Amazon Elastic Container Service (ECS) Anywhere enables you to simply run containers in whatever location makes the most sense for your business – including on-premises. Security is a key concern for organizations shifting to the cloud. Sysdig has validated our Secure DevOps platform with ECS Anywhere, giving AWS customers the security and visibility needed to run containers confidently on the new deployment model.
In this article, we’ll take a look at the capabilities of Sysdig that help Amazon ECS users secure and monitor containers and cloud.
Running containers in a hybrid cloud model with ECS Anywhere
One of the great things about ECS is its simple managed control plane. The service helps users run containerized apps without having to dive into complex setup and management features necessary with other solutions. This is a plus for AWS users, helping them get started quickly, which in the end reduces time to build and deploy apps.
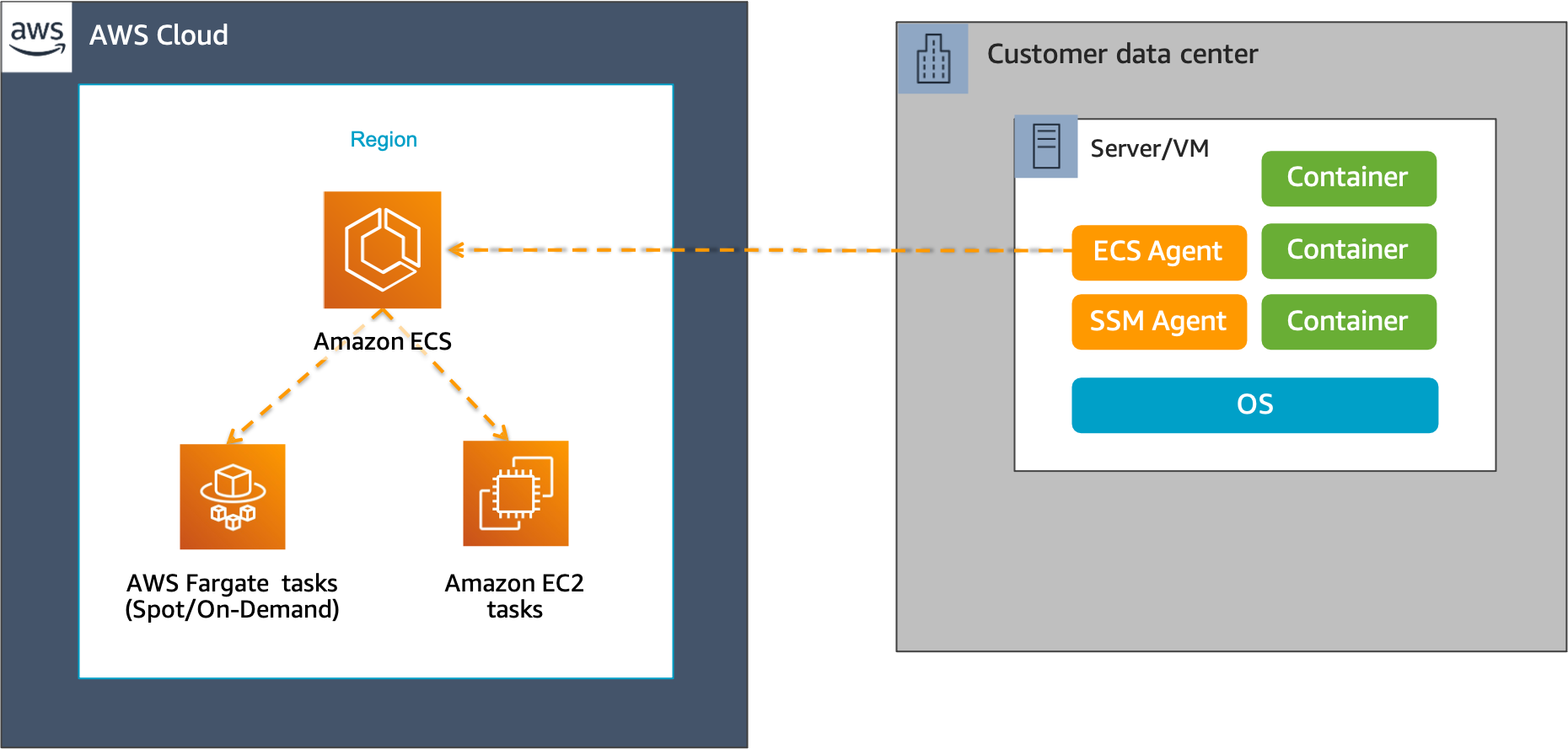
With the GA launch of ECS Anywhere, AWS now makes available a full spectrum of deployment options for ECS use. Here’s a view of the various ways you can run ECS.
