In this blog, we will cover the various requirements you need to meet to achieve NIST 800-53 compliance, as well as how Sysdig Secure can help you continuously validate NIST 800-53 requirements for containers and Kubernetes.
NIST 800-53 rev4 is deprecated since 23 September 2021
Read about the differences between versions down below →
What is NIST 800-53 compliance?
The National Institute of Standards and Technology (NIST) is a non-regulatory government agency that develops technology, metrics, and standards to drive innovation and economic competitiveness. It has several publications about security, among them is NIST Special Publication (SP) 800-53: Security and Privacy Controls for Information Systems and Organizations.
Contractors and supply chain businesses that expect to work with the U.S. federal government use NIST 800-53 to prove their solvency in cybersecurity.
NIST 800-53 compliance cost implications and consequences
Validating compliance is the number one blocker for faster application delivery. Regulators are increasingly enforcing financial penalties for failure to comply.
Studies have shown that:
- Annual cost of non-compliance to businesses runs an average of $14.8 million.
- The cost of compliance, on the other hand, was found to average $5.5 million.
Kubernetes is a dynamic environment in which it’s difficult to detect when assets fall out of NIST 800-53 compliance. Without a clear mapping of NIST 800-53 guidelines to this new environment, your teams won’t be able to prove they meet compliance requirements. As a result, meeting a NIST 800-53 audit becomes an expensive fire drill, slowing down application delivery for your cloud teams. Kubernetes compliance requires a new approach.
Your teams need to have a clear mapping of controls to their containerized workloads and the ability to continuously track compliance over time. This will let them be confident in their ability to manage security risk and pass security audits. Ultimately, you need to ensure that compliance is not blocking cloud adoption, so your business can ship cloud applications faster.
What is the difference between Revision 5 and Revision 4?
SP 800-53 Revision 5 Final was published on Sept. 23, 2020, after being a draft document since 2016. It supersedes Revision 4, which was published in 2015 and officially withdrawn on Sept. 23, 2021. Organizations looking to be compliant with NIST 800-53 had a year of overlap where using either of the revisions was accepted, so they could adapt to the new standard..
Among revision 5 changes are:
- Updates to control descriptions, so instead of centering on the responsible agent, the focus is on the expected outcome.
- All individual controls are given a distinctive name, and information security and privacy are consolidated as a single goal.
- Two new families are introduced: “Processing and Transparency” and “Supply Chain Risk Management.”
- Baseline controls are moved to a new document, NIST SP 800-53B, specific for federal agencies, so other organizations can implement their own baselines.
- Overall, control count increases from 513 to 1189.
You can check the full list of changes in the NIST blog post announcement.
Why is NIST 800-53 compliance different in containers and Kubernetes?
NIST 800-53 is defined as “a catalog of security and privacy controls to protect organizational operations and assets, individuals, other organizations, and the Nation from a diverse set of threats and risks, including hostile attacks, human errors, natural disasters, structural failures, foreign intelligence entities, and privacy risks.”
It has a very broad spectrum of controls that covers a lot of fields, and is not specific to containers and Kubernetes security. We have to “translate” its recommendation to specifics related to these technologies.
Another challenge is the massive number of controls (513) compared to other standards (NIST 800-190 has 18, PCI DSS has 30, SOC 2 has 47), so we immediately see that a special approach is needed for this standard.
Also, a recommended reading is a separate guideline, NIST SP 800-53A “Guide for Assessing the Security Controls in Federal Information Systems and Organizations.” It provides security controls baselines to help you select the relevant controls when getting started. We’ve summarized the controls and identified the ones that are relevant for containers, Kubernetes, and cloud below.
