
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Welcome to another monthly update on what's new from Sysdig! Happy Janmashtami! Shanah Tovah! 中秋快乐!With lockdown lifting by varying degrees across the world, we hope you had a safe but pleasant holiday! It has certainly been long overdue. Here at Sysdig, we celebrated Labor Day in the USA with an extended weekend and a well being day for the team. It's important for everyone to get the opportunity to recharge and make the most of the final summer days (for those in the northern hemisphere anyway!). We hope you've had similar opportunities, and managed to get the kids packed off and back to school.Over in the community, a few of us were involved in Kubernetes Community Days UK. If you missed this live, you can catch up on some of the awesome talks on their YouTube channel. The KCD events around the world are a great way to connect with some folks local to you that are working in the cloud-native world. Maybe you're looking for some advice and guidance, maybe just interested in what others are doing, or maybe you're looking at a career move and want to know who's doing cool stuff! Whatever your reason, the KCD and Cloud-Native communities are great to get involved with and they're all very welcoming.From a release perspective, this month was all about compliance. We've been on a roll and we've been expanding the compliance coverage within Sysdig. We really hope you find this useful. Feedback on how you're using Sysdig and our updated features is always very welcome!As always, please go review our own Release Notes for more details on product updates, and ping your local Sysdig contact if you have questions about anything covered in here.
Sysdig Secure
New and Updated Compliance Standards
Sysdig Secure has added new and updated compliance standards. See also: Compliance
Updates to PCI DSS v3.2.1 Compliance for Workload
We have implemented some changes to the PCI DSS v3.2.1 for workload compliance checks. The control coverage for PCI is now: 1.1.2, 1.1.3, 1.1.5, 1.1.6.b, 2.2, 2.2.a, 2.2.1, 2.2.2, 2.4, 2.6, 4.1, 6.1, 6.2, 6.4.2, 6.5.1, 6.5.6, 6.5.8, 7.2.3, 10.1, 10.2, 10.2.1, 10.2.5, 10.2.7, 10.5.5, 11.5.1Checks added:
- Check for Network Security enabled added to controls 1.1.2, 1.1.3 and 1.1.5
- Check for Kubernetes audit enabled added to controls 4.1, 6.4.2 and 6.5.8
Rules added:
- Rule Outbound or Inbound Traffic not to Authorized Server Process and Port added to control 2.2.1
- Rule Attach to cluster-admin Role added to controls 7.2.3 and 10.5.5
- Rules EphemeralContainers Created and Terminal shell in container added to controls 10.1 and 10.2.1
- Rules ClusterRole With Pod Exec Created, ClusterRole With Wildcard Created, and ClusterRole With Write Privileges Created added to control 10.2
- Rule Launch Privileged Container added to control 10.2.5
- Rules Container Drift Detected (chmod) and Container Drift Detected (open+create) added to control 11.5.1
Rules removed:
- Rule All K8s Audit Events rule removed from controls 10.1, 10.2, 10.2.1, 10.2.7
New PCI DSS v3.2.1 Compliance for AWS
The PCI Quick Reference describes the full range of controls required to pass a PCI 3.2 audit. In this release, Sysdig Secure will add the following controls.For AWS protection: 2.2, 2.2.2, 10.1, 10.2.1, 10.2.2, 10.2.5, 10.2.6, 10.2.7, 10.5.5, 11.4
New AWS Well Architected Framework Compliance
The AWS Well Architected Framework whitepaper defines best practices to build secure, high-performing, resilient, and efficient infrastructure for applications and workloads.For workload protection, Sysdig Secure will check the following sections: OPS 4, OPS 5, OPS 6, OPS 7, OPS 8, SEC 1, SEC 5, SEC 6, SEC 7, REL 2, REL 4, REL 5, REL 6, REL 10, PERF 5, PERF 6, PERF 7For AWS protection, Sysdig Secure will check the following sections: OPS 6, SEC 1, SEC 2, SEC 3, SEC 8, SEC 9, REL 2, REL 9, REL 10