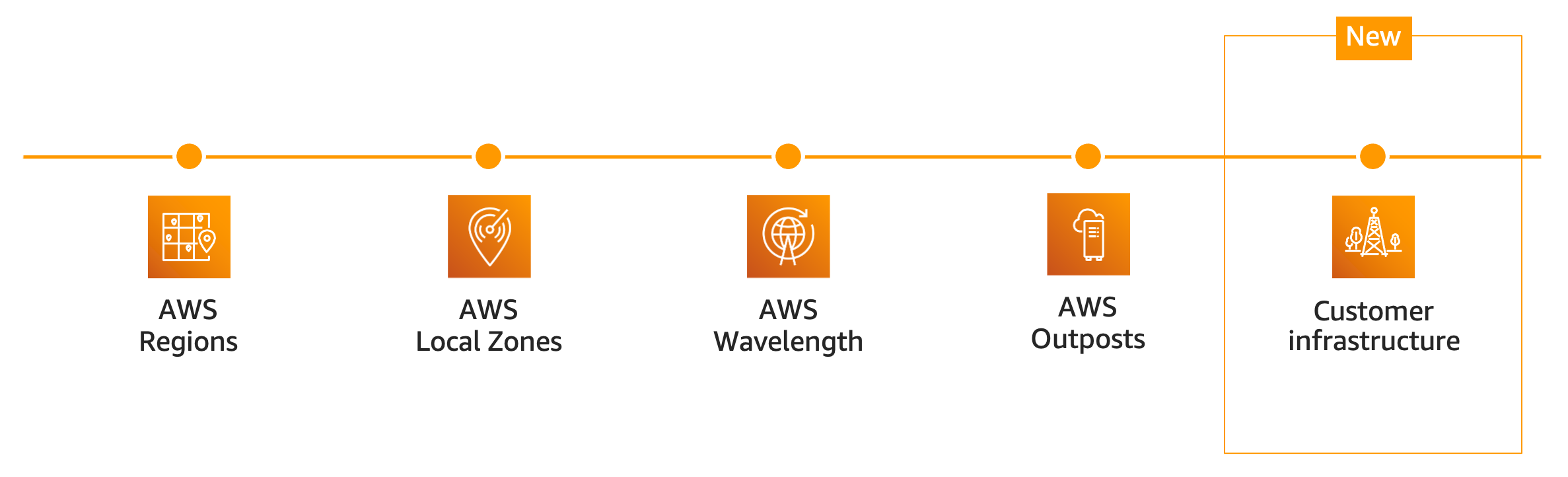
With ECS Anywhere, you can use the managed ECS control plane regardless of where your actual workloads run. Now you can containerize existing on-prem apps and maintain them on-prem. In addition, with ECS Anywhere you can bypass the need to run, update, or maintain container orchestrators on-prem.
One of the questions that customers have asked is, “What happens if you get disconnected from the cloud where your ECS orchestration is?” No problem – AWS has you covered. They have factored in disconnected operations. During disconnection, tasks will continue to run and upon reconnection, the control plane re-evaluates the state of instances and any pending tasks are placed and started.
Using Sysdig to secure and monitor ECS Anywhere
Sysdig is uniquely suited for ECS Anywhere because it gives customers a single view into their container operations across diverse, hybrid cloud deployments. Deploying to the cloud? Using AWS Outposts? Running on your own bare-metal servers? You can deploy the Sysdig agent anywhere you need to implement security and monitoring.
Specifically for ECS Anywhere, you can follow these steps to run the agent.
