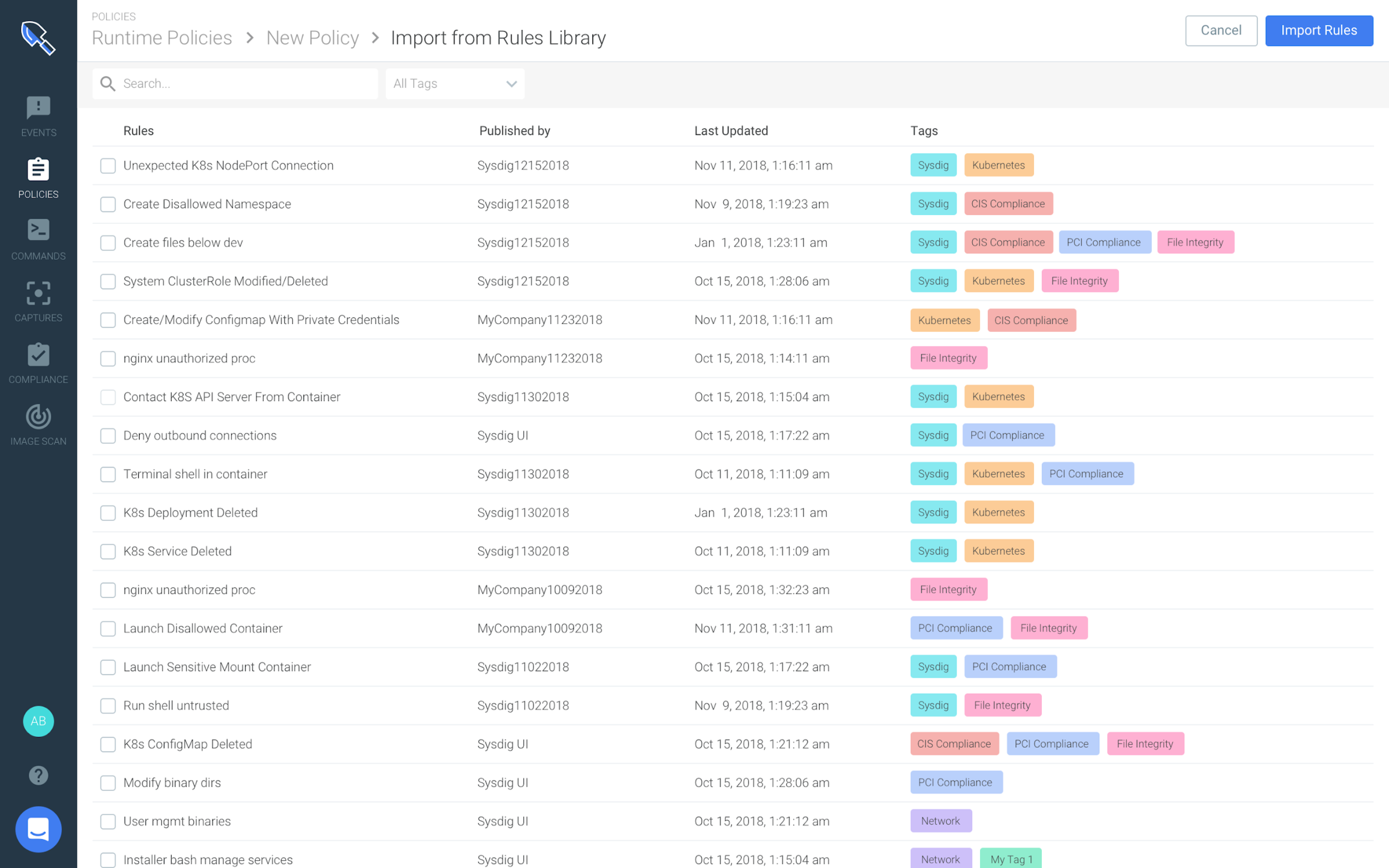
Security ops teams can apply these community or framework driven policies from the Rules Library and have more assurance in their container runtime security posture.
Read more about the new
Sysdig Secure policy editor.
III. Sysdig Secure vulnerability reporting
Sysdig Secure now provides a unified console for easy
vulnerability management including reporting and advanced querying.
