Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

This week CVE-2019-3874 was discovered which details a flaw in the Linux kernel where an attacker can circumvent cgroup memory isolation using the SCTP socket buffer. In containerised environments, this has the potential for a container running as root to create a DoS.
\r\r
To verify if you're vulnerable, you can check if the SCTP module is loaded:
\r\r$ modprobe sctp; lsmod | grep sctp\r\r\r
sctp 311296 2\r
libcrc32c 16384 4 nf_conntrack,nf_nat,raid456,sctp\r
If you see SCTP like in the output above, you may be vulnerable. SELinux prevents binding to the SCTP socket by non-root users, however where SELinux is not enforcing, it is advised to disable and blacklist the SCTP kernel module (requires a hard reboot).
\r\r
This vulnerability has been given a CVSS rating of 5.3 – a kernel patch is in development and expected soon. Detecting + preventing cgroups escape via SCTP – #CVE-2019-3874 #Kubernetes #security. Click to tweet
\r\r
Detecting & stopping CVE-2019-3874 using Sysdig Falco
\r\r
Sysdig Falco is an open source, container security monitor designed to detect anomalous activity in your containers. Sysdig Falco taps into system calls to generate an event stream of all system activity. Falco's rules engine then allows you to create rules based on this event stream, allowing you to alert on system events that seem abnormal. Falco's rich language, allows you to write rules at the host level and identify suspicious activity.
\r\r
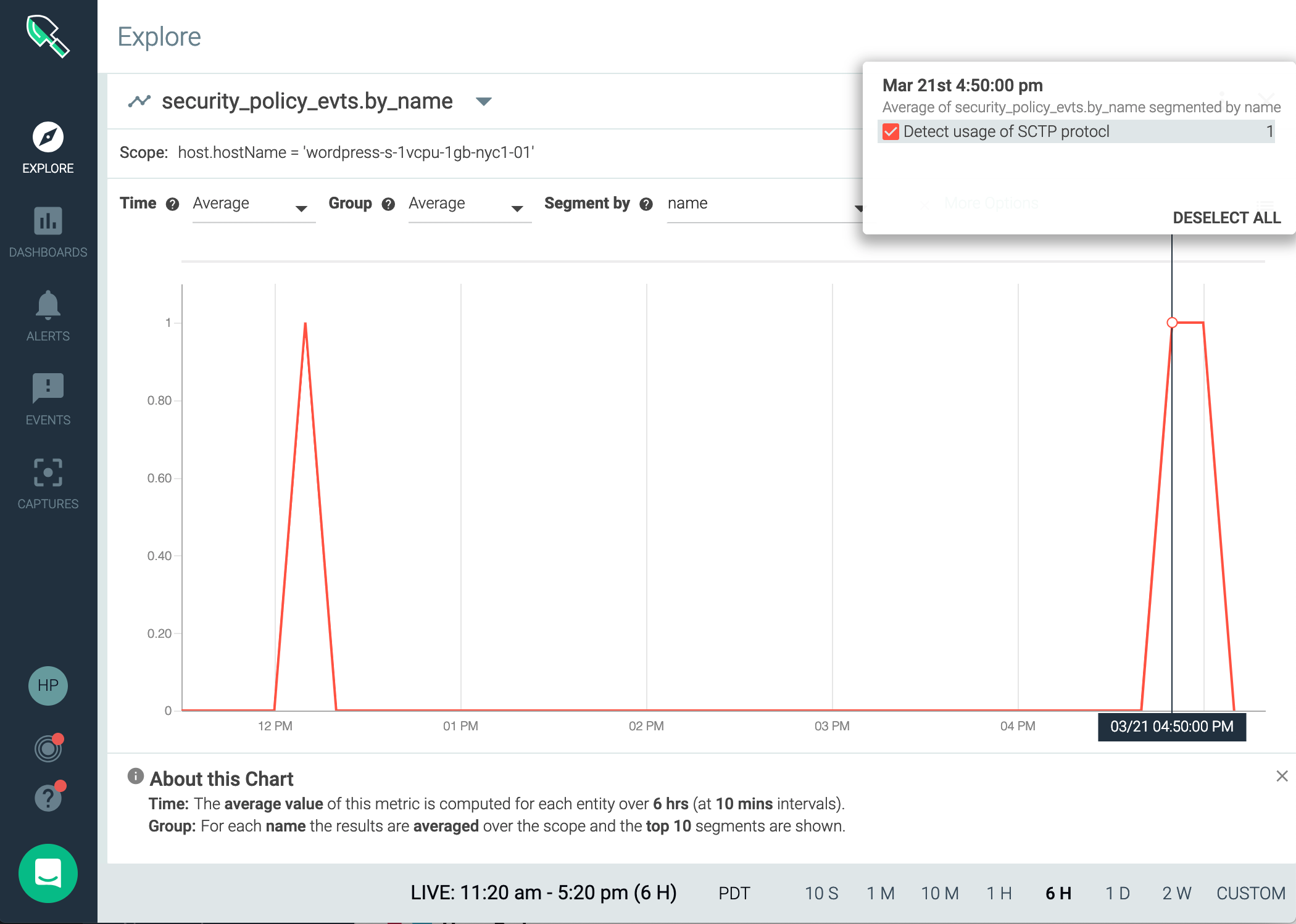
Using Falco we can create a rule to detect containers attempting to bind SCTP and kill them before a DoS attack can be accomplished.
