Welcome to another monthly update on what’s new from Sysdig. Eid Mubarak! Our team continues to work hard to bring great new features to all of our customers, automatically and for free!
Most importantly, of course, was our recent funding round! I won’t repeat all the details as you can read more about what it means here. However, we are super excited about all the new feature improvements we can fund and bring to our customers!
May was a month of events, with KubeCon, SUSECON, and DockerCon virtual events all occurring. If you didn’t manage to make any of them, most of the recordings should be available online. A few personal highlights from KubeCon:
- Hacking into Kubernetes Security for Beginners
- We Didn’t Start the Fire: Communication Breakdowns and How to Prevent Them
- Shaping Kubernetes Community Culture
- Understanding Isolation Levels in the Kubernetes Landscape
- The CNCF Sandbox: An Exploration and Guided Tour
- FalcOMG That’s AWESOME
As always, please go check out our own Release Notes for more details on product updates https://docs.sysdig.com/en/release-notes.html, and ping your local Sysdig contact if you have questions about anything covered in here.
Sysdig Secure
Regulatory Compliance for ISO27001:2013 and HIPAA Now Available
Two new compliance standards have been added to Sysdig Secure’s compliance feature:
- ISO27001:2013
- HIPAA (Health Insurance Portability and Accountability Act)
See also: Compliance for information about the specific controls Sysdig covers for each security standard.
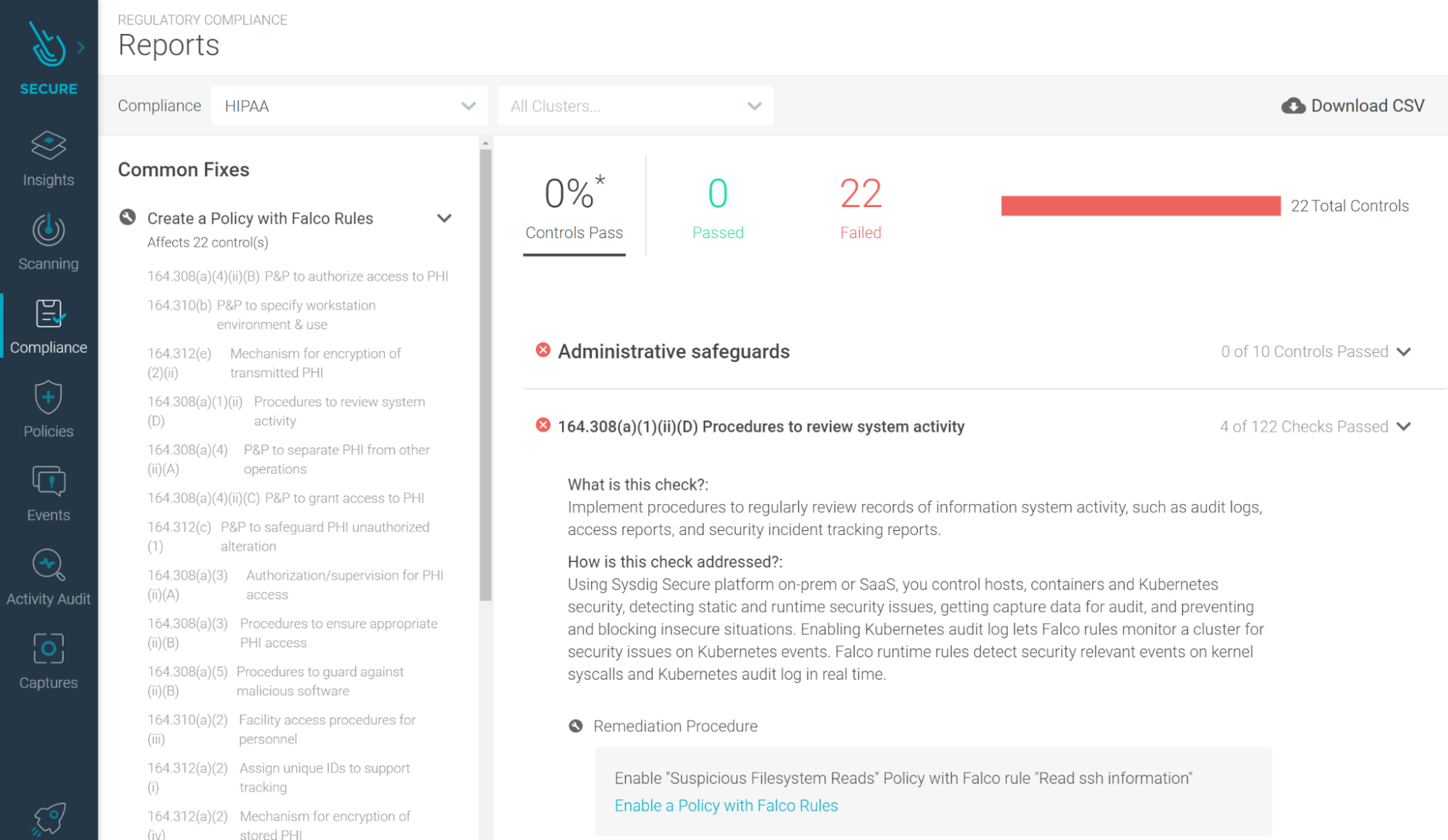
New and Improved Host OS and Container Scanning Tools
We, at Sysdig, are working hard to improve your security posture and compliance experience. As part of this commitment we are implementing a new framework to generate host benchmark results, introducing host scanning, and making backend improvements to the image scanning mechanism.
