
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Sysdig Secure adds Rapid Response feature to streamline detection and response in container environments
The increasing number of yearly reported data breaches and new critical vulnerabilities, such as log4j, impacting both small and large businesses shows that cyberthreats are real and targeting everyone. You can minimize risk by implementing runtime security and having an incident response plan in place to contain attacks. But, in container environments, responding fast to incidents is challenging.
Cloud-native complexity and ephemerality leaves security teams without an easy way to perform investigations and detect suspicious activities in containers.

Existing EDR solutions cannot solve this, because they were designed for hosts. As they don't see containers, they just present a list of all processes running on the host. Which processes belong to each container is up to the response team to figure out. For instance, they don't zoom in and isolate the troubled container in a Kubernetes cluster. Response teams are left with event alerts without context, data evidence, and quick access to containers for mitigation.
To address the need for a fast response in cloud-native and Kubernetes environments, Sysdig released Rapid Response, the first runtime security solution with EDR functionality for containers.
Security incidents' MTTR is increasing in cloud-native environments
A mean time to respond (MTTR) to a security incident that spans days or weeks sounds like an eternity when you think in terms of the period an intruder stays in your environment.
But, unfortunately, it is a reality for many organizations dealing with lack of container visibility and limited resources to handle an increasing number of incidents. Life is not easy for those investigating security events and controlling and eradicating threats in cloud-native environments.
Think of an event triggered by a suspicious activity in a Kubernetes cluster. If you feel that you need a lot of visibility and context before killing containers to stop a potential attack, that is life for security teams. Often, it is necessary to perform local investigation, checking running processes, looking into log files, getting a memory dump, etc., to assess the threat, determine the right mitigation path, and then act. Killing containers and processes prematurely could cause unnecessary application downtime or degradation.
