
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

In our first blog post, “Sysdig Secure-Google Chronicle integration – Why, what, and how“, we introduced the idea of connecting both platforms, highlighting their complementary strengths and providing a high-level overview. Now, we’re taking it a step further—moving beyond theory to focus on practical, real-world applications. In this post, we’ll dive into specific security challenges SOC teams face in the cloud and demonstrate how Sysdig and Google SecOps work together to address them with concrete use cases and actionable insights.
SOC teams and the cloud don’t always get along
After more than a decade of pioneering cybersecurity in the cloud-native world, we’ve consistently observed a critical gap: Production-grade cloud infrastructure operated by SRE and DevOps teams often lacks the necessary coverage from security operations centers (SOCs) and cybersecurity professionals. This disconnect can create blind spots, delay incident response, and leave critical workloads exposed in fast-moving, dynamic cloud environments.
Just to mention a couple of quotes:
- “SOCs often have limited visibility into their cloud environments, making it challenging to detect and respond to threats. Existing security toolsets may not have been chosen with cloud in mind, leading to visibility gaps.“
Future of the SOC (Deloitte 2024) - “Using the public cloud disrupts traditional cybersecurity models that many companies have built over years. Cybersecurity technologies for on-premises IT systems may not work as intended unless reconfigured for the public cloud“.
Making a secure transition to the public cloud (McKinsey 2018)
Security teams often struggle to keep up with the complexity of modern cloud environments. On one hand, SOC tools are still rooted in traditional enterprise IT—built to monitor employee devices and office networks—far removed from today’s reality where “every company is a software company” (Satya Nadella, Microsoft). On the other side, the fast-paced, ephemeral nature of cloud services makes it difficult to maintain visibility and control, leaving teams blind to their true attack surface.
This is where Sysdig and Google SecOps step in, empowering security teams to regain control with confidence.
The shifting threat landscape in the cloud
The ‘wall of confusion,’ a concept popularized by the founders of the DevOps movement, is equally relevant in cybersecurity: cloud teams prioritize agility while security teams focus on protection. These goals, though seemingly at odds, can—and must—be aligned.
There are some key questions that both teams need to understand.
1. What does my real cloud inventory look like?
Understand exactly what assets, services, and dependencies are running across your cloud infrastructure.
2. What are my top risks and who is responsible for fixing them?
Identify critical vulnerabilities and misconfigurations considering their context in the cloud – is the asset publicly exposed, are the vulnerabilities loaded in memory – and ensure the right teams take action.
3. What is happening in my environment and why?
Gain deep visibility into cloud activity to detect, investigate, and understand suspicious behavior in context.
4. How do we respond to cloud threats?
Build a response strategy that’s tailored to the speed, scale, and complexity of cloud-native workloads.
Sysdig simplifies cloud security: Making the complex digestible
The Sysdig platform turns overwhelming into actionable by consolidating real time visibility, risk, and compliance into a single, intuitive interface. As a cloud-native expert, Sysdig interprets what traditional EDR tools can’t understand.
In line with modern cloud requirements, a consolidated Cloud-native application protection platform (CNAPP) must cover several key points along the cloud application lifecycle:
- Track Infrastructure as Code (IaC) from the source (Git repositories).
- “Shift left” with continuous container image scanning at build time, at rest, and – a key strength for Sysdig – at runtime.
- Identify and report on posture risks, enforce compliance, and provide actionable recommendations (including identity analysis and attack path).
- “Shield right” on your cloud services, cloud-native workloads, and serverless at scale. Correlate and consolidate findings to prevent alert fatigue.
- Move at the speed of the cloud, surfacing risks contextualized with surrounding events using runtime insights to prioritize what matters in real time.
How Google SecOps redefines SIEM and SOAR
It is well known that traditional SIEM (Security information and event management) and SOAR (Security orchestration, automation, and response) solutions have struggled to keep up, especially during the “era of expansion” of the public clouds. Google SecOps is a game-changing platform that combines the power of Google Chronicle (a next-gen SIEM) and Siemplify (a leading SOAR tool) to redefine how organizations detect, investigate, and respond to threats.
A unified approach
- Unmatched scalability: Built on Google’s global infrastructure, Google SecOps SIEM ingests and analyzes petabytes of data in real time—without breaking a sweat. Its lightning-fast search capabilities allow security teams to query years of data in seconds, turning what was once a bottleneck into a strength.
