The last few months at Sysdig have seen incredible product velocity as we accelerate our vision to create the leading cloud security platform, also known by the Gartner category Cloud-Native Application Protection Platform (CNAPP). In June, we enhanced our platform with end-to-end detection and response. Today, we are thrilled to unveil a suite of new capabilities powered by runtime insights:
- Cloud Attack Graph: A new engine for connecting the dots of cloud risk in real time, designed for the speed and sophistication of cloud attacks.
- Imminent Risk Prioritization: A prioritized list of risks generated by the Cloud Attack Graph and enhanced with indicators of active compromise.
- Emerging Attack Paths: A visualization of risks and exploitable links across resources, overlaid with real-time detections revealing active lateral movement.
- Inventory: Continuous visibility of all the code and deployed resources in your cloud environment, including vulnerabilities found on in-use packages.
- Agentless Scanning: Agentless host scanning expands on our existing agentless misconfiguration scanning and threat detection capabilities.
Skip ahead to the launch details!
The speed and sophistication of cloud attacks requires runtime insights
The same things that make the cloud great are now being weaponized. The scalability and extensibility of cloud services drive innovation, but attackers are exploiting this expanded attack surface to automate reconnaissance, move laterally, and exploit credentials. In short, today’s cloud attacks are fast and sophisticated, evading traditional EDR solutions.
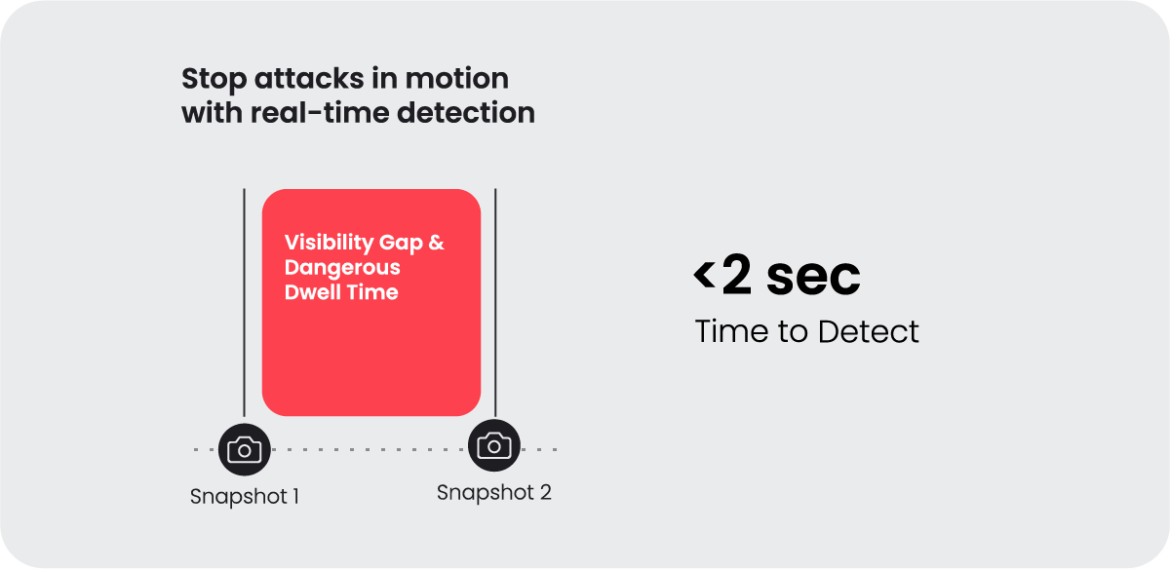
To put it in numbers, the Sysdig 2023 Global Cloud Threat Report found that cloud attackers are spending less than 10 minutes to execute an attack. Compare this to the median dwell time on-premises of 16 days (Mandiant).