Installation Steps
The new features require a new component to be installed called the Node Analyzer. We’ve provided an installation script to automate the installation or to upgrade an existing Node Image Analyzer daemonset, if applicable.
Once you’ve installed or updated the components, the UI will automatically show Host Scanning and new Benchmarks functionality (Legacy Benchmarks can still be accessed).
Host Scanning: New
In addition to Sysdig Secure’s rich array of tools for scanning container images, you can now scan the hosts as well.
- Scan hosts for vulnerabilities, and detailed Software Bill of Materials (SBoM).
- Support for OS (e.g., rpm) and non-OS (e.g. ,Java, Ruby, Python) packages.
- Compare and diff scan results.
Host Benchmarks: Updated
- More checks.
- Better results.
- Clustered aggregations. Understand the posture of your environments, not just a single entity.
Image Scanning: Updated
- Automatically scan images if they have not been scanned.
Falco Rules
v0.16.0 is the latest version. Below is a diff of changes from v0.12.1, which we covered last month.
There have been a humongous number of changes during these versions. This includes:
- New rules like
Launch Root User Container. - Changes to existing ones, like
Detect outbound connections to common miner pool portsnow checks for additional known miner domains. - Additional exception fields added to many rules.
- Changes on macros that end up affecting many rules. Like
spawned_processnow only considering successful executables.
Check the full scope of these updates on the Falco rules changelog.
Sysdig Monitor
Silencing Alert Notifications
Sysdig Monitor allows you to silence alert notifications for a given scope for a predefined amount of time, and schedule silence in advance. When silenced, the alert will still be triggered and posted on the Events feed and in the graph overlays, but will indicate it has been silenced. The types of notification channels you can use are Email, Slack, and Amazon SNS.
You will be notified 30 minutes before the start time and 30 minutes before the end time of a silence window. You will also be able to easily extend or end an active silence. To access the feature, navigate to Alerts > Silence on the Monitor UI.
For more information, see Silence Alert Notifications.
Workload Label
Sysdig Monitor now supports two new labels, kubernetes.workload.name and kubernetes.workload.type, which can be used for scoping Dashboards and configuring Groupings.
