
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

"What's New in Sysdig" is back with the October 2023 edition! My name is Zain Ghani, based in Austin, Texas, joined by my colleague, Matt Baran, based in Los Angeles, California, to share our latest updates with you.
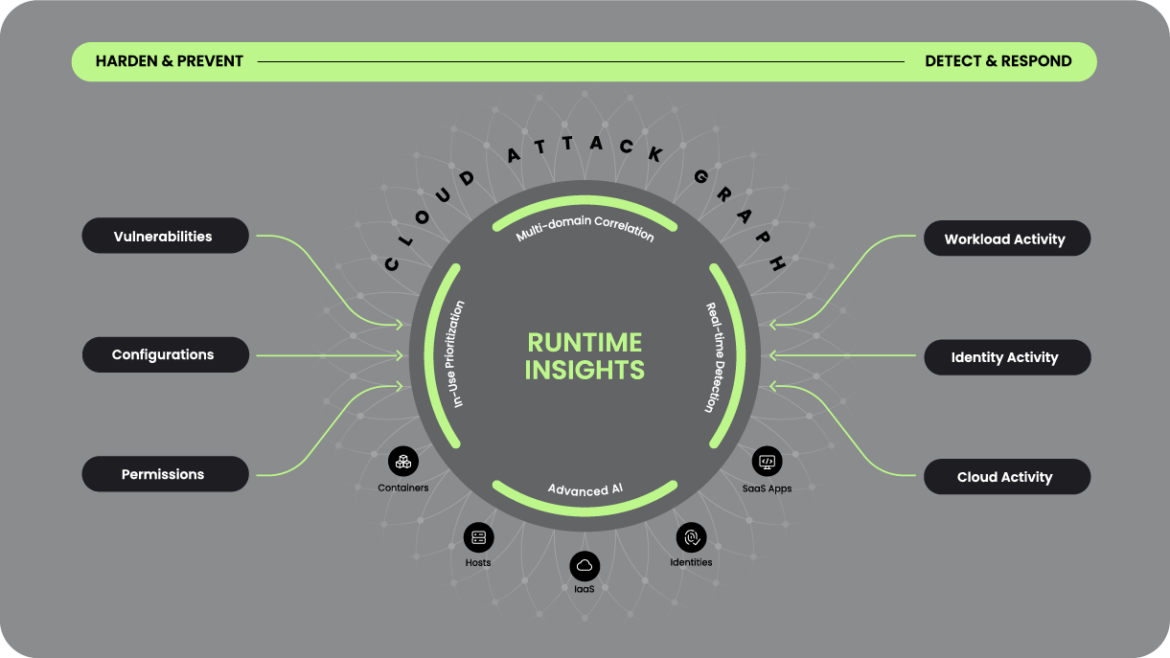
The last few weeks have been really exciting at Sysdig. We unveiled Sysdig's Industry-Leading Cloud-Native Application Protection Platform (CNAPP), leveraging the Cloud Attack Graph, powered by Runtime Insights to correlate assets, detect risks, and provide real-time insights. You can read more about it in this article or watch this informational video.
Sysdig and Docker also announced a partnership to accelerate and secure Cloud-Native Application Delivery at the 2023 DockerCon. Sysdig's runtime insights will be integrated into Docker Scout to help developers prioritize risk and move faster. This integration will help customers reduce software supply chain noise, prioritize the insights that matter, and build leaner container images. Sysdig is the first runtime security integration in Docker Scout. You can read more about it in our press release.
Stay tuned for more updates from Sysdig, and let's get started!
Sysdig Secure
Custom Posture Controls
You can now tune your compliance results by customizing your posture controls. This includes the ability to customize the evaluation parameters and severity.
This feature requires new Posture Control edit permissions, which are automatically granted to the Team Manager and Advanced User roles. Administrators can manage these privileges for all roles under Settings as follows:
[Select role] → Policies → Posture Controls
Reporting for Image Pipeline Vulnerability Scanning
The Vulnerability Management team is pleased to announce the release of Reporting for Image Pipeline scanning. The Vulnerability Management engine now has reporting for all scanning functionality (Runtime, Registry, Host, and Pipeline). Pipeline reporting mirrors the Runtime and Registry reports, with just a change in the scoping context.
