Welcome to the first update of the year on what’s new from Sysdig. Before starting, once again, Happy New Year, Voorspoedige nuwe jaar, Buon anno, Gelukkig nieuwjaar, عام سعيد, bon any nou, godt nytår, bonne année, Frohes neues Jahr, שנה טובה, あけまして おめでとう ございます, laimīgu Jauno gadu, szczęśliwego nowego roku, Mutlu yıllar, С Новым Годом and Feliz año nuevo!
As you already know, the “What’s new in Sysdig” blog team is involving more and more people, and this month is up to me, Giulio Puri. I’m based in Milan, Italy, and I’ve been part of the Sysdig EMEA team since May, 2021 as a Sales Engineer. I’m passionate about technology, innovation and cybersecurity, and in my free time, I love to cook, experiment with recipes and – not always successfully – surprise my friends with new dishes.
I want to start this monthly post with the recent news that thrilled all of us Sysdiggers: Wireshark creator, Gerald Combs, joined the Sysdig team to extend the open-source project for cloud security! If you want to read more about this exciting news, here is the link to the announcement from Sysdig CTO and Founder, Loris Degioanni.
Product-wise, I’m happy to mention some important achievements in Sysdig Secure: Rapid Response, a new tool to further support the investigation and analysis of security events; IaC Security, a first milestone in the integration of additional capability to further support the identification of potential posture issues; New Scanning Policies/Rule Bundles, which extend the Vulnerability Management Tech Preview with more security scan workflows. More details can be found below, as well as all the updates about our blogs, webinars, and tradeshows.
As always, please go check out our own Release Notes for more details on product updates, and ping your local Sysdig contact if you have questions about anything covered here.
Sysdig Secure
Welcome Infrastructure-as-Code!
The new feature allows you to integrate Kubernetes IaC checks into your Git pipeline. With just a few clicks, the standard compliance checks will be integrated into the Pull Request (PR) flow and alert developers when they create violations of the policy before they merge.
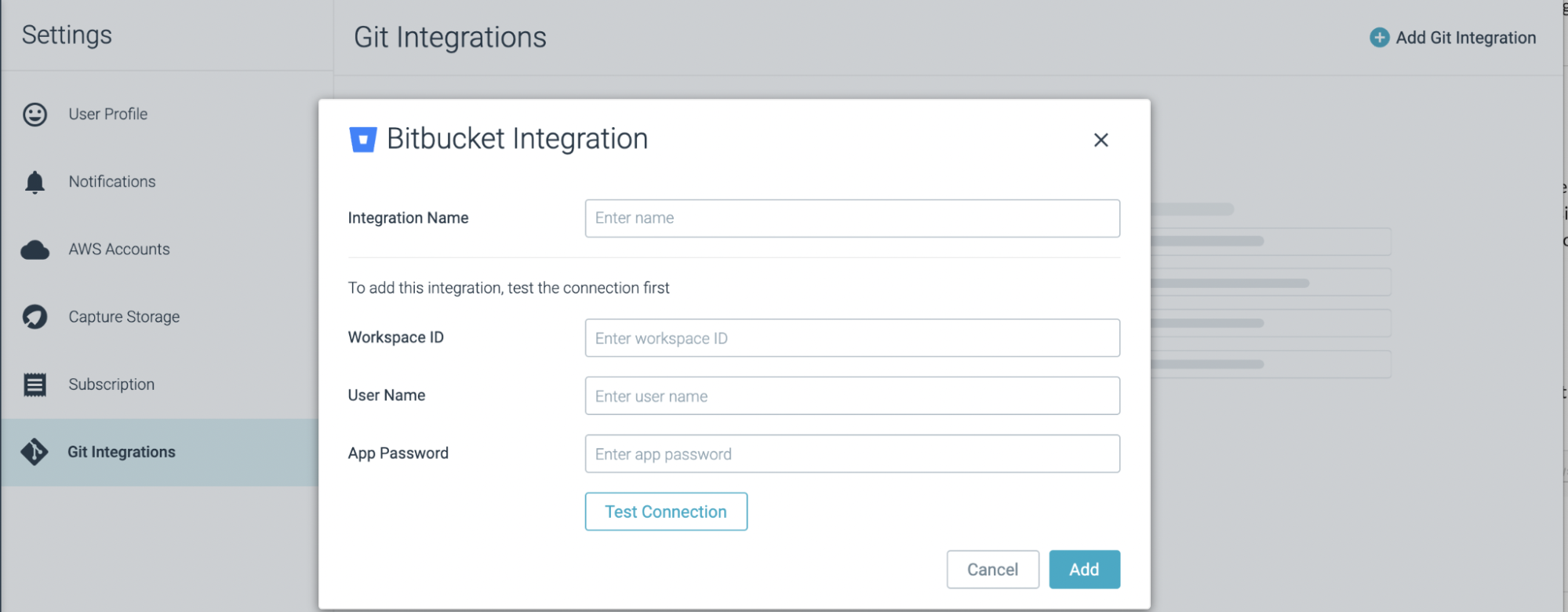
Sysdig currently supports Github, Bitbucket, GitLab, and Azure DevOps integrations, and for each provider you can define the repos and folders to protect, as well as branches on which to perform the evaluation.