The response needed is delayed because security response teams don't have an automated process to access a production container to do the necessary investigation and remediation.
Why aren't existing EDR tools helping?
Existing EDR tools are not effective in cloud-native environments because they were not designed to deal with ephemeral infrastructure. They don't provide container visibility and they don't understand Kubernetes.
Current EDR tools are host-centric. They leave response teams with the last mile problem to solve, piecing information together to identify container processes, files, scope, and user activities. And when doing deep investigation looking into memory dumps, the security incident responder will not have any container delimitations to guide the analysis. While "what" and "how" are sorted out, MTTR is ticking.
What is needed?
Real-time response capabilities in Kubernetes container environments. Direct access to compromised containers right from the event alert will significantly improve MTTR from days and weeks to immediate response.
To address this requirement, Sysdig Secure introduced the Rapid Response feature. Rapid Response provides modern EDR functionalities for cloud workloads, enabling direct shell access to containers and hosts. It gives security teams the ability to act on incidents straight from the incident detection. No extra steps needed, no time wasted.
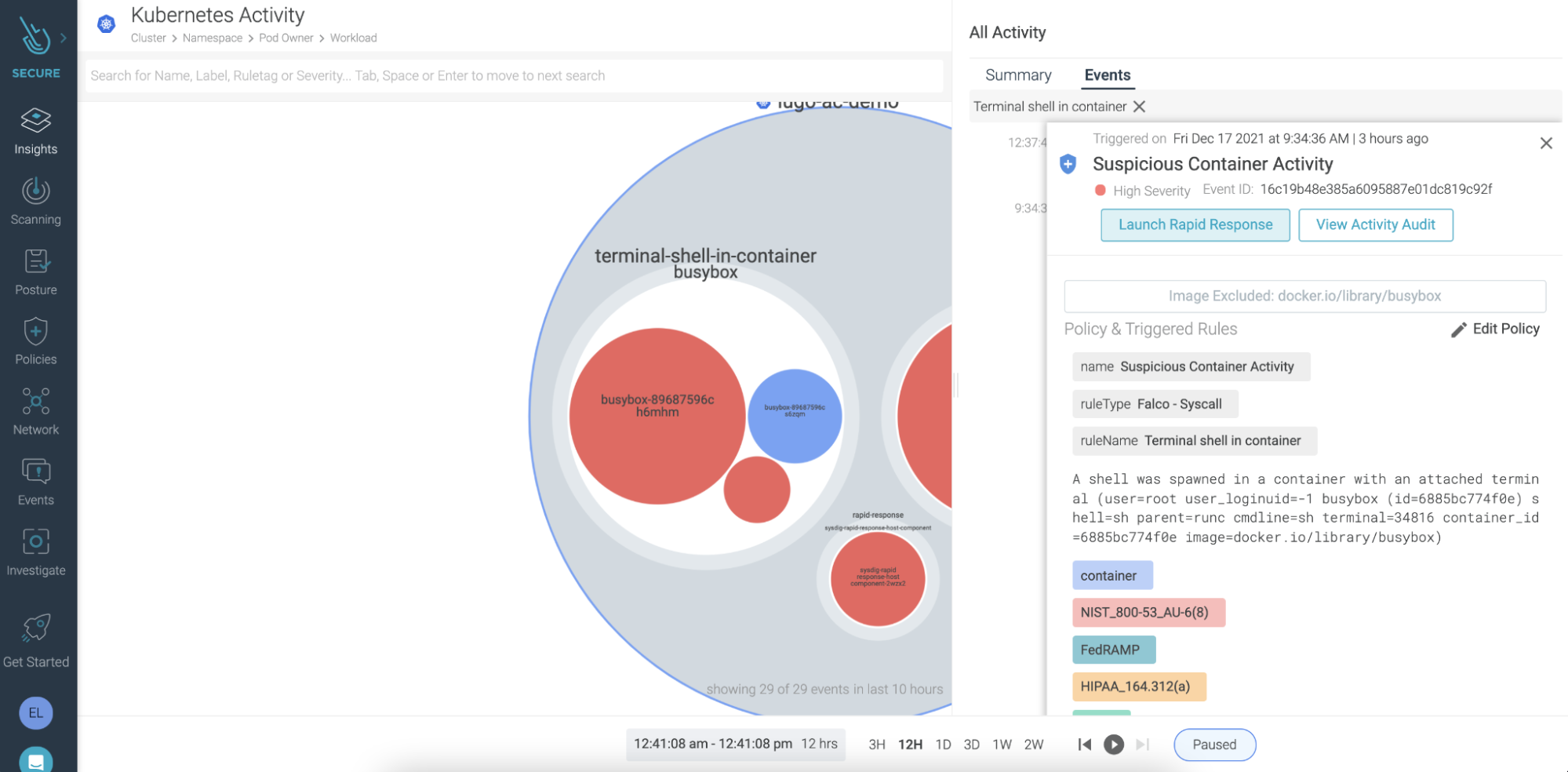
What else is important?
Seamless integration into existing practices. Skills gap is a top reason for security to lag behind in organizations. Response teams, including the SOC engineer, IT operations, and developer should operate and collaborate in a shared and common knowledge environment.
Rapid Response feature doesn't require any learning of additional language, commands, or scripting skills. The response team can mount their own investigation and remediation scripts in Rapid Response, as well as use host tooling already installed, such as kubectl, docker commands, and cloud CLIs. No learning curve, just out-of-the-box benefits.
