Welcome to another monthly update on what’s new from Sysdig! Happy Pride month! We hope you are celebrating safely, in whatever manner you choose. It’s been over 50 years since the Stonewall riots, but we continue to fight for equality and justice. Love is love, and we’re sending you all of ours! Thank you to Marsha P. Johnson, Brenda Howard, and countless others for fighting for the freedom that many of us today enjoy.

Our team continues to work hard to bring great new features to all of our customers, automatically and for free! This month, there were a lot of user experience improvements. Two of my favorites are:
- Falco Policy Tuner – Although currently released in beta, I already love it! We’ve had the manual policy tuner available in the background for some time, but now this can automatically tune noisy rules and false positives, as well as make use of the exceptions syntax which makes it a lot simpler to maintain.
- More Prometheus! I’m cheating and there’s actually two great new features here: PromQL Library and Prometheus Remote Write. We’ll go into more details below, but we continue working hard to make life easier for our customers using Prometheus.
As always, please go check out our own Release Notes for more details on product updates, and ping your local Sysdig contact if you have questions about anything covered in here.
Sysdig Secure
CIS RedHat OpenShift Container Platform v4 Benchmark
Support for CIS RedHat OpenShift Container Platform v4 Benchmark has been added to Sysdig Secure.
As part of this release, Sysdig is allowing you to scan and validate compliance with 112 controls included in the CIS Bencmark requirements.
See the Compliance documentation for usage details and the controls implemented.
Sysdig Secure UX Improvements: “Investigate” Navigation & Activity Audit
Sysdig navigation just got a facelift. To help our Sysdig Secure users navigate easily, we:
- Added the new menu item Network (previously found under the Policies menu).
- Grouped Activity Audit + Captures into Investigation to better describe the use-case it helps users resolve.
Activity Audit
The Activity Audit module also got several interface and user experience improvements:
- Runtime scope moved to the top to align with other Secure interfaces and allow more space for activity data.
- Activity types (
network,file,kubectl,command) can now be filtered directly from the graph using the legend. - Attributes of the displayed elements can be filtered directly from the list, without displaying the side detail panel.