Sysdig connects the dots between your image scanning vulnerabilities database and what’s currently running on your platform so each person can focus on the relevant information for them and build complex queries to understand what was the status at any point in time.
Let’s illustrate this with an example, imagine a query like:
Show me all the vulnerabilities in prod namespace where the severity is greater than high, the CVE > 30 days old, and a fix is available. This question is now easily answered with Sysdig.
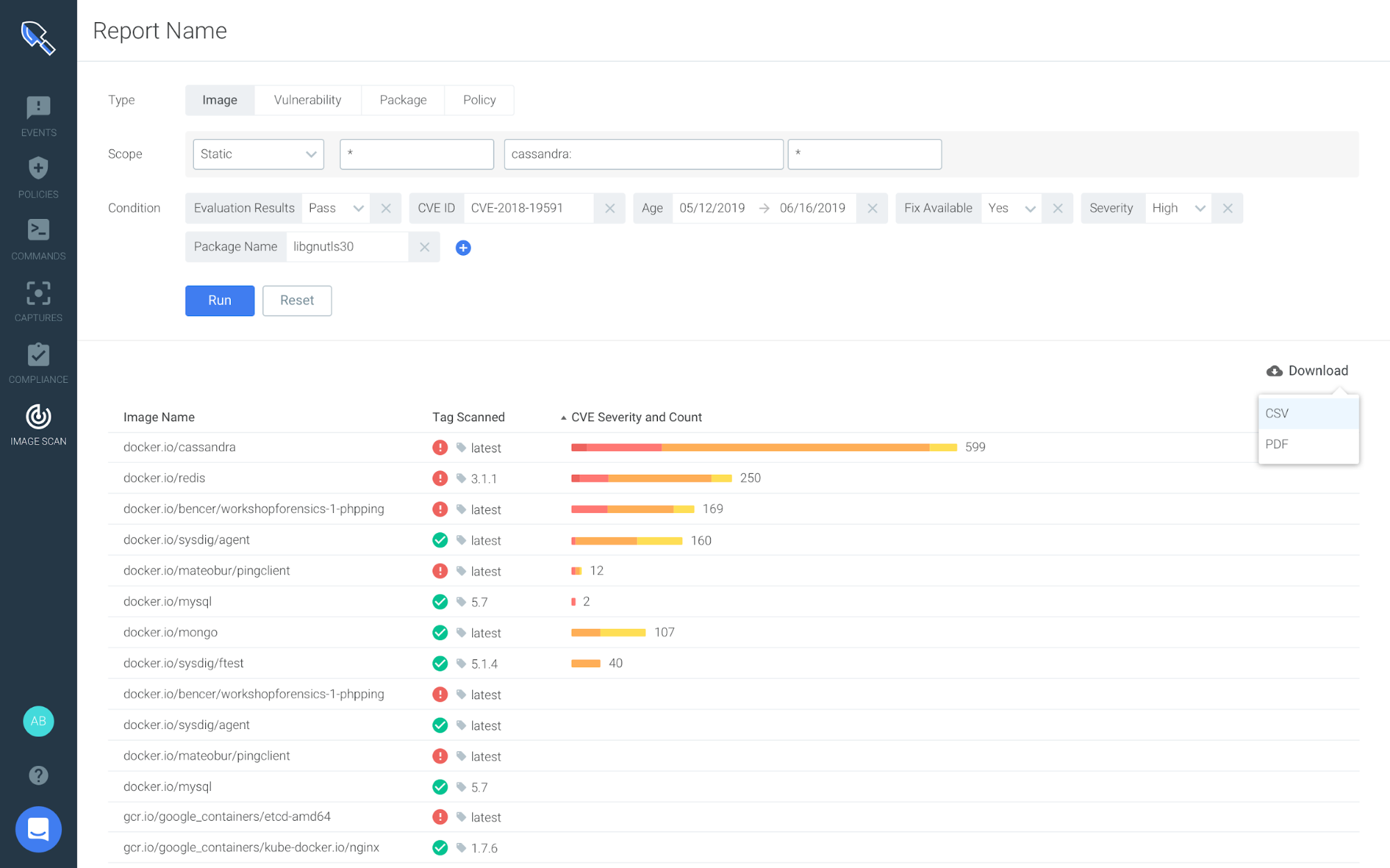
With the new vulnerability reporting capabilities, DevOps and security teams can easily query across a catalog of images, packages, CVEs, as well as check for advanced conditions like CVE age, fix available, software version etc. Finally, these reports can be downloaded and shared (PDF/CSV) with vulnerability management teams, CISO’s, etc.