For more details, please refer to the IaC Security documentation page
Rapid Response
With Rapid Response, Sysdig has introduced a way to grant designated Advanced Users in Sysdig Secure the ability to remotely connect into a host directly from the Event stream, and execute desired commands there.
Finding the team or developer responsible for an application in a cloud or Kubernetes environment can take hours or days. Troubleshooting a live issue or security event may require faster investigation to lower the MTTR of these events.
Rapid Response allows security teams to connect to a remote shell within your environment to start troubleshooting and investigating an event using the commands they are already accustomed to, with the flexibility they need to run the security tools at their disposal, directly from the event alert.
Vulnerability Management Tech Preview (not for production!)
Following the Sysdig new Scanning Engine preview release, we’re happy to announce the availability of the new iteration of Scanning Policies and Rule Bundles as a tech preview (not for production yet).
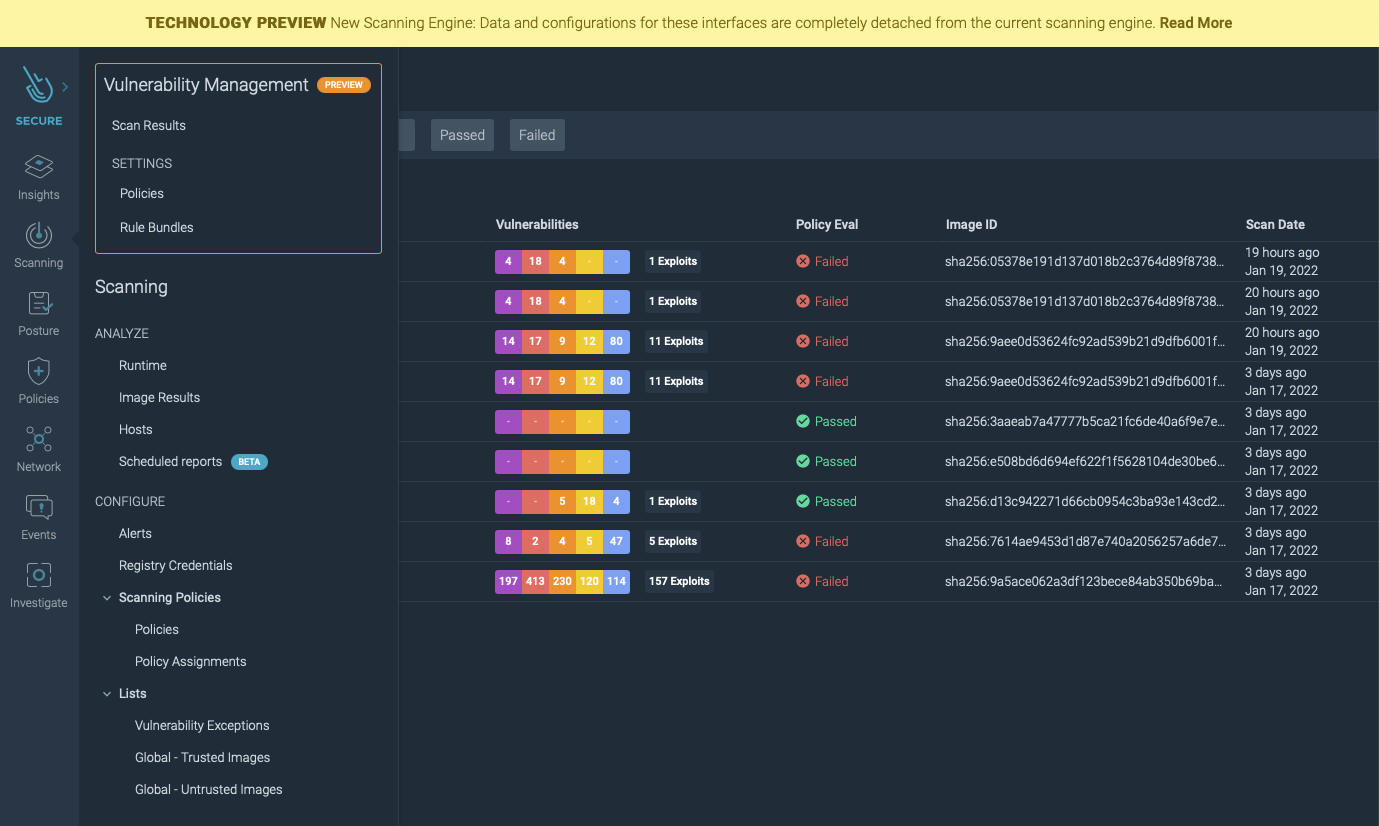
Sysdig is developing a new scanning engine with major improvements and additional features. Some of the features offered with the first iteration of the new engine are:
- Provides faster scan times when analyzing an image from the CI/CD pipeline or your developer machine.
- Offers more advanced and accurate vulnerability data and CVSS vector scoring from different vendors and exploitability metrics.
- Features improved and more intuitive user experience.
The new engine is currently under development, but it can be enabled already as a preview.
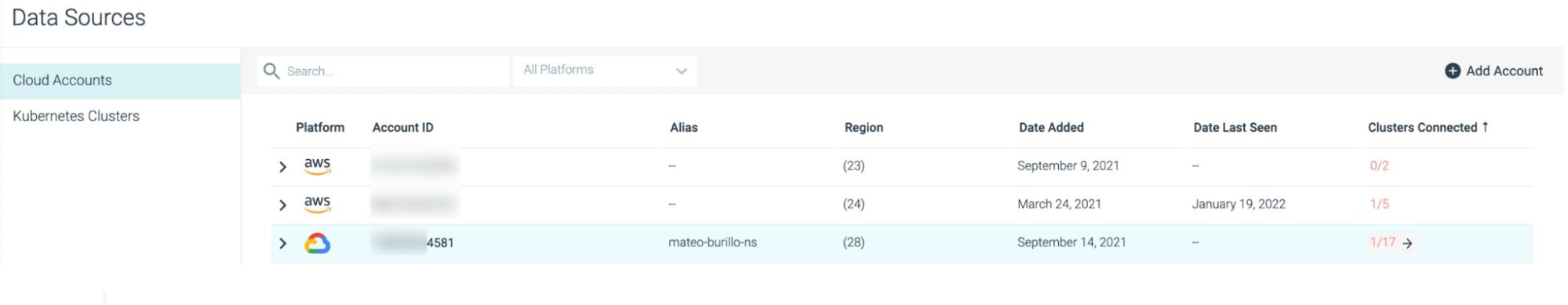
New Data Source Page
We are excited to announce the release of the updated Data Sources page for the cloud! This page gives a consolidated view into the Cloud Accounts that have been onboarded with Sysdig Secure, as well as displaying information about the Managed Kubernetes Clusters (EKS, GKE & AKS) in each of their connected Cloud Accounts.
Unified Compliance Reporting
We are pleased to announce a rework of our Compliance and Benchmarking capabilities. This change brings a number of improvements:
- Compliance and Benchmark tasks are now scheduled, managed, and generate reports in an updated and unified interface, including simpler pathways to remediation and easier-to-navigate reports.
- The logic used to check individual controls now checks for events signaling control failures, and ensures the correct Runtime rules are configured to detect these events. This leads to a more comprehensive audit that captures activity as well as configuration.