Admission Controller v0.14.9 Released
Kubernetes audit events are now enriched with container metadata to give additional insight into your infrastructure. With this enhancement, all the pod events now display container.name, pod.name, and pod.namespace labels. You can view these labels on the Secure Event detail panel for events such as Create HostNetwork Pod and Attach/Exec Pod.
Exception UI Improvements for Threat Detection Rules
Sysdig is introducing a new user-friendly exception builder. The new exception UI, built into the Rules Editor, helps users create, update, modify, and delete exceptions for threat detection rules. For more information, see Manage Threat Detection Rules.
Cloud Logs
Sysdig introduces a new product bundle intended for users who are interested in Cloud Detection and Response (CDR) for Cloud Logs but do not want to use Cloud Security Posture Management (CSPM). For more information, see Cloud Logs.
Agent Tags Support through Zone Scopes in Posture
Do you need to scope your Zones using the Agent Tags applied to your hosts and clusters?
You can now add Zone scopes: Kubernetes and Host with Agent Tags attributes. Add Agent Tags Key:Value pairs just as you add Labels. See the Posture Host Analyzer installation for details.
Advanced Users Can Apply Tuning Suggestions (Preview)
To simplify identifying and applying exceptions, we are enabling the ability for Advanced Users and Team Managers to see and apply Tuning suggestions from Insights and Event detail pages.
To enable:
- Log into Sysdig Secure as Admin and go to Settings
- Toggle Advanced User Tuner Enablement on
This will become the default behavior starting Oct. 15th.
Support for Rancher Kubernetes Engine (RKE2)
We are happy to announce the support for Rancher Kubernetes Engine (RKE2) which, lacking an official CIS benchmark, is supported by the addition of a new in-house policy.
Sysdig Secure Coverage Improvement for AWS
Sysdig Secure posture control library has been expanded to improve its AWS resources coverage. The control library now includes 26 new controls providing support for 17 new resource types (both deployed and from Terraform code) across the following AWS services:
- Amazon DynamoDB
- Amazon EC2
- Amazon Elastic File System (EFS)
- Amazon Kinesis
- Amazon RDS
- Amazon SageMaker
- Amazon Simple Queue Service (SQS)
- AWS Elastic Beanstalk
- AWS Network Firewall
- AWS Systems Manager (SSM)
OOTB Policy Content Updates
The following policies have gone through updates:
- Sysdig Mirantis Kubernetes Engine (MKE) Benchmark v1.1.0
In collaboration with Mirantis, we have updated some of the audits in order to provide more accurate results. - AWS Well Architected Framework
The Well Architected Framework has been augmented with 26 new controls, providing support for the recently added resource types, as well as for some of the already existing.
As a fundamental part of the support for Rancher Kubernetes Engine, Sysdig now provides the following new policy:
- Sysdig Rancher Kubernetes Engine (RKE2) Benchmark v1.6.0
The hardening guide provides prescriptive guidance for hardening a production installation of RKE2, and this benchmark guide is meant to help you evaluate the level of security of the hardened cluster against each control in the CIS Kubernetes benchmark. It is to be used by RKE2 operators, security teams, auditors, and decision makers.
Sysdig Monitor
Metrics Usage Enhanced with Dashboards and Alerts Usage Metadata
Metrics Usage now displays which Dashboards and Alerts are using a given metric, enabling you to better understand the value a given metric provides to teams.
Notification Snapshot for Metric Alert Notifications (CA)
Metric Alert notifications forwarded to Slack or Email include a snapshot of the triggering time series data. For the Slack notification channels, you can toggle the snapshot within the notification channel settings. When the channel is configured to Notify when Resolved, a snapshot of the time series data that resolves the alert is also provided in the notification.
This feature is released as controlled availability.
Sysdig Agents
12.17.0 Oct. 24, 2023
This hotfix is applicable only to Sysdig on-prem deployments. It fixes an issue where the agent generates events in large numbers when Legacy Compliance is enabled due to incorrect throttling.
12.17.0 Oct. 17, 2023
Feature Enhancements
Capability for Malware Detection
Sysdig Agent provides the ability to detect malware and suspicious binary execution by using known bad hashes on hosts and containers.
When a malware control policy is enabled, the agent computes the hash for every binary execution and checks if the hash matches any of the known malicious ones. On match, the agent will prevent the execution and generate an event.