Moreover, the cloud’s vast scale and complexity present unique security challenges, as the interconnected nature of cloud services creates a complex web of dependencies and potential vulnerabilities. In fact, this year we’ve seen a notable increase in attackers taking advantage of this to move laterally across environments, steal cloud IAM credentials, gain persistence, and exfiltrate data.
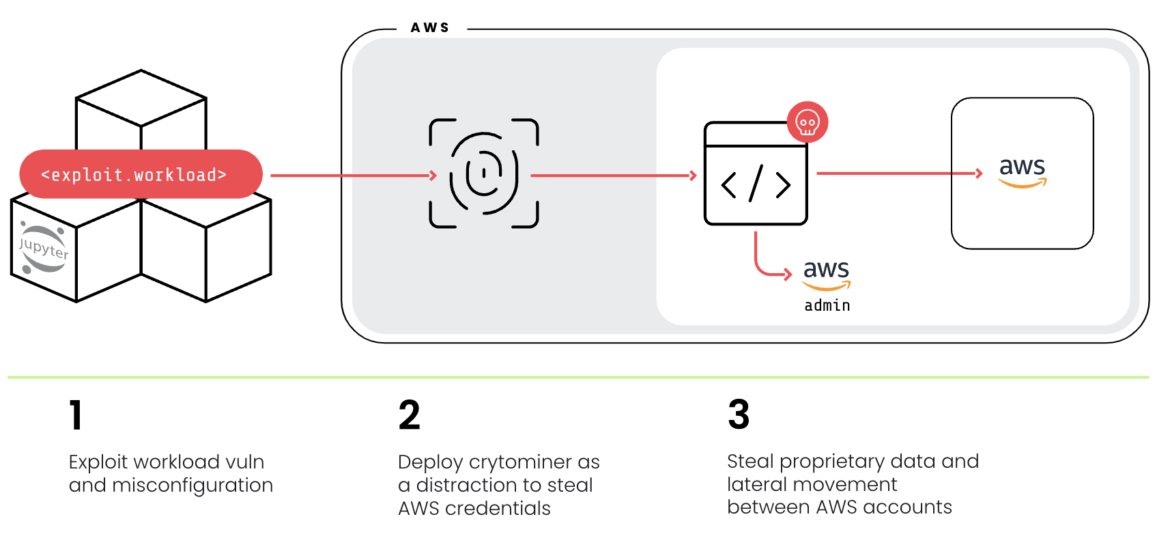
The speed and sophistication of cloud attacks demands a new approach that incorporates runtime insights, which address three key requirements in cloud security:
1. Real-time detection of active threats, instead of hours or days that you get with snapshot approaches.
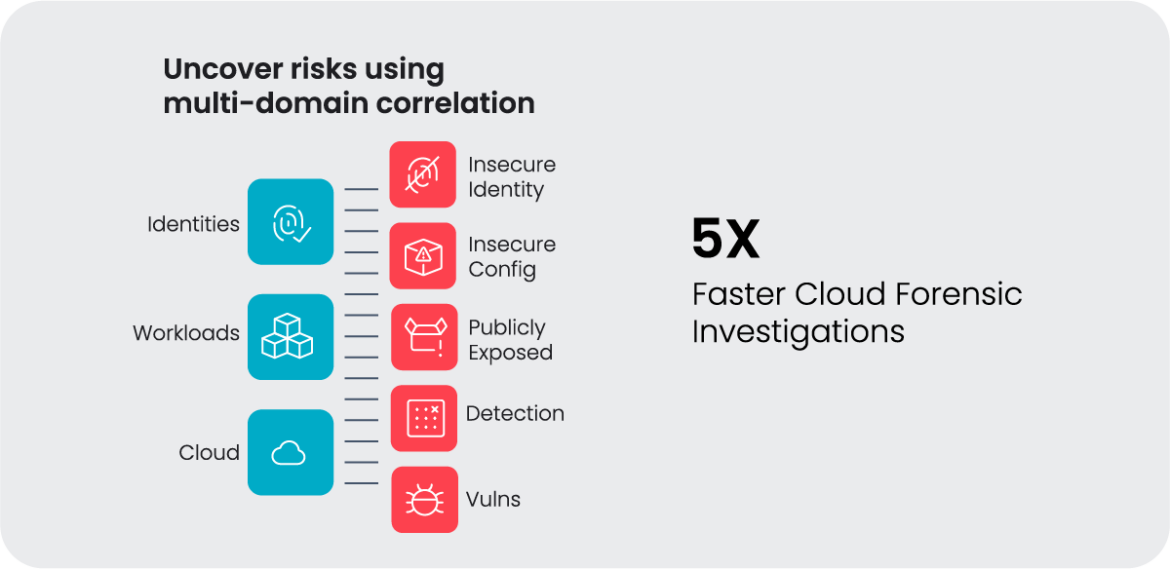
2. Multi-domain correlation to identify risky combinations across environments that create attack paths to sensitive data.