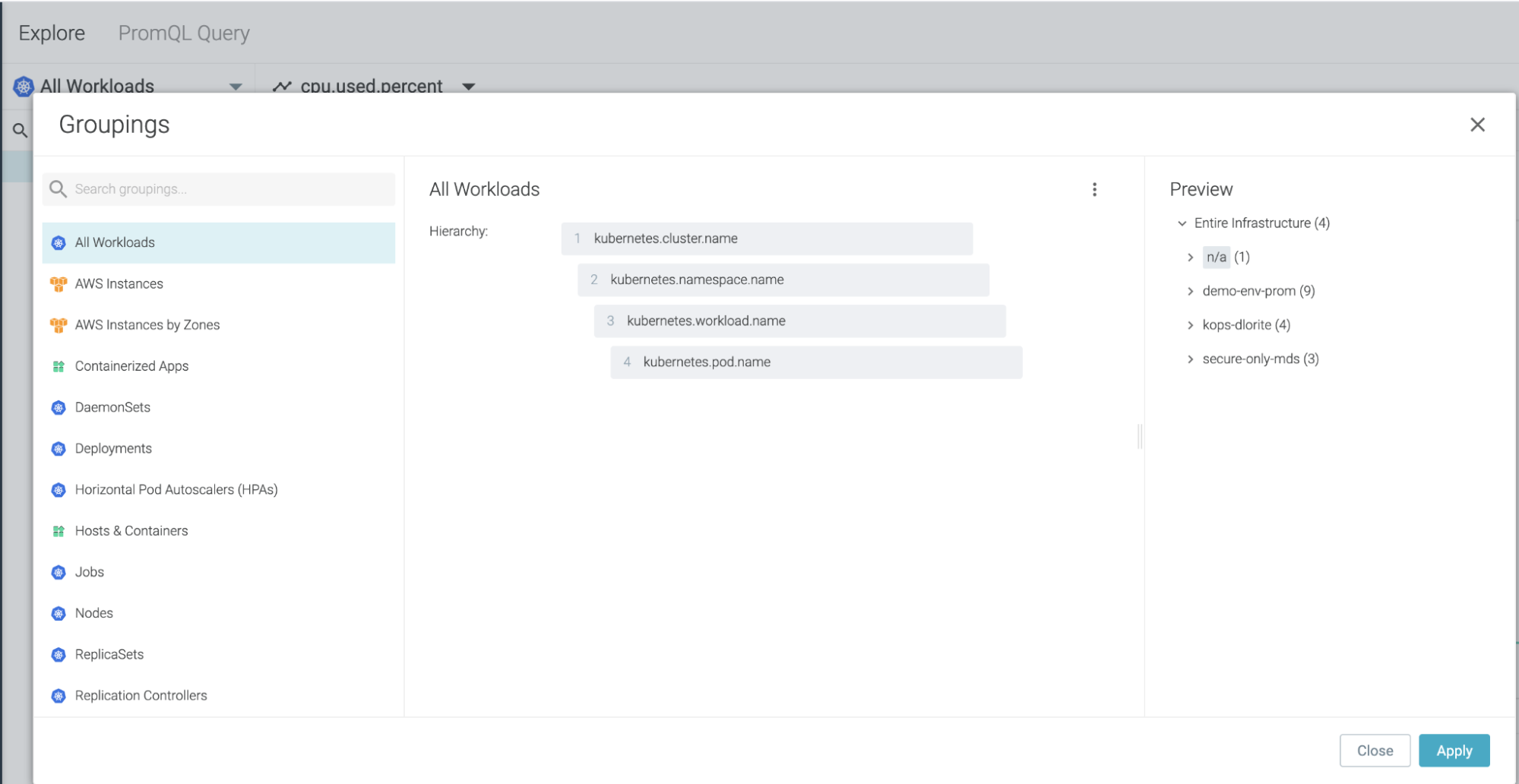
Earlier, each type of object (deployment, replicaset, statefulset, etc.) was unique. In turn, you needed to use different types of Kubernetes Dashboards and a different Grouping ,resulting in n/a , where distinct types of Kubernetes objects are listed.
For more information, see Unified Workload Labels.