Your environment requires Linux kernel v5.0 or beyond for malware detection to work.
This feature is enabled by default. To disable globally on the agent, add the following to the dragent.yaml file:
malware_control:
enabled: falseTo enable the feature for the underlying host node, add the following to the dragent.yaml file:
protections:
malware_control:
enable_for_host: trueUse Protocol Buffer to communicate to Kubernetes API Server
Cointerface uses Google Protocol Buffers as a wire format for communicating with the Kubernetes API server.
Update OpenSSL Library to OpenSSL v3.1 and include a FIPS-Validated Crypto Module
In light of OpenSSL v1.1.1 reaching end-of-life, this release updates its bundled OpenSSL libraries to v3.1.3.
Additionally, this release bundles a FIPS-validated OpenSSL crypto module with the agent. Adding the crypto module removes the requirement for user-provided, FIPS-validated OpenSSL shared libraries when the fips_mode configuration parameter is set to true.
This update breaks the agent's backward compatibility with OpenSSL v1.1.1. If you have configured the openssl_lib parameter, do one of the following:
- Provide OpenSSL v3.1 shared libraries
- Remove the parameter and rely on the bundled OpenSSL shared libraries
End of Support for OpenShift v3
Sysdig Agent versions beyond 12.17.0 will no longer be supported on OpenShift 3. v12.17.0 will be the last version supporting OpenShift 3.
Defect Fixes
Prevent transition during restarts
The agent will no longer release the Kubernetes delegation lease during teardown to avoid unwanted transitions during restarts.
Policy scoping in Fargate now respects agent labels
Fargate agents will no longer skip agent labels when performing policy scoping.
Display resolved IPs in the Network Security Policy egress
The agent uses improved logic to resolve services and endpoints, and therefore, the network communications in some namespaces will not be dropped as unresolved.
Use get_mm_exe_file()
A safer version of the Linux kernel API call is used where get_mm_exe_file() is available.
Show correct Kubernetes status
Fixed defects in the Kubernetes status reporting. The kube_workload_status_available and kube_workload_status_unavailable metrics should report correct values even when the cluster node count changes, and the Kubernetes status should reflect the state correctly after the cointerface switches run modes.
Prevent unintended agent restart
A defect was fixed where an invalid message from the backend caused an unintended agent restart.
Store device metrics as expected
A defect was fixed where I/O metrics for devices were not stored.
Display Kubernetes cluster association correctly
A defect was fixed which caused incorrect agent association with Kubernetes clusters on the Agents page in the Data Sources UI.
Display correct time series count in Prometheus logs
Filtered timeseries counts in Prometheus statistics logs are now reported correctly.
SDK, CLI, and Tools
Sysdig CLI
v0.8.2 is still the current release. The instructions on how to use the tool and the release notes from previous versions are available at the following link:
https://sysdiglabs.github.io/sysdig-platform-cli/
Python SDK
Python SDK updated to v0.17.1.
Terraform Provider
We have just released the 1.15.0 version of Terraform provider. This release includes:
- Feature: Adding api only secure onboarding support
https://docs.sysdig.com/en/docs/developer-tools/terraform-provider
Terraform Modules
- AWS Sysdig Secure for Cloud remains unchanged at v10.0.9
- GCP Sysdig Secure for Cloud remains unchanged at v0.9.10
- Azure Sysdig Secure for Cloud remains unchanged at v0.9.7
Falco VSCode Extension
v0.1.0 is still the latest release.
https://github.com/sysdiglabs/vscode-falco/releases/tag/v0.1.0
Sysdig Cloud Connector
New Cloud Connector changes to (v0.16.54) under helm chart 0.8.6.
Admission Controller
New Admission Controller release (3.9.34) under helm chart 0.14.12.
Sysdig CLI Scanner
Sysdig CLI Scanner latest version is v1.6.0.
https://docs.sysdig.com/en/docs/sysdig-secure/vulnerabilities/pipeline/
Sysdig Secure Inline Scan Action
The latest release remains unchanged at v3.5.0.
https://github.com/marketplace/actions/sysdig-secure-inline-scan
Sysdig Secure Jenkins Plugin
The Sysdig Secure Jenkins Plugin remains at version v2.3.0.
https://plugins.jenkins.io/sysdig-secure/
Prometheus Integrations
Prometheus Integrations has been updated to v1.23.0:
- Fix legacy Pod Overview Dashboard
- Update OOTB Openshift/Rancher dashboards required metric
Sysdig On-Premises
Sysdig On-Premises has been updated to 6.5.0 with the following changes.
