29 Docker security tools compared
There are quite a few Docker security tools in the ecosystem – how do they compare?
We have gathered a list of the most popular Docker security tools so you can evaluate what fits your needs better, including features and use cases. Here you will find both open source projects, Docker and Kubernetes security commercial vendors.choosing the right Docker security tool depends on your specific needs, environment, and security goals.
Whether you opt for an open-source project or a commercial solution, understanding the features and use cases of each tool will help you make an informed decision. A secure containerized infrastructure starts with the right tools—take the time to evaluate what aligns best with your requirements.
But is Docker insecure? Not at all. Actually features like process isolation with user namespaces and resource encapsulation with cgroups reduce the attack vector providing a great deal of protection. But moving into Docker provides an opportunity for much better security: Docker image scanning to detect known vulnerabilities, runtime security to identify and block threats on production, network security, compliance, audit and forensics are some of the areas where you can improve your security with the following Docker security tools.
Alphabetical index of Docker Security tools
- Anchore Engine
- Aporeto
- AppArmor
- AquaSec
- BlackDuck Docker security
- Calico
- Capsule 8
- Cavirin
- Cilium
- CoreOS Clair
- Docker capabilities and resource quotas
- Docker-bench security
- Dockscan
- Falco
- Google Cloud Security Command Center
- HashiCorp Vault
- Layered Insight
- NeuVector
- Notary
- OpenSCAP
- Open Policy agent
- REMnux
- SELinux
- Seccomp
- StackRox
- Sysdig Secure
- Sysdig
- Tenable Flawcheck
- Twistlock
Top 5 use cases for securing cloud and containers
Keep your containers safe, while keeping up with the speed of innovation.
Anchore Engine
License: Open source.
Use Cases: Pre production vulnerability analysis and policy based security and compliance checks.
The Anchore Engine allows developers to perform detailed analysis on their container images, run queries, produce reports and define policies that can be used in CI/CD pipelines.
Developers can extend the tool to add new plugins that add new queries, new image analysis, and new policies.
Aporeto
Homepage: https://www.aporeto.com/
License: Commercial
Use Cases: Platform independent software identity and security enforcement.
Aporeto focuses on providing a unique, cryptographically certified identity to the different pieces of software that conform your stack. This approach allows you to abstract away the underlying platform or platforms you use to run your services, whether you are using Kubernetes, cloud services, bare-metal hosts or any combination of them.
For example, you may have a database running in DC/OS and any number of consumer processes running in a few Kubernetes clusters. Using Aporeto identity services, the database can accept or deny the communication based on the identity of its peers and the operator will have a full trace of the agents involved in this operation.
AppArmor
License: Open Source.
Use Cases: Runtime protection, Mandatory Access Control (MAC).
AppArmor lets the administrator assign a security profile to each program in your system: filesystem access, network capabilities, link and execute rules, etc.
It's a Mandatory Access Control (or MAC) system, meaning that it will prevent the forbidden action from taking place, although it can also report profile violation attempts.
AppArmor it's sometimes considered a more accessible and simplified version of SELinux, both are closely related. You only need to learn the profile language syntax and fire your favorite editor to start writing your own AppArmor rules.
Docker context: Docker can automatically generate and load a default AppArmor profile for containers named docker-default. You can create specific security profiles for your containers or the applications inside them.
AquaSec
License: Commercial.
Use Cases: Pre-production analysis, runtime protection, compliance & audit, etc.
"page" title="Page 6">
"section">
"layoutArea">
"column">
AquaSec is a commercial security suite designed for containers in mind. Security audit, container image verification, runtime protection, automated policy learning or intrusion prevention capabilities are some of the most relevant features.
/span>>
The platform provides programmatic access to its API and can be deployed both locally or in the public cloud.
/span>>
/div>>
/div>>
Code language: Perl (perl)BlackDuck Docker Security
License: Commercial
Use Cases: Pre-production analysis, vulnerability newsfeed, license/legal assessment.