New AWS Foundational Security Best Practices v1 (FSBP) Compliance
AWS Foundational Security Best Practices v1 (FSBP) describes the full range of controls to detect when your deployed accounts and resources deviate from security best practices.For AWS protection, Sysdig Secure will check the following sections: AutoScaling.1, CloudTrail.1, Config.1, EC2.6, CloudTrail.2, DMS.1, EC2.1, EC2.2, EC2.3, ES.1, IAM.1, IAM.2, IAM.4, IAM.5, IAM.6, IAM.7, Lambda.2, GuardDuty.1
New NIST 800-171 rev2 Compliance
The National Institute of Standards and Technology (NIST) Special Publication 800-171 rev2 describes the full range of controls required to pass a NIST 800-171 audit. It provides agencies with recommended security requirements for protecting the confidentiality of Controlled Unclassified Information (CUI) when the information is resident in nonfederal systems and organizations.For workload protection, Sysdig Secure will check the following sections: 3.1.1, 3.1.2, 3.1.3, 3.1.5, 3.1.6, 3.1.7, 3.1.12, 3.1.13, 3.1.14, 3.1.15, 3.1.16, 3.1.17, 3.1.20, 3.3.1, 3.3.2, 3.3.5, 3.3.8, 3.3.9, 3.4.3, 3.4.5, 3.4.6, 3.4.7, 3.4.9, 3.5.1, 3.5.2, 3.11.2, 3.12.1, 3.13.1, 3.13.2, 3.13.3, 3.13.4, 3.13.5, 3.13.6, 3.13.8, 3.14.1, 3.14.2, 3.14.3, 3.14.4, 3.14.5, 3.14.6, 3.14.7For AWS protection, Sysdig Secure will check the following sections: 3.1.1, 3.1.2, 3.1.3, 3.3.1, 3.3.2, 3.3.7, 3.5.7, 3.5.8, 3.14.6, 3.14.7
New Terraform Onboarding Options for Secure for cloud
Users can now onboard Sysdig Secure for cloud with their AWS accounts (single or organizational) using Terraform. See the feature description and the deployment/onboarding instructions.
Date Columns Added for Scheduled Scanning Reports
In Sysdig Secure, the Scheduled Reports for Scanning now display additional vulnerability metadata for both runtime and registry reports.Specifically:
- Disclosure date: Time when the vulnerability information was registered in the feed
- Solution date: Time when the fix version for this vulnerability (if any) was registered in the feed
To avoid breaking compatibility with existing reports and external instrumentation, these fields will only be available for newly created reports; existing Scheduled reports (even if they are modified and saved again) will not contain these columns.
Falco Rules
v0.36.0 is the latest version. Below is a diff of changes from v0.33.0, which we covered last month.Added the following rules:
- Console Login Through Assume Role
- AWS Command Executed by Untrusted User
- Console Login Success
- Console Login Success From Untrusted IP
- Delete AWS user
- Remove AWS User from Group
- Put Object in Watched Bucket
- Read Object in Watched Bucket
- Unprivileged Delegation of Page Faults Handling to a Userspace Process
Added new / updated lists:
- trusted_aws_users
- watched_buckets
- sysdig_commercial_images
- falco_hostnetwork_images
Updated rules:
- Console Login Without MFA now does not fire on assumed role
- Console Root Login Without MFA now does not fire on assumed role
- Add AWS User to Group now outputs the user added to the group
Added / updated macros:
- Interactive macro updated checking the tty state. The interactive session is with proc.tty != 0
Check the Falco Rules Changelog for a full list of changes.
Cloud security posture management for GCP based on Cloud Custodian:
Sysdig adds cloud asset discovery, cloud services posture assessment, and compliance validation for Google Cloud. Cloud security teams can manage their security posture by automatically discovering cloud services, flagging misconfigurations and violations, and assessing compliance with regulatory requirements. The new CSPM features are based on Cloud Custodian, an open source tool for securing cloud infrastructure.
