Secure and Accelerate Innovation on Red Hat OpenShift
Attackers move fast. Sysdig helps you move faster with the power of runtime insights.
Security and Visibility for Red Hat OpenShift
In the cloud, every second counts. From prevention to defense, Sysdig prioritizes the risks that matter most and secures workloads, OpenShift, and cloud services in real-time.
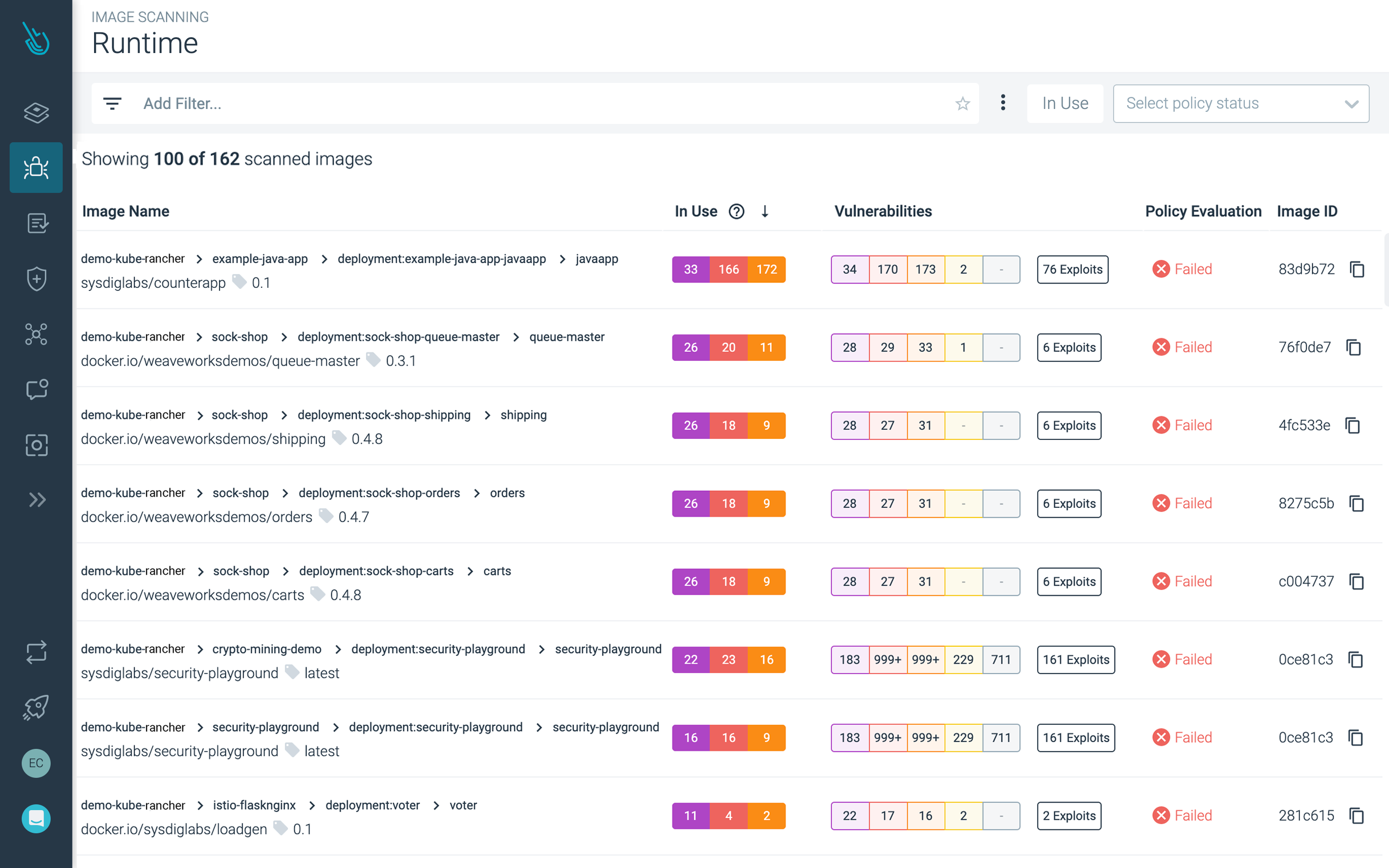
Find and prioritize vulnerabilities
Automate image scanning in CI/CD pipelines and registries. Prioritize vulnerabilities based on runtime context and risk.