Black Duck Hub specializes in container inventory and reporting image inventory, mapping known security vulnerabilities to images indexes and cross project risk reports. You can easily pinpoint the specific libraries, software packages or binaries that are causing the security risk and the assistant will automatically offer you a list of known fixes.
As opposed to similar solutions, Black Duck Hub also analyzes the "License Risk" considering the different software licenses that you are currently bundling together to deploy your containerized distributed system.
div class="page"
title="Page 7">
div class="section">
div class="layoutArea">
div class="column">
p>span>BlackDuck focuses more on scanning and pre-production than run- time security and forensics. span>p>
div>
div>
div>
div>Code language: HTML, XML (xml)Cilium
License: Open Source.
Use Cases: HTTP-layer security, network-layer security.
Cilium provides transparent network security between container applications. Based on a new Linux kernel technology called eBPF, it allows you to define and enforce both network-layer and HTTP-layer security policies based on container/pod identity.
Cilium leverages BPF to perform core data path filtering, mangling, monitoring and redirection. These BPF capabilities are available in any Linux kernel version 4.8.0 or newer.
Calico
Homepage: https://www.projectcalico.org/
License: Open Source
Use Cases: Virtual networking and network security for containers.
Calico is often deployed during installation with the rest of your Kubernetes cluster components to provide the inter container network layer. Calico implements the default Kubernetes Network Policy interface to define firewalling capabilities and extends it providing features like namespace isolation, advanced endpoint ACLs, annotation-based network security and outgoing (egress) container rules. Although several of its features are designed to integrate with Kubernetes, you can also use Calico with Docker Swarm or just plain Docker containers.
Capsule8
Homepage: https://capsule8.com/
License: Commercial
Use Cases: Real time vulnerability detection, zero-day attack live response and intrusion prevention.
Once the capsule8 sensor is deployed throughout your IT infrastructure whether is cloud, bare metal, virtual machines or a combination of those, you will receive a live stream of security filters that are created combining machine-learning techniques and expert-driven analytics and target the latest attack vectors, including zero-day vulnerabilities. These filters will be in charge of analyzing your software and networking activity to detect the patterns that match the targeted attacks, and also to perform automated mitigation measures that can range from simply alerting the operators to blocking network connections or restarting affected containers.
Cavirin
License: Commercial.
Use Cases: Runtime protection, pre-production analysis, compliance & audit
Cavirin works with organizations such as CIS to collaboratively develop and maintain the security standards that any other tool can benefit from. At present, it has authored CIS Docker Security Benchmark as well as CIS Kubernetes Security Benchmark. They have minted the term “DevSecOps” to stress their focus at integrating the security and DevOps/container fields. Apart from the features you can expect in a one-stop DevOps security platform (maybe comparable to Twistlock or AquaSec in their feature proposal and approach), we can highlight their compliance&audit tooling for security standards like PCI, HIPAA, NIST or GDPR.
CoreOS Clair
License: Open Source.
Use Cases: Pre-production analysis, vulnerability newsfeed.
Clair is an open source project for the static analysis of vulnerabilities in containers (currently supporting AppC and Docker). Clair periodically refreshes its vulnerability database from a set of configured CVE sources, scrubs the available container images and indexes the installed software packages. If any insecure software is detected, it can alert or block deployment to production.
Since Clair image analysis is static, containers never need to be actually executed, so you can detect a security threat before is already running in your systems. Clair is the security engine that CoreOS Quay registry uses internally.

Top 5 use cases for securing cloud and containers
Keep your containers safe, while keeping up with the speed of innovation.
Docker capabilities and resource quotas
License: Open Source.
Use Cases: Runtime protection, resource DoS protection.
We shouldn't forget the basic security measures that come already bundled with our OS and the Docker engine.
Resource abuse and denial of service is an often overlooked but very real security problem in a containerized environment with vast amounts of software entities competing for the host resources.
Control Groups (cgroups) is a feature of the Linux kernel that allows you to limit the access processes and containers have to system resources such as CPU, RAM, IOPS and network.
Capabilities allows you to break down the full root permissions into several split permissions, this way you can remove specific capabilities from the root account or augment the capabilities of user accounts at a more granular level.
Docker-bench security
License: Open Source.
Use Cases: Compliance & security audit.
The Docker Bench for Security is a meta-script that checks for dozens of common best-practices around deploying Docker containers in production.
This script is conveniently packaged as a Docker container, just copying and pasting the docker run one-liner from its homepage you can instantly see the results of ~250 checks for your running Docker containers and the host running the Docker engine (Docker CE or Docker Swarm). Docker Bench tests are inspired by the CIS Docker Community Edition Benchmark v1.1.0.
Dockscan
License: Open Source.
Use Cases: Compliance & audit.
A simple ruby script that analyzes the Docker installation and running containers, both for local and remote hosts.
It's easy to install and run with just one command and can generate HTML report files. Dockscan reports configured resource limits, containers spawning too many processes or with a high number of modified files, also if your Docker host is allowing containers to directly forward traffic to the host gateway, to name a few examples.
Falco
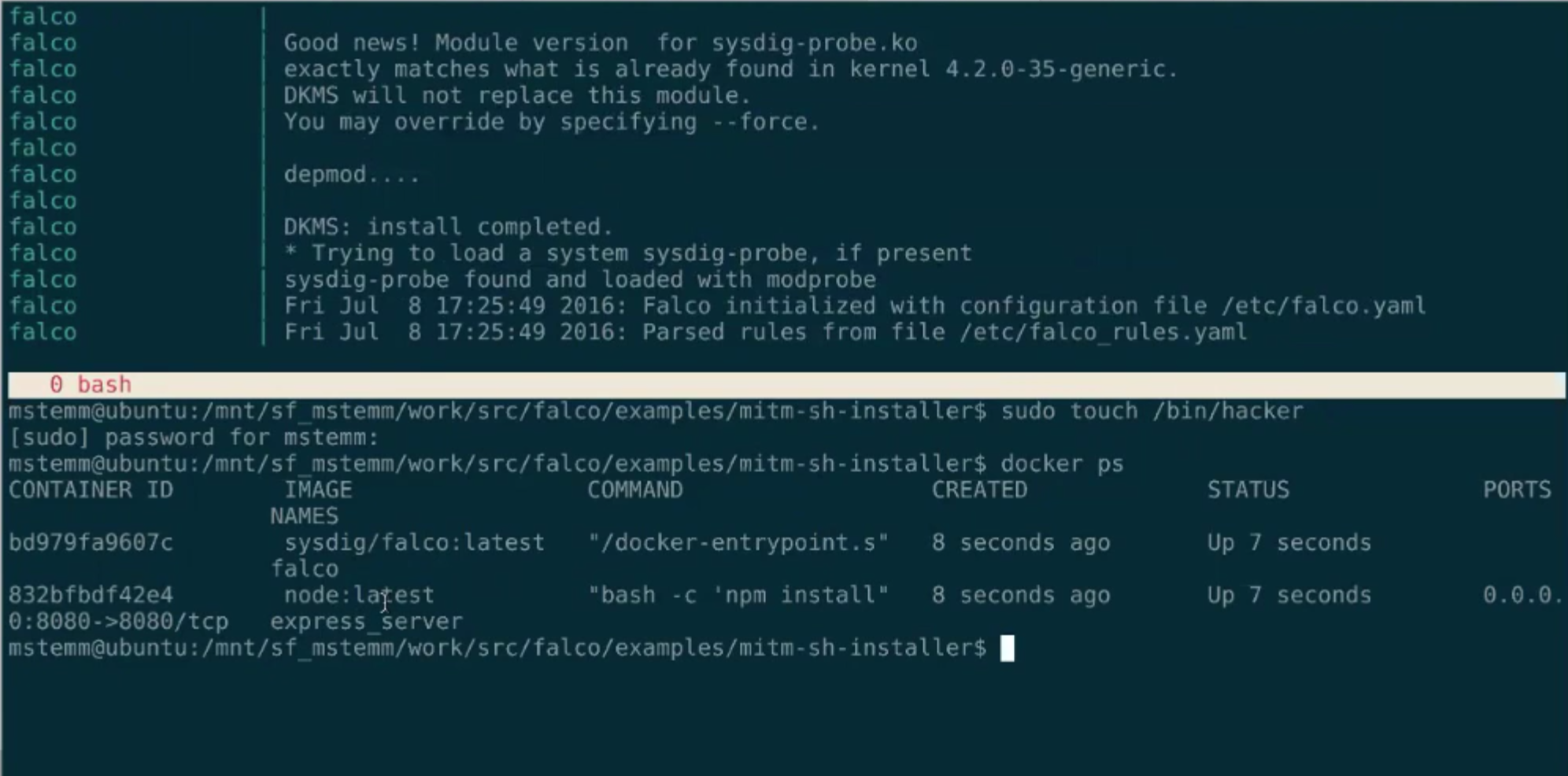
Homepage: https://sysdig.com/opensource/falco/
License: Open Source.
Use Cases: Runtime alerting, forensics.
Sysdig Falco is an open source, behavioral monitoring software designed to detect anomalous activity based on the Sysdig monitoring technology. Sysdig Falco also works as a intrusion detection system on any Linux host.
Falco is an auditing tool as opposed to enforcement tools like Seccomp or AppArmor. It runs in user space, using a kernel module to retrieve system calls, while other similar tools perform system call filtering/monitoring at the kernel level. One of the benefits of a user space implementation is being able to integrate with external systems like Docker, Docker Swarm, Kubernetes, Mesos, etc and incorporate their metadata and tags.
Docker context: Falco supports container-specific context for its rules. Using this tool you can monitor the containers behaviour without instrumenting or modifying them in any way. Custom rule creation is very easy to grasp and the default rules file comes prepopulated with sane defaults.
Google Cloud Security Command Center (Cloud SCC)
Homepage: https://cloud.google.com/security-command-center/
License: Commercial
Use Cases: Canonical security and data risk database for Google Cloud Platform (GCP), extensible with security feeds from multiple third-party operators.
With Google Cloud Security Command Center, you can manage the security of your Google Cloud infrastructure: browse through the inventory of your cloud assets, scan storage systems for sensitive data, detect common web vulnerabilities, and review access rights to your critical resources. Using Google Cloud SCC you can, for instance, identify and protect your sensitive data volumes, detect widespread vulnerabilities like XSS or SQL injections, identify threats like botnets, crypto mining, track unexpected network traffic and much more. SCC can aggregate security events from different sources like: Sysdig Secure – Container security for Cloud-Native applications or Falco opensource runtime security engine.
HashiCorp Vault
License: Free with enterprise version.
Use Cases: Secure container-aware credentials storage, trust management.
Hashicorp's Vault is an advanced suite for managing secrets: Passwords, SSL/TLS certificates, API keys, access tokens, SSH credentials, etc. It supports time-based secret leases, fine-grained secret access, on-the-fly generation of new secrets, key rolling (renewing keys without losing access to secrets generated using the old one) and much more.
Vaults keeps a detailed audit log to keep track of all the secrets and the access and manipulations performed by each user/entity, so operators can easily trace any suspicious interaction.
Docker context: The secure distribution and traceability of secrets is a core concern in the new microservices and containerized environments, where software entities are constantly spawned and deleted. Vault itself can be deployed as a Docker container.
Layered Insight
Homepage: https://layeredinsight.com/
License: Commercial
Use Cases: Static image scanning, container security compliance, runtime and network analysis.
Layered Insight is a container security solution that provides image vulnerability scanning and compliance validation. Once the container is validated it will need to be instrumented by injecting the Layered binary probe as part of the final image. When this instrumented container is deployed, Layered Insight will combine static user-defined policies with automatic behavior learning to create an “expected” behavior profile that will be injected as a set of security rules associated to any instance of this image. These containers will be monitored at runtime to detect code or networking activity that doesn’t conform to the injected security rules, triggering notifications and alerts.
NeuVector
License: Commercial.
Use Cases: Runtime protection, compliance & audit.
div class="page" title="Page 16">
div class="section">
div class="layoutArea">
div class="column">
p>span>NeuVector focuses on real-time security protection at runtime. Automatically discovers behavior of applications, containers, and services, detects security escalations and other related threats in a similar fashion to other Linux IDS. NeuVector privileged 'enforcer' containers are deployed on each physical host, with full access to the local Docker daemon, apart from that, the internal technology used by NeuVector is not thoroughly detailed in the publicly accessible documentation. span>p>
p>span>NeuVector aims to be a non-intrusive, plug&play security suite, performing automatic discovery of running containers and their default behavior to assist and counsel the operators in the design of their infrastructure security profiles. NueVector focuses on container network security rather than the underlying system like many of the other run-time players. span>p>
div>
div>
div>
div>Notary
License: Open Source
Use Cases: Trusted image repository, trust management and verifiability.
Image forgery and tampering is one major security concern for Docker-based deployments. Notary is a tool for publishing and managing trusted collections of content. You can approve trusted published and create signed collections, in a similar fashion to the software repository management tools present in modern Linux systems, but for Docker images.
Some of Notary goals include guaranteeing image freshness (most up to date content, to avoid known vulnerabilities), trust delegation between users or trusted distribution over untrusted mirrors or transport channels.
OpenSCAP
License: Open Source.
Use Cases: Compliance & audit, certification
OpenSCAP provides a suite of automated audit tools to examine the configuration and known vulnerabilities in your software, following the NIST-certified Security Content Automation Protocol (SCAP).
You can create your own custom assertions and rules and routinely check that any software deployed in your organization strictly abides.
These set of tools is not only focused on the security itself, but also on providing the formal tests and reports that you may need to meet an official security standard.
Docker context: The OpenSCAP suite provides a Docker-specific tool oscap-docker to audit your images, assessing both running containers and cold images.
Open Policy Agent
Homepage: https://www.openpolicyagent.org
License: Open Source
Use Cases: Pluggable and platform-agnostic policy definitions, easily extendable and customizable rule engine and language.
Open Policy Agent can decouple security policies and security best practices from your runtime platform (Kubernetes, Docker) and services (Kafka, etc…). Security policies are written using OPA's purpose-built, declarative language: Rego. Your software can then offload security decisions to the OPA engine, so you can update your policies or load new ones live without affecting operations. Using OPA you can, for example, enforce a naming convention for your containers or avoid downloading certain tags like "latest".
REMnux
License: Open Source.
Use Cases: Forensics.
A security oriented distribution based on Ubuntu. REMnux is a free Linux toolkit for assisting malware analysts with reverse-engineering malicious software, commonly known as forensics. As you can guess, this system bundles a vast amount of pre installed analysis and security tools: Wireshark, ClamAV, tcpextract, Rhino debugger, Sysdig, vivisect... just to name a few.
REMnux aims to be the swiss knife that you carry around in a usb memory in case you suspect any of your systems have been compromised.
Docker context: The REMnux project conveniently provides several of its integrated security tools as Docker containers, so you can instantly launch difficult-to-install security applications when you most need them.

Top 5 use cases for securing cloud and containers
Keep your containers safe, while keeping up with the speed of innovation.
SELinux
License: Open Source.
Use Cases: Runtime protection, Mandatory Access Control (MAC).
Security-Enhanced Linux (SELinux) is a Linux kernel security module. It is often compared with AppArmor, and it's also a Mandatory Access Control system. SELinux provides security capabilities from mandatory access controls to mandatory integrity controls, role-based access control (RBAC) and type enforcement architecture.
SELinux has a reputation of being particularly complex but powerful, fine-grained and flexible.
Docker context: Similarly to AppArmor, SELinux offers an extra layer of access policies and isolation between the host and the containerized apps.
Seccomp
License: Open Source.
Use Cases: Runtime protection, Mandatory Access Control (MAC).
Seccomp is not so much a tool but rather a sandboxing facility in the Linux kernel. You can think of it as an iptables rules-based firewall but for system calls. Newer versions use Berkeley Packet Filter (BPF) rules to filter syscalls and control how they are handled.
With Seccomp you can selectively choose which syscalls are forbidden/allowed to each container. For example, you can forbid file-permissions manipulations inside your container.
You may have noticed the similarities with Falco, both are closely related to the Linux Syscall API. This article compares these two (with AppArmor and SELinux) solutions. TL;DR: Unlike the others, Falco integrates rich high level container specific context to build rules.
Docker context: Docker has used Seccomp since version 1.10 of the Docker Engine, Docker has its own JSON-based DSL that allows you to define profiles that will be compiled to seccomp filters.
StackRox
License: Commercial.
Use Cases: Runtime protection, machine learning, pre-production analysis.
StackRox feature proposal revolves around the concepts of “Adaptive security” and auto discovery of components and behaviors. Highly focused on machine learning, StackRox aims to provides security that will evolve with your platform.
StackRox provides the usual features of commercial security platforms like cold image scanning or default security profiles ala SELinux.
StackRox understands containers and the images in your environment but can’t enforce policies based services determined by your orchestrator. They focus more on pre-production and run-time workloads rather than forensics and incident response.
Sysdig Secure
License: Commercial
Use Cases: End-to-end Kubernetes security, container security compliance standards, image scanning and vulnerability management, runtime security for cloud-native apps, forensics and audit.
Sysdig Secure protects your applications across the Kubernetes and container lifecycle securing both the CICD pipeline and production environments. It provides image scanning, ML based run-time protection, and forensics to identify vulnerabilities, enforce compliance, and block threats across your microservices.
Sysdig
Homepage: https://sysdig.com/
License: Open source, commercial products built on top of the free technology.
Use Cases: Anomalous behaviour debugging, forensics.
Sysdig is a full-system exploration, troubleshooting and debugging tool for Linux systems. It records all system calls made by any process, allowing system administrators to debug the operating system or any processes running on it.
Sysdig has a command line interface with a syntax similar to tcpdump and a ncurses interface to visually navigate and filter through the events, in a similar fashion to htop or wireshark. The system call capture files allows you to perform forensics on your containers even if they are long gone.
Tenable Flawcheck
License: Commercial.
Use Cases: Pre-production analysis, vulnerability newsfeed.
Tenable, the company perhaps best know for Nessus, the security scanner, acquired Flawcheck, a specific container-focused security solution.
FlawCheck, like other commercial tools in this list, stores container images and scans them as they're built, before they can reach production. FlawCheck leverages Tenable/Nessus know-how and database of vulnerabilities, malware and intrusion vectors and adapts it to containerized and agile CI/CD environments.
Twistlock
License: Commercial.
Use Cases: Pre-production analysis, runtime protection, compliance & audit, etc.
Twistlock advertises itself as a cloud-first, container-first platform, providing specific integrations with cloud providers (AWS, Azure, GCP), container orchestrators (Kubernetes, Mesospehere, Openshift, Docker), serverless runtimes, mesh frameworks (like Istio) and CI/CD tools.
Apart from the usual container security features like CI/CD pipeline integration, compliance with container security protocols or image scanning, Twistlock uses machine-learning techniques to generate behavioural patterns and container-aware network rules.
Conclusion
Choosing the right Docker security tool depends on your specific needs, environment, and security goals. Whether you opt for an open-source project or a commercial solution, understanding the features and use cases of each tool will help you make an informed decision. A secure containerized infrastructure starts with the right tools—take the time to evaluate what aligns best with your requirements.

Top 5 use cases for securing cloud and containers
Keep your containers safe, while keeping up with the speed of innovation.
%201.svg)