\r\r
Because Falco uses Sysdig's powerful filter engine, we can easily identify the use of SCTP by looking for protocol number 132 (SCTP) used as part of a socket bind. We can then create a rule that detects a SCTP bind attempt within a container:
\r\r
\r\r\r <pre><code>\r<br>File: falco-CVE-2019-3874.yaml\r<br>------------------------------\r<br># We're looking for a socket() bind using protocol number 132 (SCTP)\r<br>- macro: sctp_bind\r<br> condition: (evt.type=socket and evt.arg.proto=132)\r<br># Detect an SCTP bind from inside a container \r<br>- rule: Memory cgroups escape via sctp - CVE-2019-3874\r<br> desc: Potential exploit of CVE-2019-3874 - see https://bugzilla.redhat.com/show_bug.cgi?id=1686373\r<br> condition: >\r<br> sctp_bind and container\r<br> output: >\r<br> sctp bind attempt! (%container.name, %proc.exeline)\r<br> priority: WARNING\r<br></code></pre>\r\r\r
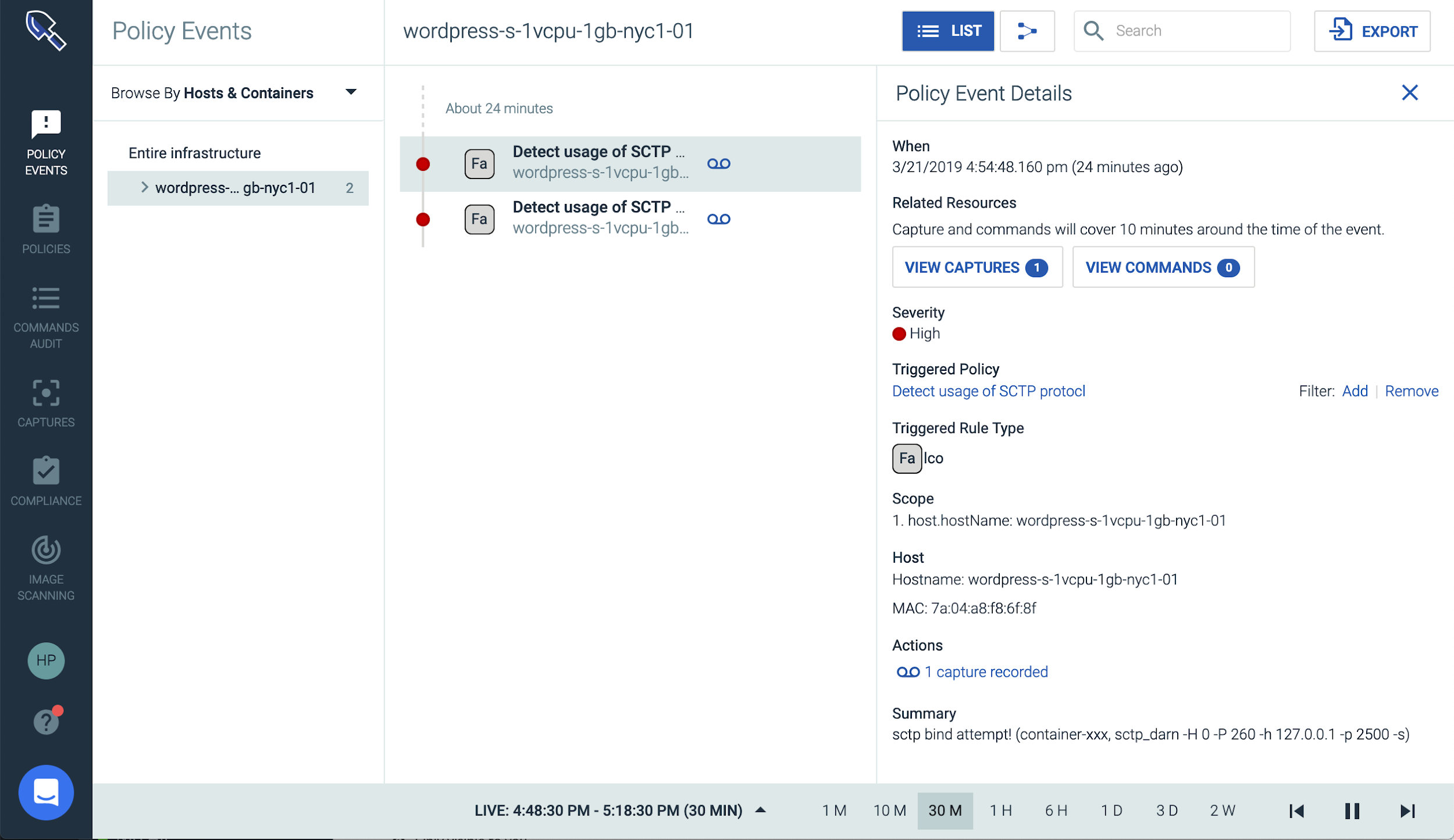
Leveraging this rule within Sysdig Secure allows us to provide some enforcement by stopping the container. This effectively stops the attack in its tracks. With our policy configured to capture all activity that took place before, during, and after an attack, we have all the data we need to perform detailed forensics.