- New compliance standards and platforms were added:
- For workload, AWS, GCP, and Azure: NIST 800-82 Rev2
- For workload and AWS: Fedramp, HITRUST CSF 9.4.2
- For GCP and Azure: GDPR, HIPAA, ISO 27001:2003, NIST 800-53 Rev4 and Rev5, NIST 800-171, NIST 800-190, PCI / DSS v3.2.1 and SOC 2
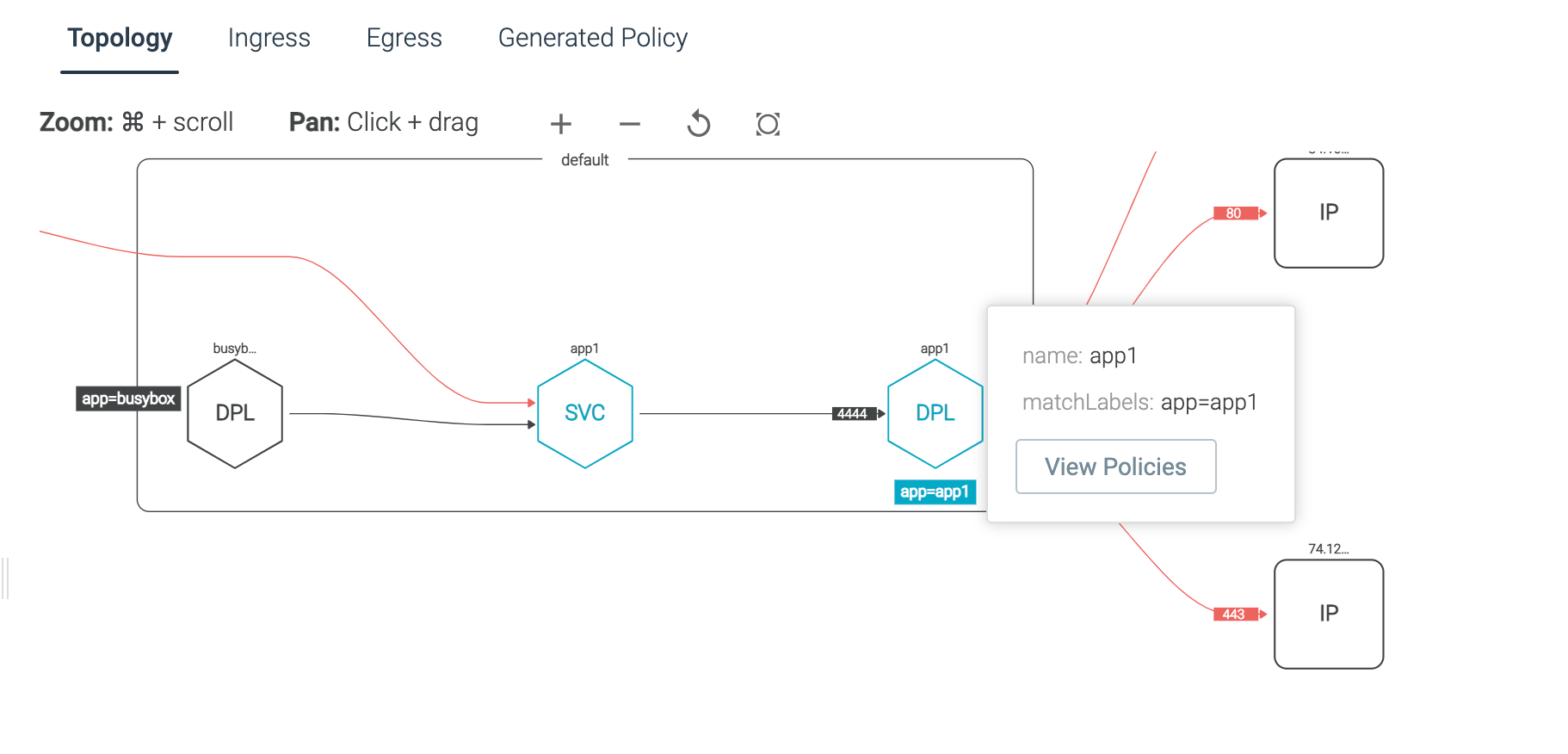
New Feature: Review Applied Kubernetes Network Policies
Sysdig Secure has added the ability to view the KNPs that have been applied directly from the Network Security Policy UI.
Falco Rules
v0.50.5 is the latest version. Here there are some highlights of the changes from v0.36.0, which we covered in September.