Kubernetes Network Security: New Configuration and Improved User Experience
Sysdig’s Kubernetes Network Policy tool has been updated to include additional fine-tuning configurations and an improved user experience.
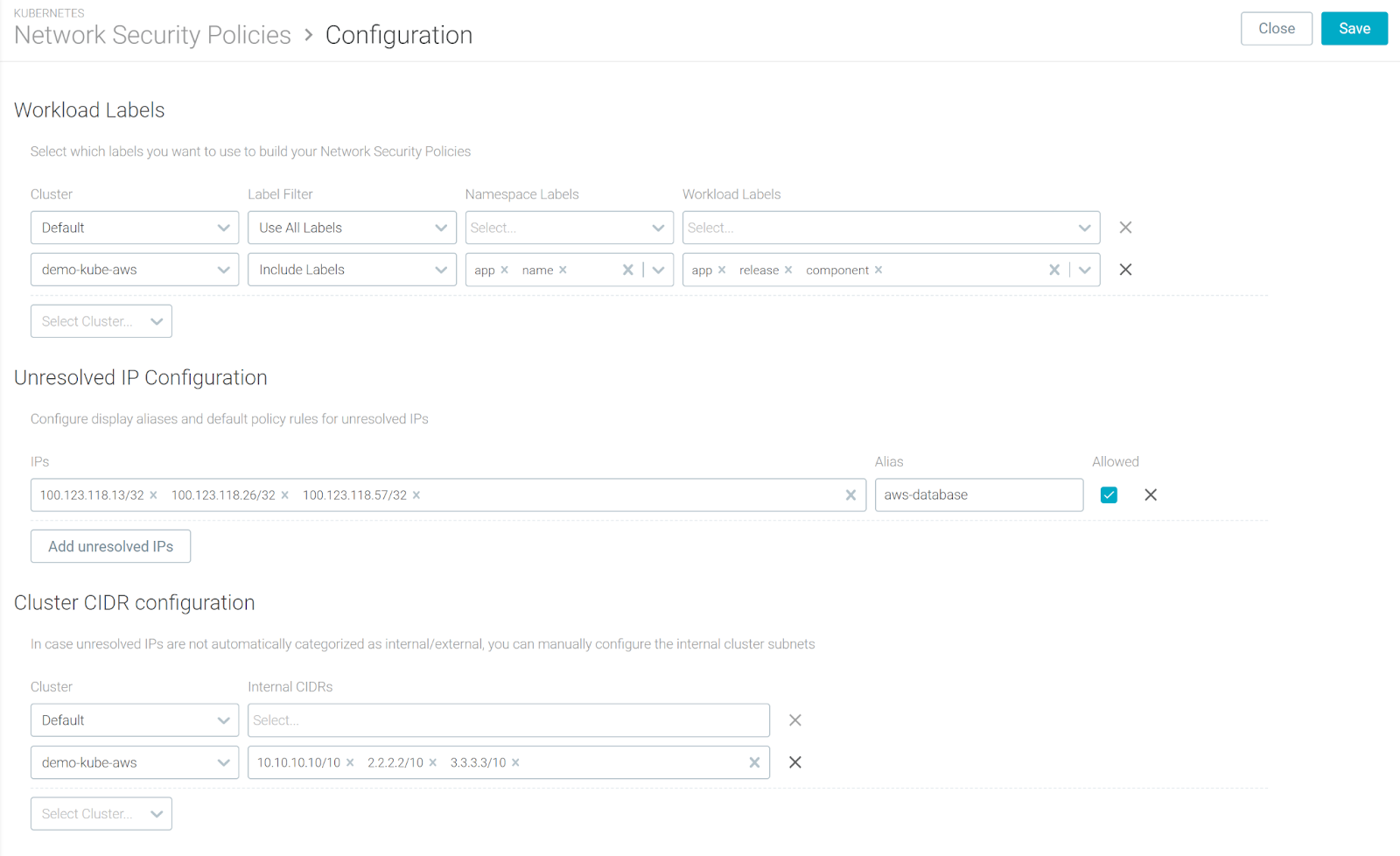
Additional Configuration Panel
- Workload Labels: Depending on your workload labeling policy, some labels may not be relevant for generating a KNP policy. Use the additional config to include/exclude a particular set of labels per cluster/namespace to declutter your UI and the resulting policy.
- Unresolved IP Configuration: Now, it is possible to label raw IPs that are not mapping to your Kubernetes/OpenShift entities (i.e. external cloud provider services), so these labels will be automatically applied to the topology and ingress / egress tables.
- Cluster CIDR configuration: If the CIDR configuration is not automatically detected by the agent, you can now directly configure internal subnets per cluster using the Sysdig interface.
Improved UX
- Topology map: Additional information pop-up when hovering over a network connection or a network node, such as server process, source, destination, and more.
- Unresolved IP filtering: In the ingress and egress tables, by type or using free text search.
Additionally, Network is now presented as a top-level item in the Sysdig Secure navigation.
Falco Policy Tuner – Beta
Sysdig is now releasing a managed version of the standalone Falco Tuner.
Previously, you had to run the tuner in your local environment, print suggestions, and manually update a rule with those suggestions. The new feature runs in the background and automatically tunes noisy rules and false positives. To streamline the creation of these exceptions, we’ve created a new object within Falco called exceptions.
Note: To enable the tuner, Admin access rights to Sysdig Secure are required.
Feature Enhancement: Falco Exceptions
Previously, exceptions were created using and not conditions inside a Falco rule. For example:
- rule: Write below binary dir
...
condition: >
bin_dir and evt.dir = < and open_write
and not package_mgmt_procs
and not exe_running_docker_save
and not python_running_get_pip
and not python_running_ms_oms
and not user_known_write_below_binary_dir_activities
....
However, this process can be unwieldy and can result in unintended behavior. The new format, using exceptions, looks like this:
- rule: Write below binary dir
...
condition: bin_dir and evt.dir = < and open_write
....
exceptions:
- name: package_mgmt_procs
fields: proc.name
comps: in
values: package_mgmt_binaries # list of known binaries
...