| ID | Family | Num Controls | Relevant cloud, containers & K8S |
| AC | Access Control | 147 | 16% * |
| AU | Audit and Accountability | 69 | 22% * |
| AT | Awareness and Training | 17 | 0% |
| CM | Configuration Management | 66 | 27% * |
| CP | Contingency Planning | 56 | 0% |
| CA | Assessment, Authorization and Monitoring | 32 | 22% * |
| IA | Identification and Authentication | 70 | 4% * |
| IR | Incident Response | 42 | 2% * |
| MA | Maintenance | 30 | 7% * |
| MP | Media Protection | 30 | 0% |
| PS | Personnel Security | 18 | 0% |
| PE | Physical and Environmental Protection | 59 | 0% |
| PL | Planning | 17 | 0% |
| RA | Risk Assessment | 26 | 12% * |
| SA | System and Services Acquisition | 145 | 25% * |
| SI | System and Information Integrity | 118 | 30% * |
| SC | System and Communications Protection | 162 | 20% * |
| PM | Program Management | 37 | 5% * |
| PT | PII Processing and Transparency | 21 | 0% |
| SR | Supply Chain Risk Management | 27 | 0% |
Table: NIST 800-53 (Rev. 5) families, number of controls,
and percentage of controls relevant to cloud, container, and Kubernetes security
* Note: You can cover all these controls with Sysdig Secure.
Working with the full XML or tab-delimited controls list provided by NIST can be daunting. You will eventually need to deal with it, but at the beginning, it’s better to invest your time and resources on the parts where you can make a bigger impact for containers and Kubernetes security. For example, to build this guide, we started by quickly analyzing each control family, then focusing on those more relevant to containers and Kubernetes security.
We recommend leaving the detailed analysis of all families and controls as a last step.
How NIST 800-53 compliance maps to security in containers and Kubernetes?
Here are the control families that are more relevant to containers and Kubernetes security, with examples of fields of application to these technologies.
Access controls
Control Summary: How user accounts are generated, secured, controlled, and authorized.
For cloud, containers and Kubernetes: Implement detections for processes or users trying to break beyond the security constraints of their assigned user and service accounts. Do it at container image or runtime level.
Audit and accountability
Control Summary: How audits of activity are generated and stored, and how alerts are triggered, reviewed, and responded to.
For cloud, containers and Kubernetes: Set up tools that enable auditing Kubernetes events and general security issues. Generate reports that show the general security state of infrastructure.
Assessment, Authorization and Monitoring
Control Summary: How security assessments and compliance, user authorization, and security monitoring are conducted.
For cloud, containers and Kubernetes: Assess usage of security tools and their features, the security posture of your digital assets, review user authorization procedures and continuously monitor risks.
Identification and Authentication
Control Summary: Security measures for users identification and authentication.
For cloud, containers and Kubernetes: Check bypassing authentication on operations, like a rogue node joining a cluster, or a non-corporate account operating in the cloud environment.
Risk Assessment
Control Summary: Identify threats and vulnerabilities in the system and determine the likelihood and magnitude of harm.
For containers and Kubernetes: Automate container vulnerability scanning and benchmarks to provide a global view of the security posture of the whole infrastructure.
System and communications protection
Control Summary: How to implement cypher mechanisms and prevent counterfeit data and components.
For cloud, containers and Kubernetes: Implement mechanisms to detect and counter attempts to impersonate or modify legitimate systems inside containers, detecting drifts from container images on runtime.
Configuration management
Control Summary: How the baseline configuration of a system is kept under configuration control, and how changes to it are tested before implementation.
For cloud, containers and Kubernetes: Test container images for security and misconfiguration issues. Do it in CI pipelines, or right before they are deployed.
System and information integrity
Control Summary: Mechanisms for identification, correction, and reporting of system flaws.
For cloud, containers and Kubernetes: Implement a centralized pipeline for CI/CD with image scanning. Install an admission controller that can intercept deployments that bypass the pipeline. Set up runtime detections for abnormal behavior that can only be detected while a container is running. Implement notification and reporting mechanisms.
System and services acquisition
Control Summary: Quality metrics and guarantees from developers about the systems they provide.
For cloud, containers and Kubernetes: Similar to the previous point, focus on checking for misconfigurations and vulnerabilities on the software deployed in containers.
Incident response
Control Summary: Incident response policy characteristics and how incidents are handled.