- AI-driven threat detection: It leverages Google’s expertise in machine learning to surface high-fidelity threats, reducing noise and helping teams focus on what truly matters. It’s not just about detecting threats faster; it’s about detecting the right threats.
- Seamless automation with SOAR: Enables security teams to automate repetitive tasks, orchestrate complex workflows, and respond to incidents at machine speed. By integrating directly with Google SecOps SIEM, it eliminates the gaps between detection and response.
Better together: SOC-ready cloud environments
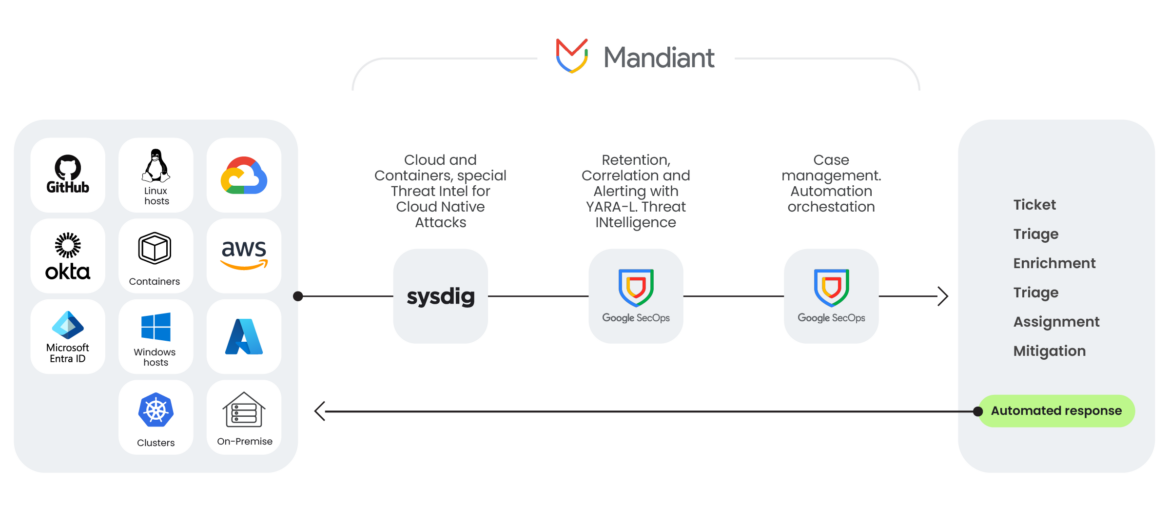
Securing the cloud is no longer about collecting more data—it’s about making the right data work harder. By integrating Sysdig Secure with Google SecOps, the SOC has the context and coverage needed to detect, investigate, and respond across multi-cloud environments with confidence.
Here’s how they work better together:
- Expanding cloud visibility
Sysdig delivers deep runtime insights from Kubernetes, containers, and cloud services. Pushing this context into Google SecOps unlocks unlimited correlation, allowing you to connect cloud-native events with broader security signals—instantly.
- Reducing costs without losing context
Stop sending noisy, raw telemetry. Sysdig helps you optimize the data you forward to Google SecOps, keeping only high-fidelity detections. Less data in transit means lower costs, without sacrificing coverage.
- Advanced threat detection with YARA-L
Detect complex, evasive threats in real-time by combining SecOps YARA-L rules control with Sysdig’s high resolution and depth.
- Surfacing cloud entities
Sysdig findings and Indicators of Compromise feed into Google SecOps, giving analysts a single place to see the full story.
- Extending retention and threat context
Google SecOps combines the best of a SIEM and a Data Lake to get the most out of all the critical information beyond the Sysdig default retention windows.
- Optimizing response operations
Escalate high-confidence results into Google SecOps SOAR for centralized triage and response.
The Sysdig + Google SecOps integration delivers clear, actionable insights – turning complex cloud events into something teams can easily understand and respond to.
Solving real challenges
Sysdig insights in SecOps SIEM
The most fundamental use case, which we briefly covered in our previous post, involves sending Sysdig detections to Google SecOps. This allows security events to be forwarded, normalized to a Unified Data Model (UDM), and then analyzed (through immediate alerts and IoCs) and retained (in long-term storage).
