
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

On Monday, March 24, 2025, a set of critical vulnerabilities affecting the admission controller component of the Ingress NGINX Controller for Kubernetes was announced. In total, five vulnerabilities were announced; the most severe vulnerability, CVE-2025-1974 (CVS 9.8), may result in remote code execution (RCE). Exploitation of this vulnerability can be detected with Sysdig Secure or the Falco rule provided in this article.
While there is no publicly available proof of concept as of this blog’s publication, there are enough technical details for this vulnerability that one will likely be developed and readily available soon.
Vulnerabilities
CVE-2025-1974 (CVSS score: 9.8) — Unauthenticated remote command execution
CVE-2025-1098 (CVSS score: 8.8) — Configuration injection via unsanitized annotation
CVE-2025-1097 (CVSS score: 8.8) — Configuration injection via unsanitized annotation
CVE-2025-24514 (CVSS score: 8.8) — Configuration injection via unsanitized annotation
CVE-2025-24513 (CVSS score: 4.8) — Path traversal
Amazon EKS and Google GKE do not install the NGINX Ingress Controller by default.
How ingress controllers work
An ingress controller is a component in the Kubernetes infrastructure that works as a reverse proxy and load balancer. It converts configurations from Kubernetes Ingress into routing rules, providing an entry point for external traffic to the services inside the cluster.
Different software and open source projects implementing ingress controllers are available in Kubernetes environments. One of the most used is NGINX. To translate Kubernetes Ingress objects into routing NGINX configurations or any other technology, as soon as they get deployed, the controller uses a validating admission webhook to validate the final configuration before applying it. However, due to unsafe handling of NGINX configuration, a specially crafted ingress request could lead to credential exfiltration and arbitrary command execution.
IngressNightmare impact
By default, the NGINX Ingress Controller is not publicly exposed. However, an attacker who gains a foothold on a pod may be able to access the controller. If the controller has been configured to be publicly exposed, then remote attackers may be able to exploit the vulnerability.
An attacker that can reach the NGINX admission controller service must craft malicious ingress objects to exploit the vulnerability. Once the vulnerability is exploited, the attacker can run arbitrary commands from the NGINX Ingress Controller pod, which has a highly sensitive service account mounted. Such service accounts could be used to get secrets from the whole cluster, potentially leading to cluster and service compromise and credential theft.
Detecting CVE-2025-1974
Among the vulnerabilities reported, the most impactful is the CVE-2025-1974, which allows unauthenticated remote code execution. This class of vulnerability allows an attacker to execute arbitrary code, potentially leading to a cluster-wide impact due to the Kubernetes role assigned to the NGINX Ingress Controller pod. Since this role has elevated permissions, an attacker could exploit it to escalate privileges within the cluster
To exploit the vulnerability, an attacker needs to perform the following steps:
- Use NGINX Client Body Buffering to upload a shared library to the target pod
- Send an AdmissionReview request to the NGINX admission controller with the
ssl_engine load_moduledirective, causing NGINX to load the previously uploaded shared library - Get the shared library being executed using the file descriptor reference from the
/procfilesystem (in particular, by searching for it in/proc/*/fd/*)
This exploit can be detected by monitoring shared libraries loaded from /proc in the NGINX Ingress container.
Sysdig Secure customers automatically have the rule Potential IngressNightmare Vulnerability Exploitation added to the Sysdig Runtime Threat Detection policy.
