
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Image vulnerability scanning is a critical first line of defense for security with containers and Kubernetes. In February 2021, Sysdig Secure was recognized by Red Hat as a certified Red Hat security partner. At that time, based on Sysdig's former Vulnerability Scanner, the Sysdig team worked to standardize on Red Hat's published security data with Sysdig Secure.
Today, Sysdig announces the renewal of the Red Hat Vulnerability Scanner certification for the last release of its Vulnerability Scanner Engine. With this certification, achieved through collaboration with the team at Red Hat, Sysdig can not only provide more consistency for container vulnerability scanning results with Red Hat-published images and related packages, but also bring some of its killer features, like Sysdig Risk Spotlight powered by runtime insights. As a result, mutual customers benefit from a higher level of accuracy, transparency, and trust in detecting, prioritizing, and fixing Common Vulnerabilities and Exposures (CVEs) with in-use data from your environments.
Driving consistency for scan results
Modern application development, built on CI/CD pipelines, containers, and open source, moves at a fast pace. There is an inherent security risk as organizations assemble code to save time, instead of writing it from scratch. Finding ways to automate security scanning for images is top of mind for DevOps teams. Image scanning helps to secure the developer build pipeline and automates the analysis of image contents and container configurations to identify and classify known security issues, vulnerabilities, and bad practices.