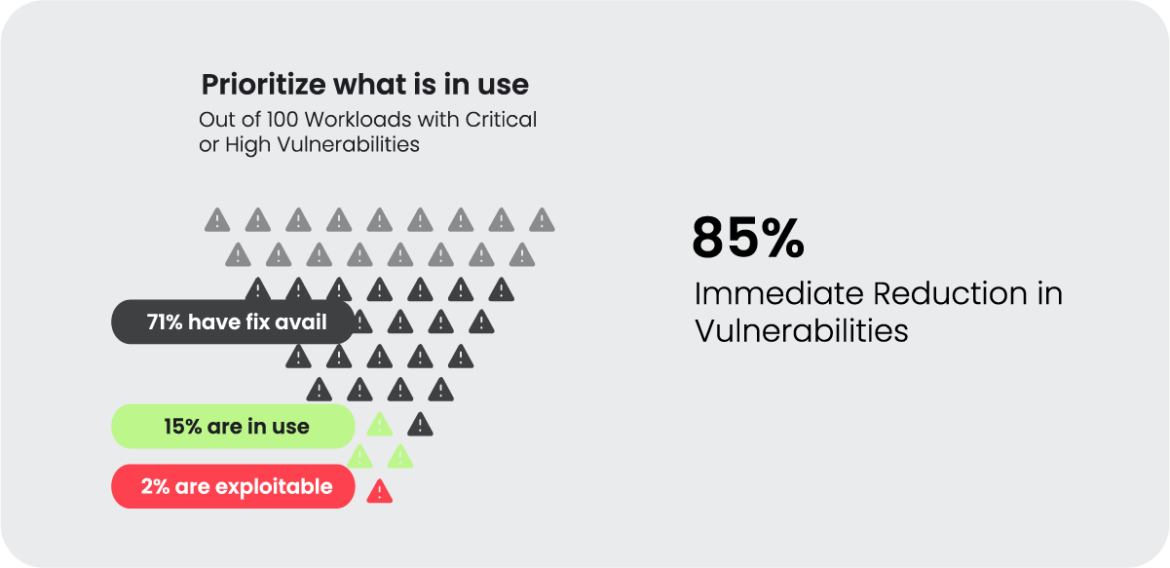
3. Prioritization of the most critical security risks by focusing on what’s in use, which significantly filters out noise
It’s clear a new approach is needed to address these new dynamics of the cloud and answer questions, such as:
- How can I easily understand what assets I have across my entire cloud estate?
- Where are my top risks today across all my interconnected resources and environments?
- If and when prevention efforts fail, how can I stop attacks in motion?
Let’s get into what we’re announcing.