See the full documentation here.
GCP Rules for Cloud Security
Earlier this month, we added a series of runtime security rules that feed off the Google Cloud Auditlogs. This aims to give parity to the experience our AWS customers get with CloudTrail integration. This integrates with Google Cloud Auditlogs and feeds audit data into Sysdig Runtime Security by using the Falco engine. We provide a set of default rules that use this audit feed from Google and are included as default in the runtime security rules.
Additionally, these are now also visualized in Secure Insights, so you can quickly see this activity, filter down to what’s important, and investigate any activity you need to.
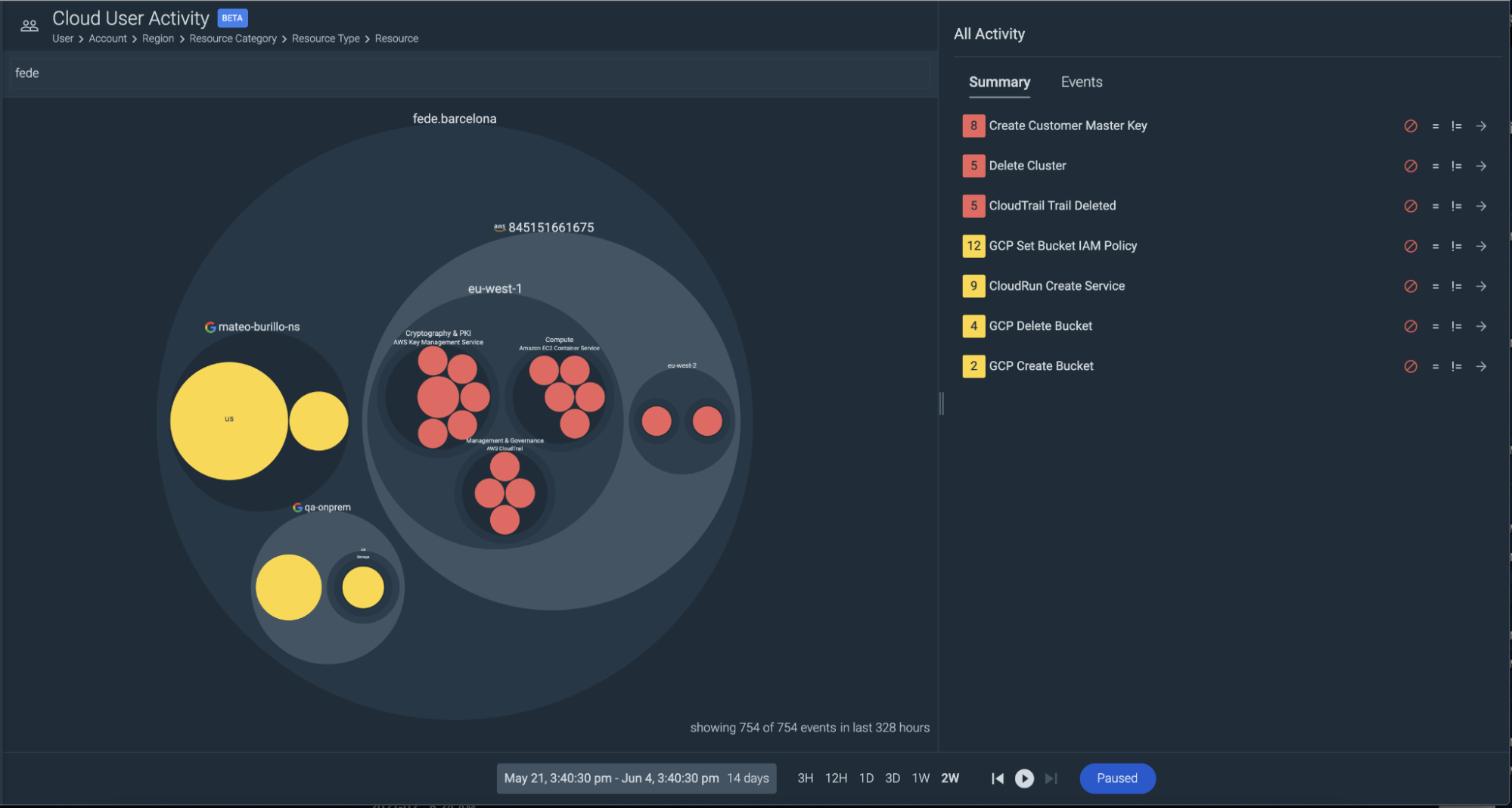
Falco Rules
v0.20.1 is the latest version. Below is a diff of changes from v0.16.0, which we covered last month.