Register the task definition
aws ecs register-task-definition \
--cli-input-json file://sysdig-ecs-a-agent.json
Run the agent as a daemon
aws ecs create-service \
--cluster $CLUSTER_NAME \
--service-name sysdig-ecs-agent-svc \
--launch-type EXTERNAL \
--task-definition sysdig-ecs-a-agent \
--schedulingStrategy DAEMON
Notice the launch-type of EXTERNAL. This is the only difference between running the agent on ECS Anywhere vs. “regular” ECS in the cloud where the launch type is EC2.
The cli-input-json in the first part refers to the file sysdig-ecs-a-agent.json. Here’s what this file looks like – and again, the main difference is the notation for EXTERNAL with the “requiresCompatibilities” property.
sysdig-ecs-a-agent.json
{
"family": "sysdig-ecs-a-agent",
"containerDefinitions": [
{
"name": "sysdig-ecs-a-agent",
"image": "sysdig/agent",
"memory": 512,
"privileged": true,
"environment": [
{
"name": "ACCESS_KEY",
"value": "12345678-1234-1234-1234-123456789012"
},
{
"name": "TAGS",
"value": "environment:production"
}
],
"mountPoints": [
{
"readOnly": true,
"containerPath": "/host/boot",
"sourceVolume": "boot"
},
{
"containerPath": "/host/dev",
"sourceVolume": "dev"
},
{
"readOnly": true,
"containerPath": "/host/lib/modules",
"sourceVolume": "modules"
},
{
"readOnly": true,
"containerPath": "/host/proc",
"sourceVolume": "proc"
},
{
"containerPath": "/host/var/run/docker.sock",
"sourceVolume": "sock"
},
{
"readOnly": true,
"containerPath": "/host/usr",
"sourceVolume": "usr"
}
]
}
],
"pidMode": "host",
"networkMode": "host",
"volumes": [
{
"name": "sock",
"host": {
"sourcePath": "/var/run/docker.sock"
}
},
{
"name": "dev",
"host": {
"sourcePath": "/dev/"
}
},
{
"name": "proc",
"host": {
"sourcePath": "/proc/"
}
},
{
"name": "boot",
"host": {
"sourcePath": "/boot/"
}
},
{
"name": "modules",
"host": {
"sourcePath": "/lib/modules/"
}
},
{
"name": "usr",
"host": {
"sourcePath": "/usr/"
}
}
],
"requiresCompatibilities": [
"EXTERNAL"
]
}
With the agent installed, Sysdig will begin auto-discovering your containers and other aspects of your ECS environment.
Container and cloud security with ECS Anywhere
Sysdig Secure is built on the open-source Falco detection engine. It extends Falco cloud-native runtime security with a graphical user interface (GUI) for simplifying security policy management and is built to provide container and cloud security at scale.
In addition to runtime security, Sysdig Secure provides a whole range of security and compliance capabilities that you can apply to your AWS and ECS Anywhere environment – from the time you’re building applications through production.
Container-level visibility with ECS orchestration context will help you understand the behavior of your container applications. You can also tap into AWS CloudTrail logs to get a view into your cloud account activity. What this means is that you can spot something like an intrusion into sensitive data via a container running on ECS Anywhere, but also understand if there were misconfigurations or suspicious access in your AWS account that could further explain the breach.