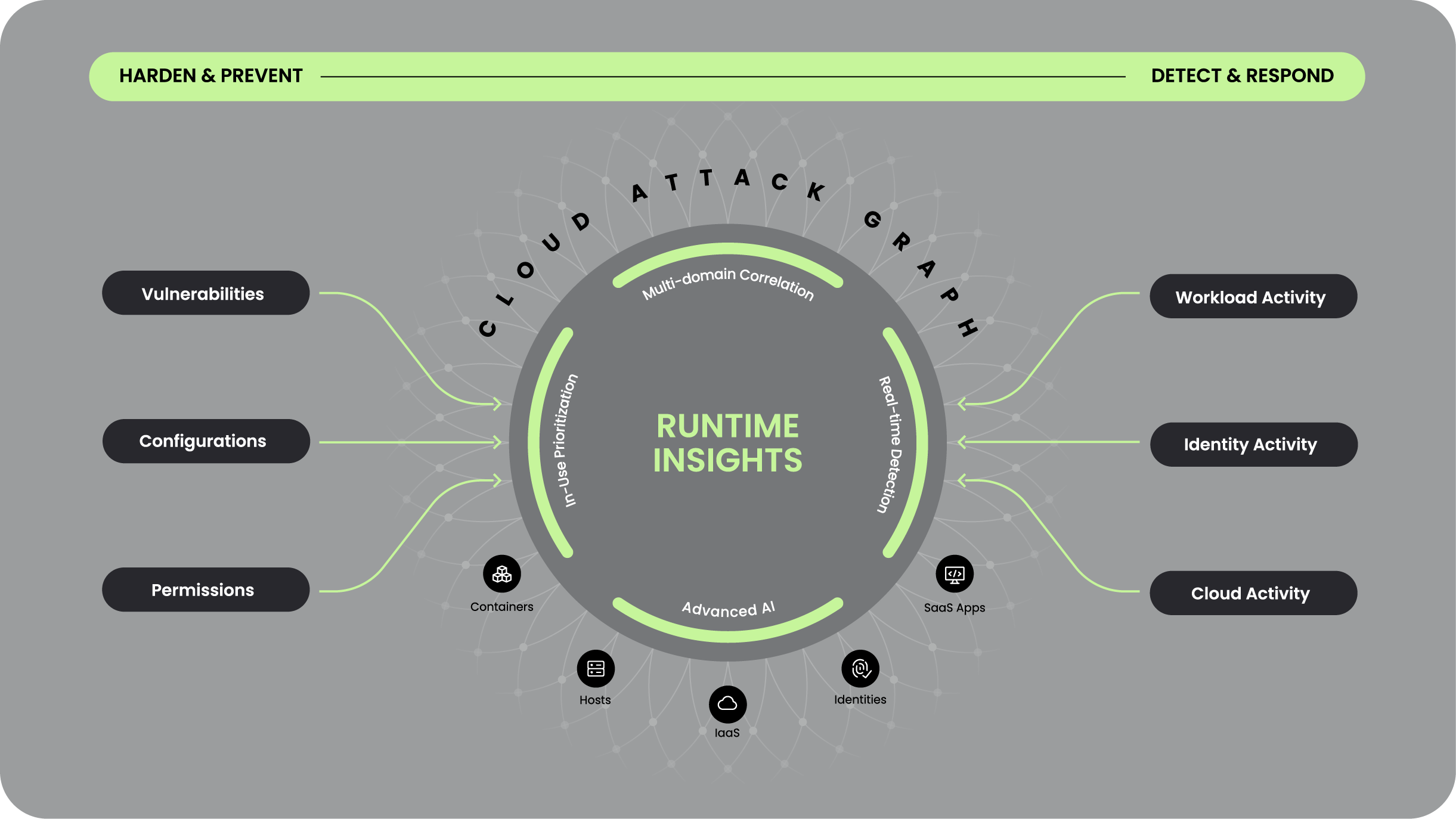
Cloud Attack Graph powered by runtime insights
Many security vendors offer some form of security or threat graph, but the speed and sophistication of cloud attacks required us to take a first principles approach to model complex cloud relationships and build real-time analysis layers.
We’re excited to unveil the Cloud Attack Graph, which functions as the neural center of the Sysdig platform, correlating assets, users, activity, and risk to identify threats in real time.