Once again, there are a lot of changes and improvements during these versions as we continue to bring you more cloud security rules and improve our container security rules. This includes:
- Transforming more rules to use the
exceptionsformat to make them easier to read and modify. - Added additional `known good` processes to rules like
Read Sensitive File UntrustedandWrite below etcrule, such as clamscan (ClamAV), db2ckpw (IBM DB2 credential checker), Qualys binaries, New Relic processes, TaniumEndpoint, and macmnsvc (McAfee service host). - New AWS CloudTrail events rules.
Check the full scope of these updates on the Falco rules changelog.
Sysdig Monitor
PromQL Library
We have compiled a list of PromQL queries to give you one-click insights into the health and performance of your infrastructure. The library also includes a PromQL 101 category to give you hands-on exposure to PromQL. For more information, see PromQL Library.
Prometheus Remote Write
Sysdig supports ingesting metrics from Prometheus servers by using remote_write capabilities. In Sysdig terminology, the remote endpoints that can read Prometheus metrics are known as Prometheus Remote Write. Prometheus Remote Write does not require the Sysdig agent to be installed in the Prometheus environment. This facility expands Sysdig monitoring capability, beyond Kubernetes and regular Linux kernels, to environments where the Sysdig agent cannot be installed.
Dark Mode
The dark appearance, known as Dark Mode, is available in Sysdig applications.
Sysdig can now automatically match your OS preferences, available in the US East and rolling out globally. For more information, see Configure Theme Preference.
Improved Dashboard Templates
The following Dashboard templates have been enhanced to display the data better, return improved results, and add golden signals.
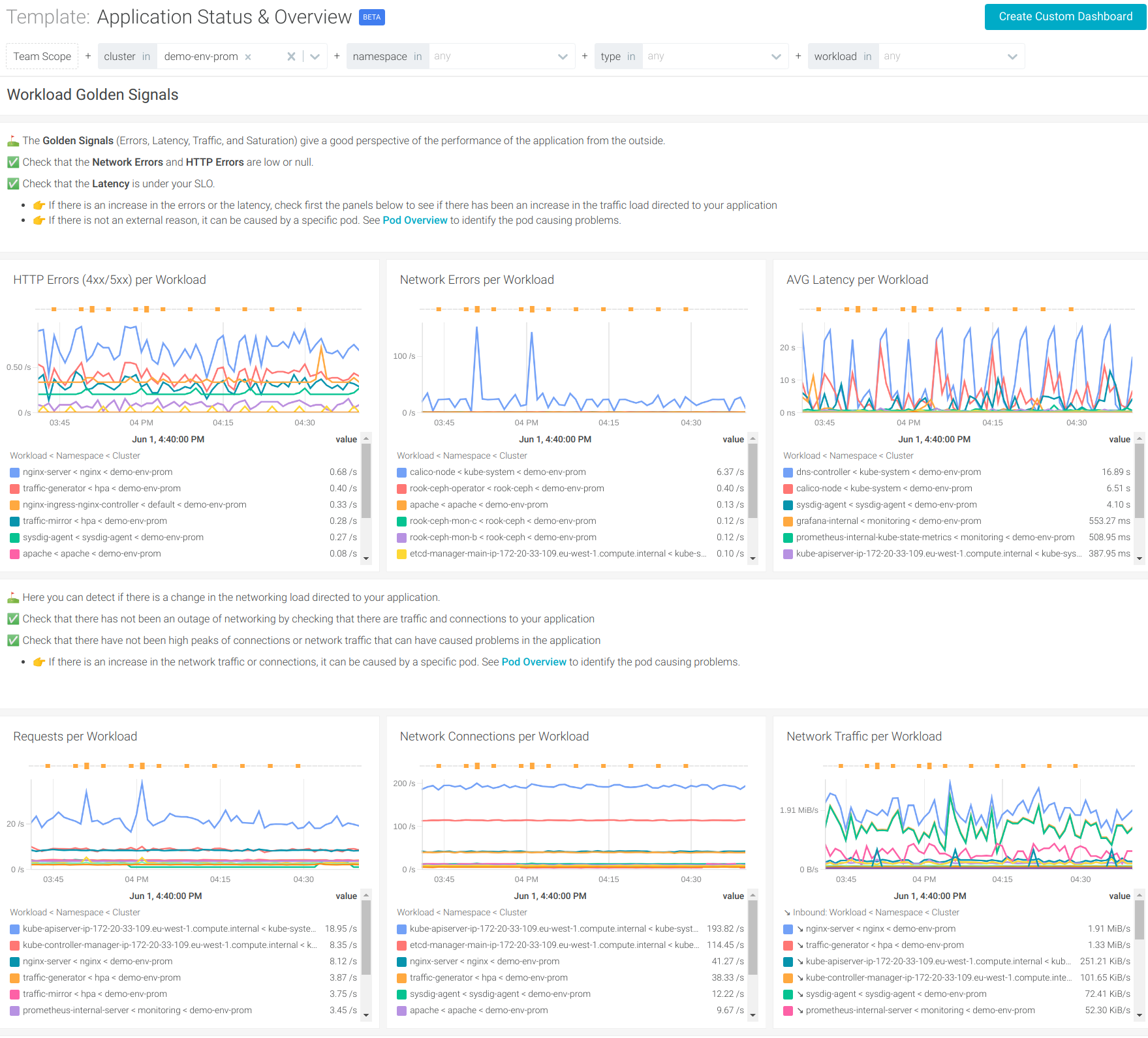
- Kubernetes
- Application
- Ngnix
- Ceph
- Ngnix Ingress
- ElasticSearch