\r\r
\r\r
Detecting CVE-2019-3874: End to end security with Sysdig
\r\r
Of course, ideally Sysdig's container run-time protection is a last line of defense against the most nefarious attacks. The Sysdig platform provides a comprehensive suite of steps to secure our environment, such as image scanning, container compliance and visibility that can help detect and prevent the exploitation of such an attack.
\r\r
1. Prevent vulnerable images prior to deployment
\r\r
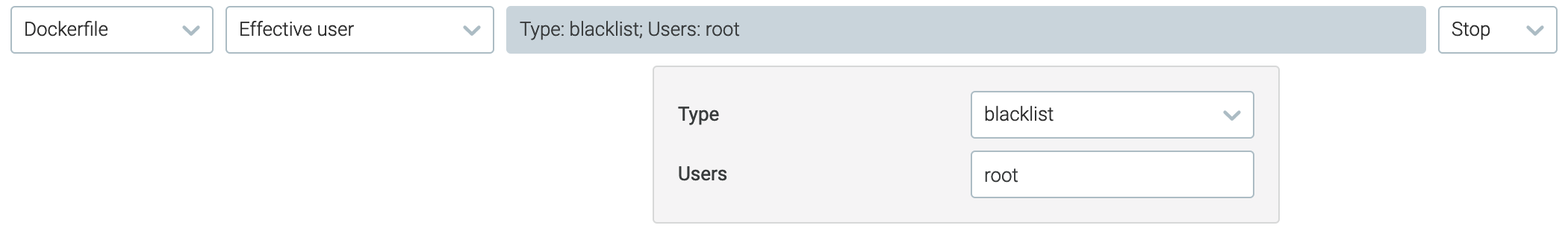
Sysdig Secure prevents misconfigured images from being pushed through your CICD pipeline by integrating with tools like Jenkins scanning, Bamboo scanning, etc or run in production. When securing your deployment pipeline with Sysdig's image scanning policies, you can block containers from being deployed where the effective user is root:
\r\r
\r\r
In addition, if you're not yet using pod security policies, you can generate effective policies with kube-psp-advisor.
