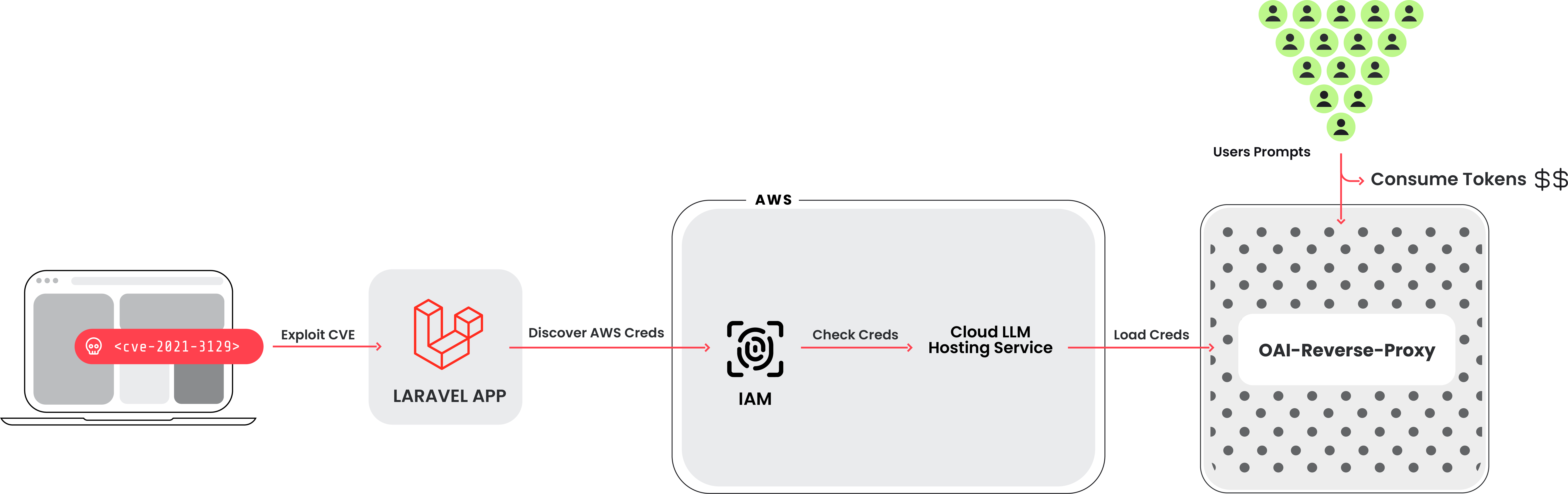
Discovering the latest attacks and providing defensive measures to keep organizations safe

The Cloud Defense Report 2025
Discover key insights and trends in real-world cloud security and usage — and see how enterprises are advancing their defenses.
Rules feed
Name
Severity
Framework 1
Framework 2
Link
Long name for up to ten words “vulnerability management” test
Critical
Example text that can
Example text
Led by the industry’s most elite threat researchers
Meet with us / upcoming events
Browse all resources
2025 Cloud-Native Security and Usage Report
2024 Cloud-Native Security and Usage Report
About the team
The Sysdig Threat Research Team (TRT) are highly skilled security experts dispersed across the globe, with experience in governmental, commercial, and academic arenas. Their expertise includes offensive and defensive security operations, computer network operations, malware analysis, and beyond.
The team is well-known for introducing the 10-minute timeframe for cloud attacks, setting the 555 Benchmark for Cloud Threat Detection and Response, and uncovering novel threats like SCARLETEEL.