- Redis
Sysdig Agents
Sysdig Agent
The latest Sysdig Agent release is 11.3.0. Below is a diff of updates since 11.2.1, which we covered in our last update.
In addition to the following improvements, the Sysdig Agent can also now be installed in AWS ECS Anywhere!
Feature Enhancements
- Console Logging: Introduced per-component-level console logging feature. See Manage Console Logging for Agent Components.
- Replication Controller Fields: Added missing replication controller fields to the aggregator Actions.
- Non-Delegated Agents Retrieve Less Data From the API Server: Use Kubernetes leases to better control the load on the Kubernetes API Server. This is disabled by default.
Defect Fixes
- Support Container Action on Containerd: Container actions are now properly supported on
containerd(CRI-O and other CRI engines that already had support). Actions for unsupported container engines are now properly reported to the Sysdig backend, and a warning message is logged in the agent logs. - Recovery During Agent Shutdown: Introduced a detection and recovery mechanism for hangs during agent shutdown.
- Promscrape V2 Termination No Longer Causes Agent Crash: Fixed a problem causing the agent to crash after
promscrape_v2is terminated. - Agent No Longer Restarts in Kubernetes Environment: The agent tries to fetch the metadata of the AWS instance in which it is running in order to tag metrics generated with the information unique to the AWS instance. If the metadata structure is not as expected, the agent continuously restarts due to an error in fetching such metadata. This issue has been fixed.
- Profiling Works as Expected: Fixed an issue that disabled support for performance profiles in the agent.
- Slim Agent for eBPF Probes:
agent-kmoduleandagent-kmodule-thincan now be used to build eBPF probes.
Sysdig Serverless Agent
Sysdig Serverless Agent is still on the latest release of 1.0.1, which we covered in our last update.