For cloud, containers and Kubernetes: Ensure security events triggered in containers and Kubernetes are correctly notified and filtered, and that the information provided facilitates incident response tasks.
Other families
NIST 800-53 rev.5 includes other families defining controls that may also be relevant to you outside the containers and Kubernetes scope. Once you are confident you have the other ones under control, don’t hesitate to review the rest of the families as well as a deep dive in the full list of controls.
Sysdig Secure helps you validate NIST 800-53 compliance
Sysdig Secure helps you validate NIST 800-53 compliance, covering all controls relevant to containers and Kubernetes security, to ensure that compliance is not a blocker for cloud adoption. Here are a few examples of how we address NIST 800-53 controls.
Example 1: Kubernetes network topology maps – NIST 800-53 major control AC-4
“Enforce approved authorizations for controlling the flow of information within the system and between connected systems based on organization-defined information flow control policies.”
Sysdig will dynamically generate topology maps of all hosts, containers, and processes on your infrastructure, and map any network connection they make inside and outside your network. These topology maps can also be customized to show the logical services and how they’re connected as well.
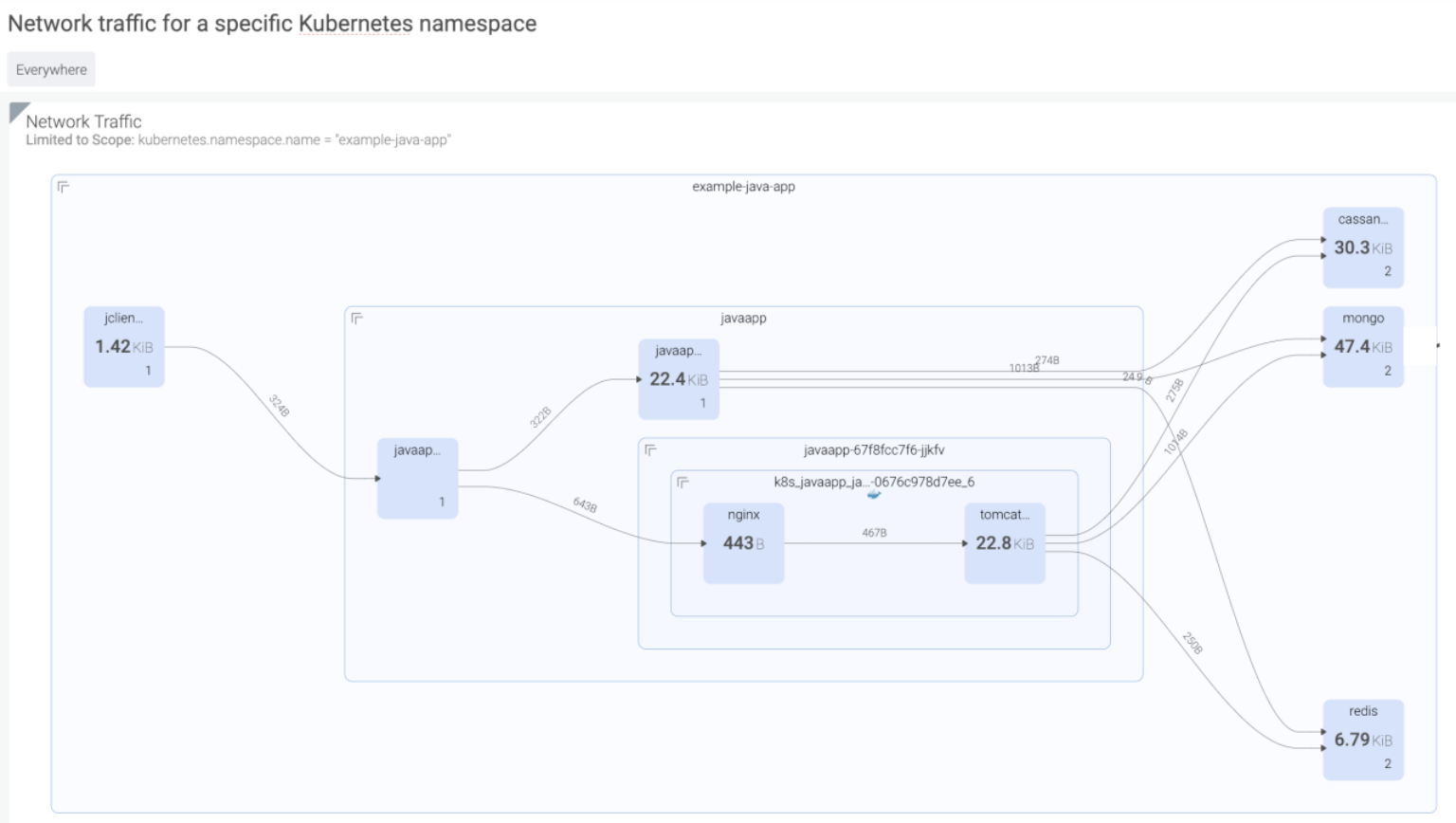
Example 2: Asset inventory management – NIST 800-53 control AU-6(5)
“Integrate analysis of audit records with analysis of vulnerability scanning information, performance data, system monitoring information, to further enhance the ability to identify inappropriate or unusual activity.”
Sysdig comes with an explore feature that will give you a view of all hosts, containers, or any process grouped by metadata running on their system. They can use this table to slice and dice all system components however they choose.
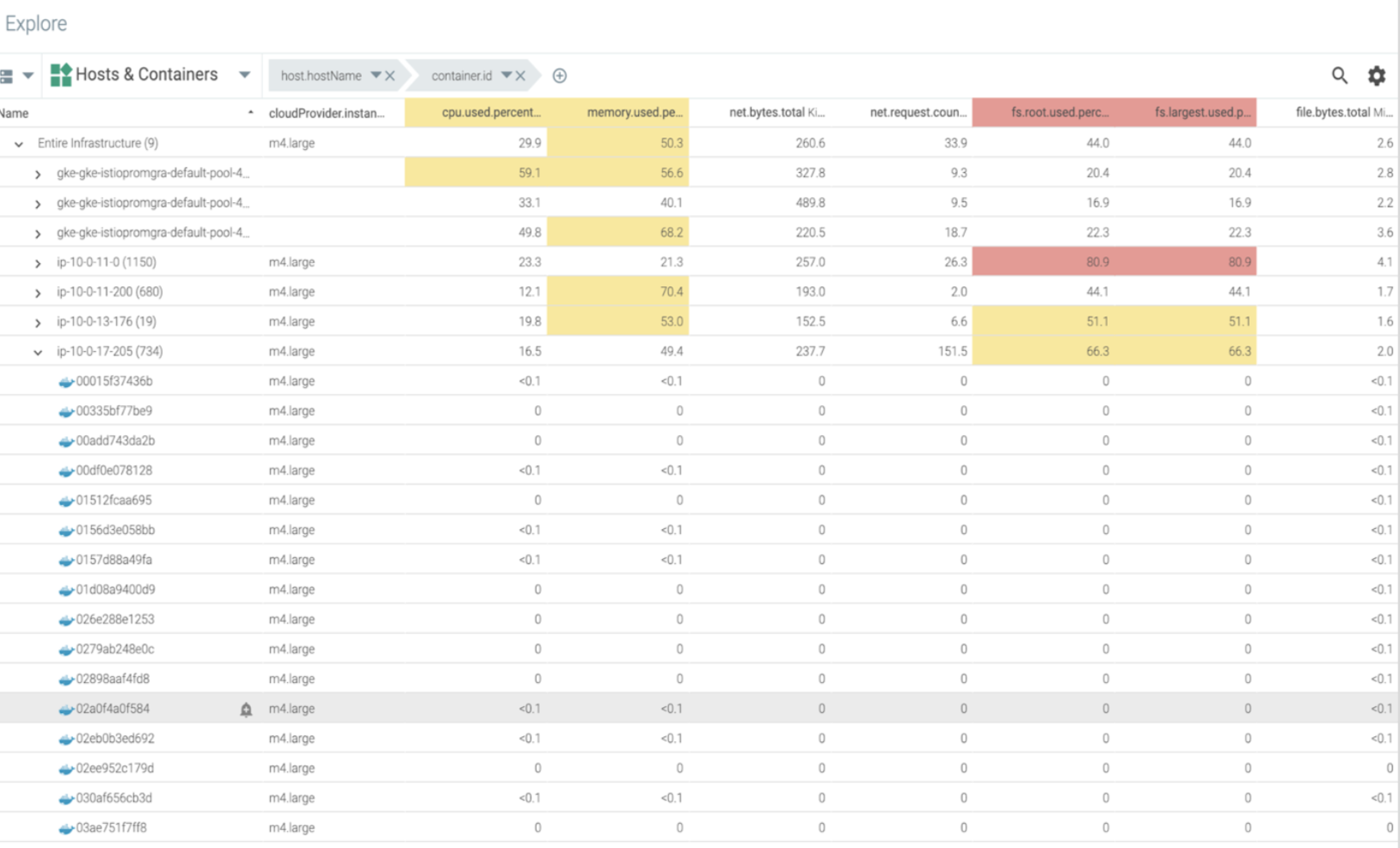
Example 3: Access control of cardholder data – NIST 800-53 configuration management control CM-3b
“The organization reviews proposed configuration-controlled changes to the system and approve or disapprove such changes with explicit consideration for security and privacy impact analyses.”
Sysdig analyzes the requirements of the Pod spec in your Deployment definition and creates the least privilege PSP for your application. This controls if you allow privileged pods, users to run as the container, volumes, etc.
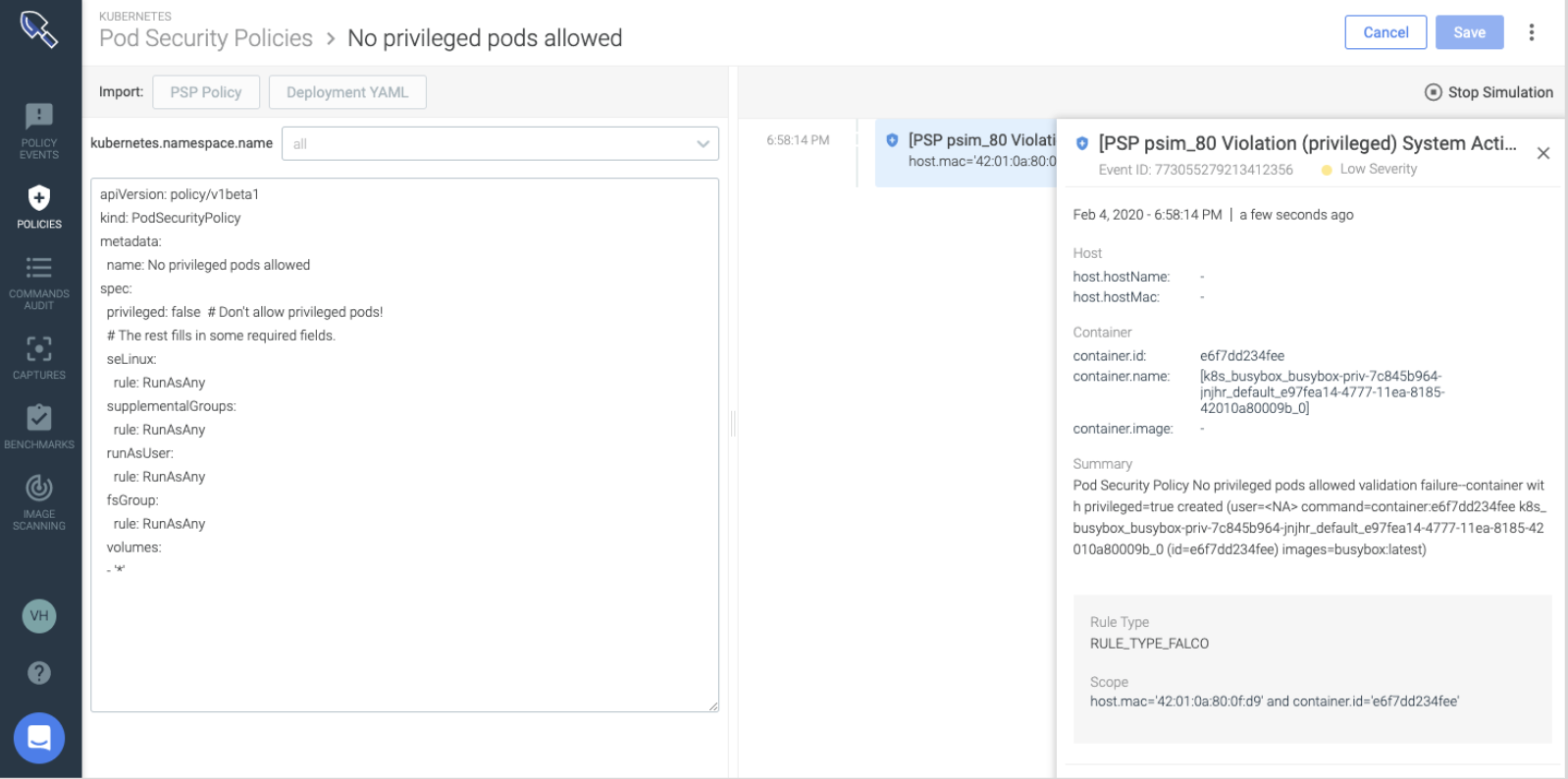