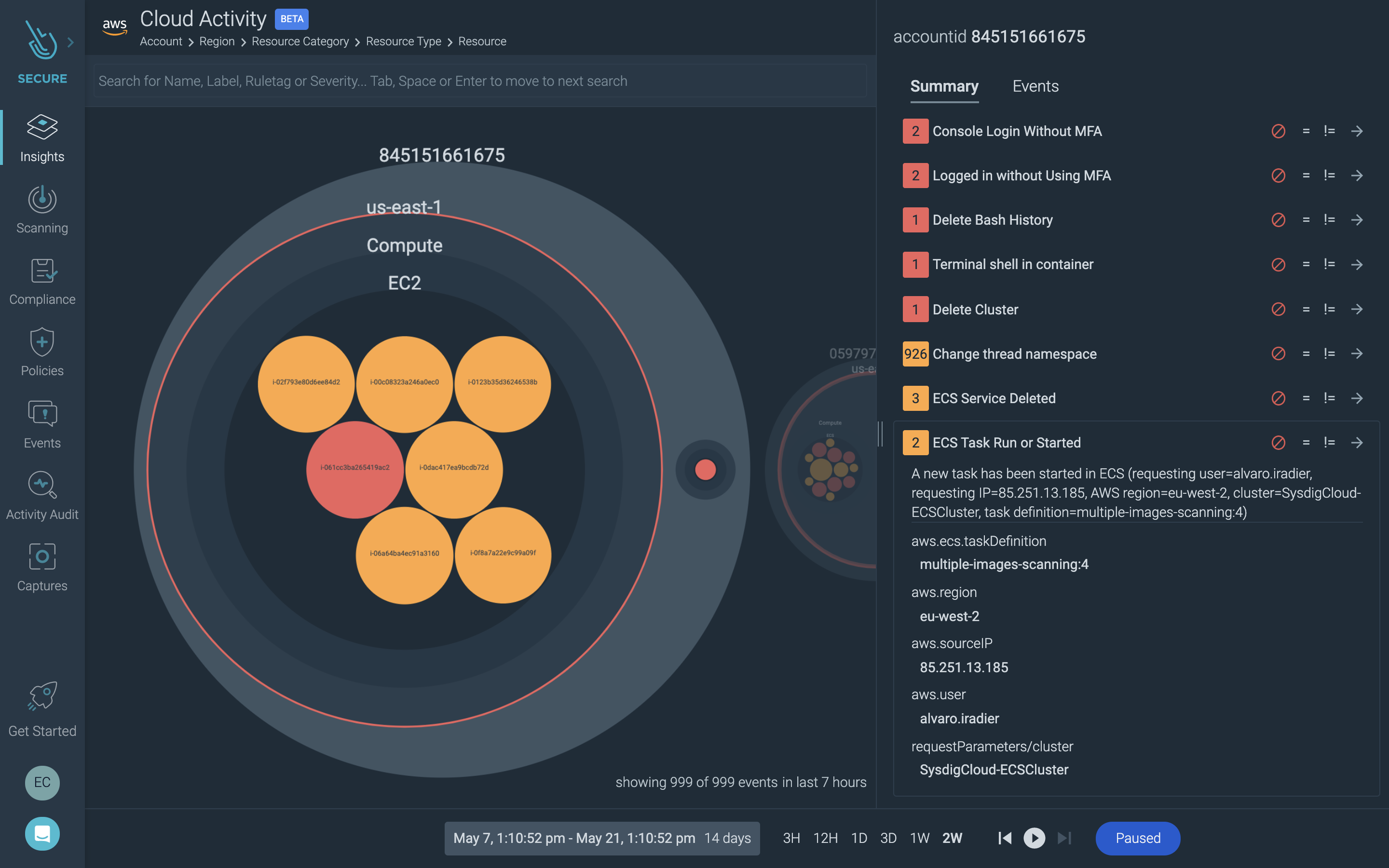
Read more about Sysdig’s CloudTrail integration here. This cloud security functionality is included in the Sysdig Free Tier as well as Enterprise license.
One of the key values for ECS Anywhere is to provide consistent operations for cloud and on-prem so customers can free themselves from disparate operational models. Similarly, Sysdig helps alleviate the need to support different security and monitoring tools for containers and cloud.
Combining cloud workload protection and threat detection with cloud security posture management gives you more information from one solution, one agent, and one tool – in one place. Seeing events for containers, users, and cloud services together makes the triage of incidents far more effective and less time-consuming.
Continuous compliance with ECS Anywhere
One of the key use cases for ECS Anywhere is compliance. Customers in regulated industries have been locked out of managed services because of mandates that called for strict ownership of infrastructure. The hybrid approach offered by ECS Anywhere lets you keep custody of containers and data locally for compliance, but still leverage the managed control plane via the AWS cloud.
Sysdig Secure supports your compliance initiatives with compliance-specific policies and checks that you can turn on or off to help you meet requirements for standards such as PCI, NIST, SOC2, and HIPAA. See below for examples.