Upgrade process
Supported upgrades from: 5.0.x, 5.1.x, 6.x
For the full supportability matrix, see the Release Notes. This repository also includes the on-prem installation instructions.
Use of MinIO
Starting from release v6.5.0, MinIO has been added to the on-prem stack, specifically importing the MinIO binary from the upstream, for use in conjunction with Sysdig services.
You can download the MinIO source code in this repository. It is licensed under the AGPL 3.0.
This product includes software developed at MinIO, Inc. Copyright: MinIO Project, (C) 2015-2023 MinIO, Inc.
Sysdig Secure
Vulnerability Management landing page
Sysdig Secure offers a landing page to identify, track, and initiate Vulnerability Management workflows. This is designed to support users looking to see trends, priorities, and top action items on the vulnerability risks in their environment. The landing page covers all the scanning capabilities for images, workloads, and hosts, as collected by the installed scanners: vulnerability CLI, registry, host, and runtime. All widgets on the page enable a workflow to take action or export data to your native information security tool ecosystem.
What?
- Enable Vulnerability Managers to easily identify changes in vulnerability Risk Posture (trends), most pervasive vulnerabilities, newest released vulnerabilities, and infrastructure segments with the most vulnerabilities.
- Enable Program Managers to get easy insight into Policy posture on findings.
- Enable Architects to easily access the data regarding scan counts and adoption rates.
Why?
- Give a Vulnerability Management team an easy place to prioritize and manage vulnerabilities at a program level.
Container Registry Scanning
Image Registry Scanning functionality is available as part of the Sysdig Vulnerability Management suite in on-prem deployments.
This feature provides an added layer of security between the pipeline and runtime stages, allowing you to gain complete visibility into potential vulnerabilities before deploying to production.
The supported vendors are:
- AWS Elastic Container Registry (ECR) – Single Registry and Organizational
- JFrog Artifactory – SaaS and On-Premises
- Azure Container Registry (ACR) – Single Registry
- IBM Container Registry (ICR)
- Quay.io – SaaS
- Harbor
Once the container registry is instrumented and analyzed, you can generate registry reports to extract, forward, and post-process the vulnerability information.
Added Vulnerability Management APIs
The following new API endpoints have been released in Technical Preview to list and filter vulnerability scan results for Pipeline, Registry, and Runtime, as well as to fetch detailed scan results in JSON format:
- Get a list of pipeline scan results: GET /secure/vulnerability/v1beta1/pipeline-results
- Get a list of registry scan results: GET /secure/vulnerability/v1beta1/registry-results
- Get a list of runtime scan results: GET /secure/vulnerability/v1beta1/runtime-results
- Get full scan results: GET /secure/vulnerability/v1beta1/results
These API endpoints are applicable only to the current Vulnerability scanning engine.
New Vulnerability Management engine for airgap environments
The new Vulnerability Management engine, a major upgrade to the vulnerability and image scanning functionality for the Sysdig Secure product, is available in airgapped on-prem deployments. Contact your Sysdig representative for technical support.
Major highlights
- Scanning time has been drastically reduced: 8x faster on average!
- Additional data for vulnerabilities and remediation
- CVSS scores and metrics: Network Attack Vector, Privileges Required, etc.
- Flagging of publicly available code exploits
- Suggested package fix version
- Risk spotlight: Focus on the vulnerabilities that Sysdig detects in active packages at runtime. This is a new filter that only shows CVEs with active packages, to save time browsing infrastructure and to help focus on high-impact CVEs.
- New Vulnerability Reporting module
- Up to 14 days retention of individual reports
- Ability to generate a report instantly from the UI
- Flexible policies that can be attached to the different runtime and security contexts
Migrate to the new scanning engine
The new vulnerability management engine uses a different data storage, API, host components, and user interfaces than the legacy scanning.
- Contact your Sysdig representative. They will guide you through the process of migrating your subscription and vulnerability management configuration to the new engine.
- For more information, see Vulnerabilities.