New advanced alert configuration
We also added a new advanced alert configuration to notify changes in images, policies or CVE exposures via Slack, PagerDuty, email, etc. This is important because your vulnerability management teams can be alerted if:
- A new image tag is pushed to a registry
- A specific policy change was triggered (pass or fail)
- A change in CVE information for a specific image (example nginx:latest)
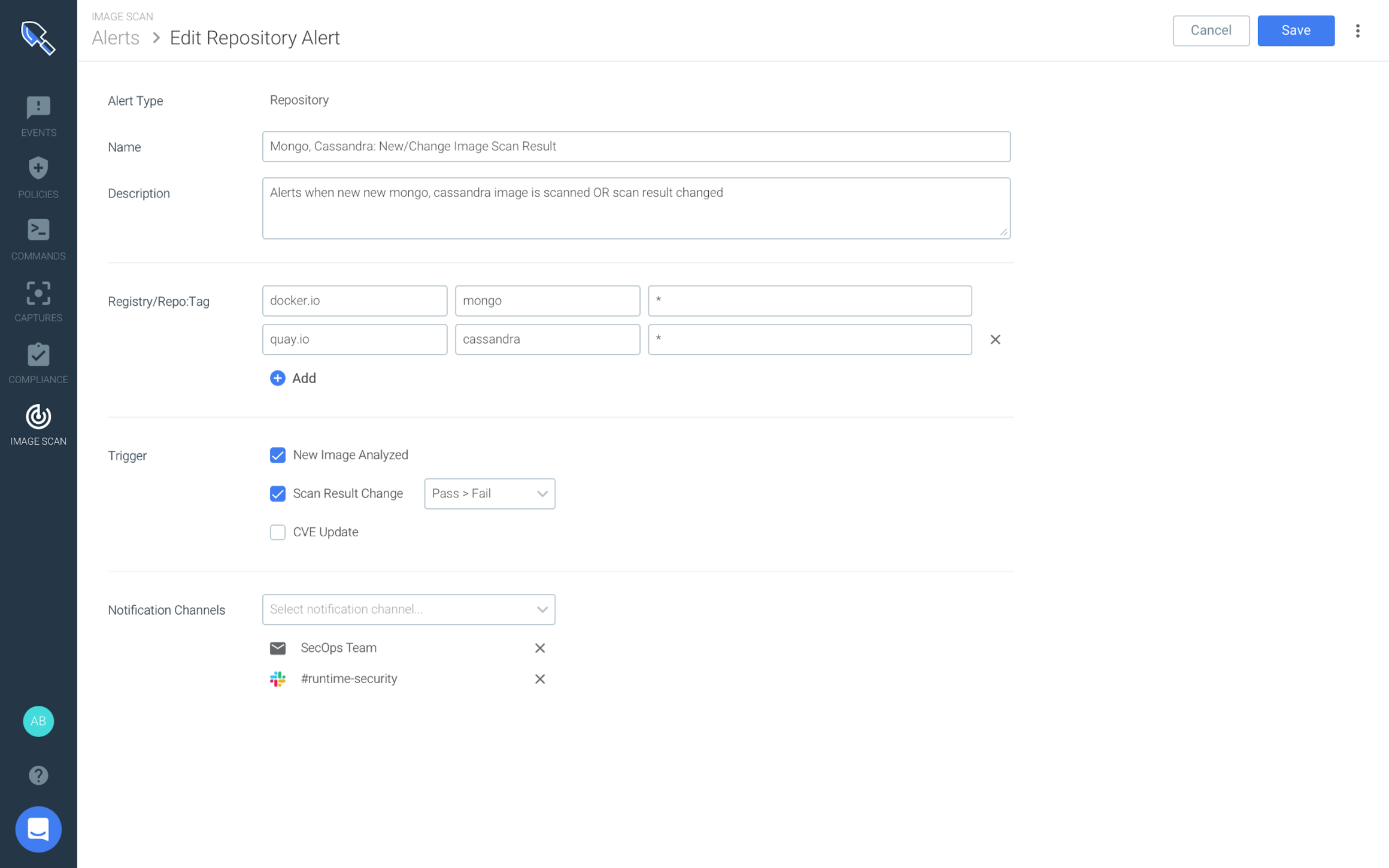
This limits security alerts to only people that information is relevant to based on the applications they are responsible for, while it enables security teams to fix issues faster, while also reducing the impact of alert fatigue.