\r\r
\r\r
2. Ensure best practices based security posture
\r\r
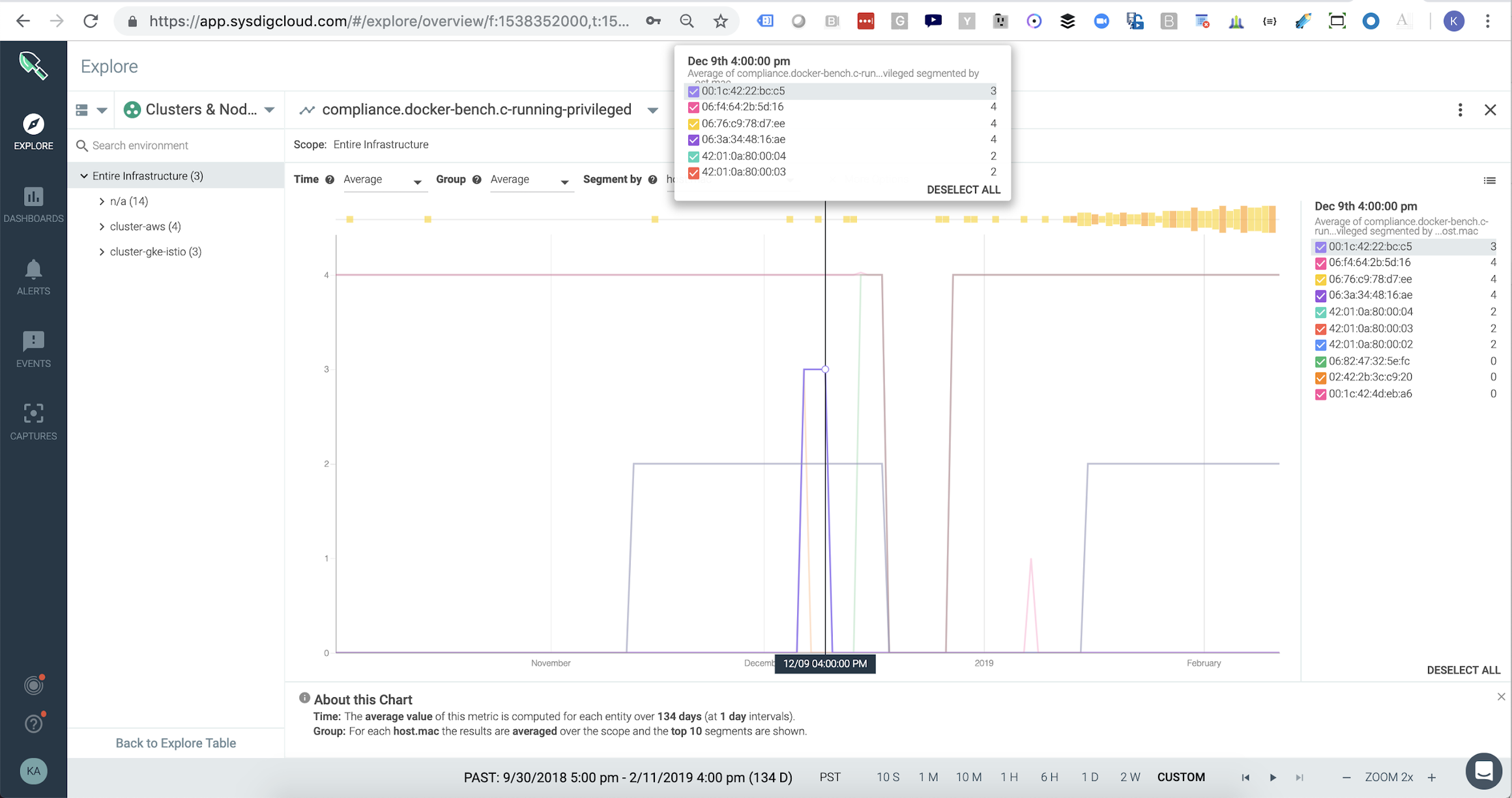
Sysdig Secure offers comprehensive container compliance for Docker and Kubernetes environments. Users can run CIS benchmark checks for their Docker containers. This allows them to quickly isolate containers that are running in privileged mode.