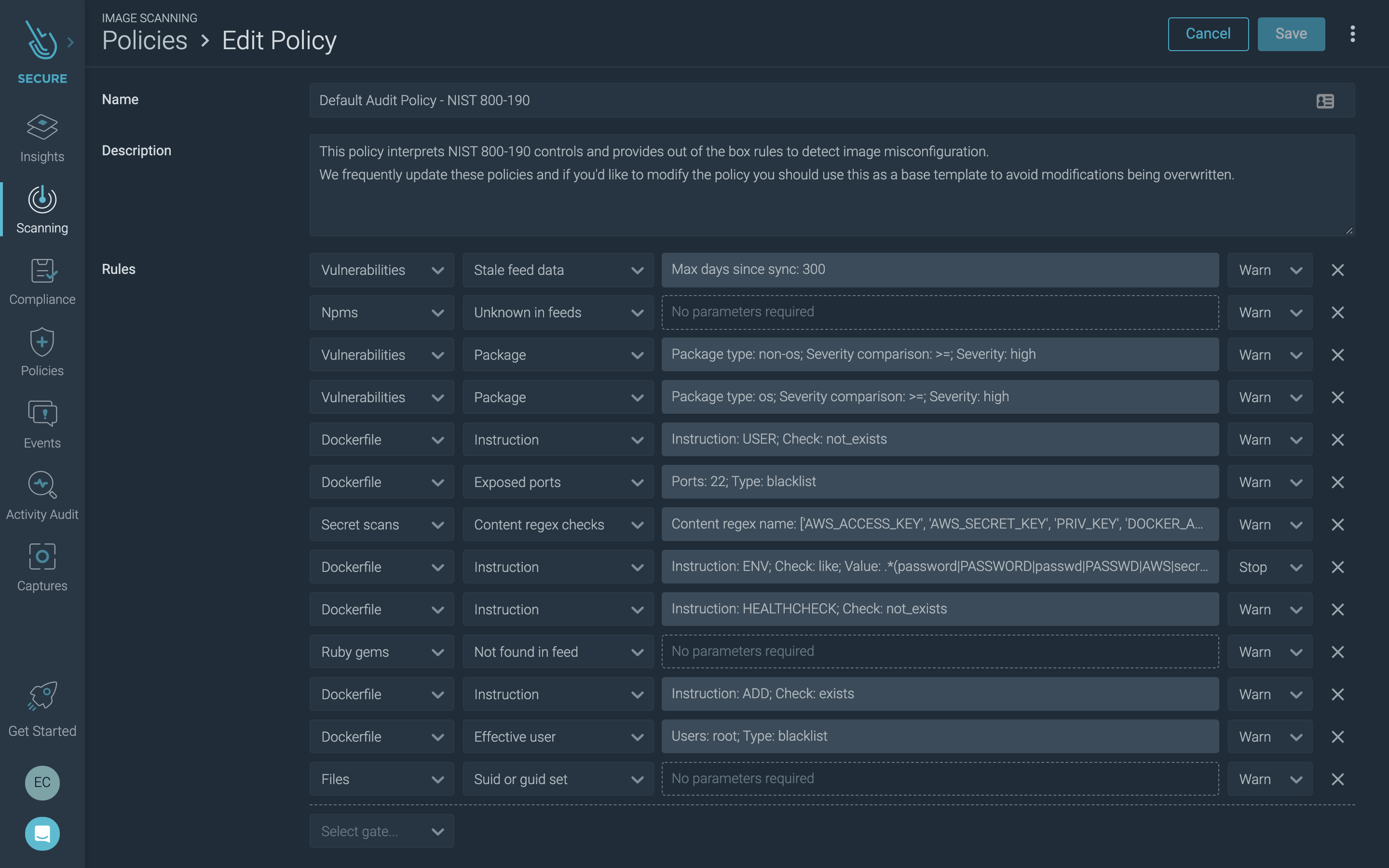
Image Scanning Audit Policy – NIST 800-190
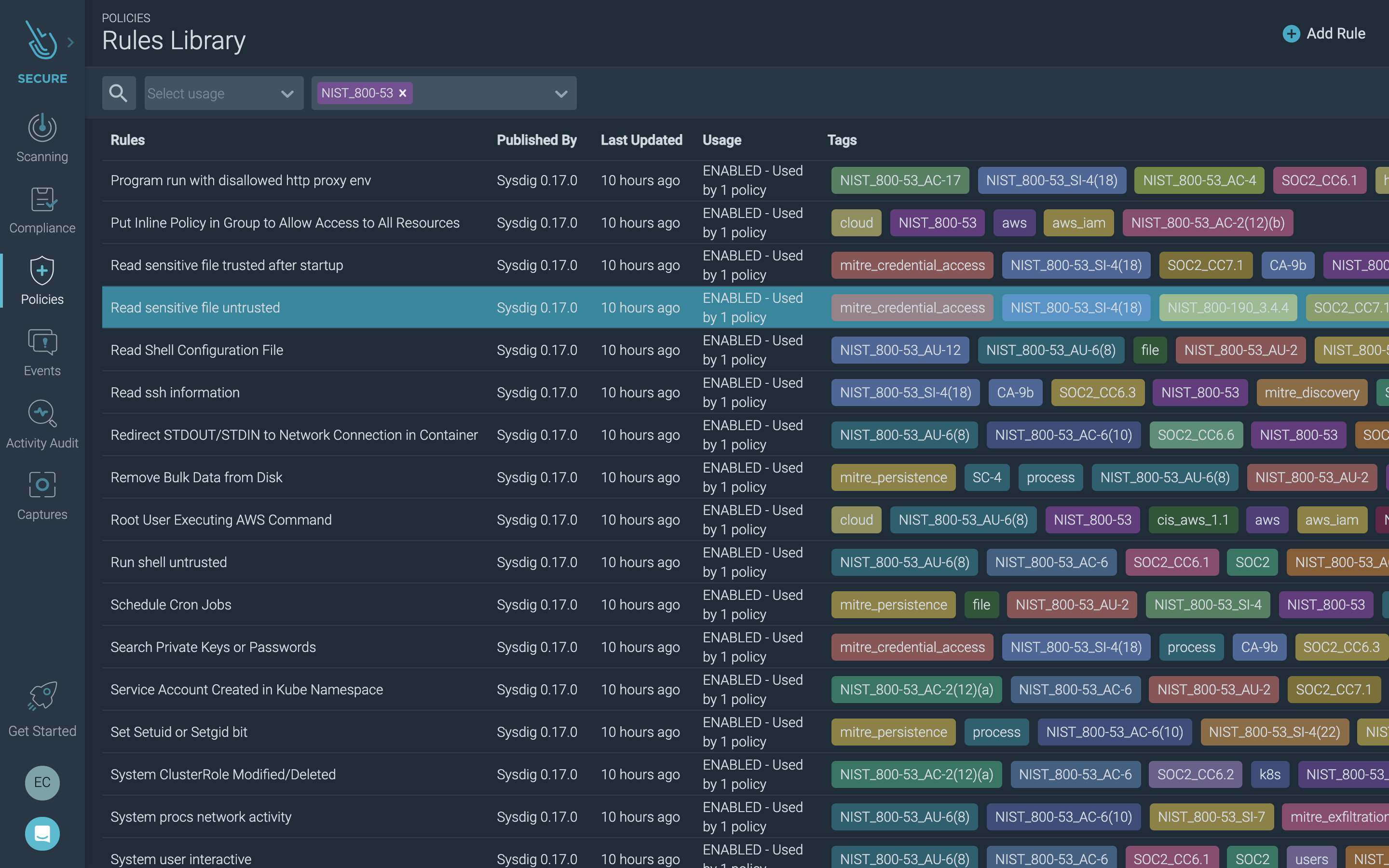
Runtime Security Rules – NIST 800-53
Using ECS Anywhere with AWS Fargate
If you choose to deploy on-prem with ECS Anywhere you can also take advantage of compute in the cloud for parts of their application infrastructure, including AWS Fargate to run tasks.
In serverless environments, without access to the host, visibility into workload activity can be limited. To help you secure a mixed environment of ECS Anywhere and Fargate, Sysdig also includes automated Fargate image scanning as well as Fargate runtime detection and response. For more insight on securing Fargate, check out the Securing Containers on AWS Fargate Checklist.
Conclusion
With ECS Anywhere, AWS is helping its customers expand their application infrastructure beyond the public cloud. Both within the cloud and in your own data center, security is something that should be carefully planned and executed.
Our collaboration with AWS to support all of the available deployment models means you can confidently run containers anywhere that makes sense for your business. If you’d like to check out the Sysdig product, you can get started for free. Just click here.