Key Use Cases
Our customers have long expressed their frustration trying to use EDR tools in cloud-native environments. Here are some key Rapid Response use cases that address existing challenges faced by Tier 1 and Tier 2 responders when dealing with container threats:
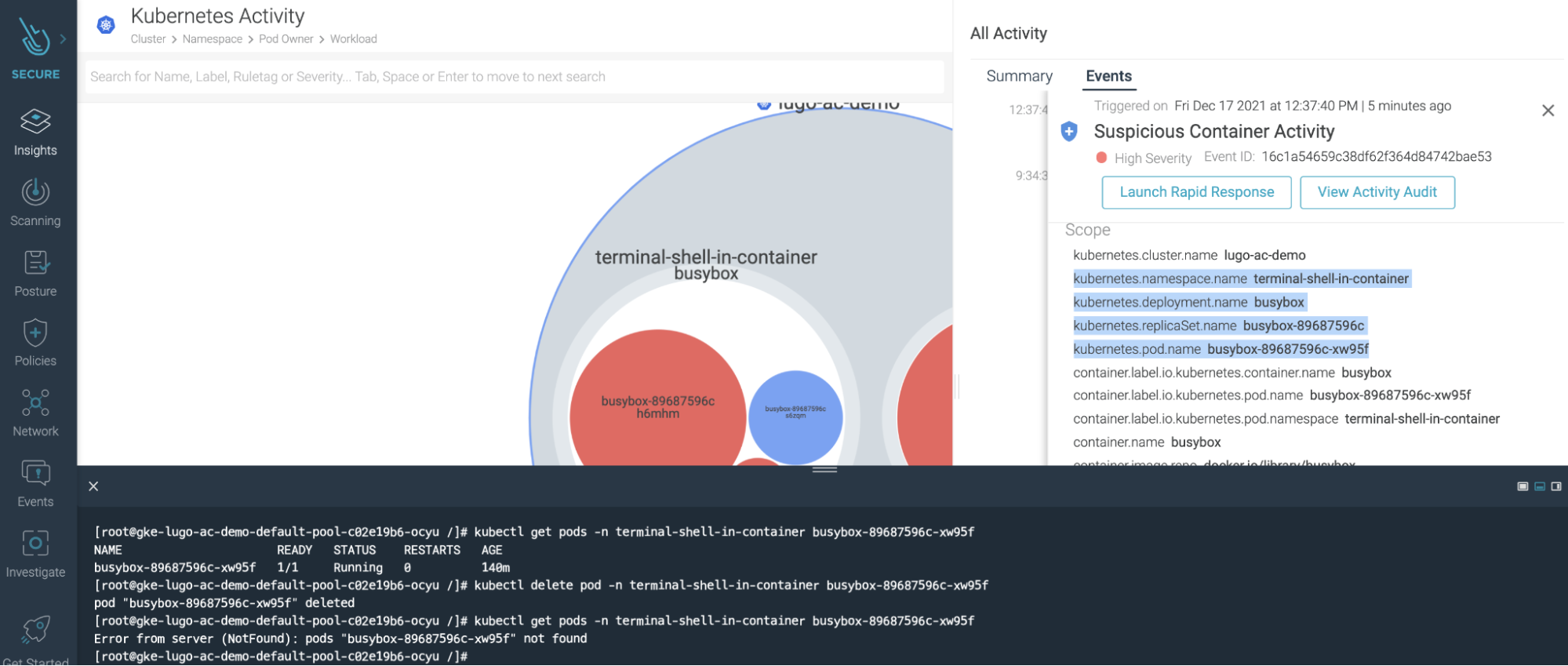
Use Case: Tier 1 on-demand shell access to investigate a suspicious Kubernetes container
One-click direct access to a container or host to investigate and troubleshoot locally.
Tier 1 responders team can take a deep look at malware files and suspicious activity, check if a suspicious file, or a malware file, is active in the system, and verify container escape and file-less attack by looking at CPU and memory data.
Use Case: Tier 2 advanced analytics and remediation
Shell in for fast mitigation without having to maintain admin role over the entire cloud environment.
Tier 2 responder can perform remediation with fine-grained actions such as kill processes and remove files, as well as perform quick containment like stopping the container.
Use Case: Enable collaborative work between developers and response teams
Get seamless integration with existing development, operations, and security remediation processes to apply the right containment, mitigation, and malware hygiene actions. Response teams can use the same cloud, host, and container utilities used by cloud, security, and development teams.