New Kubernetes Dashboards
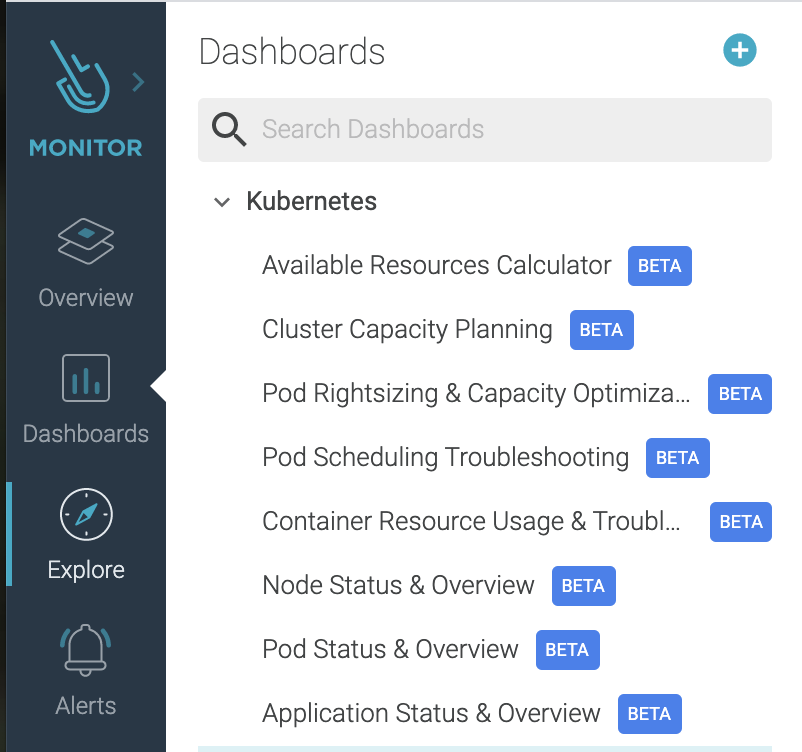
Available Resources Calculator. Ensure there is sufficient capacity in a cluster to deploy a new application.
Application Status & Overview. Understand the status of applications (workloads) running in a cluster by monitoring performance, pod health, and resource usage
Cluster Capacity Planning. Monitor the capacity of Kubernetes clusters ensuring they’re correctly sized to support new applications when they’re deployed.
Container Resource Usage & Troubleshooting. Understand the performance of the different containers running in pods across your infrastructure, and identify any that are behaving anomalously.
Node Status & Overview. Monitor the health, resource usage, and network statistics for nodes running in clusters.
Pod Rightsizing & Capacity Optimization. Optimize your infrastructure and better control cluster spend by ensuring pods are sized correctly. Understand if you can free up resources by reducing memory and/or CPU requests.
Pod Scheduling Troubleshooting. If a pod cannot be scheduled due to insufficient resources, use this dashboard to identify where the resource bottleneck is.
Pod Status & Overview. Monitor the health, resource usage, and network statistics for pods running as part of workloads.
Extended Label Set
Running PromQL queries is now smoother and faster with the extended label set. The extended label set is created by augmenting the incoming data with the rich metadata associated with your infrastructure and making it available in PromQL. You now no longer have to write complex queries in order to troubleshoot infrastructure issues or build dashboards and alerts. For more information, see Run PromQL Queries Faster with Extended Label Set.
Microsoft Team Channel
You can now use Microsoft Teams as a notification channel in Sysdig Monitor.
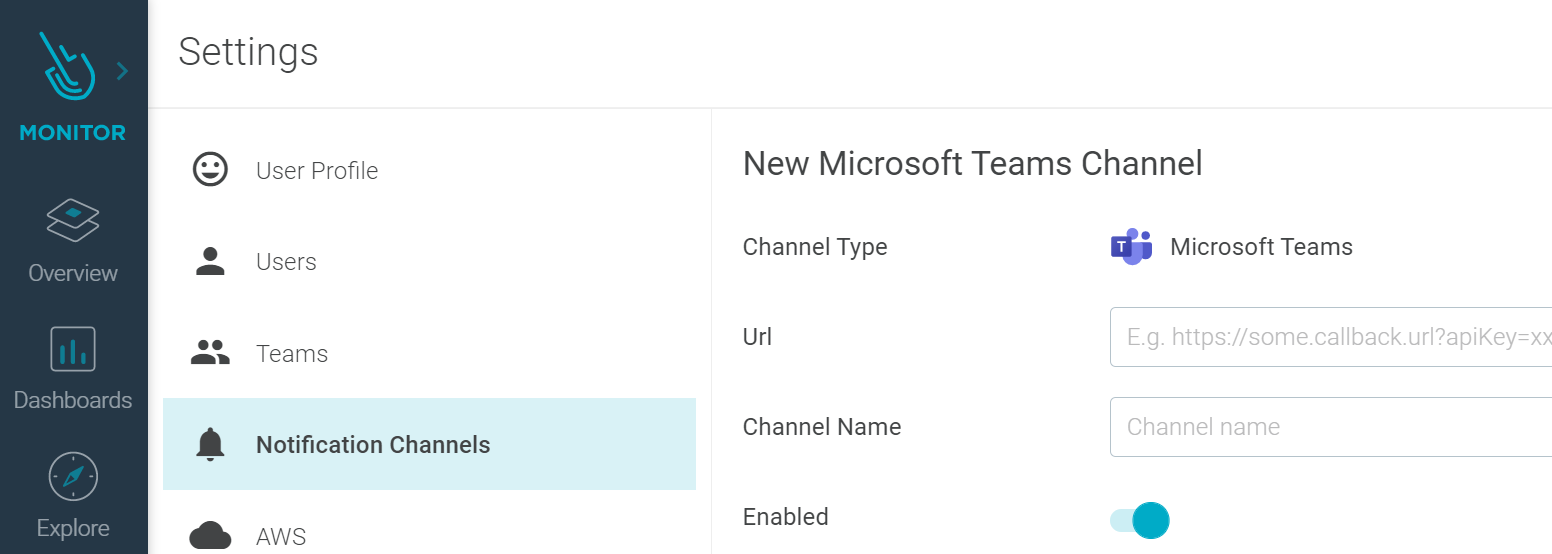
See Configure a Microsoft Teams Channel for more details.