Improved scan results UI
This feature** **provides the ability to view a summary of all policies an image was evaluated against, understand what exactly failed (and passed), any vulnerabilities including specific OS and non-OS package checks, and image contents.
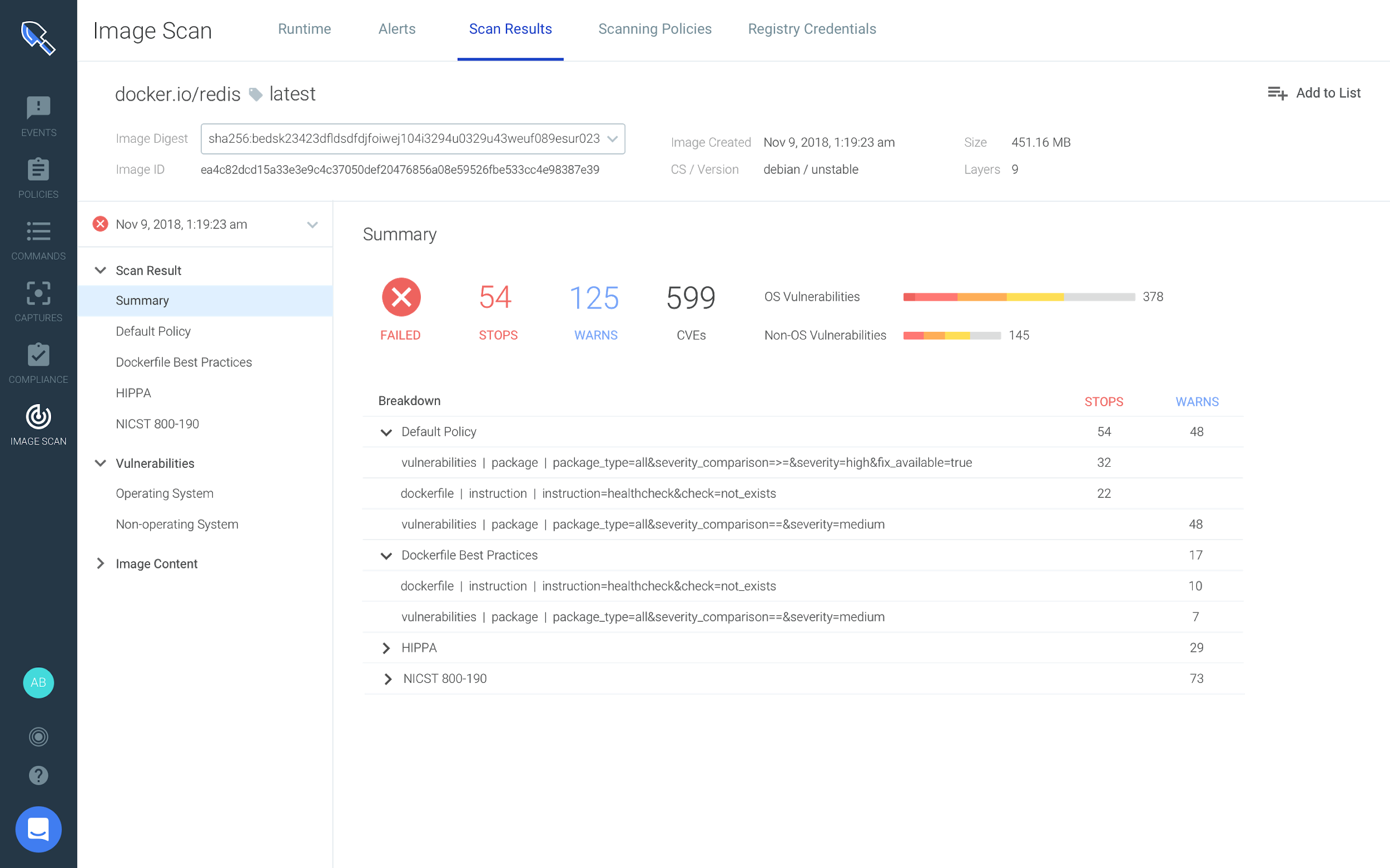
With the new scan results UI teams have:
- Interactive and sortable scan results, including filtering by CVE’s (critical, high, medium, etc).