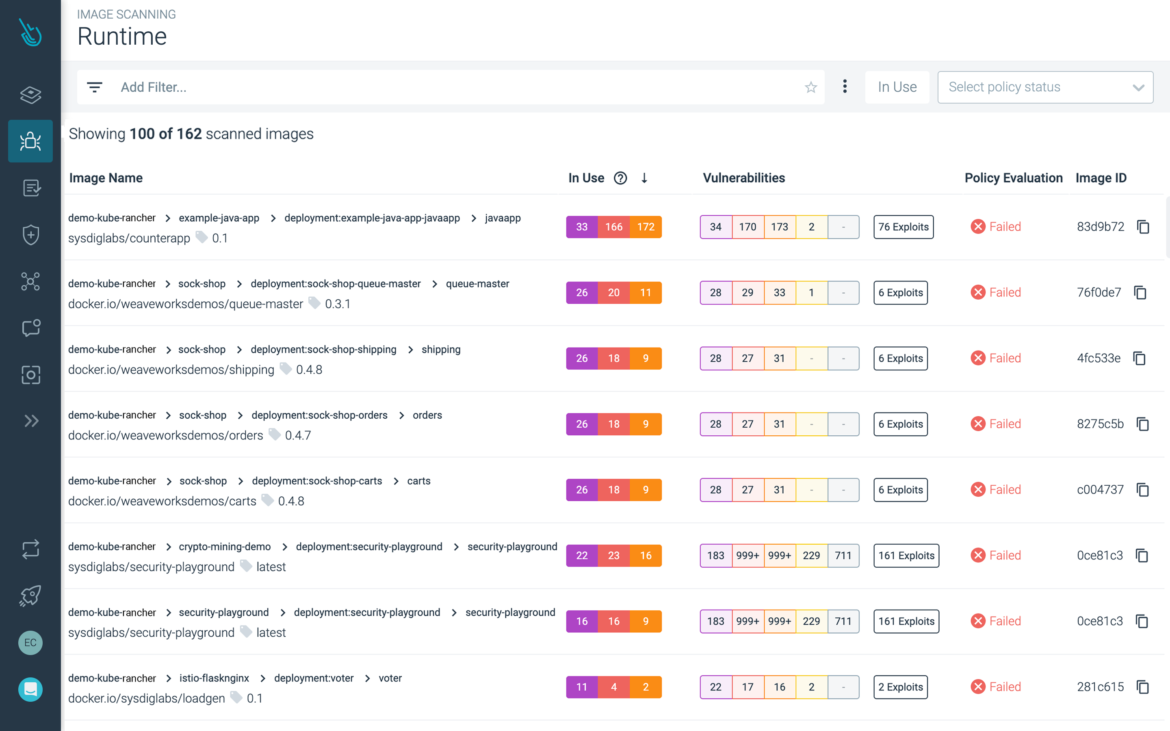
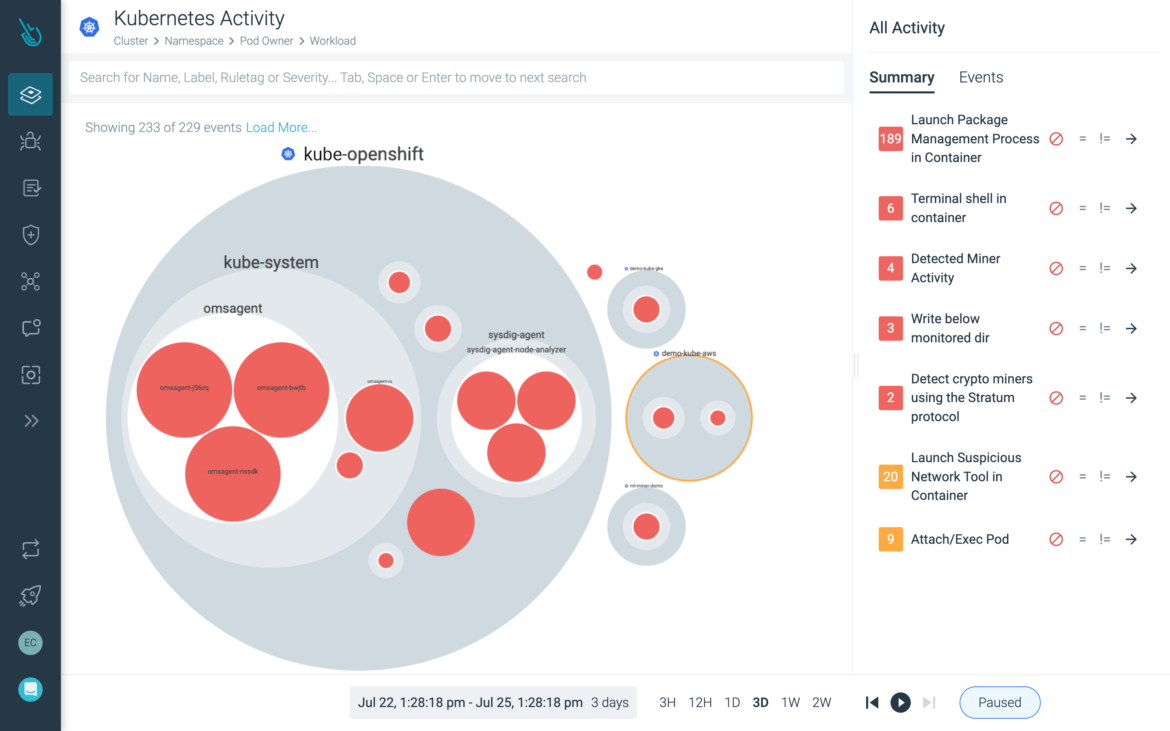
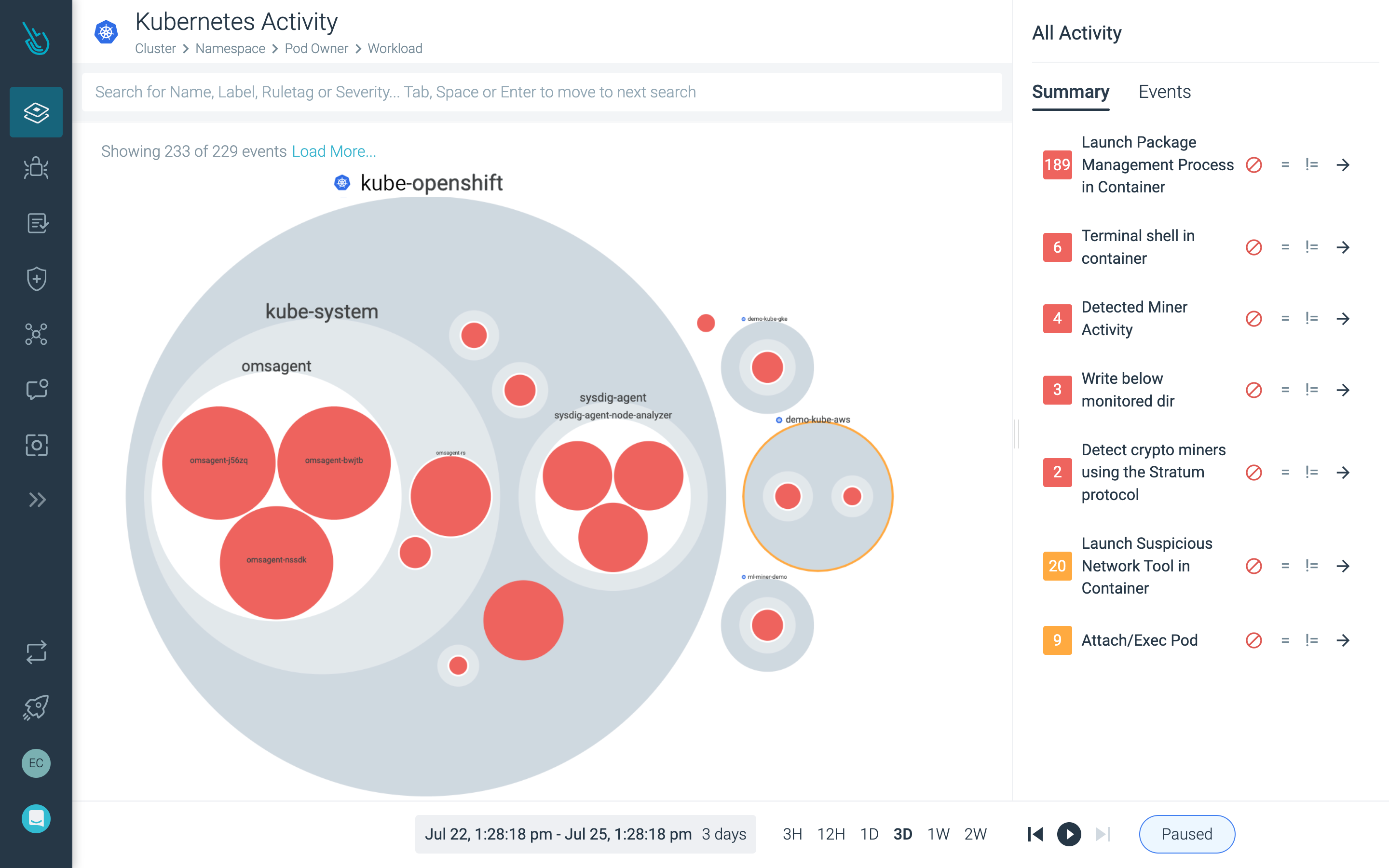