What differentiates it from other security graphs is a capability we call “runtime insights,” which powers the Cloud Attack Graph with four unique capabilities:
- Real-time detection of security events.
- Understanding the context of what is actually in use to prioritize what to fix.
- Using this context to do multi-domain correlation to identify risky combinations across environments.
- Deploying advanced AI for higher fidelity detections and simple plain language queries of the graph.
Prioritize the top risks and visualize the attack paths
As previously mentioned, the Cloud Attack Graph functions as the neural center of the Sysdig platform that connects the dots between assets, users, activity, and risk across domains.
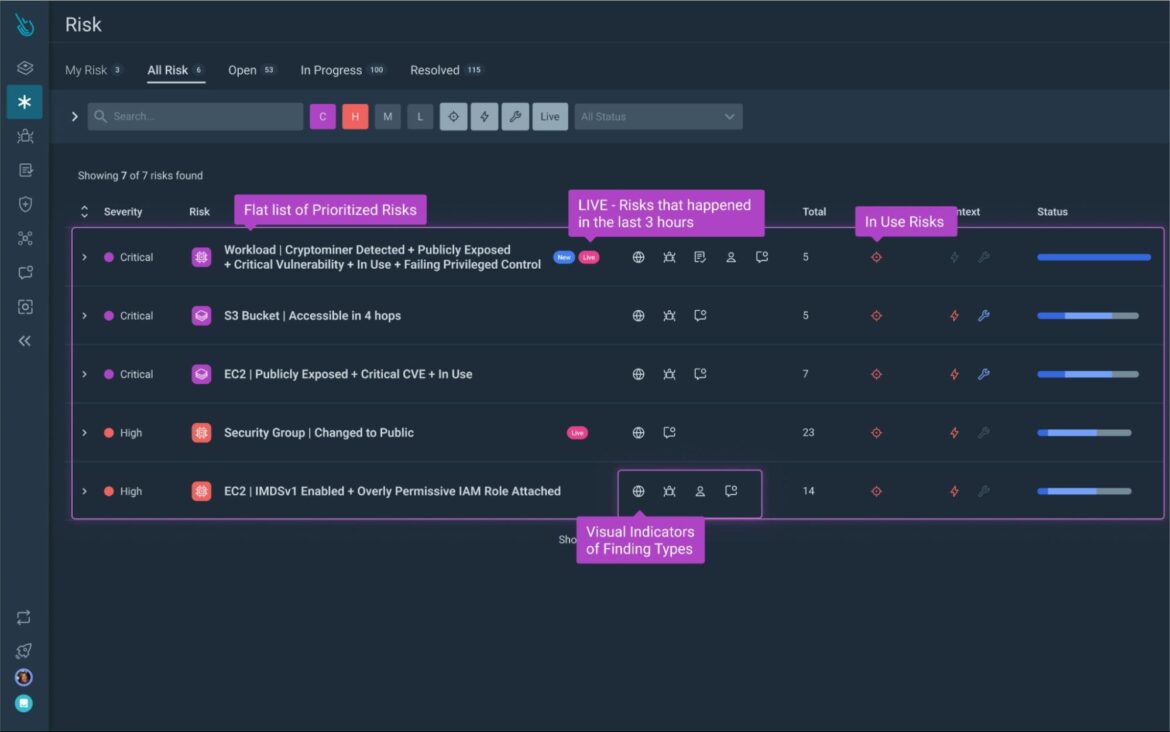
A powerful output of this technology is a new stack-ranked view of risks, helping you prioritize what to fix across your cloud environment. The risks are generated by evaluating the specific combination of findings, context, and potential attack paths, and are presented alongside guided remediation suggestions to take action fast.
Let’s look at the prevalence of security findings in isolation and how they can be correlated to uncover the top risks across your cloud environment.