Defect Fixes
- Addressed a number of critical and high vulnerabilities
- Fixed the issue where Compliance v2 reports return 204 status
- Fixed the issue where you are forced to use the email address format for login when LDAP is enabled. You can now log in using your username.
- Post GKE Nodepool upgrade elastic search pods no longer fail to start
- Added support for Linux cgroup v2 to the Sysdig PostgreSQL implementation for memory optimization
Falco Threat Detection Rules Changelog
Our Threat Research team has released several versions of the rules in the last month, including 169 new rules to extend support for Azure. Below are the release notes for the most recent rules changes.
https://docs.sysdig.com/en/docs/release-notes/falco-rules-changelog/
Rule Changes
- Added the following rules:
- CodeBuild Create Project with Miner
- CodeBuild Start Build with Miner
- CodeCommit Create Repository
- CodeCommit Git Push
- CodeBuild Create Project
- CloudFormation Create Stack
- SSH keys added to authorized_keys
- SageMaker Create Notebook Instance Lifecycle Configuration
- Image Builder Create Component
- Amplify Create App
- EC2 Create Auto Scaling Group
- Potential IRC connection detected
- CodeBuild Start Build
- ECS Create Cluster
- EC2 Create Launch Template
- Change memory swap options
- GLIBC "Looney Tunables" Local Privilege Escalation (CVE-2023-4911)
- Reduced false positives for the following rules:
- Mount launched in privileged container
- Kernel startup modules changed
- Read SSH information
- Possible Backdoor using BPF
- Suspicious Cron Modification
- Fileless Malware Detected (memfd)
- eBPF Program Loaded into Kernel
- Updated MITRE tags
- Updated the IoCs Ruleset with new findings
- Improved the sysdig_commercial_images & log_files lists
- Improved host and container tags
Default Policy Changes
- Added the following rules:
- GLIBC "Looney Tunables" Local Privilege Escalation (CVE-2023-4911)
- AWS CLI used with endpoint url parameter
- Hexadecimal string detected
- Unexpected Unshare event in Container
- Disallowed SSH Connection Non Standard Port
- Azure Suspicious IP Inbound Request
- GCP Change Owner
- Container escape via discretionary access control
- Updated the policy for:
- Suspicious device created in container
- Modification of pam.d detected
- Added SSM rules to
awscloudtrailpolicy - Added the Sysdig Azure Threat Intelligence policy
Open Source
Falco
Falco 0.36.1 is the latest stable release:
https://github.com/falcosecurity/falco/releases/tag/0.36.1
We suggest reviewing the release notes for 0.36.0 (released late September), which contains a number of major enhancements, as well as some breaking changes:
https://github.com/falcosecurity/falco/releases/tag/0.36.0
New Website Resources
Blogs
When Seconds Count: Expanding Real-Time Capabilities Across CNAPP
CVE-2023-38545: High Severity cURL Vulnerability Detection
How Sysdig can Detect Impersonation Attacks in Okta IdP
Agentless Vulnerability Management: A Complete Guide to Strengthening Your Security
eBPF Offensive Capabilities – Get Ready for Next-gen Malware
Scarleteel 2.0 and the MITRE ATT&CK framework
AWS's Hidden Threat: AMBERSQUID Cloud-Native Cryptojacking Operation
Webinars
How to Stop Cloud Attacks in Real-Time with Runtime Insights
Strengthening Cyberattack Preparedness Through Identity Threat Detection and Response (ITDR)
Rethinking Security at Cloud Speed
Combating Critical Cloud Vulnerabilities
Cloud Security Turbocharged: A Wild Ride of Innovation, Threats, and Staying Ahead
Beyond CSPM: Mastering Cloud Defense in the Age of Rapid Attacks
Sysdig Education
Sysdig Sage: https://www.youtube.com/watch?v=LoPaplPV4KA
Intro to Secure (video): https://www.youtube.com/watch?v=jJv4_HTxwVI
Intro to Monitor (video): https://www.youtube.com/watch?v=SyD_4sNadAQ
Vulnerability Management Landing Page (video): https://www.youtube.com/watch?v=1_uPQnVKZAI
Sysdig Live: https://www.youtube.com/watch?v=bo1D-jQssw8
Process Trees: https://www.youtube.com/watch?v=wqf_ZY_cqwQ


