Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Today's digital organizations thrive in the cloud. The advantages are undeniable – cost savings, scalability, and seamless access to resources, applications, and data all foster better business agility, collaboration, and innovation. With over 85% of organizations adopting a cloud-first strategy by 2025, it's clear that the cloud is integral to modern operations.
However, the increased integration of businesses with cloud environments has transformed the cloud into an alluring target for cybercriminals. As organizations extensively conduct their business operations and store valuable data in the cloud, it becomes a profitable focus for attackers seeking financial gains. In response to the escalating risk of cyber threats, organizations must actively reassess and enhance their approaches to fortify cloud security.
The unique challenge of cloud attacks
A cloud cyber attack zeroes in on an organization's chosen cloud service provider – think AWS, GCP, or Microsoft Azure – employed for storage, computing, or hosting services.
As businesses increasingly embrace cloud services models such as SaaS, IaaS, and PaaS, they unwittingly expand their attack surface. Take the adoption of microservices, for instance, which leads to a proliferation of publicly accessible workloads. Additionally, there are containerized applications, developers using packages from third-party libraries, and third-party cloud applications, all of which serve as examples of how the cloud makes things more complex for security teams and introduces many entry points for attacks.
Gaining comprehensive visibility into the many cloud services distributed across an organization's various providers is not just desirable, it's an absolute necessity for robust security. However, conventional security tools were not tailored for the array of new environments, services, and resources in the cloud, resulting in significant gaps. The multitude of assets to monitor amplifies these visibility gaps, posing a considerable security risk.
These challenges raise a crucial question for organizations: What are the best tools for cloud security management?
Innovations in cloud security solutions
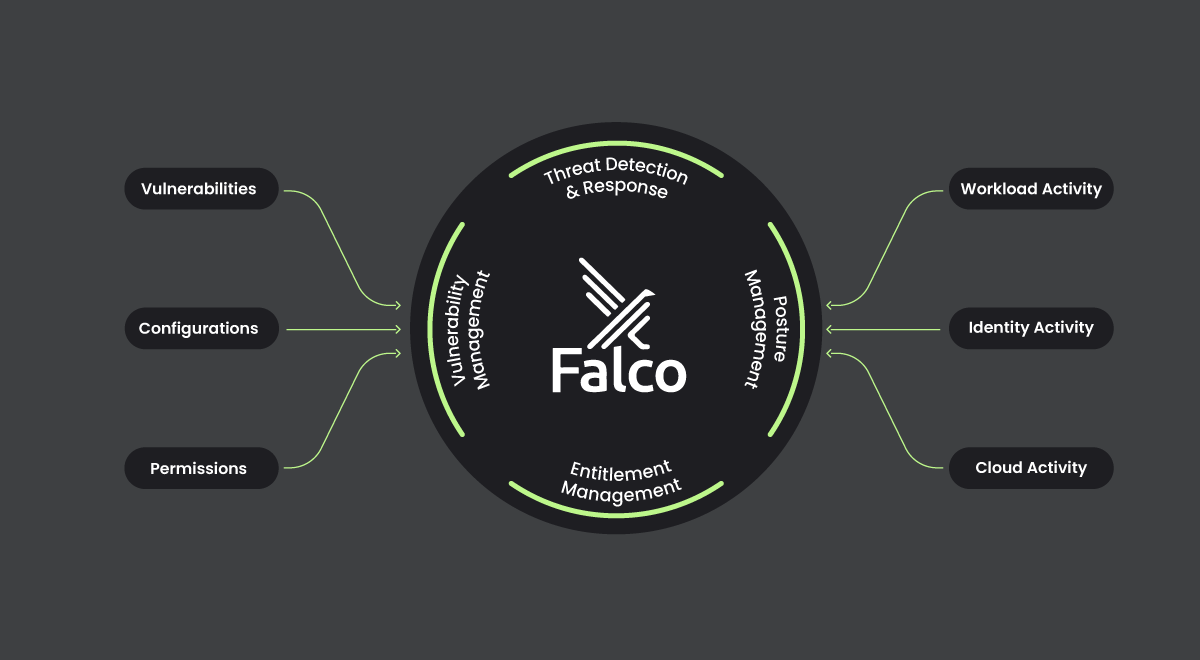
Amid the mounting cyber threats in the cloud, security vendors have adapted their solutions for cloud platforms. The past decade witnessed the emergence of point solutions that address specific aspects of cloud security, such as configuration management, permissions and entitlement management, and threat detection and response. However, with the exacerbation of cloud security risks, organizations have come to recognize the limitations of these baseline security solutions. These tools prove insufficient in meeting the dual needs of prevention – entailing the hardening of posture and addressing vulnerabilities and misconfigurations in cloud infrastructure – and defense, which involves runtime security and threat detection.
