Cloud attacks are different
Organizations are transitioning into the cloud at warp speed, but cloud security tooling and training is lagging behind for the already stretched security teams. In an effort to bridge the gap from endpoint to cloud, teams are sometimes repurposing their traditional endpoint detection and response (EDR) and extended detection and response (“XDR) on their servers in a “good enough” approach.
Server or host security has historically been an ownership gray zone, where the protection approach varies based on organizational preferences. Security teams have typically focused protection on the host itself, while DevSecOps teams have prioritized protection of their crown jewels such as containers, Kubernetes, VMs, and workloads. Both approaches are half measures that don’t provide adequate outcomes. A more pragmatic approach is to both protect the server and mission-critical applications.
Traditional EDR is too slow for cloud
Security teams and leaders are under increased pressure to protect business interests, in part because the operational impacts of a breach can affect revenue, reputation, and even share prices. Unfortunately, the average dwell time for an attacker before being detected is 16 days, according the Mandiant M-Trends 2023 report, yet it only takes 10 minutes on average for attackers to breach a cloud environment, as reported in Sysdig’s 2023 Global Cloud Threat Report.
Enter the Sysdig 5/5/5 framework. 5 seconds to detect, 5 minutes to correlate, and 5 minutes to initiate a response. The traditional EDR approach to detecting attacks just doesn’t work in the cloud, where attacks are faster and environments are more complex. For instance, the average lifespan of a container is just 5 minutes. In an attack scenario, if the analyst does not see the detection within those 5 minutes, they will be unable to understand the scope of the event beyond just the alert. Security teams need the inherent advantages of cloud-native tooling for rapid and high-fidelity detections, followed by automatic contextualization and correlation of complex feeds. Accelerating detection and correlation across cloud-native services buys teams critical time as they initiate a response, a luxury not afforded with traditional EDR.
Advanced attacks, such as SCARLETEEL and ZERO TO ADMIN shown above, have the ability to move laterally between server and cloud. Traditional EDRs typically lack the visibility to see beyond the host, limiting context and correlation. This myopic view prevents security teams from being able to understand the incident context needed to respond within the 5/5/5 framework.
Sysdig’s end-to-end detection, investigation, and response capabilities accelerate teams, enabling the SOC to respond to threats at cloud speed. Traditional EDR just can’t deliver the speed, context, and response capabilities needed to stay ahead of attackers in the cloud.
Stepping back to move forward
To better understand why EDR’s “good enough” approach fails, we need to step back and look at the origins of traditional EDR: Windows workstations. Being purpose built for workstations and later being stretched into data centers, bare metal servers, and eventually the cloud results in critical shortcomings that security teams need to account for. Time-intensive tasks, such as attempting to correlate and contextualize events in container, Kubernetes, and serverless environments, slow teams to a crawl as they attempt to understand events. These core shortcomings set security teams up to fail.
Despite trying to change their spots to stripes, these traditional approaches are still unable to efficiently deliver adequate protection because of their foundational endpoint roots and immature Linux capabilities. The crux of this limitation is that EDR is purpose-built for endpoints, and as teams move into cloud-native services, those same value-drivers don’t exist.
For example, incidents in the cloud are multidimensional, so traditional EDR has trouble connecting and contextualizing the events that, although detected, are happening in separate dimensions. They simply can’t stitch them together. The only way for security teams to truly secure the cloud is with tools and platforms that are purpose-built for the cloud.
The future of cloud security – Bringing security and Dev together
Sysdig started deep in the cloud with containers and Kubernetes. These deep cloud roots are at the core of Sysdig’s cloud-native application protection platform (CNAPP), empowering Dev and security teams to protect cloud-based applications and infrastructure. Sysdig’s unified CNAPP capabilities, pictured below, create a bridge, connecting Dev, engineering, and security teams across their cloud estate. Detection and response capabilities within Sysdig CNAPP are part of Cloud Detection and Response (CDR). These capabilities, such as centralized controls, threat detection, and incident response, are built for maximal efficacy in the cloud. CDR supports the security center’s growing ownership of not only the server, but its contents and larger cloud relationships.
Upgrade to cloud-centric detection
Being rooted in the endpoint means EDR tools are primarily Windows workstation/endpoint centric. This relational misalignment limits visibility to cloud attacks where the focus should instead be centered on Windows and Linux services and applications. Further, EDR identification of lateral movement can be heavily dependent on network visibility, while cloud security tools achieve better visibility of lateral movement through identity and entitlements. Essentially, cloud logs and recording API calls provide better visibility and correlation by default (compared to traditional on-prem workloads), where lateral movement can only be inferred. These misalignments have major implications across critical instrumentation for collection, enrichment, correlation, and response in Linux environments.