\r\r
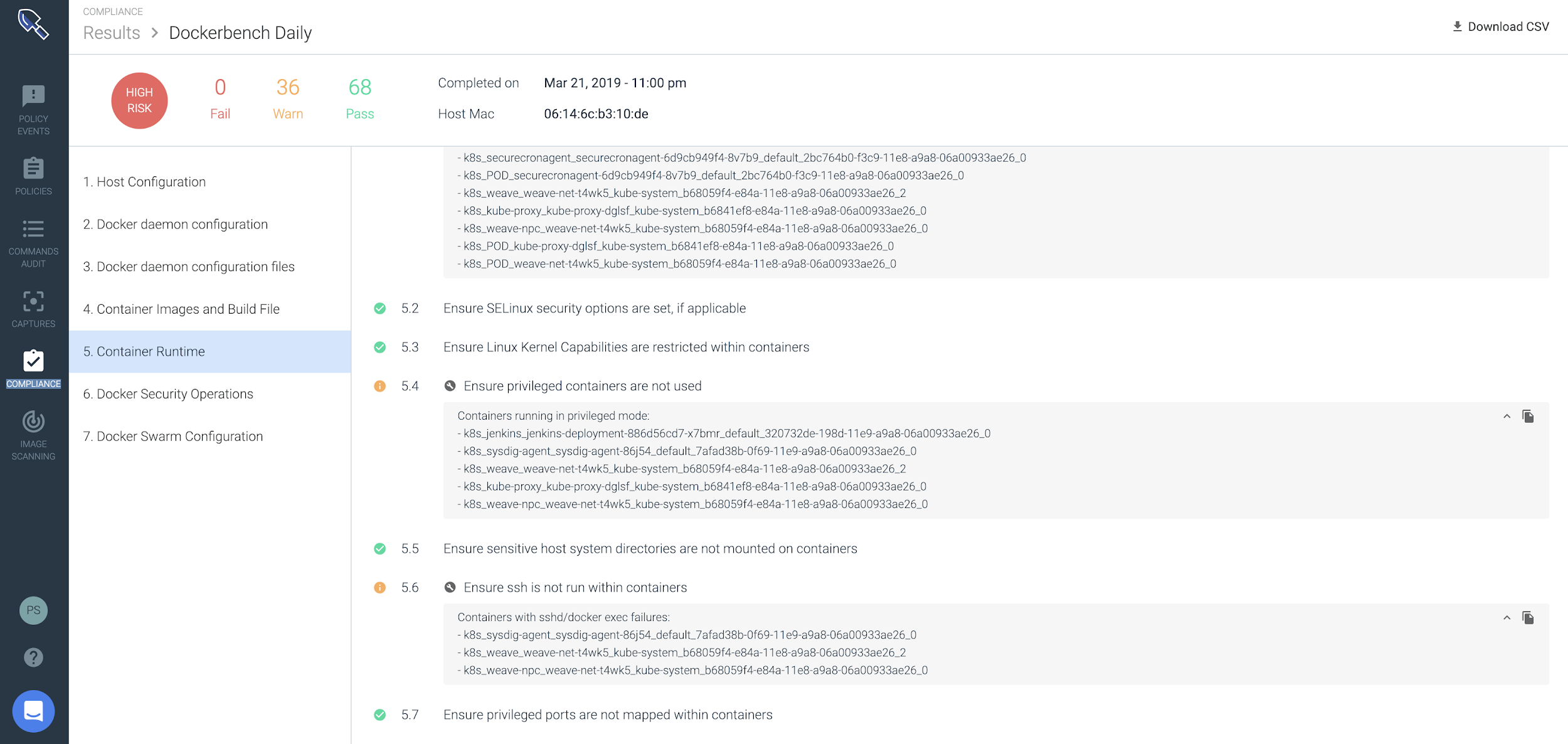
\r\r
3. Gain visibility into container infrastructure
\r\r
Sysdig Monitor provides a topology map that shows the average of all images running with a root user across your multiple kubernetes clusters either on-prem or in the cloud.