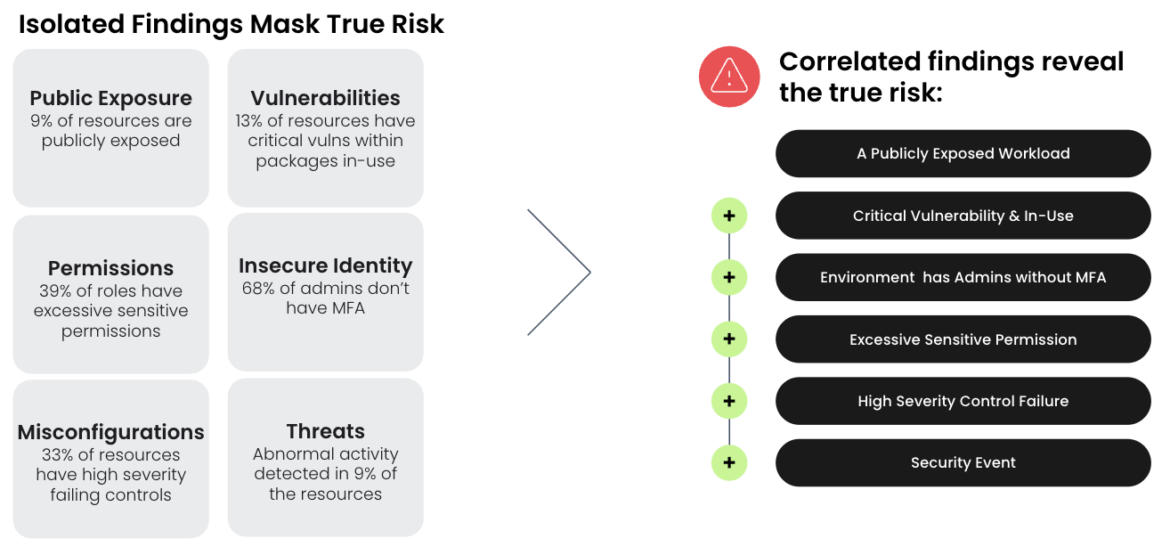
This combination of findings results in an imminent risk that would be at the top of your list to address; they would have not been revealed if you combed through the myriad of findings in isolation. Runtime insights are required to spotlight such a risk, layering on real-time detection of events, vulnerabilities tied to in-use packages, and in-use permissions.
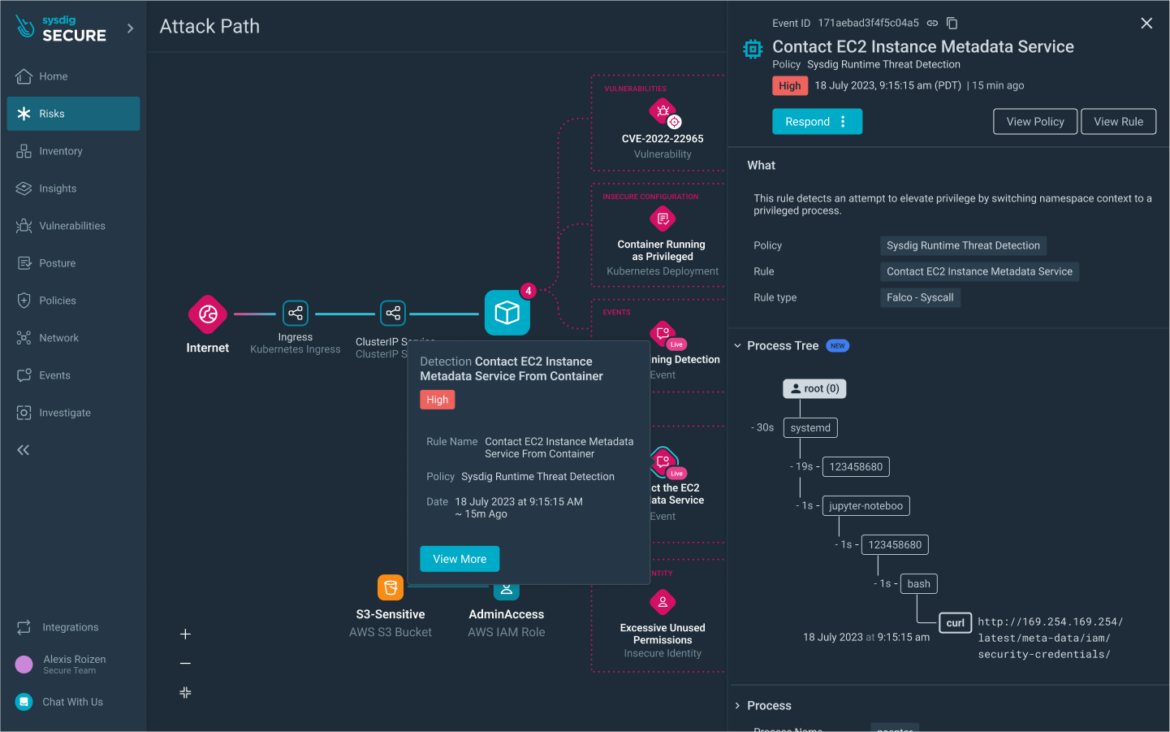
For each risk, you can now visualize the exploitable links across resources to uncover potential