Ditch the confines of traditional EDR black boxes
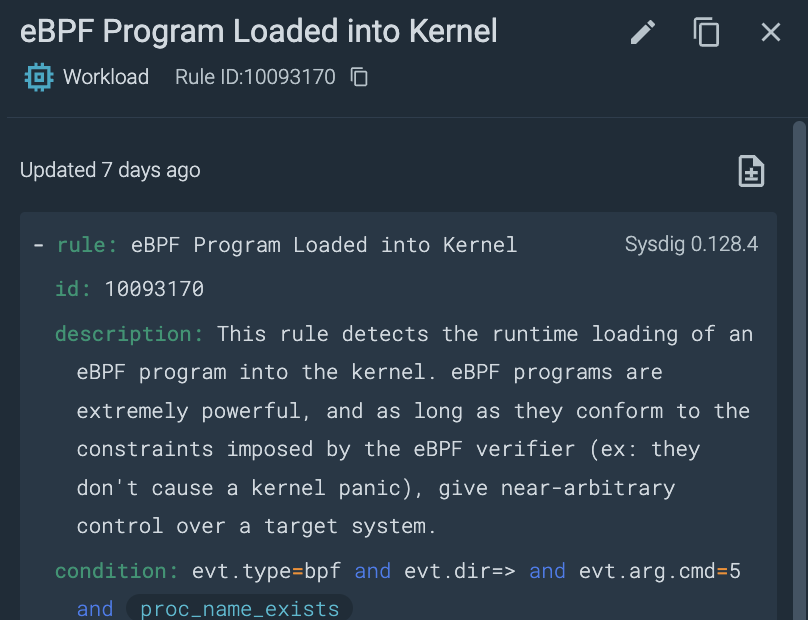
While traditional EDR operates from an opaque black box model, Sysdig’s Linux detections stand apart. Based on Falco, Sysdig has over 100 transparent rules for Linux servers across attack types, extending beyond traditional EDR capabilities in the cloud. Behavioral-based, fileless, and machine learning (ML) attack detections add additional layers of protection to the customizable logic teams can leverage to protect their organization. Real-time intrusion detection and response for kernel-level attacks uncover the subtlest of deviations from normal behavior, detecting stealthy techniques, such as BPF backdoor injection, even with obfuscation attempts. Malware-specific detections leverage behavioral, ML, and artificial intelligence (AI) approaches to protect cloud estates from a broad spectrum of cloud-relevant malware, including cryptominers and fileless attacks. Windows support also offers Sysdig’s superior transparency and support of custom logic to fit unique customer environments.
Graduate to cloud speed for correlated and contextualized investigations
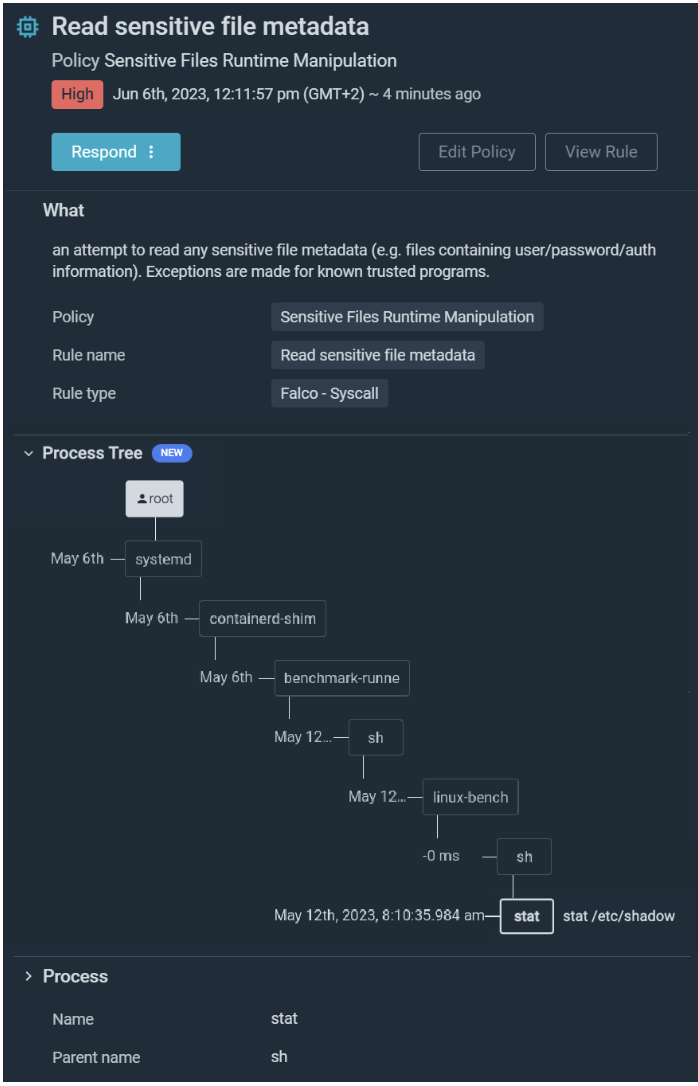
Security teams with traditional EDR must manually stitch isolated events together, slowing their ability to effectively respond. Sysdig provides easy access to relevant, rich context so security teams can trace and build on an event across containers, hosts, and cloud activity. Activity Audit captures all interactive command executions, including every network connection, file access, and process creation. System call captures are able to recreate every syscall, even when the container goes away. Event Details are enhanced with Sysdig’s process tree (Shown below) visualizations for workload-related events such as ancestral lineage to the root process. Simplified forensic context and correlation across domains into a single view accelerates triage and investigation.