\r\r
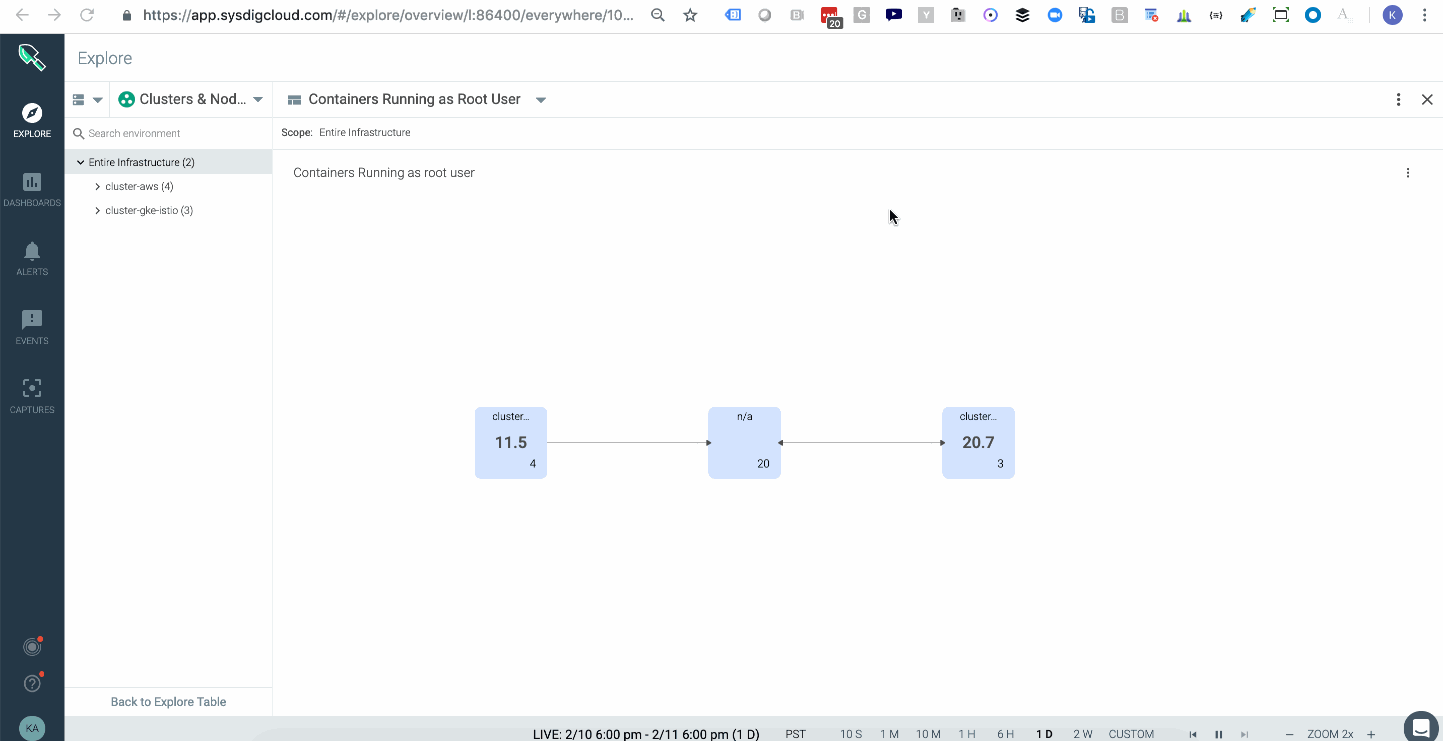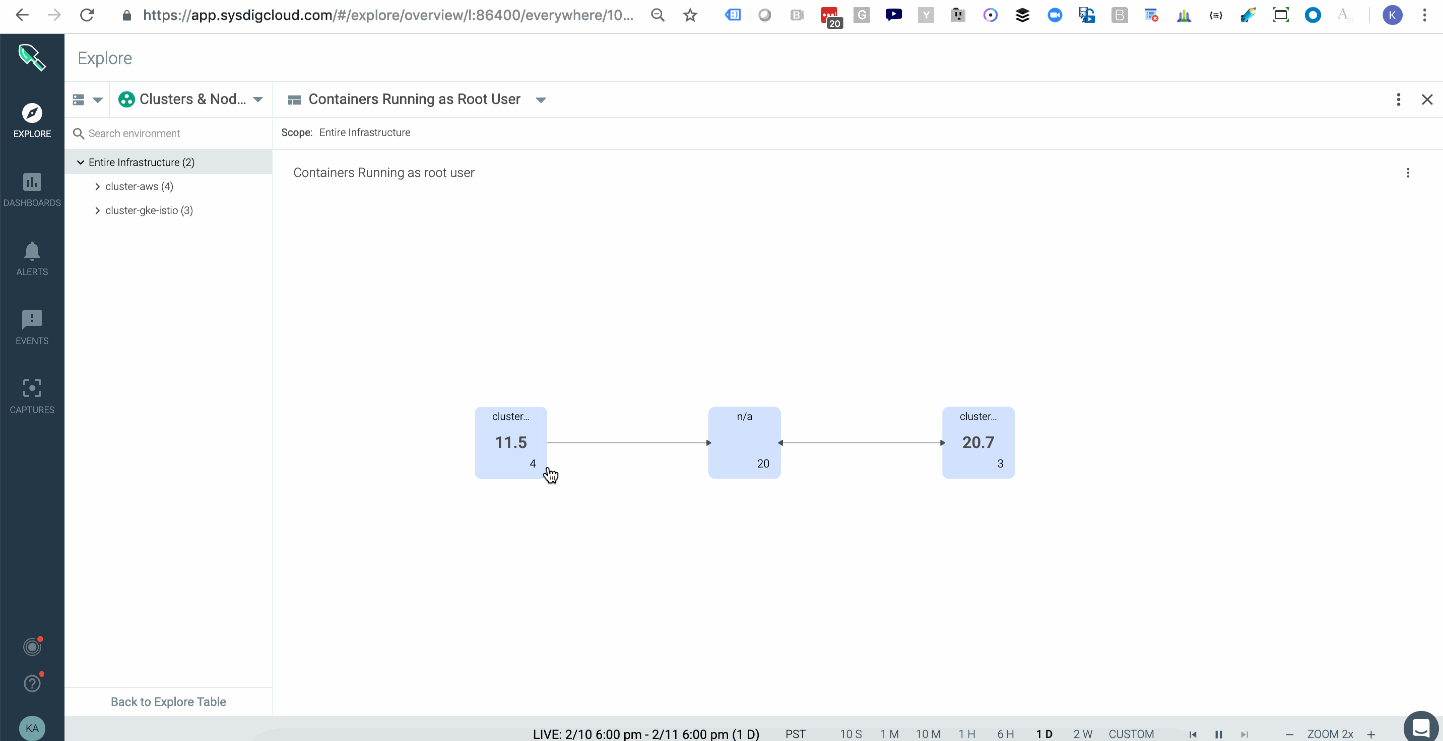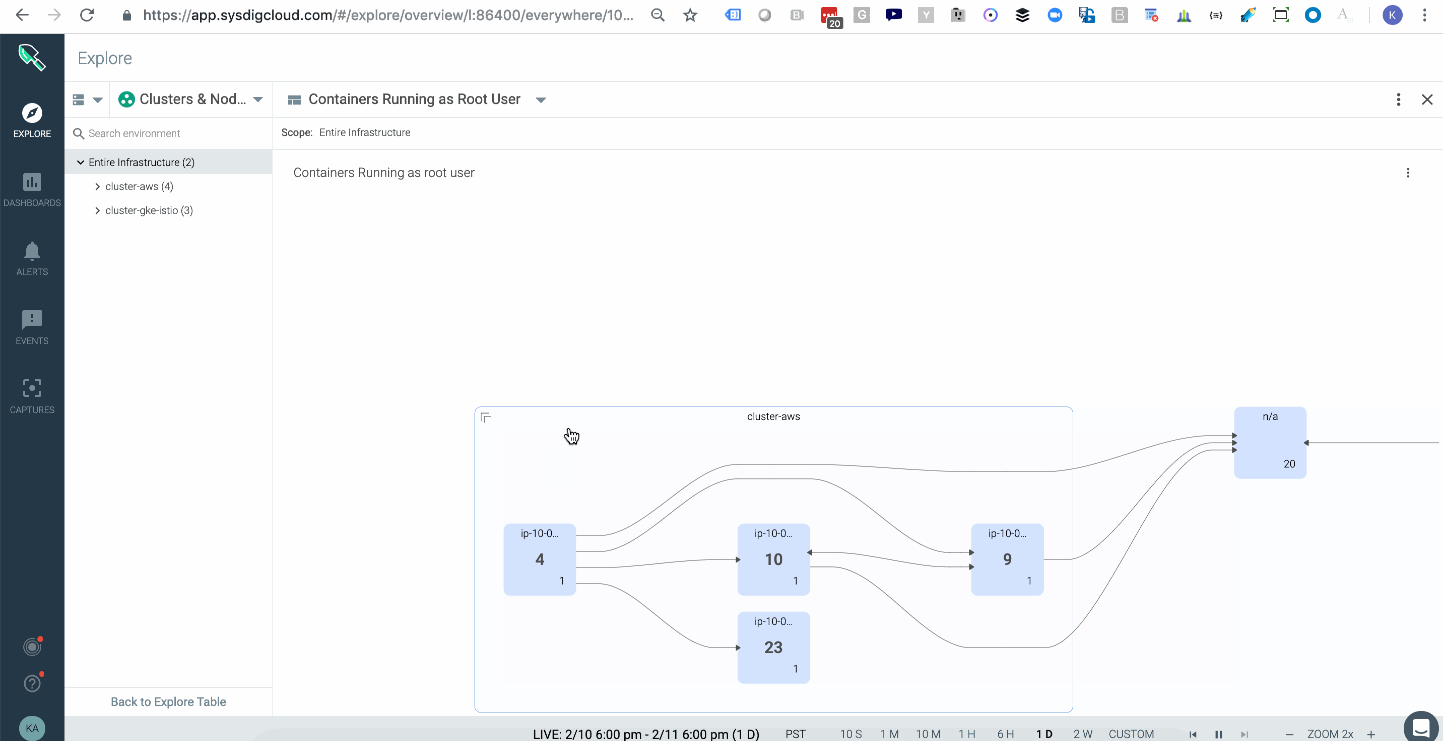