Sysdig Secure-Google Chronicle Integration – Why, What and How
Get Demo
Sysdig and GCP Partnership
Sysdig on Google Cloud Marketplace
The case for combining SIEM and CWPP
Cloud adoption and digital transformation have enlarged attack surfaces that can be exploited by malicious actors to harm your organization. Traditional SIEMs and EDRs fall short as they are not cloud-native and also difficult to scale. Further, there are inherent fixed costs that need to be considered when adopting any modern threat detection apparatus.
A combination of Cloud Workload Protection Platform (CWPP) and Security information and event management (SIEM) solutions have become critical to provide clear signals and security intelligence to teams so that they do not fail to detect any suspicious activity.
Brief primer on Google’s security stack and Chronicle
Starting in 2022 Google has made heavy investments and also acquisitions of cloud security companies. Today, this enhanced security stack from Google includes:
- Mandiant as the incident response provider & consulting partner
- Google Chronicle for SIEM functions
- Seimplify for SOAR functions within Chronicle one platform
- Google Cloud and Virus Total for sourcing threat intelligence
- EDR integrations to enrich threat intelligence
Google Chronicle is a premier SIEM solution for the cloud that skips the problems associated with traditional SIEMs and also takes away the associated CAPEX investments. It focuses on the following 6 important value drivers:
- Speed and data quality of the logs ingested
- Driving SOC analyst productivity
- Lowering the total cost of ownership vs traditional SIEM setups
- Lowering time to extract value
- Performance
- Threat visibility
Why is it a good idea to use a tool like Google Chronicle?
With Chronicle, you hunt for threats with the speed and scalability of Google Cloud’s technology to get instant analysis and context on any incident.
It has a unified data model that allows for deep learning and correlation analysis of suspicious activity. Chronicle’s sophisticated threat hunting and security analytics get amplified with Seimplify. This helps you streamline SOC operations so that it takes less time to investigate incidents.
3 ways in which Sysdig Secure adds value with Google Chronicle
Threat detection and incident response for runtime security are necessary capabilities for comprehensive cloud security. Sysdig Secure and Google Chronicle together:
- Make SOC teams’ journey easy by unfolding evidence, providing answers and remediation faster and clearer to security threats.
- Enable customers to extract more value from the data we collect from their cloud workloads in their runtime environments.
- Foster cross-functional value with security, compliance, and DevOps teams.
Why should you use Sysdig Secure with Chronicle? Hear it from ApreeHealth
Sysdig has validated its security, monitoring, and compliance capabilities with multiple GCP-related services. Sysdig and GCP have a common goal of helping customers ship cloud apps faster by helping them see more, secure more, and save time in troubleshooting deployed microservices.
Reason 1: Sysdig Secure has powerful threat detection capabilities
Sysdig’s Secure is built with the Falco rules engine at its core which makes it simple to detect suspicious activity. Sysdig Secure can then forward enriched events from Sysdig to Google Chronicle SIEM and SOAR setups.
Reason 2: Sysdig lends deep and contextual visibility to Google Chronicle
Sysdig Secure is able to look into system call-level detail for containers and hosts. It leverages Falco rules to detect activity, such as the spawning of a terminal shell within a container. By monitoring Kubernetes API calls together with system calls, it can detect suspicious activity and then send the details, including Kubernetes context, over to Chronicle. With Sysdig you can go beyond the capabilities of agentless solutions and:
- Have multiple Falco rules tagged by the relevant best practices/compliance mandates
- Enhance Google Chronicle’s security capabilities beyond cloud metadata and audit logs
- Get the full context about activities within container and host workloads at runtime
Reason 3: Chronicle (SIEM and SOAR) allows for extensive forensic activities based on the event data provided by Sysdig Secure
These capabilities can be summarized as follows:
- Data visualization of threats and suspicious activities on dashboards
- Correlation with other data points to further investigations
- Alerting based on advanced forensics
Runtime security: The core of the integration
Sysdig Secure provides an event forwarding feature that sends Runtime Policy Events detected by Falco rules to Google’s SIEM and SOAR platforms. This enables you to view and correlate Sysdig security findings directly in the tools you use for analysis or use these events as triggers within your SOAR playbooks.