Bring the entire toolbox with cloud response capabilities
In addition to limited visibility and needing to manually stitch events together, traditional EDR responses are still stuck on an endpoint approach. Security teams have limited capabilities when responding to threats beyond the host and into containers. For instance, if a server with a compromised image containing malware (e.g., from software supply chain tampering) were deployed into a production environment. If the EDR is able to detect the malware, it may be able to kill or isolate the rogue process or whole container. Unfortunately, traditional EDR tooling lacks the capabilities to prevent that compromised image from reaching deployment in production.
While the kill or isolate actions may be appropriate for a laptop, they are fundamentally flawed in the cloud. This is because units of computing in the cloud are backed by auto-scalers to ensure infrastructure can scale to the limits of the internet. In this scenario, those very autoscalers would recreate the workload or host virtual infrastructure to ensure limited downtime, as the number of instances/containers has to equal the threshold specified in the autoscaling group resource. In this instance, traditional EDR and its limited capabilities in cloud infrastructure only function as a speed bump in delaying the pain.
Sysdig has a radically different approach to cloud response. Sysdig integrates with existing cloud Infrastructure-as-Code (IaC) resources that can make changes at the cloud resource level. We cannot treat a cloud VM or container the way we would with traditional endpoints/workstations, since they are fundamentally different.
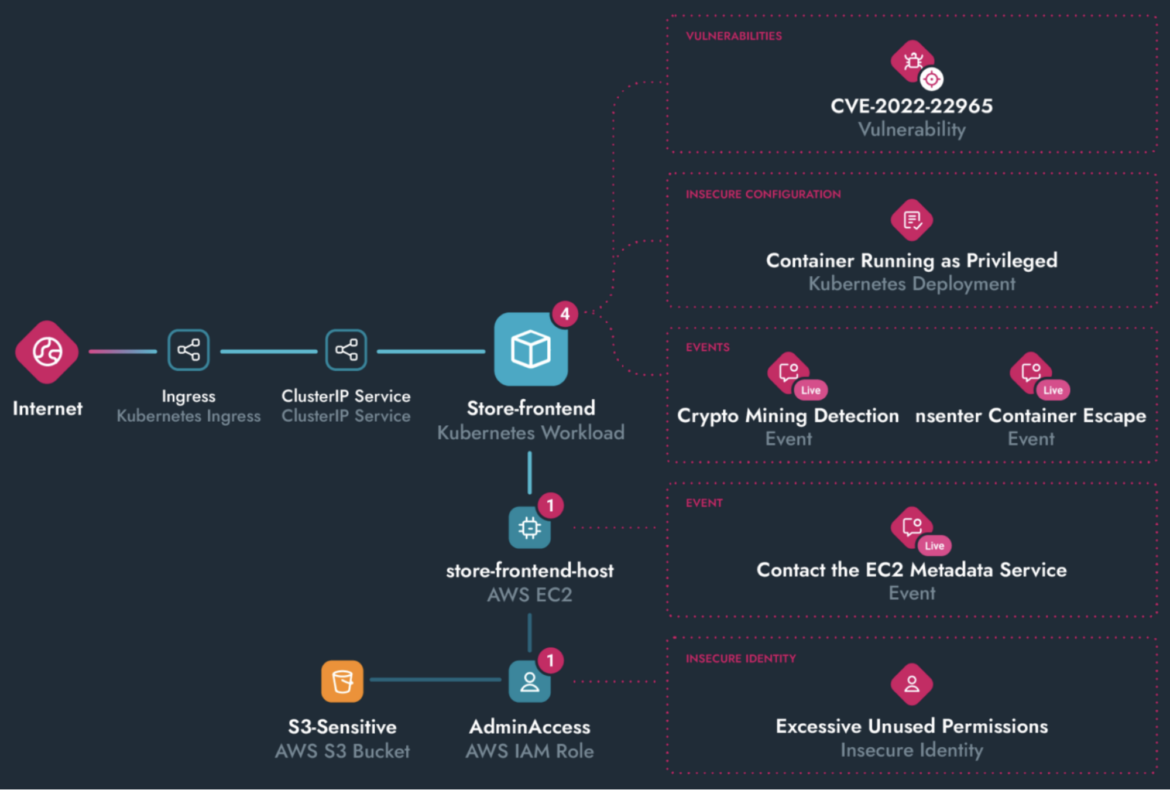
Further, Sysdig’s actionable, runtime-aware attack path (shown below) enables teams to proactively mitigate threats and risks with extensive response capabilities across their cloud estate. Malware processes are prevented automatically, while container-centric actions are more robust with pause, stop, and kill options. Post detection, Sysdig automatically creates forensic captures for rapid triage and root-cause analysis. If needed, security teams can jump directly into the impacted host with Sysdig’s Rapid response for surgical remediation actions.
A Path Forward
As organizations continue on their cloud journey from lift and shift to fully cloud native, security and Dev teams need to evolve in parallel. Sysdig’s deep cloud roots and best-of-breed CNAPP unifies development and security as the optimal partner to drive innovation at cloud speed.