To set up the integration from scratch, we recommend referring to our official documentation at this link.
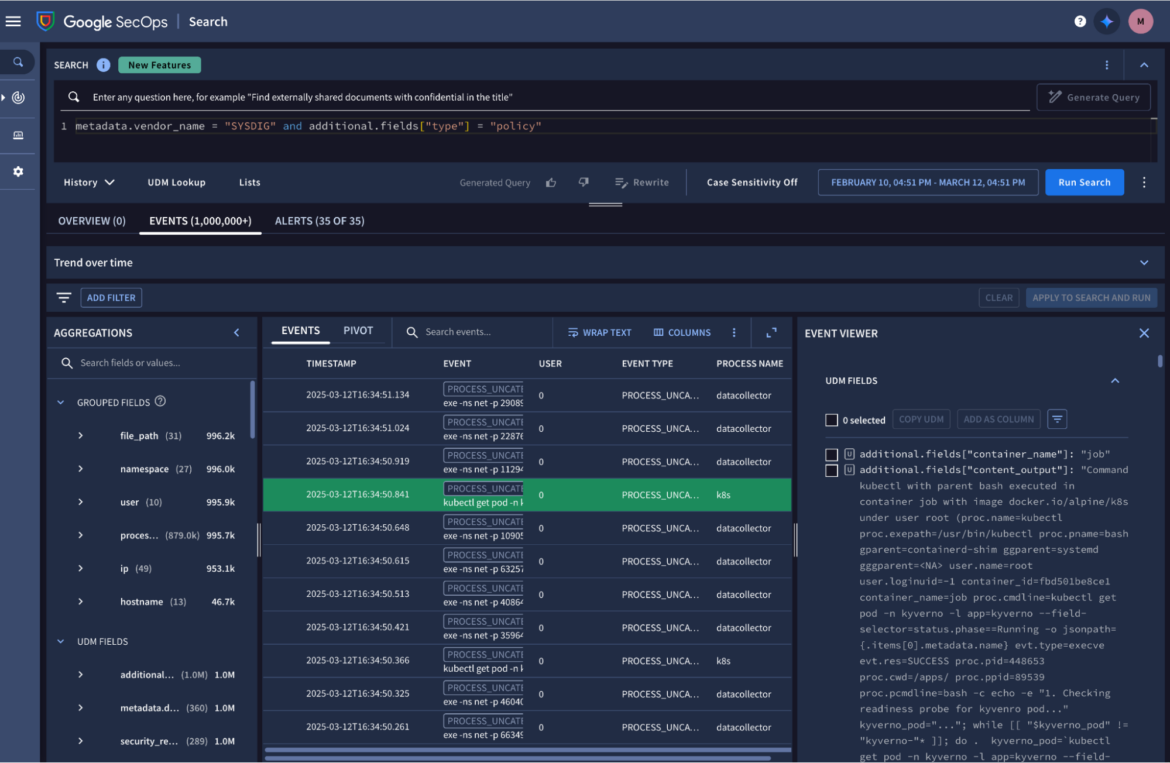
Long-term retention and UDM queries
Given that Sysdig detections are now normalized in UDM and stored in SecOps data lake, security teams can correlate real-time runtime threats with any other IT resource like a Web Application Firewall (WAF) or a Cloud Access Security Broker (CASB), using months or even years of security telemetry. This enables proactive threat hunting, retrospective analysis of zero-day exploits, and enriched investigations that go beyond ephemeral cloud workloads.
For example, a runtime detection of anomalous events in the cloud might initially appear isolated. However, when correlated with historical IAM activity and network flows stored in SecOps, it can reveal a broader attack narrative to SOC teams.