Phil Williams (SVP, Partnerships, Sysdig) states: “Security teams can be reassured only when an incident forensic story is fully narrated with its minutest details. With Sysdig integration, security teams will extract even more value from their discoveries using Google Chronicle’s powerful security intelligence features. Combining the workload side of the story with the network and cloud metrics – Security teams will now have higher confidence that an event led to a compromise in addition to the coordinates to mitigate, investigate impact radius, and identify actors and means.”
How to set up the integration?
The following steps showcase how to leverage Sysdig Secure with Google Chronicle. Although working, this integration is in beta and not officially supported by Sysdig yet as we are still carrying out rigorous testing with it.
We validated a proof-of-concept for connecting Sysdig Secure with Google Chronicle. Follow the below-mentioned steps to quickly integrate these two security systems.
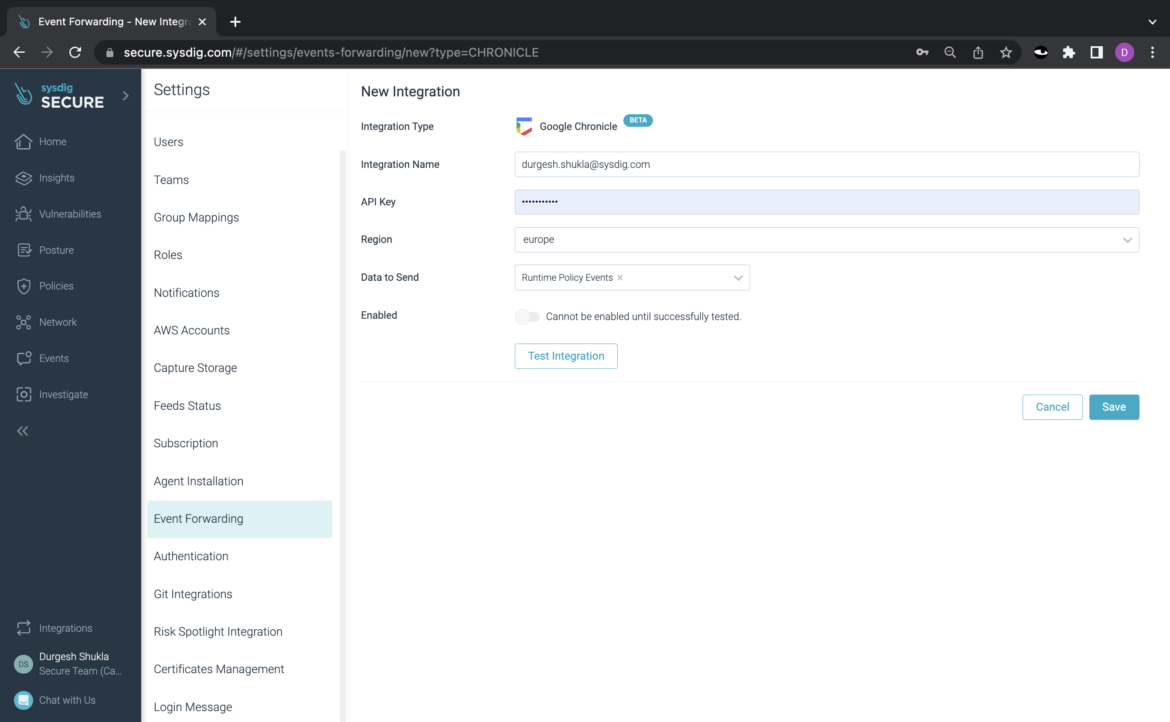
Step 1 – Set up the Google Chronicle integration within Sysdig
Within Sysdig Secure, go to “Settings” > “Event Forwarding” and select “Add Integration.” Choose Chronicle. Then, enter the integration name, and the API secret key. Also, select “Runtime Policy Events” as the type of event data you wish to send to Google Chronicle.
Step 2 – Dive into event details from Sysdig on Google Chronicle
In the Google Chronicle, you can dive deeper into any event from the list of all Sysdig events, and then use it for further forensic investigations.
Step 3 – Set up Google Chronicle visualizations for Sysdig events
Besides forensics, you can also visualize all the Sysdig events with Looker dashboards for Chronicle. These visualizations can then be added to relevant threat investigation dashboards.
Additional resources
Sysdig on Google Cloud Marketplace