S3-Compatible Storage for Capture Files for On-Premises
Configuring S3-compatible storage, such as Minio or IBM Cloud Object Storage, for your Sysdig captures is now supported on Sysdig Monitor. The capability can be turned on by configuring the system appropriately, as given in (SaaS) Configure Custom S3 Storage Endpoint.
Webhook Channel Enhancements
Sysdig supports the following on a Webhook channel integration:
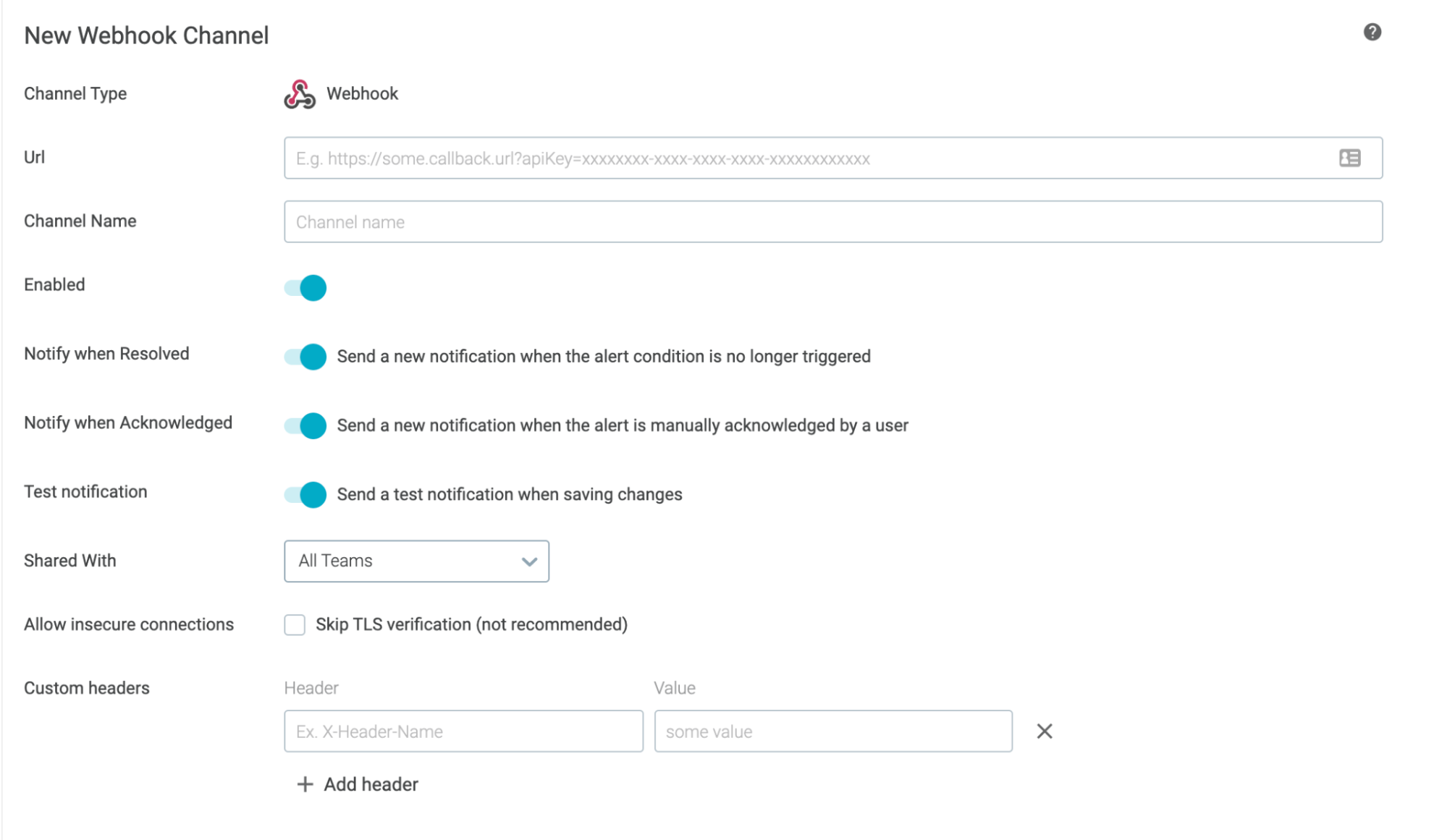
- Insecure connections: You now have the ability to skip the TLS verification.