Red Hat recognized that vulnerability risk assessments for customers were often inconsistent due to different and varying security data sources and practices across partner offerings. We know this challenge! Sysdig Secure taps into vulnerability feeds from 15+ trusted sources, like Red Hat. Each of these CVE feeds is unique, yet valuable to the extent that correlating the contents of an image with a broader set of CVE data ensures a greater level of insight into vulnerable packages, files, etc. Standardization is a great move – Red Hat has the right idea. Consistency helps eliminate misinterpretations and saves time for teams building and running containers.
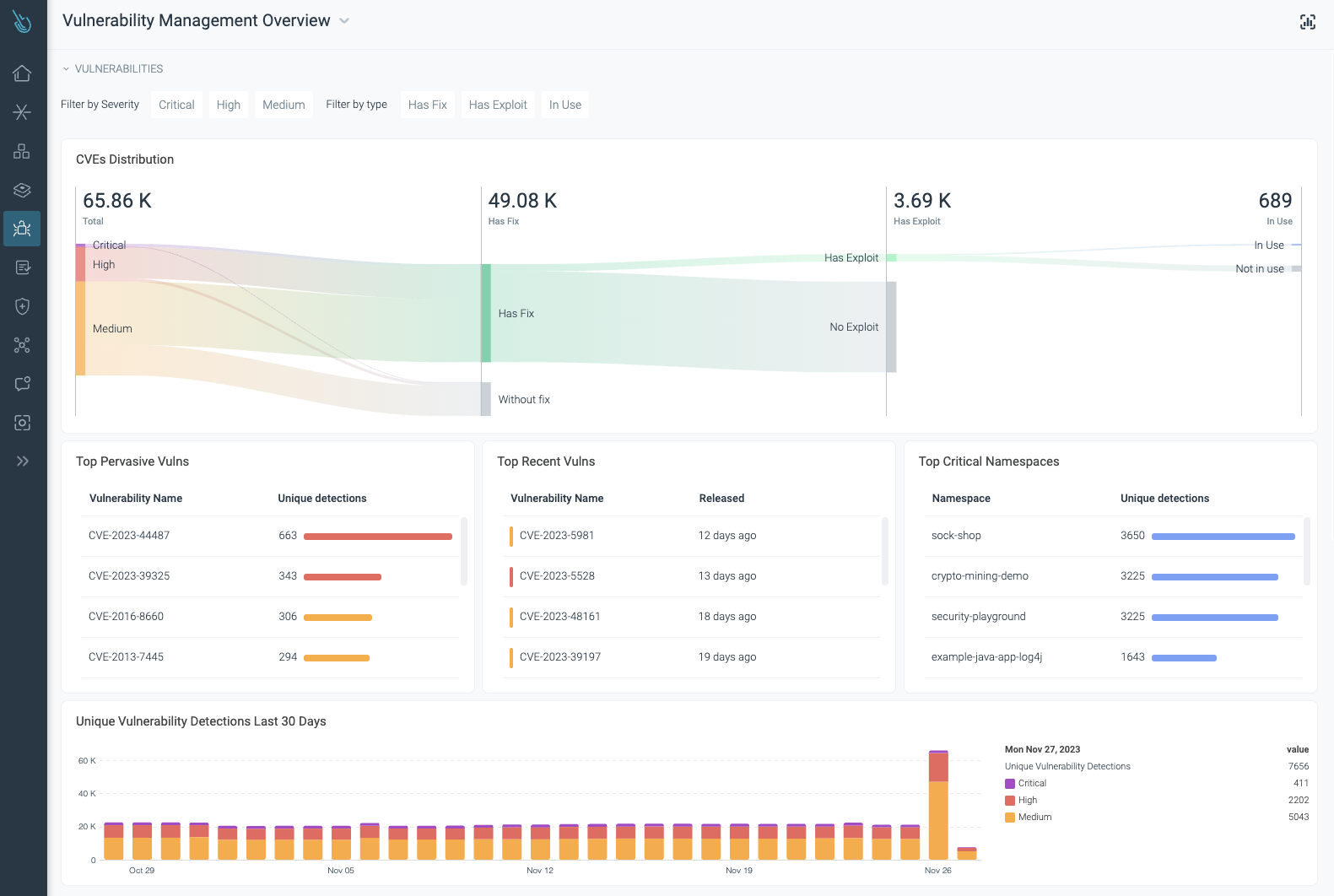
Vulnerability Management overview – Sysdig Secure
How it works
At a high level, here's how this collaboration and standardization works.
- Sysdig Secure consumes the publicly available Red Hat OVAL v2 security data feed.
- With this information, Sysdig image scanning will understand what vulnerabilities affect Red Hat-supported packages and whether a fix (patch) is available.
- Sysdig Vulnerability Scanner Engine scans images throughout the software lifecycle: pipeline, registry, and runtime.
- Sysdig Secure displays the appropriate severity ratings for CVEs in scan results for every stage. For those images deployed at runtime, the in-use packages are also reported. That way, Red Hat users can prioritize and fix the security issues that matter most.
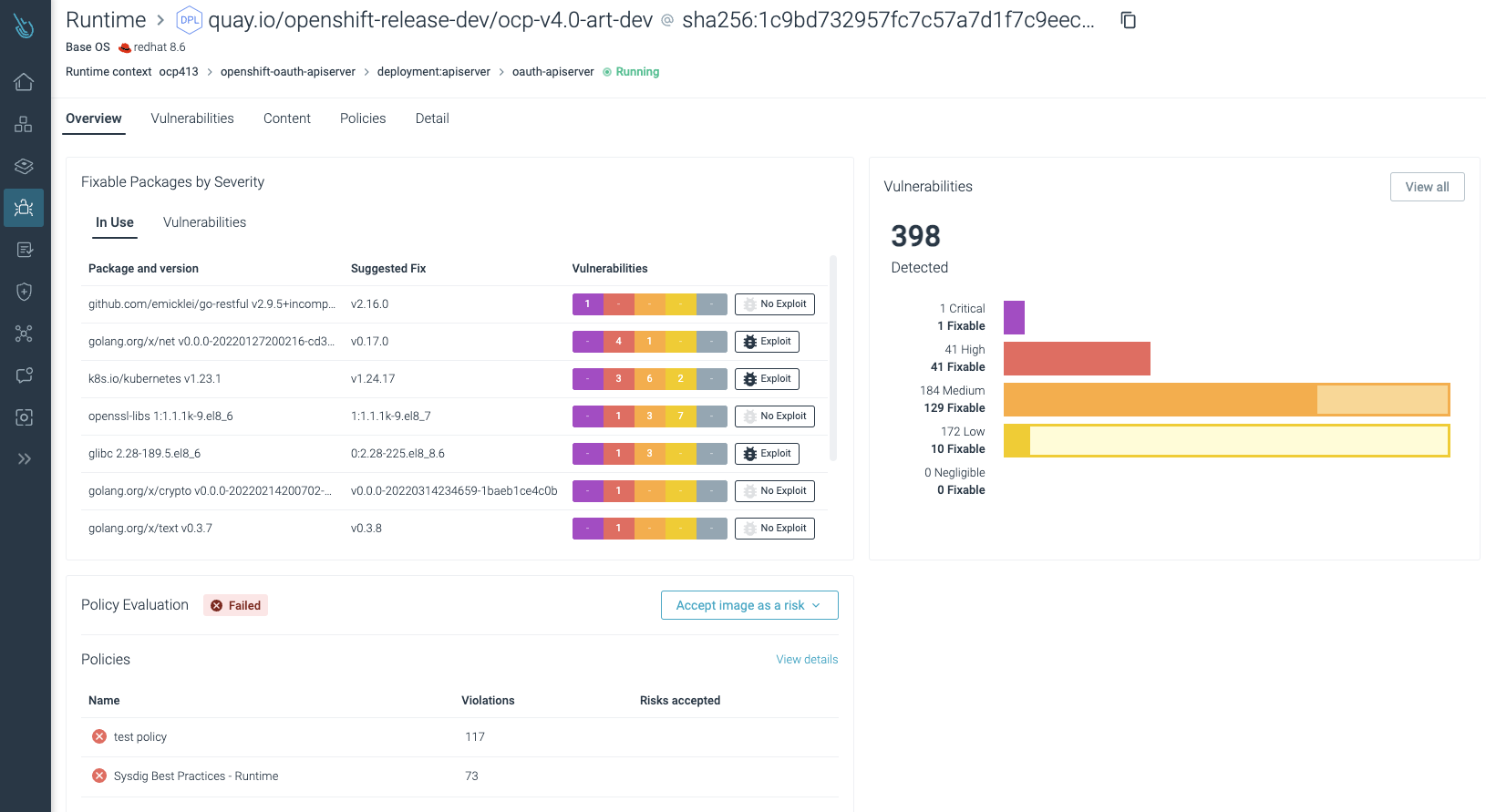
Vulnerability Management with Runtime Insights – Sysdig Secure
Securing build pipelines
Nowadays, it's quite common to see DevOps teams embracing "shift left" security practices. Their goal is to apply a security lens earlier in the development lifecycle. The annual Sysdig 2023 Cloud-Native Security and Usage Report found that 42% of images scanned for the first time happen in the earliest stages of the software lifecycle, while around 50% of the images are scanned for the first time at runtime.
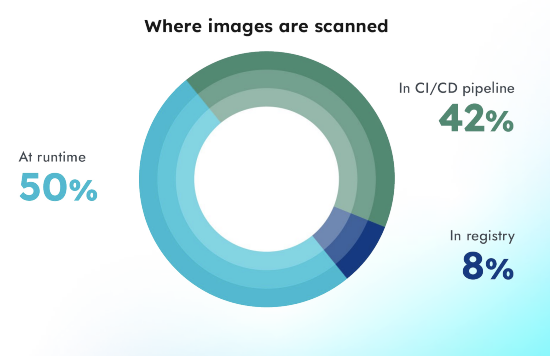