Sysdig Agent – Helm Chart
The Helm Chart 1.12.7 is the latest version. Below is a diff of updates since v1.12.1, which we covered in our last update.
- Updated agent to 11.3.0.
- Included get/list/create/update/watch leases in agent clusterrole permissions.
- Fixed
collector_endpointin configmap for image-analyzer. - If
nodeImageAnalyzer.settings.collectorEndpointis set, deploy old NIA to prevent onboarding instructions from older Sysdig Secure versions from failing. - eBPF with Agent slim image did not work on GKE (Google COS).
- Node analyzer configuration options not being honored due to invalid Configmap name.
- Fixed hostBase for Host Analyzer.
- Fixed Respect
existingAccessKeySecretindaemonset-node-analyzer.yaml. - Updated documentation links.
- Supported eBPF with Agent slim image.
Node Analyzer
Version 0.1.12 is still the latest release, which we covered in our last update.
Node image analyzer can be installed as part of the Sysdig Agent install.
Inline Scanning Engine
v2.4.2 is the latest release. Below is a diff of updates since v2.4.1, which we covered in our last update.
- Fixed bug when inspecting signed images.
See also: Integrate with CI/CD Tools.
SDK, CLI and Tools
Sysdig CLI
v0.7.11 is the latest release of the Sysdig CLI. Below is a diff of updates since v0.7.10, which we covered in our last update.
- Added –ignore-sharing-settings flag to dashboard add-json endpoint.
- Added extra HTTP headers support in config.
- Do not force all client tokens for simple section backups.
Python SDK
v0.16.1 is the latest release. Below is a diff of updates since v0.16.0, which we covered in our last update.
- Retry Policy: Solved deprecation warning on retry policy.
- Teams: Propagated old values for
defaultTeamRoleandentryPoint.
Terraform Provider
v0.5.14 is still the latest release, which we covered last month:
Falco VS Code Extension
v0.1.0 is still the latest release.
Sysdig Cloud Connector
v0.7.8 of the Sysdig Cloud Connector was released, we covered v0.7.1 last month.
Here are some highlights of the diff between these two versions:
New Features
- Added new rules for Azure and storage.
- Showed event dump when error accessing a field.
- New HTTP/PubSub ingestor for GCP. Can be configured as
gcp-pubsub-auditlog-httpin the config file. - Use
gcp.*fields in GCP rules. - Made notifications processing async.
- Improved pipeline throughput using buffered channels.
- Added Activity Audit for Secure integration for K8s Audit Events.
- Added Azure EventHub Ingestor.
- Added AWS App Runner rule to detect service deployment.
- Changed logger level to Error while parsing.
Bug Fixes
- Don’t rely on
requestObjectkind when parsing k8s events. - Always send
kubectl execevents as soon as they are received. - Fixed GCP rule over logical operator precedence.
- Don’t rely on rule name when notifying an activity audit.
- Removed
gcp_admin_rolesmacro for compatibility with Falco. - Check if the user exists before asserting on gcp rules.
- Use Gabs in k8s ingestor to avoid panics when parsing.
- Return only names on
ka.req.binding.subjects.
Check the full list of changes to get the full details.
Sysdig Secure Inline Scan for Github Actions
v3.0.2 is still the latest, which we covered last month:
Sysdig Secure Jenkins Plugin
v2.1.9 was released. Below is a diff of updates since v2.1.8, which we covered last month:
- Global option to override inline-scan container image.
- Global option for force inline scanning.
New Website Resources
Blogs
- Deploying Sysdig from the new AWS CloudFormation Public Registry
- Top 10 vulnerability assessment and management best practices
- Bad guys are watching for new openings in your cloud, are you?
- How to rightsize the Kubernetes resource limits
- Automated Falco rule tuning
- Securing containers on Amazon ECS Anywhere
- Top 10 PromQL examples for monitoring Kubernetes
- Securing the new AWS App Runner service
- Detecting and Mitigating CVE-2021-25737: EndpointSlice validation enables host network hijack