Added the following rules:
- Malicious C2 IPs or domains exploiting log4j: detect connections with malicious IPs involved in log4j exploitation
- Read Object through AWSSupportServiceRolePolicy Assumed Role
- Find AWS Credentials: Find or grep AWS credentials in host or container
- GCP Create Cloud Function
- Azure Remember MFA for User Access on Devices
- Azure Users Can Consent to Apps Accessing Company Data on Their Behalf
- Azure Deactivate MFA for User Access
- Azure Container ACL Modified
- Create Lambda Function Using Unsupported Runtime
- Malicious IPs or domains detected on the command line
- Malicious binary detected
- Malicious process detected
Further details and the full changelog can be found on Sysdig documentation.
Sysdig Agents
The latest Sysdig Agent release is v12.2.0 Below is a diff of updates since v12.1.1, which we covered in our last update.
- Improve Install Script to Support eBPF: A new option, bpf or -b is added to the native install script of Sysdig agent to support eBPF.
- Enable 10s Flush Configuration by Default: By default, the agent aggregates 1-second metrics to 10-second data before sending it to the backend. If you want to use agent versions 12.2.0 or above with the on-prem Sysdig Platform versions below 3.5.0, set the 10s_flush_enable config to false.
- Improved Log Messages: Improved the log messages to report the errors encountered while configuring subprocess_resource_limits.
SDK, CLI and Tools
Sysdig CLI
v0.7.14 is still the latest release. The instructions on how to use the tool and the release notes from previous versions are available at the following link:
Python SDK
v0.16.3 is still the latest release, which we covered in our October update.
Terraform Provider
The terraform provider has been updated and the latest version is v0.5.28.
Bug Fix
- Change terraform deploys to create compliance v2 task instead of benchmarks v2 task
Falco VS Code Extension
v0.1.0 is still the latest release.
Sysdig Cloud Connector
Sysdig Cloud Connector has been updated to v0.14.2 from v0.13.0 since last month.
New Features
- auditor: Publish cloudsec events to /events endpoint for assumed role calculations
- secure-client: Update feature enabler to use HeartBeats
- Allow user to specify concurrentDownloads from S3 on CloudTrail ingestors
- Expose a metric for SQS message consumption
- Add a rule to check Read Object through AWSSupportServiceRolePolicy Assumed Role
- Performance improvements
- Azure bruteforce login detection
Check the full list of changes to get the full details.
Inline Scanner & Image Analyzer
Both Sysdig Inline Scanner and Node Image Analyzer have been updated since last month, respectively to v2.4.8 and v0.1.15.
Bug Fixes
- Updated to the latest security fixes
- Fixed support for COPY, USER and other instructions when the image is built using buildkit
Sysdig Secure Inline Scan for Github Actions
v3.2.0 is still the latest release, which we covered in our November edition.
Sysdig Secure Jenkins Plugin
v2.1.12 is still the latest release.
Prometheus Integrations
New Dashboards and Alerts
- Kubelet dashboard and alert templates
- New alert templates for storage and PVCs
- Add Nginx ingress alert for SSL certification expiration
- Add alerts for CPU and memory consumption under 15% of the request
- Update info banner for PVC dashboard
- Update ‘Pod Rightsizing & Workload Capacity Optimization’ Dashboard to add container granularity and suggested values text
- Fix interval in ‘Windows overview’ and ‘WMI Overview (legacy)
New Website Resources
Blogs
- Detecting and mitigating CVE-2021-4034: “Pwnkit” local privilege escalation
- Sysdig 2022 Cloud-Native Security and Usage Report: Stay on Top of Risks as You Scale
- CVE-2022-0185: Detecting and mitigating Linux Kernel vulnerability causing container escape
- Endpoint Detection and Response (EDR) for containers and Kubernetes
- Vulnerable AWS Lambda function – Initial access in cloud attacks
- Sysdig Welcomes Gerald and the Wireshark Community
- Malicious modifications to open source projects affecting thousands
- Secure DevOps on Microsoft Azure: Reduce Cloud & Container Risk
- How to Secure Kubernetes, the OS of the Cloud
- Pet surveillance with Falco – Home Security
- Monitor CSGO – Counter Strike: Global Offensive with Prometheus
- Blocking log4j with Response Actions
Webinars
- Continuous Compliance on AWS
- Securing Microsoft Azure Cloud and Containers
- Cloud and Container Runtime Security on AWS
- Zero Trust Security for OpenShift and Hybrid Cloud
- Image Scanning on AWS
- Secure DevOps Best Practices for Multicloud Environments
- Addressing the log4j Vulnerability in Containers
- Compliance with Containers & Cloud