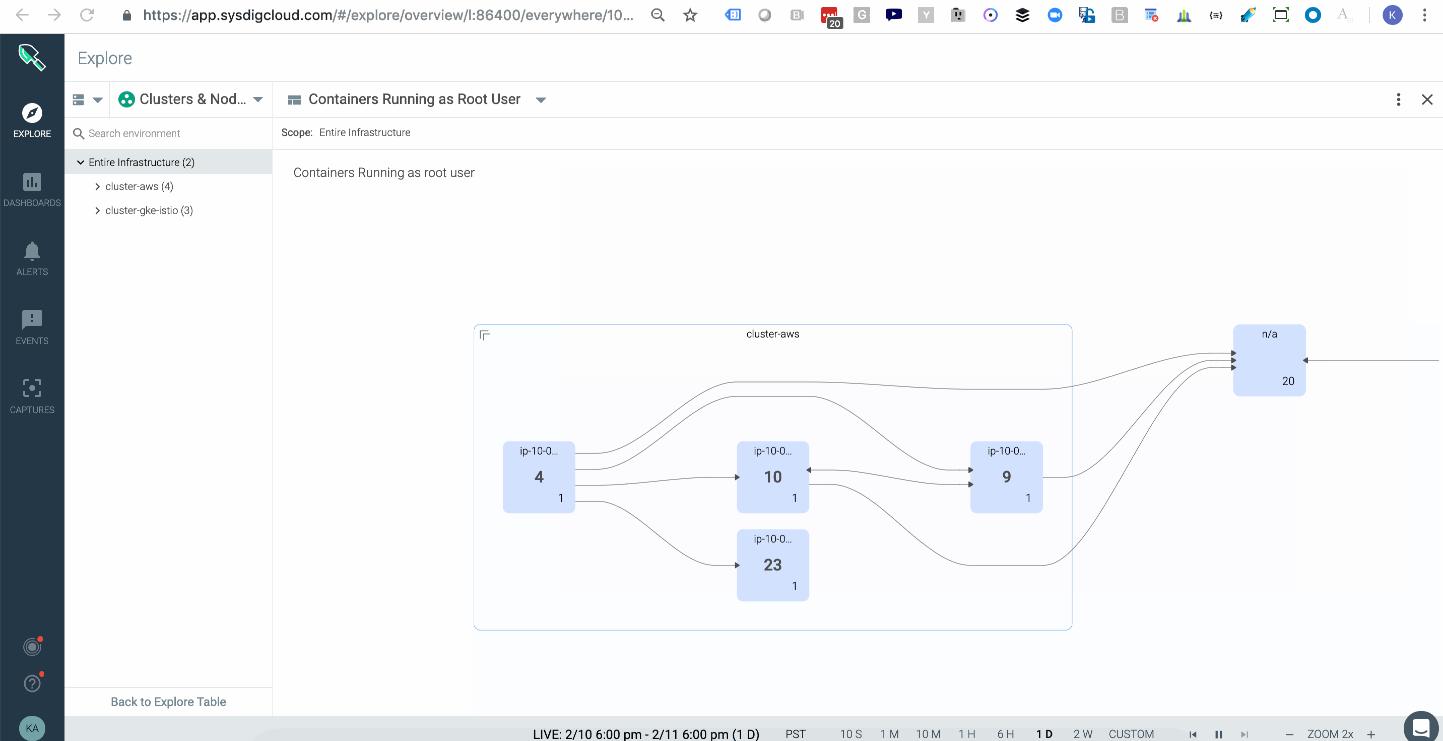
\r\r
CIS metrics like the number of privileged containers can also be viewed as time series metrics so users can quickly visualize their container security and risk posture over time.
\r\r