Detect and respond to runtime threats
Identify suspicious activity across your OpenShift infrastructure and workloads with threat detection based on open source Falco.
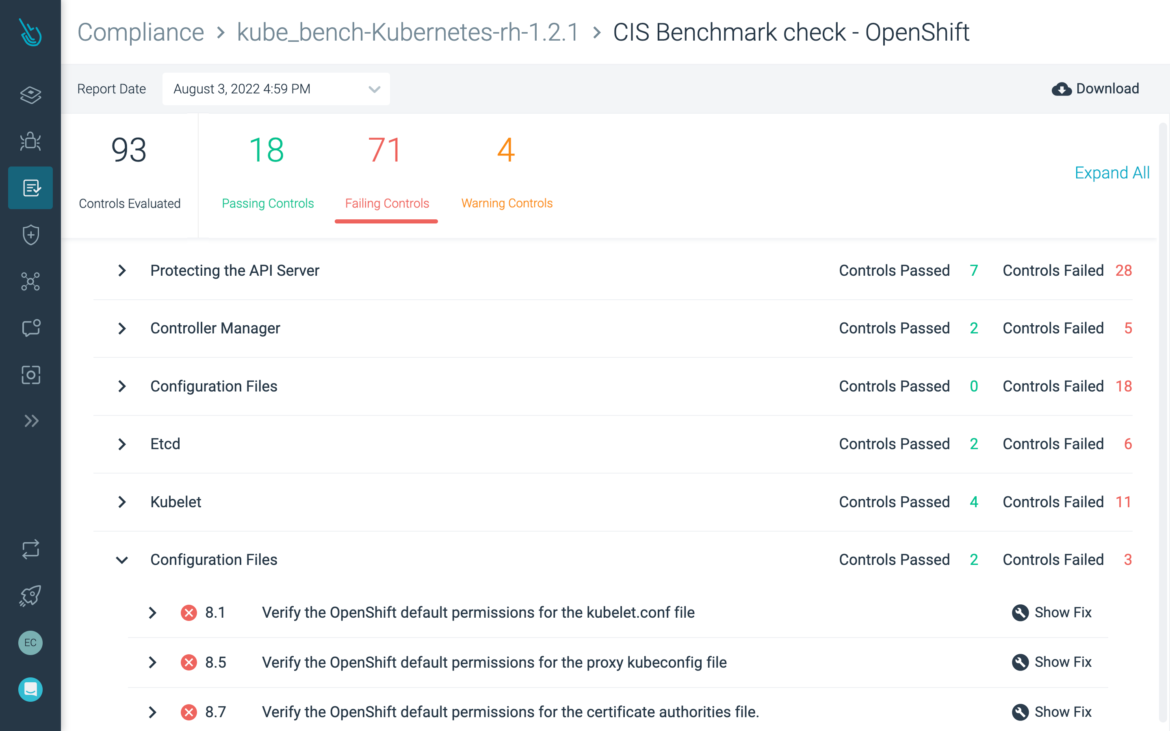
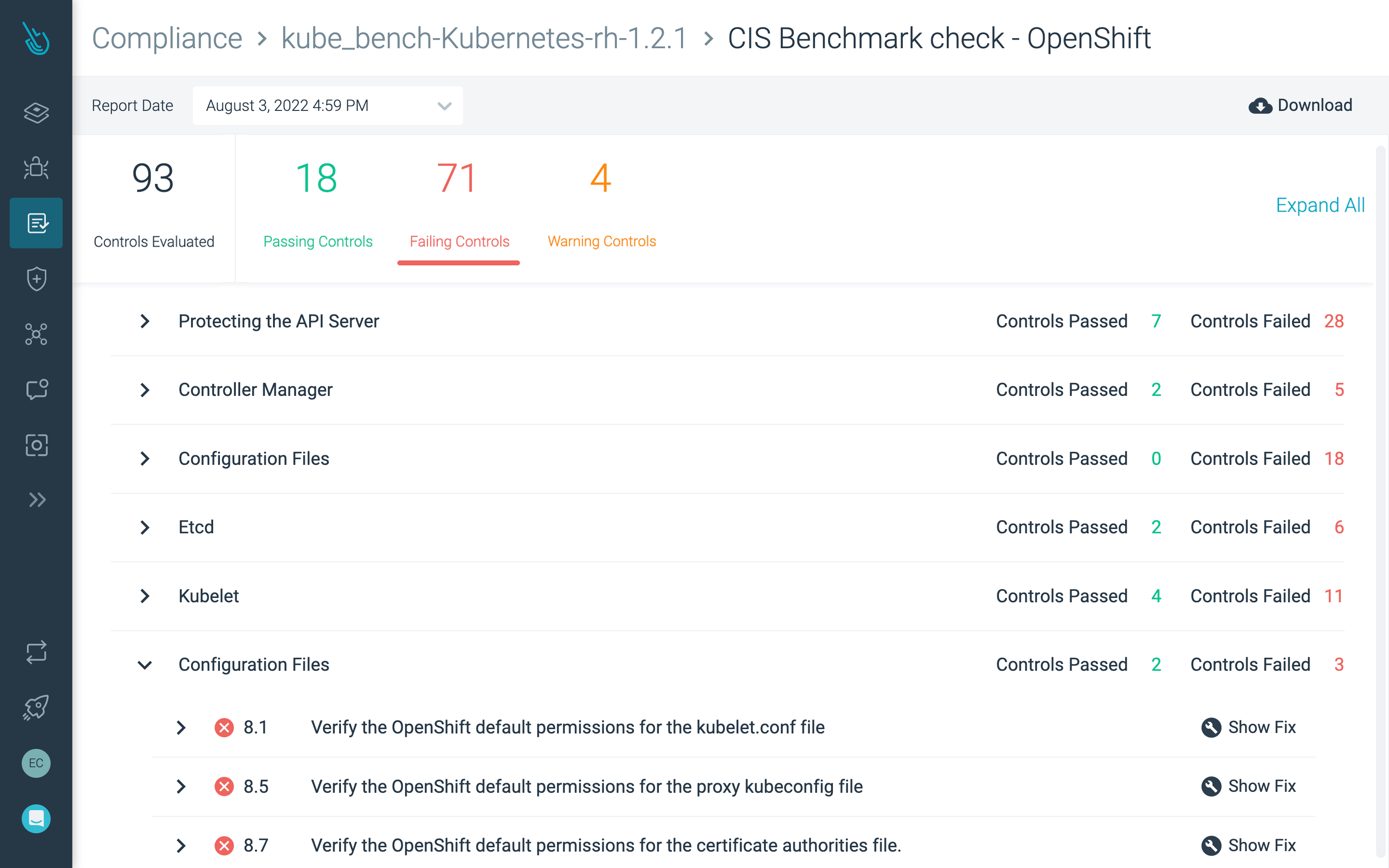
Continuously validate compliance
Save time with out-of-the-box policies for PCI, NIST, and SOC2. Quickly identify misconfigurations and compliance violations.