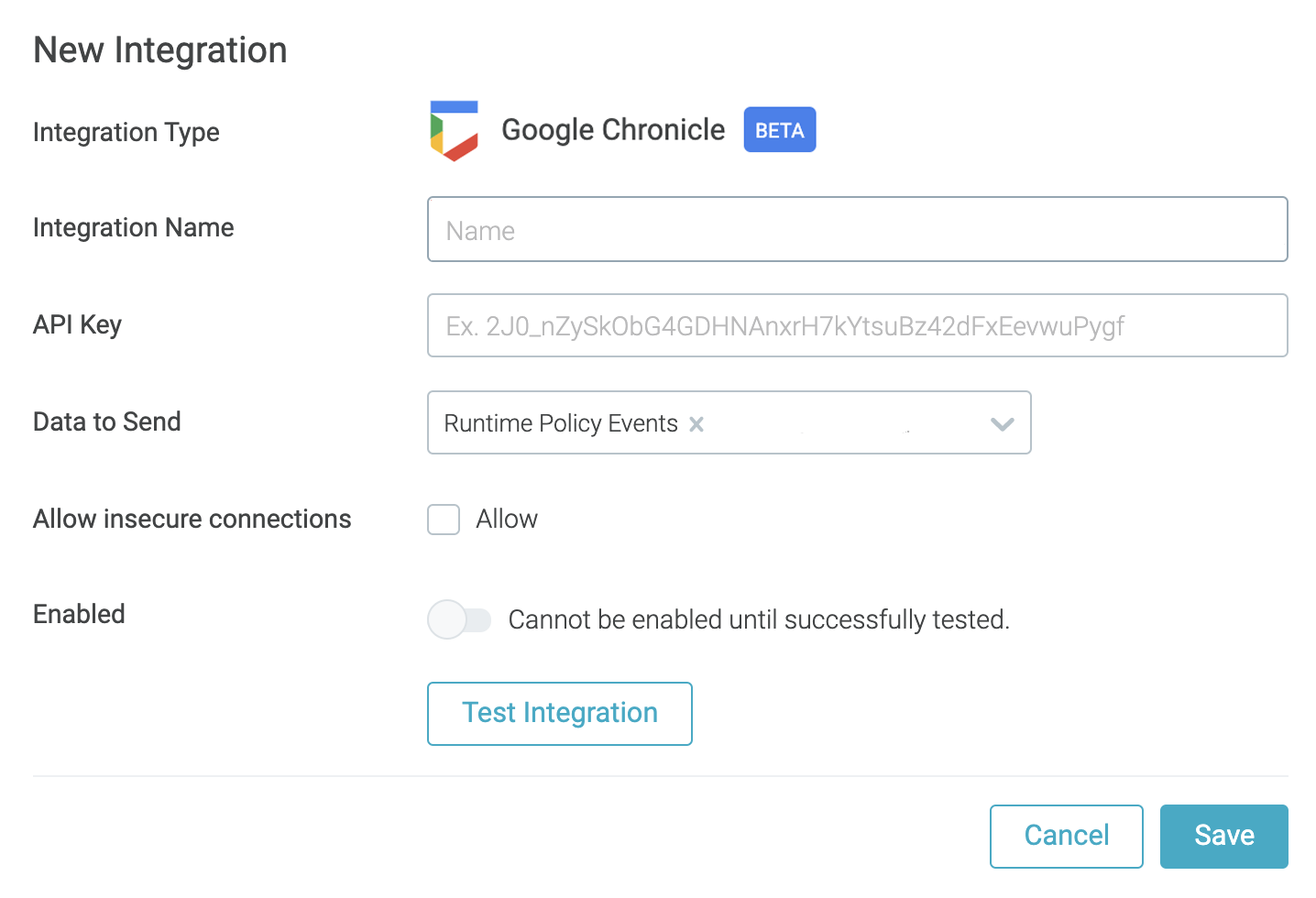
New Event Forwarding to Chronicle
Forward Sysdig runtime security events to Google Cloud's Chronicle security analytics platform. It enables Chronicle users to accelerate cloud and container threat response by incorporating Sysdig data.
Sysdig Agents
Sysdig Agent
The latest Sysdig Agent release is 11.4.1. Below is a diff of updates since 11.4.0, which we covered in our last update.This is a hotfix release.
Defect Fixes
Fixed a problem that broke app checks in agent-slim by adding the missing dependencies.
Sysdig Serverless Agent
The latest Sysdig Serverless Agent release is 2.0.0, which we covered in our last update.
Sysdig Agent – Helm Chart
The Helm Chart 1.12.8 is the latest version, which we covered in our last update.https://charts.sysdig.com/Changelog: https://github.com/sysdiglabs/charts/blob/master/charts/sysdig/CHANGELOG.md
Node Analyzer
Version 0.1.13 is still the latest release, which we covered in our last update.Node image analyzer can be installed as part of the Sysdig Agent install: https://docs.sysdig.com/en/scan-running-images.html
Inline Scanning Engine
v2.4.6 is the latest release. Below is a diff of updates since v2.4.5, which we covered in our last update.See also: Integrate with CI/CD Tools.