- Custom headers: If your Webhook integrations require additional headers or data, you can append to the alert format by using a custom header on the UI. This option is in addition to the existing API facility to add custom headers programmatically.
For more information, see Configure a Webhook Channel.
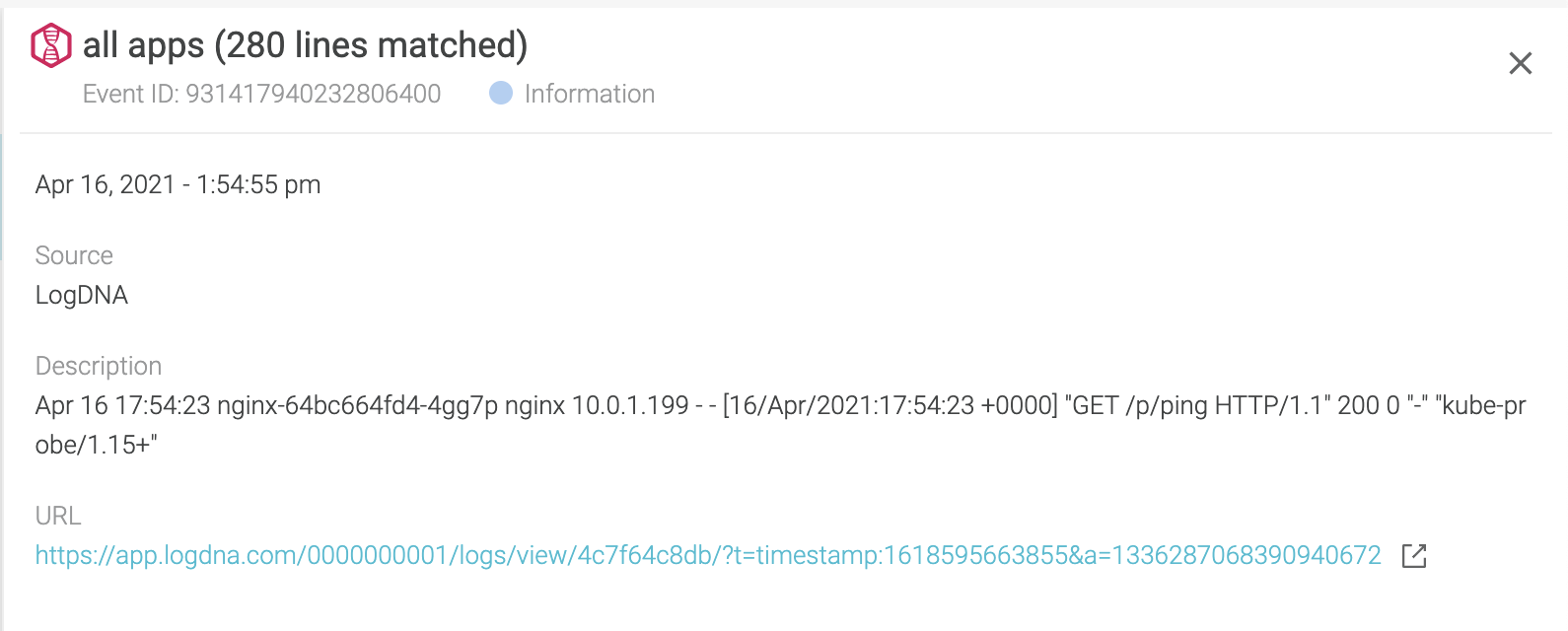
View LogDNA Alerts as Sysdig Events
If your environment has both LogDNA and Sysdig, you can view relevant LogDNA Alerts as Events in Sysdig. These Sysdig Events behave like any other type of Events in Sysdig. They will be overlaid on Sysdig graphs, listed in the Event Feed, and can be used to create an Alert in the Sysdig Platform. The link provided in the Event Details redirects you to the LogDNA Platform, in case further investigation is needed. For more information, see LogDNA Events.