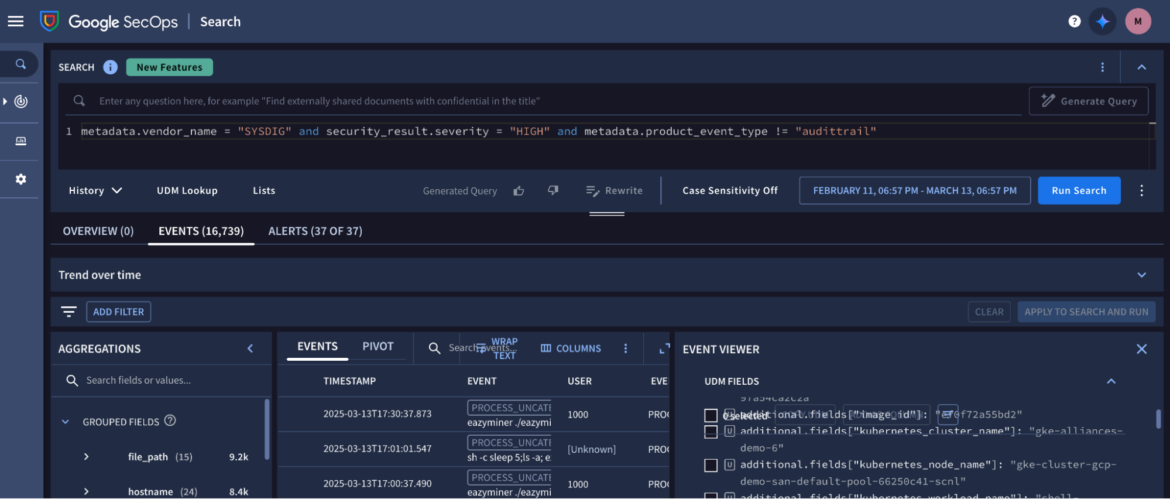
Here are just a few examples of useful SecOps queries for analyzing Sysdig data:
Get a list of high-severity events (all of them):
metadata.vendor_name = "SYSDIG" and security_result.severity = "HIGH"Inspect events generated from a given Kubernetes pod name:
metadata.vendor_name = "SYSDIG" AND metadata.event_type = "GENERIC_EVENT" AND additional.fields["pod_name"] != "shop-frontend"Retrieve a list of GCP audit logs triggered from the same user IP:
metadata.vendor_name = "SYSDIG" AND metadata.event_type = "GENERIC_EVENT" AND security_result.description = "gcp_auditlogs" AND extracted.fields["labels.source.ip"] = "257.11.22.33"Collect any finding related to a MITRE ATT&CK technique:
metadata.vendor_name = "SYSDIG" AND metadata.event_type = "GENERIC_EVENT" AND ANY extracted.fields["content.ruleTags"] = "MITRE_T1082_system_information_discovery"Or use this slightly modified version of the previous query to cherrypick multi-cloud findings, involving AWS and GCP, while discarding other sources, such as Azure:
metadata.vendor_name = "SYSDIG" AND metadata.event_type = "GENERIC_EVENT" AND (security_result.description = "awscloudtrail" OR security_result.description = "gcp_auditlog") AND ANY extracted.fields["content.ruleTags"] = "MITRE_T1580_cloud_infrastructure_discovery"Get a list of the Sysdig platform audit logs:
metadata.vendor_name = "SYSDIG" and metadata.product_event_type != "audittrail"Cloud dashboards made easy
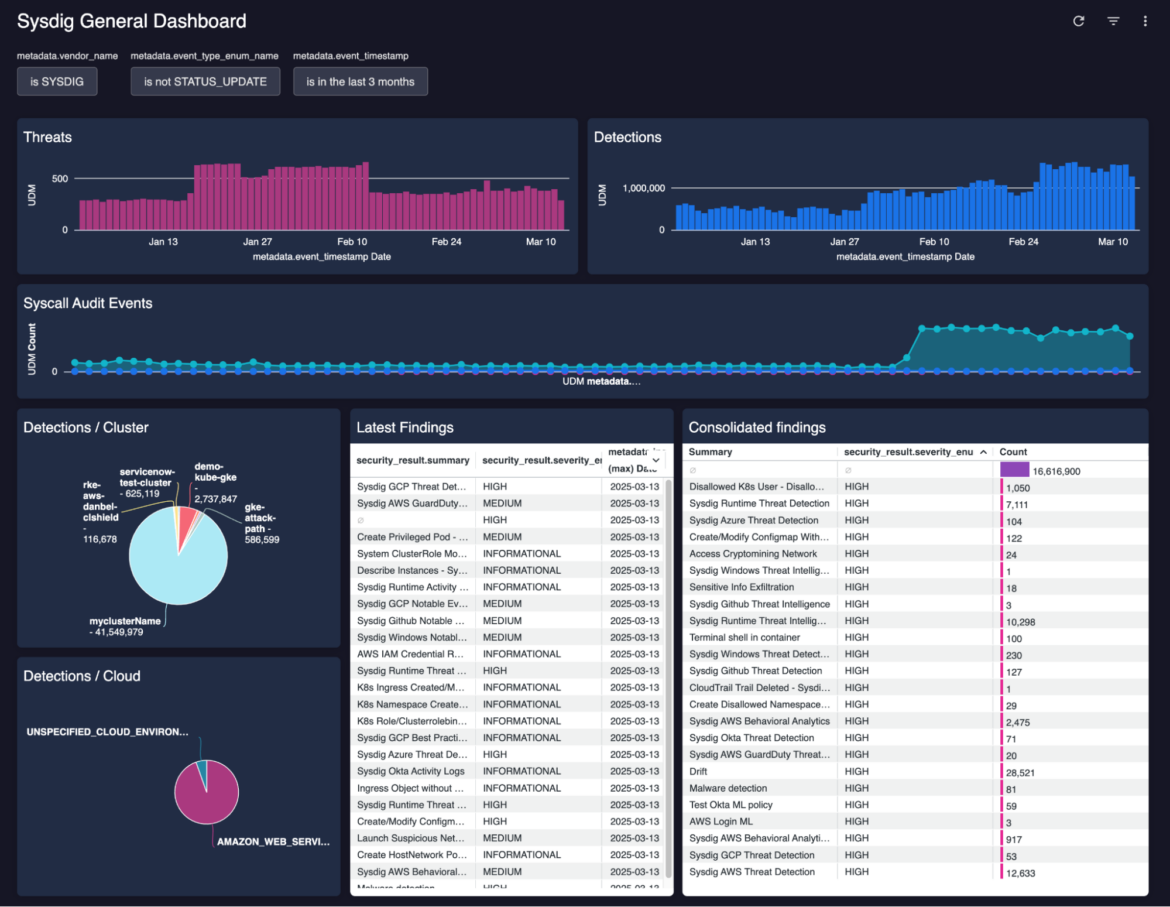
The following dashboard has been created by combining some simple queries and adjusting visualization options (please note that it is connected to a deliberately noisy test environment). It is a great example of how Sysdig makes the cloud digestible for the SOC.
In this dashboard you’re able to view:
- The number of events and threats in the past days
- Syscall-related audit events (trend)
- Number of detections by cluster
- Number of detections by cloud vendor (or datacenter)
- Consolidated findings and latest findings
Advanced threat detection
When it comes to operationalizing cloud alerts, SecOps implementation of YARA-L for custom detections is incredibly powerful.
As an example, we created a basic rule simulating a scenario where multiple events could indicate lateral movement in the cloud. SecOps will trigger an alert when a specific combination of events occurs within a defined time window, enabling SOC teams to detect and respond to potential threats more effectively.
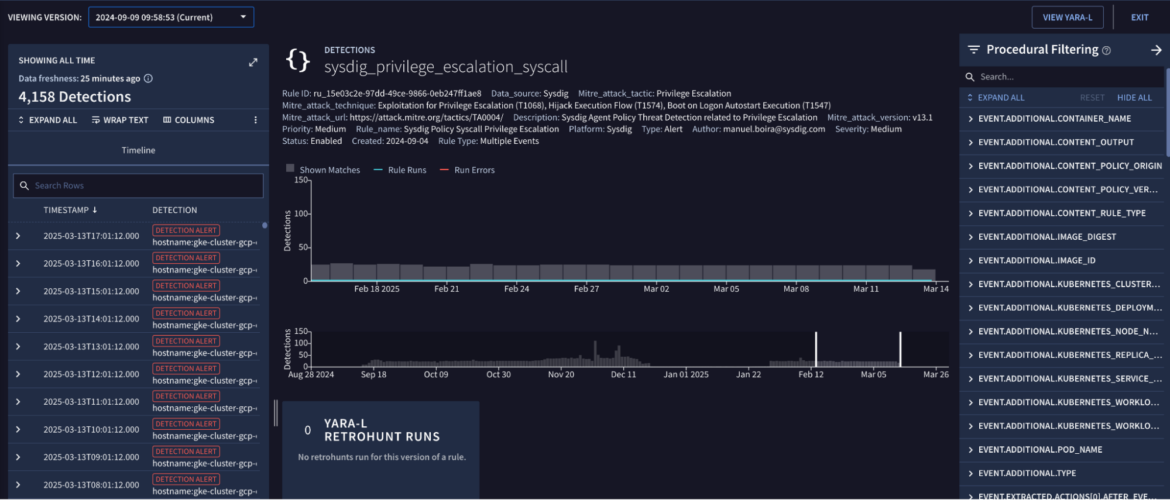
Please note that the following YARA-L rule is just a simple example created for this experiment. The real value is for our customers to build their own detection scenarios.