A likely reason that the practice of scanning in runtime is ranked highest is due to the use of third-party software downloaded from vendors. Considered trusted sources, DevOps teams may presume the images are secure and save the time and effort of scanning in the CI/CD pipeline and registry.
Considering security implications for container images earlier in the development lifecycle helps close the door to attackers and reduce the possibility of unexpected and unwanted activity impacting your running containers.
The Power of Runtime Insights
As indicated in the Sysdig 2023 Cloud-Native Security and Usage Report above, a significant amount of images are scanned for the first time at runtime. This indicates that many users may be exposed to potential security threats in the latest software lifecycle stage. The recommendation is clear: the earlier you check for vulnerabilities, the better. Detecting and fixing security issues in the early development stages prevents you from running into serious problems when your workloads are up and running in production.
However, regardless of whether you enforce a shift left approach or not, companies still need to detect vulnerabilities and malicious code at runtime. The Sysdig TRT (Threat Research Team), after a thorough analysis, unveiled that more than 10% of malicious images are completely undetectable because of the advanced techniques attackers use to hide malicious code. That elevates the importance of detecting and responding against threats at cloud speed. The Sysdig Vulnerability Scanner gives users runtime insights to prioritize and fix security issues with runtime context, reducing and focusing DevSecOps team efforts on fixing the most urgent problems first.
If you want to learn more about the latest cloud threat patterns and how to overcome those challenges, check out the Sysdig 2023 Global Cloud Threat Report.