attack paths. Unlike other solutions, Sysdig is able to layer on real-time detections to reveal active lateral movement and initiate workflows to respond to threat events, vulnerabilities, or misconfigurations.
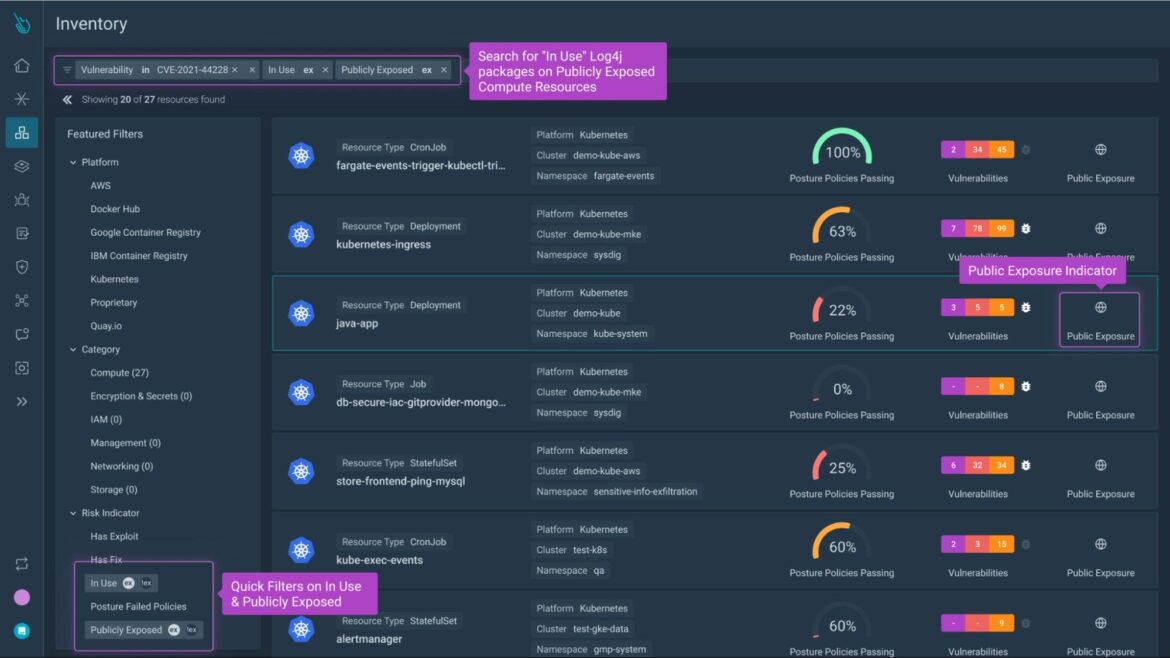
Complete cloud visibility with an enhanced Inventory
One of the top concerns we hear from security leaders is simply, “What do I have in the cloud?” But the answer to this seemingly simple question is remarkably complex, especially with the detail and context needed to take action.