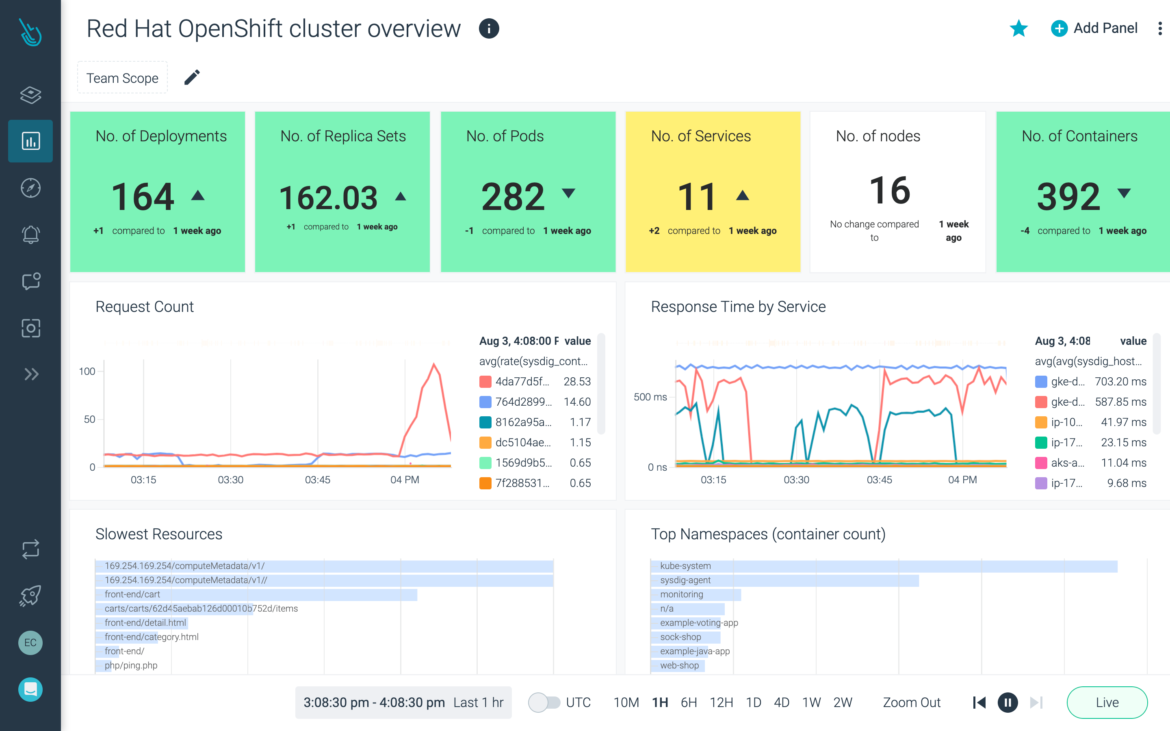
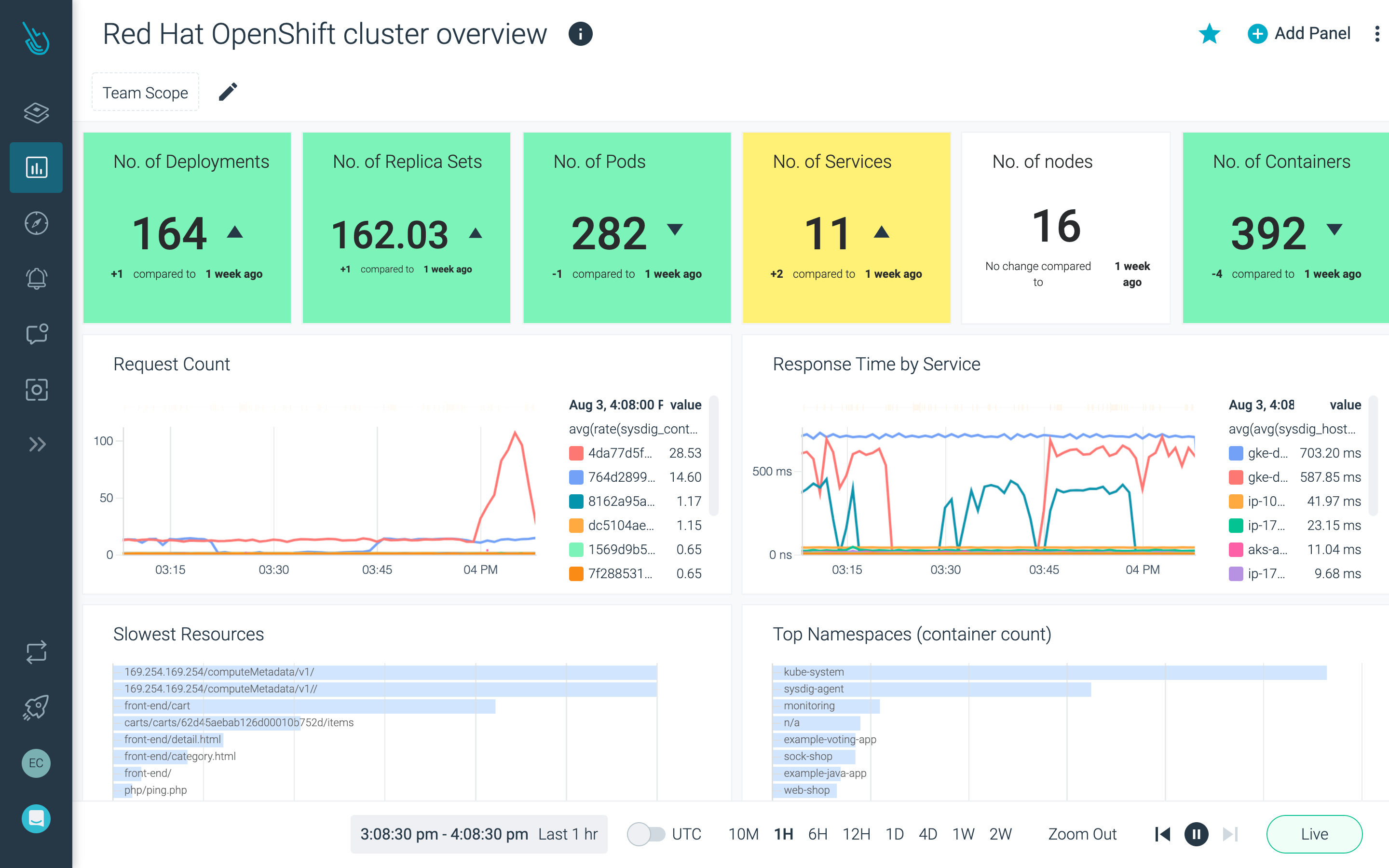
Monitor and troubleshoot
Scale monitoring with managed, enterprise-grade Prometheus and view performance metrics enriched with Kubernetes and cloud context.
Leading Companies Secure OpenShift with Sysdig





Use Cases for Red Hat OpenShift
Red Hat Integrations
Take advantage of our integrations with Red Hat solutions for a single view of risk from source to run with no blind spots, no guesswork, and no black boxes.
Click on a logo to view the integration.Featured Resources
Take the Next Step!
See how you can secure every second in the cloud.