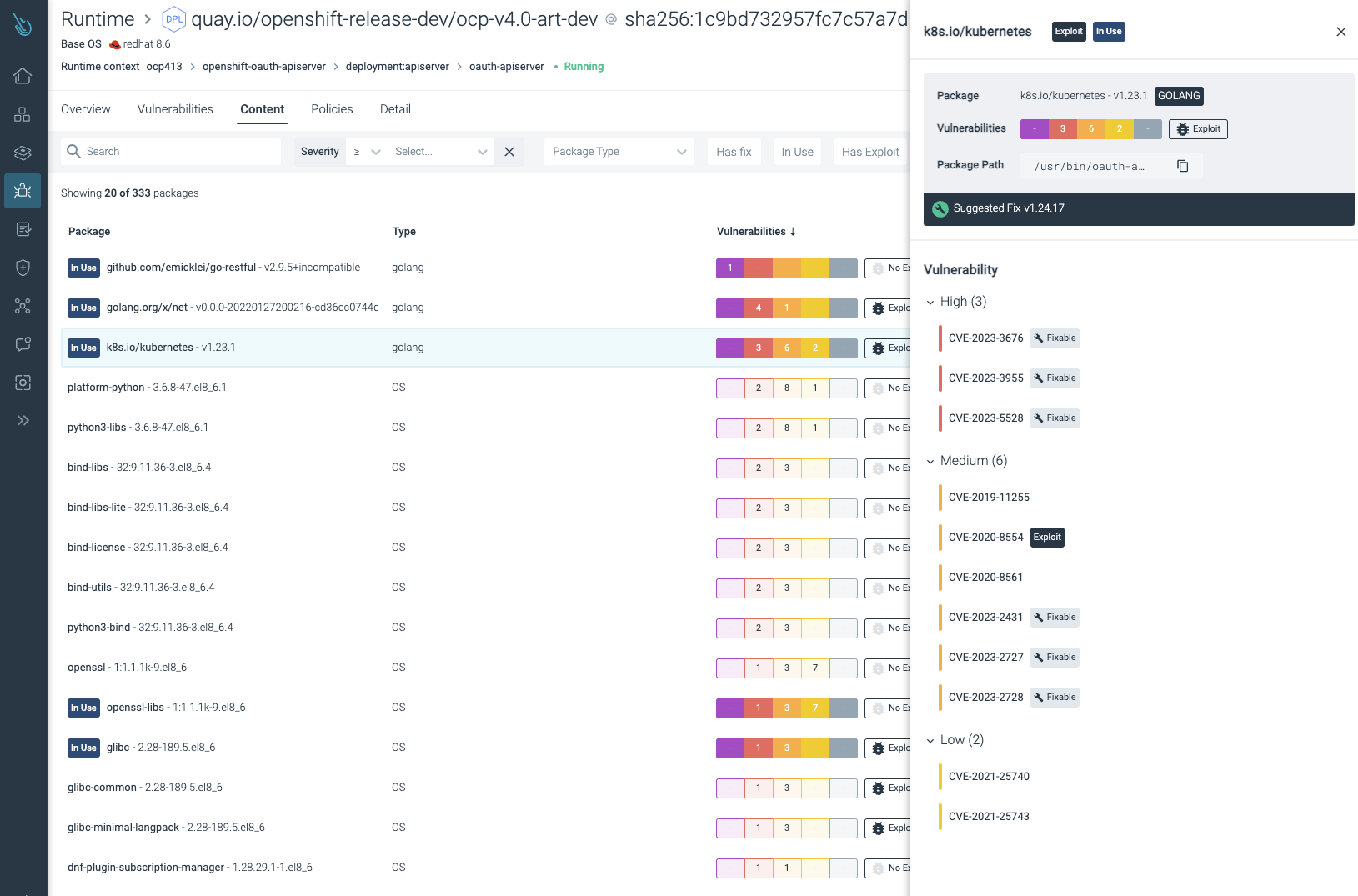
In-use package details for OpenShift images – Sysdig Secure
Conclusion:
By driving consistency and standardization with this new Red Hat Vulnerability Scanner Certification, Red Hat is helping customers who use Red Hat Certified security partner solutions have a more streamlined experience for assessing vulnerability risks of Red Hat products and packages. Aligning Sysdig Secure with Red Hat's strategy and standard means Sysdig customers can gain improved clarity and accuracy for image scanning with CI/CD pipelines and registries.
If you want to learn more about how Sysdig helps secure Red Hat OpenShift and containers, visit our Red Hat partnership ecosystem page.