Inventory provides a complete searchable list of all the resources in your cloud environment across users, workloads, hosts, and container images. Powered by Sysdig’s runtime insights, search for vulnerabilities in active packages to prioritize what matters. For example, use Inventory to quickly check exposure to a high profile vulnerability such as “all instances of Log4j in running packages and exposed to the internet.”
Then, dig deeper into potentially compromised workloads with a real-time view of associated events, vulnerabilities, and posture.
Agentless Scanning of Cloud Hosts
We’ve expanded our agentless capabilities to include host scanning, complementing our existing agentless scanning for misconfigurations and threat detection.
The onboarding experience now shows results of the scan in minutes, with no active components in your environment, and no disruption to running hosts, clusters, or pods.
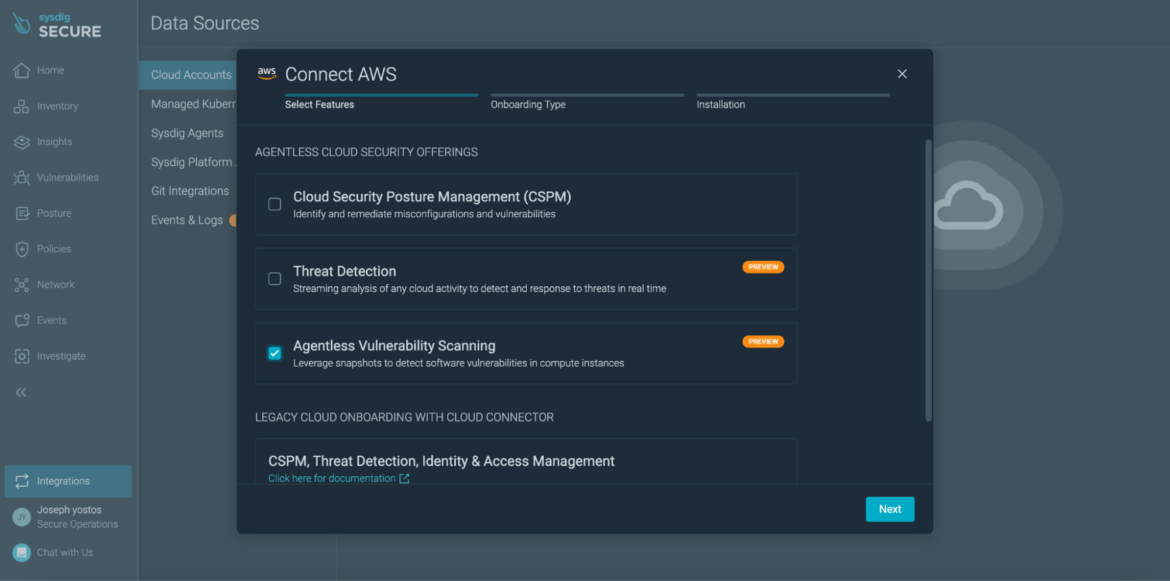
Sysdig now offers a complete agent and agentless solution. Our agentless approach provides comprehensive visibility into your cloud security posture by giving you an overview of your vulnerabilities, misconfigurations, in-use permissions, and threats in the cloud. This approach is complemented by our scalable and performant agent that provides real-time analysis of active processes across workloads and hosts, and can filter out vulnerabilities associated with packages that are not running, which is critical for prioritization.
Want to learn more?
These new capabilities greatly enhance our top-rated CNAPP solution. Wherever you are on your cloud journey, we’re here to help secure it. Click here to learn more about the Sysdig platform.