Sysdig Agents
Sysdig Agent
The latest Sysdig Agent release is 11.2.1. Below is a diff of updates since 11.1.2, which we covered in our last update.
- Report Container User Information
- Start tracking container user information and make that information accessible in container events. These events denote having a container started. This feature works for Docker as well as CRI-O container engines.
- Reporting container user information does not work in OpenShift 4.x because it does not provide necessary CRI-O information.
- Agent Console
- Sysdig supports Agent CLI, a command-line interactive tool, to troubleshoot agents. This tool helps Sysdig support solve user issues quickly and efficiently. It is currently disabled by default and requires the customer to turn it on.
- For more information, see Using the Agent Console.
- Slim Agent for IKS
- For OCP, use the new daemonset for OCP.
- For IKS, the agent is installed by default using IKS Agent Script.
- Use the -af option to install the full agent.
- Reduce Load on Kubernetes API Server
- Terminated pods are no longer collected in order to reduce the load on the Kubernetes API server.
- Audit Server Listens on All Interfaces
- The audit server, now by default, listens on all the interfaces for Kubernetes audit events. This makes integration with Kubernetes audit events in the agent easier without the need for configuration changes.
- Improved Noise-Reduction Filter for Activity Audits
- The noise-reduction filter for Activity Audit has been improved. All the filtered data is duplicated.
- CRI-O Versions Report Correct Image ID
- The new CRI-O versions (1.19+, possibly 1.18) now properly report container.image.id.
- Log Level Changes for Duplicate Host Container Groups
- Demoted logs about duplicate host container_groups from warning to debug level
- Fix CVE-2021-28831
- Fix CVE-2021-28831 in the Slim Agent container.
Sysdig Serverless Agent
The latest Sysdig Serverless Agent release is 1.0.1. Below is a diff of updates since 1.0.0, which we covered in our last update.
- Segmentation Fault Error Fixed
- Fixed a problem that caused a segmentation fault error inside a Fargate task due to Sysdig instrumentation.
- Container Definition Fields Now Support Complex Values
- Added support for complex values inside Name and Image fields of the container definition. See also the ECS Task Definition docs from Amazon.
Sysdig Agent – Helm chart
The Helm Chart 1.12.1 is the latest version. Below is a diff of updates since v1.11.11, which we covered in our last update.
- Switched default registry from docker.io to quay.io.
- Updated Benchmark Runner to 1.0.6.0.
- Corrected error in Host Analyzer Configmap.
- Added Node Analyzer (nodeAnalyzer.deploy set to true by default).
- Explained all Node Analyzer settings in values.yaml and README, and link to official Sysdig docs.
- Disabled Node Image Analyzer deployment (nodeImageAnalyzer.deploy set to false by default).
- Updated agent to 11.2.1.
- Fixed nodeImageAnalyzer.extraVolumes.volumes not correctly creating the volumes.
- New option sysdig.existingAccessKeySecret to use existing or external secrets.
- Removed –name installation parameter for helm install in README.aws,
- Removed –name installation parameter for helm install in README, unsupported in Helm 3.x.
- Fixed in probes initialDelay.
Node image analyzer
Version 0.1.12 is still the latest release, which we covered in our last update.
Node image analyzer can be installed as part of the Sysdig Agent install: https://docs.sysdig.com/en/scan-running-images.html
Inline scanning engine
v2.4.1 is the latest release. Below is a diff of updates since v2.4.0, which we covered in our last update.