rule sysdig_privilege_escalation_syscall{
meta:
author = "manuel.boira@sysdigv5.wpenginepowered.com"
description = "Sysdig Agent Policy Threat Detection related to Privilege Escalation"
rule_name = "Sysdig Policy Syscall Privilege Escalation"
mitre_attack_tactic = "Privilege Escalation"
mitre_attack_technique = "Exploitation for Privilege Escalation (T1068), Hijack Execution Flow (T1574), Boot on Logon Autostart Execution (T1547)"
mitre_attack_url = "https://attack.mitre.org/tactics/TA0004/"
mitre_attack_version = "v13.1"
type = "Alert"
data_source = "Sysdig"
platform = "Sysdig"
severity = "Medium"
priority = "Medium"
events:
$sysdig.metadata.vendor_name = "SYSDIG"
$sysdig.metadata.product_name = "SYSDIG"
$sysdig.metadata.product_event_type = "policy"
$sysdig.security_result.rule_name = /Detect malicious cmdlines|Unexpected Connection from|Possible Backdoor using BPF|Suspicious network tool downloaded and launched in container|Packet socket created in container|Read sensitive file untrusted|Shared Libraries Reconnaissance Activity/
$sysdig.principal.hostname = $hostname
match:
$hostname over 3m
outcome:
$mitre_attack_tactic = "Privilege Escalation"
$risk_score = max(65)
$event_count = count_distinct($sysdig.metadata.id)
$principal_ip = array_distinct($sysdig.principal.ip)
$principal_user_display_name = array_distinct($sysdig.principal.user.user_display_name)
$security_result_summary = array_distinct($sysdig.security_result.summary)
$security_result_description = array_distinct($sysdig.security_result.description)
$security_result_severity = array_distinct($sysdig.security_result.severity)
$security_result_severity_details = array_distinct($sysdig.security_result.severity_details)
$metadata_product_event_type = array_distinct($sysdig.metadata.product_event_type)
$kubernetes_cluster_name = array_distinct($sysdig.additional.fields["kubernetes_cluster_name"])
$kubernetes_workload_name = array_distinct($sysdig.additional.fields["kubernetes_workload_name"])
$kubernetes_namespace_name = array_distinct($sysdig.metadata.base_labels.namespaces)
condition:
$sysdig and $event_count >= 1 and $event_count <= 50SecOps SOAR playbooks for automated response
Once Sysdig events start generating alerts in SecOps SIEM, leveraging them within the SecOps SOAR platform becomes seamless.
We’ve built a sample playbook that demonstrates this integration in action. Here’s a high-level summary of its workflow:
- Capture findings categorized as “Sysdig privilege escalation”, aligning with the custom YARA-L rule created in the previous example.
- Determine the event source:
• Does it relate to syscalls, Windows, or cloud audit logs?
• Did it originate from within a cluster? - Create an external Jira ticket to alert teams X and Y (this step highlights integration capabilities).
- Enrich the case with contextual information about the threat and the affected resources – including location, security posture, and top risks.
- Provide incident responders with response options:
• Scale the node pool to zero for immediate mitigation.
• Restore the node pool if necessary.
This playbook showcases how Sysdig and SecOps work together to streamline cloud security operations, providing actionable intelligence and automated response capabilities.
Conclusion: Bridging the gap between SOC and cloud security
Integrating Sysdig with Google SecOps gives SOC teams the context and automation they need to secure cloud-native environments effectively. The deep runtime visibility with scalable SIEM and SOAR capabilities helps teams cut through the noise, detect real threats, and respond with confidence. With this integration, cloud security becomes actionable, efficient, and built for the speed – and complexity – of modern attacks in the cloud.