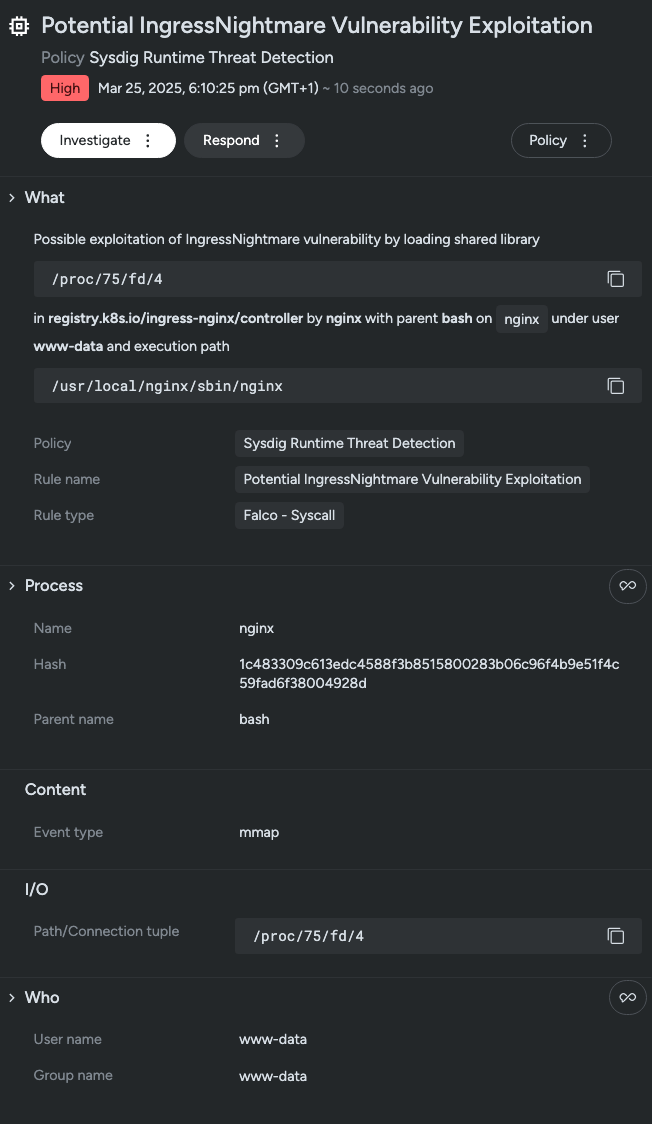
Falco users can apply the rule below to detect this vulnerability being exploited.
- rule: Potential IngressNightmare Vulnerability Exploitation
desc: This rule detects a possible exploitation of IngressNightmare vulnerability (CVE-2025-1974), where the NGINX process loads a shared library from the ProcFS. This execution may indicate a malicious actor attempting to exploit the vulnerability before executing other arbitrary code in the ingress controller container.
condition: evt.type in (mmap,mmap2) and proc.name contains "nginx" and fd.name startswith "/proc/" and fd.name contains "/fd/" and evt.arg.prot contains PROT_EXEC and container
output: Possible exploitation of IngressNightmare vulnerability by loading shared library %fd.name in %container.image.repository by %proc.name with parent %proc.pname on %container.name under user %user.name and execution path %proc.exepath (proc.name=%proc.name proc.pname=%proc.pname fd.name=%fd.name proc.exepath=%proc.exepath proc.pexepath=%proc.pexepath gexepath=%proc.aexepath[2] ggexepath=%proc.aexepath[3] gggexepath=%proc.aexepath[4] proc.cmdline=%proc.cmdline proc.pcmdline=%proc.pcmdline gcmdline=%proc.acmdline[2] ggcmdline=%proc.acmdline[3] gggcmdline=%proc.acmdline[4] gparent=%proc.aname[2] ggparent=%proc.aname[3] gggparent=%proc.aname[4] evt.type=%evt.type proc.args=%proc.args proc.pid=%proc.pid proc.cwd=%proc.cwd proc.ppid=%proc.ppid user.uid=%user.uid user.loginuid=%user.loginuid user.name=%user.name container.id=%container.id container.name=%container.name image=%container.image.repository:%container.image.tag)
priority: WARNING
tags: [container, MITRE, MITRE_TA0002_execution]Mitigating CVE-2025-1974
The following versions of the Ingress NGINX Controller are affected by these vulnerabilities:
< v1.11.0v1.11.0 - 1.11.4v1.12.0
Fixes have been released in versions v1.11.5 and v1.12.1.
Organizations should prioritize remediating this vulnerability and patch all affected systems immediately. Remediation entails upgrading all instances of Ingress NGINX Controller to the latest version in the environment and ensuring the admission webhook endpoint isn’t publicly exposed.
Conclusion
The Ingress NGINX Controller is one of Kubernetes’ most popular ingress controllers, with thousands of stars on Github. Combining all these vulnerabilities allows an attacker to achieve remote code execution and potential overall Kubernetes cluster compromise. Using Sysdig Secure, which is powered by open source Falco, this type of attack can be detected in seconds so a response can be quickly initiated.