- An understanding of how an image has performed against the different audit policies that have been put in place.
Sysdig Secure 2.4 expands on its previous runtime security and vulnerability management capabilities with the addition of runtime profiling and the new policy editor. Now it is easier than ever for security teams to ease the burden of creating their container security policy and they now have the ability to better understand at any point in time if a vulnerability exists within their containers.
Sysdig is the only platform that addresses key security challenges across the entire container lifecycle, including image scanning and vulnerability management, compliance, runtime security and incident response and forensics. With deeper insights and better understanding all of the container and environment activity.
 Sysdig uses its syscall-level understanding to gain deep insights into container runtime behavior such as:
Sysdig uses its syscall-level understanding to gain deep insights into container runtime behavior such as:
 After the learning is complete, Sysdig Secure provides visibility into auto generated runtime profiles through confidence levels. These three confidence levels (low, medium, high) reflect how much we know about the specific container runtime behavior. Security teams gain more transparency and assurance into their policy when they have full control of what’s inside a runtime profile rather than applying black box auto generated profiles.
After the profile is built, a user can simply snapshot it into a runtime policy that can be directly applied to different scopes using metadata: containers, hosts or Kubernetes resources.
After the learning is complete, Sysdig Secure provides visibility into auto generated runtime profiles through confidence levels. These three confidence levels (low, medium, high) reflect how much we know about the specific container runtime behavior. Security teams gain more transparency and assurance into their policy when they have full control of what’s inside a runtime profile rather than applying black box auto generated profiles.
After the profile is built, a user can simply snapshot it into a runtime policy that can be directly applied to different scopes using metadata: containers, hosts or Kubernetes resources.
 Users can also create new policies without needing to know in-depth Falco expressions and filtering commands.
Although Sysdig Secure focuses on containers, these custom rules can be applied to bare metal and virtual instance hosts as well.
Users can also create new policies without needing to know in-depth Falco expressions and filtering commands.
Although Sysdig Secure focuses on containers, these custom rules can be applied to bare metal and virtual instance hosts as well.

 Because of the open source contribution, a wide variety of community sourced rules are available to enhance the rules repository and allow other users to benefit from a community-driven security approach. For example, FIM rules can be easily leveraged via the Rules Library in the Sysdig Secure platform.
Because of the open source contribution, a wide variety of community sourced rules are available to enhance the rules repository and allow other users to benefit from a community-driven security approach. For example, FIM rules can be easily leveraged via the Rules Library in the Sysdig Secure platform.
 Security ops teams can apply these community or framework driven policies from the Rules Library and have more assurance in their container runtime security posture.
Read more about the new Sysdig Secure policy editor.
Security ops teams can apply these community or framework driven policies from the Rules Library and have more assurance in their container runtime security posture.
Read more about the new Sysdig Secure policy editor.
 With the new vulnerability reporting capabilities, DevOps and security teams can easily query across a catalog of images, packages, CVEs, as well as check for advanced conditions like CVE age, fix available, software version etc. Finally, these reports can be downloaded and shared (PDF/CSV) with vulnerability management teams, CISO’s, etc.
With the new vulnerability reporting capabilities, DevOps and security teams can easily query across a catalog of images, packages, CVEs, as well as check for advanced conditions like CVE age, fix available, software version etc. Finally, these reports can be downloaded and shared (PDF/CSV) with vulnerability management teams, CISO’s, etc.
 This limits security alerts to only people that information is relevant to based on the applications they are responsible for, while it enables security teams to fix issues faster, while also reducing the impact of alert fatigue.
This limits security alerts to only people that information is relevant to based on the applications they are responsible for, while it enables security teams to fix issues faster, while also reducing the impact of alert fatigue.
 With the new scan results UI teams have:
With the new scan results UI teams have:

