
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

\rWelcome to another iteration of What's New in Sysdig in 2022! Before starting, once again Happy Easter, Happy Passover, Happy Rama Navami, and Ramadan Mubarak! In general, happy spring break, and we hope you recovered from the chocolate egg drop.\r
\r
\rThis month, I have the pleasure of writing the "What's new in Sysdig" blog! Hi, I'm Balaji Thirunavukkarasu, a Sales Engineer based out of the San Francisco Bay Area and a part of the Sysdig US West Enterprise team. My journey into the software industry started as a Support Engineer, then forayed into Technical account management and recently transitioned to Sales. My areas of interest have always been around distributed systems, cloud computing, Security, and OSS tools. On a personal front, I love to spend time with my kids, play professional cricket, golf with friends, and mountain bike.\r
\r
\rContinuing with the usability improvements with new navigation from previous months, we are excited to announce a few additional features and improvements to the Sysdig Platform, which we will highlight below.\r
\r\r\r
Sysdig Monitor
\r\r\r
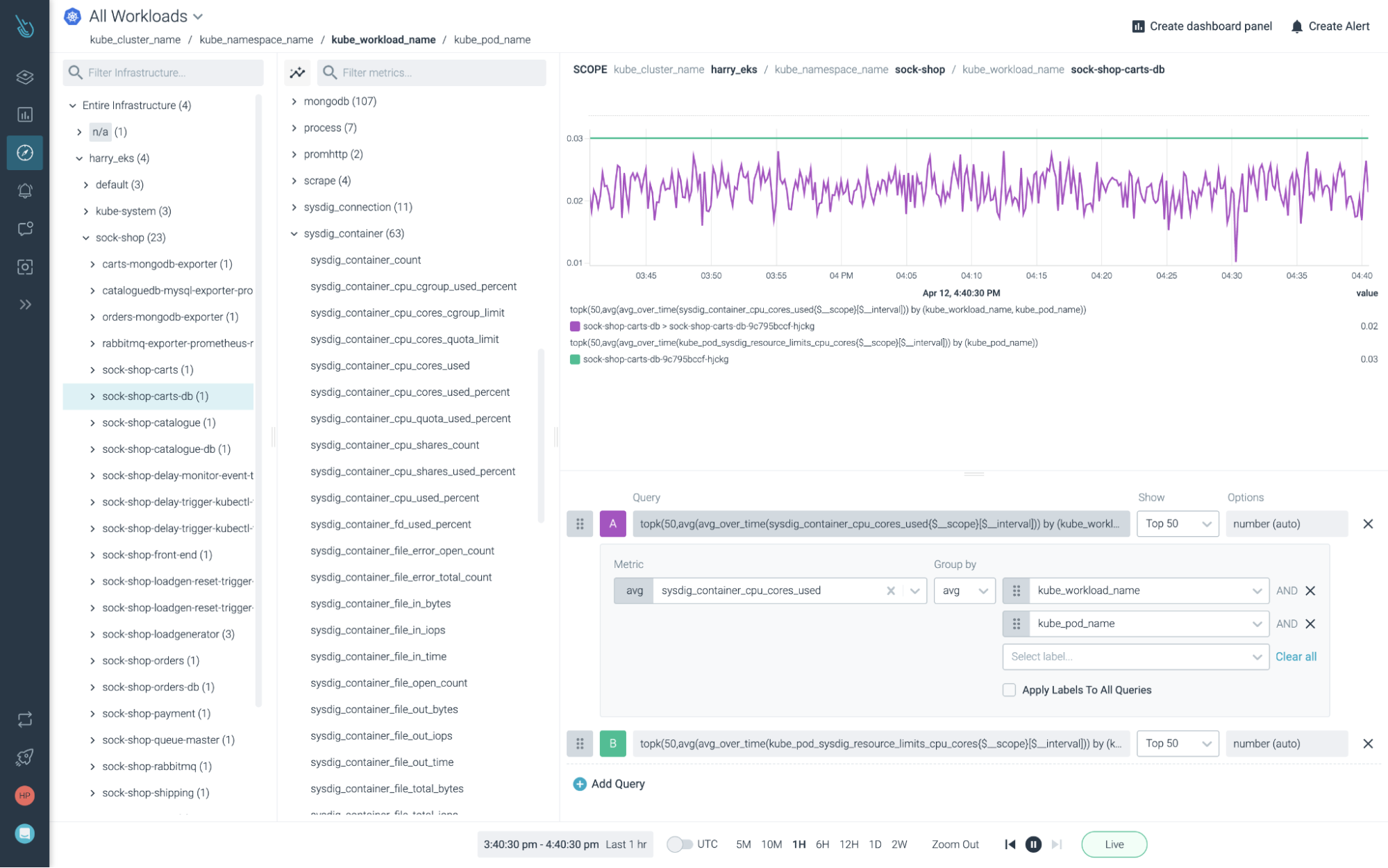
Metrics Explorer
\r
\rMetrics Explorer has been rebuilt from the ground up to focus on advanced metric exploration and querying.\r
\r
\r
\r
\r
\rImprovements to Metrics Explorer include:\r
\r
- \r
- Simple querying that builds PromQL queries under the hood. Metrics Explorer is the easiest way to build PromQL queries.\r
- Graph multiple metrics at once for correlation. For example, CPU usage vs. Kubernetes limits.\r
- Queries are ungrouped by default, showing the individual time series for a metric. This allows you to spot problems faster. For example, one of 50 Cassandra nodes with high pending compactions. Instead of segmenting, you now group by one or more labels. For example,
workload,podandcontainer.\r - When selecting a scope in the tree, only those metrics that are applicable to that entity are displayed.\r
- Metrics are now more logically categorized by metric namespace (prefix).\r
- Resolution has been improved. For example a one-hour view now shows 10 seconds of data. Additionally, the concept of time realignment has been removed.\r \r
\r
\rFor more information, see Explorer.\r
\r
\rAs always, please go check out our own Release Notes for more details on product updates, and ping your local Sysdig contact if you have questions about anything covered here.\r
\r\r\r
Sysdig Secure
\r\r\r
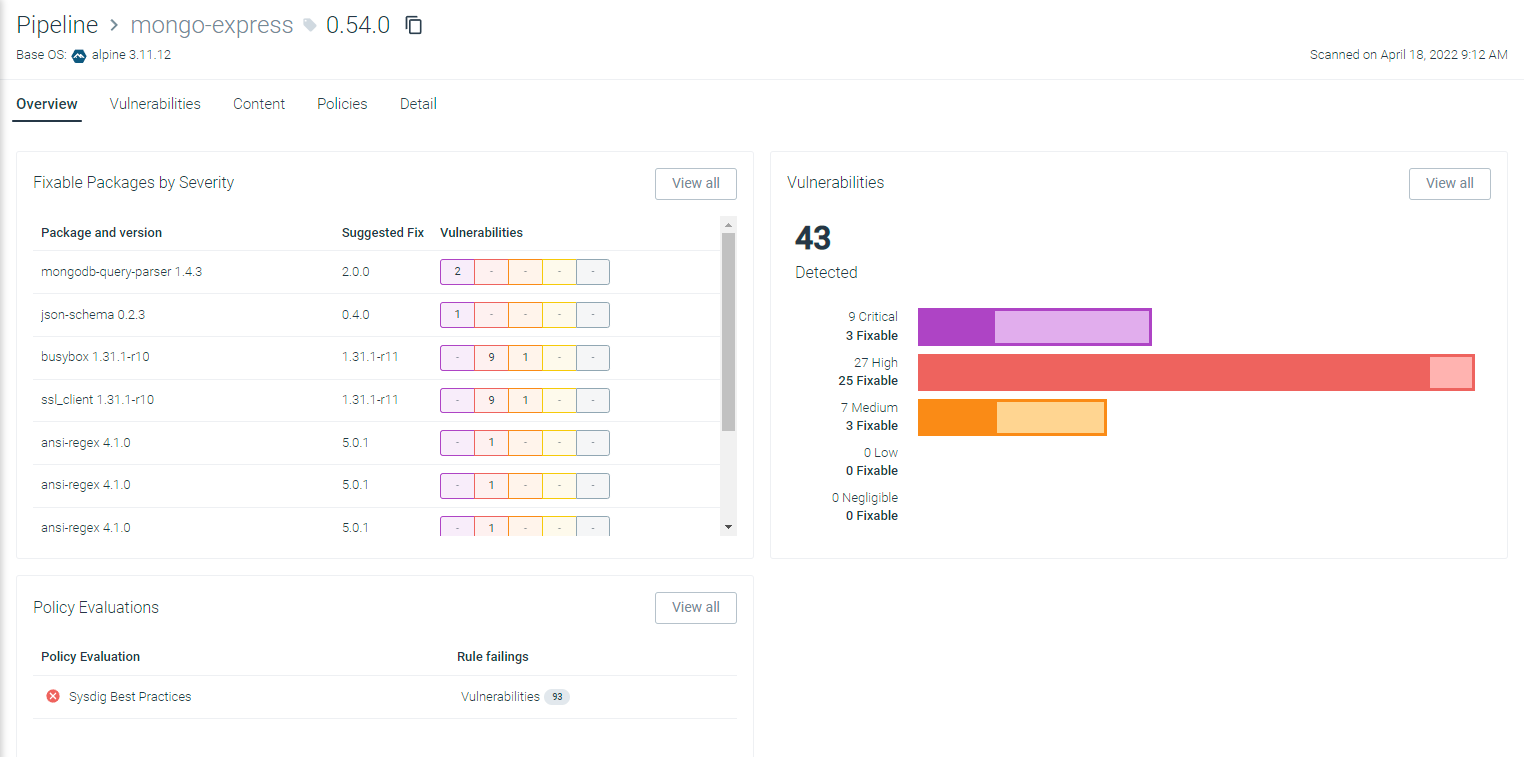
New Image Scanning Engine
\r
\rThis month, we are announcing the release of our new image scanning engine! The new scanning engine is developed 100% in-house and provides super fast scanning capabilities. Complete with a new UI, The new scanning engine makes it easy to prioritize vulnerabilities and focus on what matters most.\r
\r
\r
\r
\r
\rFor now, both the old scanning engine and the new one are available. To enable the new scanning engine, navigate to Settings->Sysdig Labs and enable "New Vulnerabilities engine" to start using it.\r
\r\r\r
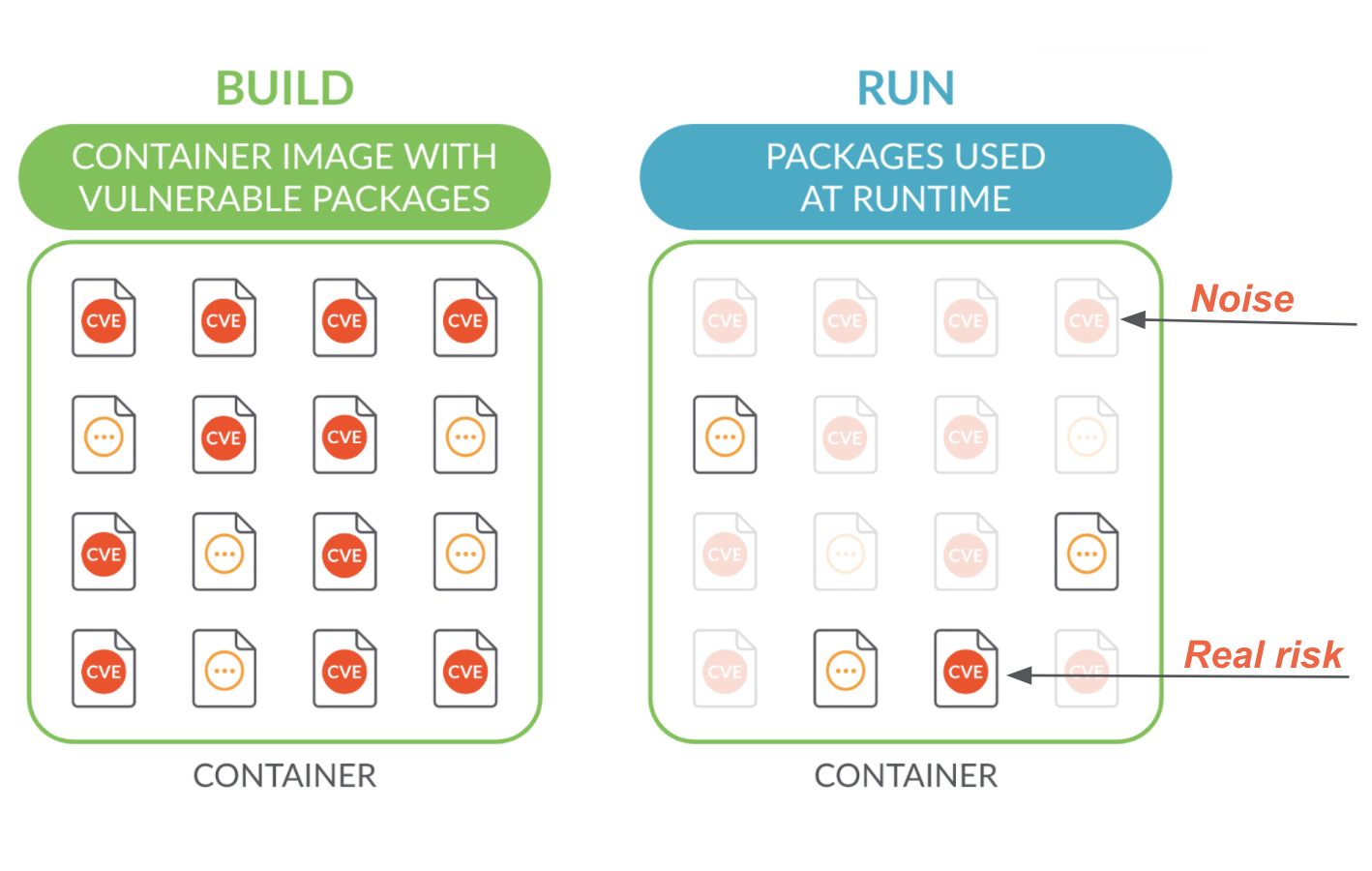
Announcing Risk Spotlight
\r
\rEliminate noise and prioritize the vulnerabilities that really matter with Risk Spotlight. Most of the vulnerabilities reported in container environments are actually noise. Containers are loaded with packages that are never used. Risk spotlight focuses on vulnerabilities in packages that are active at runtime, allowing you to focus on what matters.\r
\r
\r
\r
\r
\rKey Benefits of Risk Spotlight\r
\r
- \r
- Reduce vulnerability noise by up to 95%. Risk Spotlight eliminates the noise from vulnerabilities that pose no immediate risk by identifying the packages not used at runtime.\r
- Manage risk with actionable insights. Risk Spotlight delivers rich vulnerability details – such as the CVSS vector from multiple sources, the fix version, and link to publicly available exploits – and a package-centric view that facilitates remediation and managing vulnerability risk at scale.\r
- Comprehensive vulnerability management for containers from source to run. Risk Spotlight provides a single view of vulnerability risk across the container lifecycle, from build to runtime. Developers can take immediate actions to mitigate the few vulnerabilities that pose real risks and also apply security best practices early by removing unused packages during the build process.\r \r
\r
\rRead all about Risk Spotlight in the blog post Eliminate noise and prioritize the vulnerabilities that really matter with Risk Spotlight.\r
\r\r\r
Falco Rules
\r
\rv0.63.0 is the latest version. Here there are some highlights of the changes from v0.50.5, which we covered in January.\r
\r
\rAdded the following rules:\r
\r
- \r
- Modify ld.so.preload\r
- Polkit Local Privilege Escalation Vulnerability(CVE-2021-4034)\r
- Privileged Shell Spawned Inside Container\r
- Debugfs Launched in Privileged Container\r
- Mount Launched in Privileged Container\r
- Unprivileged Delegation of Page Faults Handling to a Userspace Process\r
- Launch Ingress Remote File Copy Tools in Container\r
- Suspicious Cron Modification\r \r
\r
\rFurther details and the full changelog can be found on Sysdig documentation.\r
\r\r\r
Sysdig Agents
\r
\rThe latest Sysdig Agent release is v12.4.0. Below is a diff of updates since v12.3.1, which we covered in our last update.\r
\r
- \r
- Support for New Architectures: ARM (aarch64) and s390x (zLinux)\r
- Custom-Metrics-Only Mode\r
- Prevent Processing Policy Updates\r \r
\r
\rPlease refer to our v12.4.0 Release Notes for further details.\r
\r\r\r
SDK, CLI, and Tools
\r\r\r
Sysdig CLI
\r
\rv0.7.14 is still the latest release (Download Link). The instructions on how to use the tool and the release notes from previous versions are available at the following link:\r
\r
\rhttps://sysdiglabs.github.io/sysdig-platform-cli/\r
\r\r\r
Python SDK
\r
\rv0.16.3 is still the latest release, which we covered in our October update.\r
\r
\rhttps://github.com/sysdiglabs/sysdig-sdk-python/releases/tag/v0.16.3\r
\r\r\r
Terraform Provider
\r
\rv0.5.37 is the newest release.\r
\r
\rDocumentation – https://registry.terraform.io/providers/sysdiglabs/sysdig/latest/docs\r
\r
\rGithub link – https://github.com/sysdiglabs/terraform-provider-sysdig\r
\r\r\r
Terraform Modules
\r
\rAWS Sysdig Secure for Cloud: v0.8.2\r
\r
\rGCP Sysdig Secure for Cloud: v0.8.5\r
\r
\rAzure Sysdig Secure for Cloud: v0.8.0\r
\r
- \r
- Note: Azure Sysdig Secure for Cloud includes a breaking change to align to the new v3.0 version of the AzureRM Provider\r \r
\r\r\r
Falco VS Code Extension
\r
\rv0.1.0 is still the latest release.\r
\r
\rhttps://github.com/sysdiglabs/vscode-falco/releases/tag/v0.1.0\r
\r\r\r
Sysdig Cloud Connector
\r
\rSysdig Cloud Connector has been updated to v0.16.7.\r
\r
\rFeatures include:\r
\r
- \r
- Restore segment tracking using customer ID instead of random UUID\r
- List last images from ECR, EKS, and Lambda\r \r
\r
\rCheck the full list of changes to get the full details.\r
\r
\rAdmission Controller\r
\r
\rSysdig Admission Controller has been updated to v3.9.1.\r
\r
\rDocumentation – https://docs.sysdig.com/en/docs/installation/admission-controller-installation/\r
\r\r\r
Runtime Vulnerability Scanner
\r\r\r
The new vuln-runtime-scanner has been released to GA state with v1.0.0.
\r
\rDocumentation – https://docs.sysdig.com/en/docs/sysdig-secure/vulnerabilities/runtime\r
\r\r\r
Sysdig CLI Scanner
\r\r\r
Sysdig CLI Scanner has been released to v1.0.0.
\r
\rDocumentation – https://docs.sysdig.com/en/docs/sysdig-secure/vulnerabilities/pipeline/\r
\r\r\r
Image Analyzer
\r\r\r
Sysdig Image analyzer is still set to v0.1.16.
\r\r\r
Host Analyzer
\r
\rSysdig Host Analyzer is still set to v0.1.6.\r
\r
\rDocumentation – https://docs.sysdig.com/en/docs/installation/node-analyzer-multi-feature-installation/#node-analyzer-multi-feature-installation\r
\r\r\r
Sysdig Secure Inline Scan for Github Actions
\r
\rv3.2.0 is still the latest release, which we covered in our November edition.\r
\r
\rhttps://github.com/marketplace/actions/sysdig-secure-inline-scan\r
\r\r\r
Sysdig Secure Jenkins Plugin
\r
\rv2.1.12 is still the latest release.\r
\r
\rhttps://plugins.jenkins.io/sysdig-secure/\r
\r\r\r
Prometheus Integrations
\r
\r Integrations:\r
\r
- \r
- feat: Updated helm charts with new exporters image tags for security updates\r
- fix: Optimized Portworx metrics in Prometheus job\r
- fix: Added label kube_namespace_name correctly to kubelet PVC metrics\r
- feat: Updated the exporter image tags in the helm charts\r\r Dashboards and alerts:\r\r
- \r
- feat: Added Kubernetes scope to troubleshooting dashboard templates\r
- feat: Deprecated the legacy troubleshooting dashboard templates for MongoDB and SQL\r
- fix: Removed non-useful disks from 'Kubernetes Node Status & Performance' dashboard\r
- fix: Added filter to exclude containers FS in 'File System Usage & Performance' dashboard template. Also added cluster scope and changed table panel position.\r \r
\r
\r
\rExporter images\r
\r
- \r
- Security updates in UBI images of the following exporters:\r
- \r
- JMX:\r
- \r
- quay.io/sysdig/promcat-jmx-exporter:v0.16.5-ubi\r
- quay.io/sysdig/promcat-jmx-exporter:v0.16.5\r \r
- MySQL:\r
- \r
- quay.io/repository/sysdig/mysql-exporter:v0.13.4-ubi\r
- quay.io/repository/sysdig/mysql-exporter:v0.13.4\r \r
- Memcached:\r
- \r
- quay.io/repository/sysdig/memcached-exporter:v0.9.2-ubi\r
- quay.io/repository/sysdig/memcached-exporter:v0.9.2\r \r
- Nginx:\r
- \r
- quay.io/repository/sysdig/nginx-exporter:v0.9.3-ubi\r
- quay.io/repository/sysdig/nginx-exporter:v0.9.3\r \r
- MongoDB:\r
- \r
- quay.io/repository/sysdig/mongodb-exporter:v0.11.6-ubi\r
- quay.io/repository/sysdig/mongodb-exporter:v0.11.6\r \r
- ElasticSearch:\r
- \r
- quay.io/repository/sysdig/elasticsearch-exporter:v1.3.2-ubi\r
- quay.io/repository/sysdig/elasticsearch-exporter:v1.3.2\r \r
- PostgreSQL:\r
- \r
- quay.io/repository/sysdig/postgresql-exporter:v0.10.6-ubi\r
- quay.io/repository/sysdig/postgresql-exporter:v0.10.6\r \r
- Apache:\r
- \r
- quay.io/repository/sysdig/apache-exporter:v0.10.5-ubi\r
- quay.io/repository/sysdig/apache-exporter:v0.10.5\r \r
- Redis\r
- \r
- quay.io/repository/sysdig/redis-exporter:v1.31.6-ubi\r
- quay.io/repository/sysdig/redis-exporter:v1.31.6\r \r
\r
\r - JMX:\r
\r\r\r
Sysdig On-Premise
\r
\rThe 5.1.0 On-Premise minor release is now official. Here are some highlights for this minor release:\r
\r
- \r
- Added support for Kubernetes versions 1.22 and 1.23\r
- Added a pre-flight check to verify the kubectl and K8s versions of the cluster with the context provided by the customer\r
- API documentation for Sysdig Secure is now enabled by default\r
- Feature Enhancement: Falco Exceptions – Create Exception Objects to a Default Rule\r
- Various bug fixes\r \r
\r
\rThe full release notes can be found here: Sysdig Docs or Github\r
\r\r\r
New Website Resources
\r\r\r
Blogs
\r
- \r
- Preventing cloud and container vulnerabilities\r
- Are vulnerability scores misleading you? Understanding CVSS severity and using them effectively\r
- Eliminate noise and prioritize the vulnerabilities that really matter with Risk Spotlight\r
- Sysdig achieves AWS DevSecOps specialization within AWS DevOps Competency\r
- Understanding Kubernetes pod pending problems\r
- Kubernetes 1.24 – What's new?\r
- Understanding cloud security\r
- Adopting Docs-as-Code: From Hackathon to Production\r
- Critical Vulnerability in Spring Core: CVE-2022-22965 a.k.a. Spring4Shell\r
- Detecting and Mitigating CVE-2022-22963: Spring Cloud RCE Vulnerability\r
- Digital Forensics Basics: A Practical Guide for Kubernetes DFIR\r
- Detect malicious activity in Okta logs with Falco and Sysdig okta-analyzer\r
- How to be prepared for Cyber Warfare Attacks\r \r
\r\r\r
Webinars
\r
- \r
- Say Goodbye to PSPs?! Migrate your PSP Rules to OPA with No Hassle\r
- Cloud and Container Runtime Security on Azure\r
- How to Prepare for the Next Log4j\r
- Protecting Against Log4j Attacks in AWS Fargate\r
- Continuous Compliance on Azure \r
- CSPM Best Practices for Multi-Cloud: Beyond Native Tools\r
- Become a Certified K8s Security Specialist (CKS) in 2022! How to Pass with Saiyam Pathak, CNCF Ambassador\r
- Containerized AppSec from Code to Production w/ Snyk, Sysdig and AWS\r
- Reduce Alerts and False Positives – Monitor Golden Signals using Sysdig\r \r
\r\r\r
Tradeshows
\r
- \r
- MARCH 1-MAY 20, Cloud Security Demo Forum, Virtual\r
- APRIL-AUGUST, AWS Summit, Americas\r
- APRIL-MAY, AWS Summit, Europe, Middle East, Africa\r
- APRIL 27 – 29, On: The Beach, Malaga, Spain\r
- MAY 10, Dockercon, Virtual\r
- MAY 10-11, Red Hat Summit, Virtual\r
- MAY 16, Cloud Native eBPF DAY, Valencia, Spain\r
- MAY 16-17, Cloud Native SecurityCon, Valencia, Spain\r
- MAY 17, Prometheus Day Europe, Valencia, Spain\r
- MAY 17-20, KubeCon, Valencia Spain\r \r
\r
\rEducation\r
\r