- Updated ClamAV 0.103.2.
See also: Integrate with CI/CD Tools.
SDK, CLI and Tools
Sysdig CLI
v0.7.10 is the latest release. Below is a diff of updates since v0.7.8, which we covered in our last update.
- Added more image contents to retrieve.
- Solved scanning image get returning error on format.
https://github.com/sysdiglabs/sysdig-platform-cli/releases/tag/v0.7.10
https://sysdiglabs.github.io/sysdig-platform-cli/
Python SDK
v0.16.0 is the latest release. Below is a diff of updates since v0.15.1, which we covered in our last update.
- SdScanningClient: Enhanced the
query_image_contentmethod to add support for more content types. - SdScanningClient: Added list all image tags method.
Terraform provider
v0.5.14 is still the latest release, which we covered last month:
Falco VS Code extension
v0.1.0 is still the latest release.
Sysdig Cloud Connector
v0.7.1 of the Sysdig Cloud Connector was released, the 7th version since we covered v0.6.4 last month.
There have been a lot of changes. Here are some highlights:
New Features
- Rules for Fargate.
- New AWS AppRunner rules.
- Added detailed scope information to GCP AuditLog events.
- A bunch of rules for GCP, including for GCP CIS Foundation.
- Upgraded to Falco rules for K8s to 0.28.0.
- Handled scope in evaluator and not in Secure notifier.
- Added pod exec / attach and private credentials configmap rules for Admission Controller.
Bug Fixes
- Don’t use
bucket.Attrsto check if a bucket exists. - Allow
JSONPointerescape characters and dash in output fields. - Binaries in
/bindon’t work in GCP Cloud Run. - Correct output with slash between fields.
- Avoid panic if the command does not exist.
- Add targetName as
ka.resp.namewhen is a pod. - Enhance compatibility with the
inoperator. - Honor
ECS_DEPLOYEDenvironment variable (type).
Check the full list of changes to get the full details.
Sysdig Secure inline scan for Github Actions
v3.0.2 was released. Below is a diff of updates since v3.0.0, which we covered last month:
- Added inline-scan-image option to override inline-scan image.
- Fixed output with inline-scan container 2.3.
- Fixed a problem creating the check run annotations when there are more than 50 annotations.
Sysdig Secure Jenkins plugin
v2.1.8 was released. Below is a diff of updates since v2.1.7, which we covered last month:
- Fix: Honor buildOnFail parameter.
PromCat.io
- Added MySQL
- Fixed CoreDNS
- Updated Cassandra
- Added GLP v3 to Sysdig generated resources
- Updated Agent configurations to Promscrape V2
- General review of documentation
New website resources
Blogs
- Securing the new AWS App Runner service
- Detecting and Mitigating CVE-2021-25737: EndpointSlice validation enables host network hijack
- Top 10 metrics in PostgreSQL monitoring with Prometheus
- See your logs and metrics together with LogDNA and Sysdig integration
- PromCon Online 2021 highlights
- Kubernetes capacity planning: How to rightsize your cluster
- Digging into AWS Fargate runtime security approaches: Beyond ptrace and LD_PRELOAD
- Unravel the hidden mysteries of your cluster with the new Kubernetes Dashboards
- Securing AWS Fargate workloads: Meeting File Integrity Monitoring (FIM) requirements
- How to monitor Microsoft SQL Server with Prometheus
- Easier and faster PromQL queries with ServiceVision for Prometheus
- Our $188M funding round fuels our mission to help customers confidently run modern cloud applications
- Exploiting and detecting CVE-2021-25735: Kubernetes validating admission webhook bypass
- Monitoring Ceph health with Prometheus
- How to detect EC2 Serial Console enabled
- Mitigating CVE-2021-20291: DoS affecting CRI-O and Podman
- Top 5 key metrics for monitoring Amazon RDS
- Unveil hidden malicious processes with Falco in cloud-native environments
Webinars
- Managing Hybrid Container Workloads with ECS/ECS Anywhere
- May 25, 2021 12pm Pacific | 3pm Eastern
- Take the CKS Exam: Hands-on with Walid Shaari
- June 10, 2021 9am Pacific | 12pm Eastern