This realization spurred the emergence of Cloud-Native Application Protection Platforms (CNAPPs) as the preferred approach for cloud security. A CNAPP solution consolidates critical features from disparate point products into a singular, streamlined platform, offering a comprehensive approach to identifying and mitigating cloud risks. Encompassing the entire spectrum from build to runtime, CNAPP seamlessly integrates cloud security posture management (CSPM), container security and workload protection, permissions management, and cloud detection and response (CDR).
CNAPP solutions elevate visibility into enterprise workloads and provide enhanced control over security and compliance risks in cloud environments. Proficient in identifying security issues at an early stage, these solutions help organizations save on costs, prevent expensive rework, and ensure that cloud workloads are inherently secure, having been fortified prior to deployment. Equally important, CNAPP also provides full visibility of threats across cloud infrastructure, enabling organizations to proactively prevent live attacks before they cause damage or access sensitive data.
Prioritizing relevance in CNAPP deployments
As organizations embrace CNAPP solutions to consolidate their security arsenal, a crucial challenge surfaces: how to effectively manage and refine the powerful visibility they offer. While CNAPPs seamlessly unify critical security capabilities, without properly prioritizing what's most relevant to an organization, they can inadvertently generate an overwhelming flood of signals.
The DevSecOps teams, tasked with deciphering this constant stream of alerts, often find themselves inundated and struggling to discern which vulnerabilities and threats pose a genuine and pertinent risk to the organization. As they navigate this wealth of signals, the sheer volume can lead to a drain on resources and team burnout.
So, what's the way forward? The key lies in leveraging Runtime Insights to enhance an organization's CNAPP strategy and streamline security operations. By adopting CNAPP solutions that infuse runtime insights into the equation, organizations can not only maintain robust visibility but also focus their efforts on addressing the most critical and imminent threats, ultimately bolstering the efficiency of their security operations and strengthening their security posture.
Elevating security through runtime insights
While it's impossible to eliminate risk entirely, the critical element in minimizing risk is guiding teams to concentrate on findings with the potential to impact the business. Runtime insights make that possible by providing DevSecOps teams with valuable information for prioritizing findings based on risk level and business context.
Runtime insights – the knowledge of what's actively running in an organization's production environment – are the key for CNAPP solutions to effectively prioritize issues and ensure users don't experience alert overload. Armed with runtime information, organizations can expertly manage their cloud security posture by focusing their attention where it matters most, including:
- Context about live operations and what services are actually in use
- Visualizations that highlight gaps in environment configuration
- Continuous and real-time detections
- Comprehensive analysis of everything in an organization's cloud environments (i.e., hosts, containers, cloud services, and serverless functions) and how they are connected
The CNAPP actively analyzes these runtime insights and correlates the activity across them to detect high-priority risks, rather than merely looking at them as isolated findings. This contextual analysis surfaces attacker activity that is leveraging several of these avenues simultaneously to execute an attack.
Together, CNAPP and runtime insights form a powerful combination that empower organizations to effectively distinguish genuine security concerns and address issues at an earlier stage. Once issues are prioritized, DevSecOps can respond to attacks at cloud speed with an understanding of what is happening, the exact location in the cloud where an issue is occurring, and what's causing the problem.
Essential elements for CNAPP integration
As threat actors escalate their focus on cloud environments, organizations must prioritize selecting a CNAPP solution capable of protecting their applications and data from cyber attacks. When integrating CNAPP into an organization's existing tech stack, it's important to consider the following key elements:
- Comprehensive cloud security coverage
Ensure the CNAPP solution covers all components of the cloud environment and workload, including containers, orchestrators, various virtual machines, and underlying cloud infrastructure. Regardless of the application type, architecture, or configuration, an organization's CNAPP should provide end-to-end coverage. - Centralized management
A streamlined and centralized management system is essential for efficient security operations. Look for a CNAPP that simplifies and consolidates security management processes. - Risk prioritization
The integration of runtime insights helps eliminate alert noise and is essential for providing visibility and context into cloud threats, enabling organizations to discern real priorities. Prioritizing risks based on business impact ensures resources are allocated where they are needed most.
Embracing the future of cloud security
The integration of CNAPPs and runtime insights are emerging as a cornerstone of innovation, enabling organizations to effectively navigate and fortify their cloud security posture. This transformative approach goes beyond mere threat response, empowering organizations to proactively anticipate and mitigate potential risks.
As organizations traverse the complexities of the cloud journey, the adoption of a CNAPP with runtime insights becomes a pivotal strategy for securing cloud environments. The narrative of cloud security is undergoing a redefinition, and the emphasis is clear – runtime insights, paired with CNAPP, are the new guide on the journey toward a secure and resilient cloud environment.