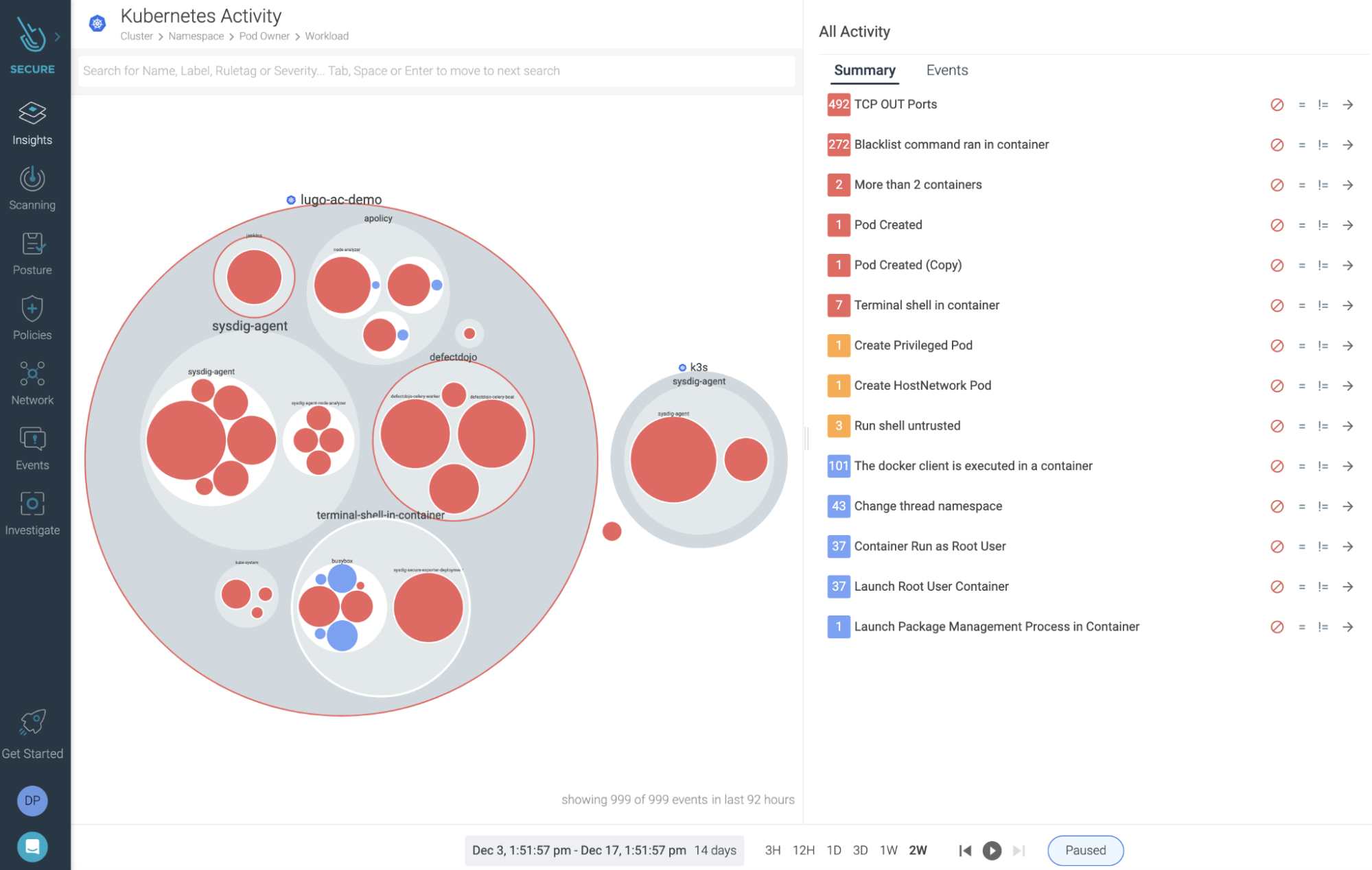
A modern solution for incident response in cloud-native environments – Sysdig Secure EDR
Sysdig Secure is the only cloud security solution with EDR functionality for containers.
With Rapid Response, response teams can perform fast alert triage, deep investigation, and immediate remediation of threats, significantly reducing MTTR, risk exposure, and attack impact.
The log4j vulnerability has shown us the importance of being flexible and resilient. Therefore, it is important to have the best tool for future security incidents and to be prepared.
Check how fast and easy is to go from detection to contention with Sysdig Secure
Sign up for a free trial
Visit our page Container Forensics & Incident Response Solutions, or the Threat Reports from the Security Research Team.