- Added support for images with the (deprecated) manifest schema V1
Admission Controller
v3.7.0 is the latest release. Below is a diff of updates since v3.4.1, which we covered in our last update.
- Add dry-run mode for Admission Controller
- Enable Kube Run detections on AC
- Notify events to Sysdig Secure only once
- Show workload name on Sysdig Secure event
https://docs.sysdig.com/en/admission-controller.html
SDK, CLI and Tools
Sysdig CLI
v0.7.14 is still the latest release. Below is a diff of updates since v0.7.12, which we covered in our last update.
- backup/restore: Allow restoration with only one provided token
- Solve policy event formatting when rule has no tags
https://github.com/sysdiglabs/sysdig-platform-cli/releases/tag/v0.7.14https://sysdiglabs.github.io/sysdig-platform-cli/
Python SDK
v0.16.2 is still the latest release, which we covered in our last update.https://github.com/sysdiglabs/sysdig-sdk-python/releases/tag/v0.16.2
Terraform Provider
v0.5.20 is the latest release. Below is a diff of updates since v0.5.16, which we covered in our last update.
- Allow enabling/disabling of benchmark tasks using the enabled field for
sysdig_secure_benchmark_task - Add
aws_account_idandaws_role_nameattributes to thesecure_trusted_cloud_identitydatasource - Add validation to
cloud_provider - Add Benchmark Task resource
- Fix Sysdig Secure Cloud
sysdig_secure_trusted_cloud_identitydatasource provided identity ARN - Adds support to handle Sysdig Secure Cloud configuration
- resources (
sysdig_secure_cloud_account) to be used with terraform-aws|gcp|azure-cloudvisionmodules - datasources (
sysdig_secure_trusted_cloud_identity)
- resources (
Falco VS Code Extension
v0.1.0 is still the latest release.https://github.com/sysdiglabs/vscode-falco/releases/tag/v0.1.0
Sysdig Cloud Connector
v0.8.5 of the Sysdig Cloud Connector was released, we covered v0.8.1last month.Here are some highlights of the differences between these versions:
New Features
- Added compliance standards tags to rules
- admission: add kube audit – attach command detection
- New rules for AWS requested by customers
- AWS command executed by untrusted user new rule
- cloud-scanning: Update Organizational Multi Account ECR and ECS scanning
- cloud-scanning: Set up organization assume role for s3 bucket
- scanning/aws: Now the scanning replaces the existing pipeline in CodeBuild, with an existing one from the binary. This will make future updates easier since the scanning logic is embedded in the binary, instead of relying on the deployed one with CFT/Terraform.
Bug Fixes
- Check value before using it to avoid panic when parsing aws.user
- Fix an integration test when writing logs to stackdriver
- Use appropriate username in AWS event_builder
- Add some delay before sending attach events to activity audit
- Correct pipeline configured with skipTLS
- Send correct rule name to event feed
- evaluator: Do not error on empty slice field. Now, it does not error on empty slice fields being extracted and adds more logging for debugging the reason why the field value has not been extracted.
- Remove azure activity log path references
- Use the user instead of user name in azure rules
Check the full list of changes to get all the details.
Sysdig Secure Inline Scan for Github Actions
v3.2.0 is the latest release, which we covered in our last update.https://github.com/marketplace/actions/sysdig-secure-inline-scan
Sysdig Secure Jenkins Plugin
v2.1.11 is the latest release, which we covered in our last update.https://plugins.jenkins.io/sysdig-secure/
New Website Resources
Blogs
- How to mitigate kubelet's CVE-2021-25741: Symlink exchange can allow host filesystem access
- How to monitor Redis with Prometheus
- NIST 800-53 compliance for containers and Kubernetes
- Kubernetes network segmentation using native controls
- Confidently deliver HIPAA compliance software with Sysdig Secure
- Smart gardening with a Raspi and Prometheus
- Securing Amazon EKS Anywhere with Sysdig
- Top 9 file integrity monitoring (FIM) best practices
- Top 10 Indicators of Compromise in Kubernetes
Webinars
- Securing Infrastructure as Code via Open Policy Agent (OPA)
- Kubernetes Monitoring Best Practices
- Align Your Cloud Security Plan with the Cybersecurity Exec Order