Example 4: Kubernetes audit trail – NIST 800-53 system and information integrity control SI-4e
“The organization deploys monitoring devices that adjust the level of system monitoring activity when there is a change in risk to organizational operations and assets, individuals, or other organizations.”
Sysdig provides a continuous audit of all container infrastructure events to facilitate incident response and NIST 800-53 compliance. Use this as proof of compliance for your third-party auditors, even after the containers are gone.

Runtime security using syscalls, Kubernetes and AWS CloudTrail
Sysdig Secure’s runtime security engine based on open-source Falco, captures syscalls at the kernel level, Kubernetes audit log events, and Amazon Cloudtrail infrastructure events. It’s able to detect insecure situations immediately as a runtime event is available, notifying who is responsible, recording auditing information, and taking automatic actions like pausing or killing the container.
Thanks to the richness of the Falco rule syntax, you can create rules for many behavior-oriented controls.
But you won’t have to create those rules from scratch. Sysdig provides many out-of-the-box rules and features with coverage across multiple controls and families at the same time:
- Access Controls: 72 Falco rules tagged for this family, like: “Terminal Shell in a container” also tagged for controls AC-2g, AC-2(4), AC-17, and AU-6(8).
- Audit and Accountability: 63 Falco rules tagged for this family, like: “Clear log activities” tagged also for controls AU-6(8), AU-2, AU-10, and CM-5.
- System and communications protection: 19 Falco rules tagged for this family, like: “Detect creation on AWS for a HTTP target group without SSL,” tagged for control SC-8(1).
- Configuration management: 41 Falco rules tagged for this family, like: “Create Sensitive Mount Pod” tagged also for controls AC-6(9), AC-6(10), CM-3, SI-4, AU-2.
- System and information integrity: 52 Falco rules tagged for this family, like: “Update Package Repository” tagged also for controls CM-5, SI-7, SI-4, SI-3.
- Assessment, Authorization and Monitoring: Several benchmarks, 6 image scanning rules, and 2 Falco rules like “Read sensitive file untrusted” that also covers controls CA-9, SC-4.
- Identification and Authentication: 3 Falco rules like “Untrusted Node Unsuccessfully Tried to Join the Cluster.”
- Incident Response: The whole Falco engine combined with Sysdig Secure captures of all activity (syscalls, memory, files, networking) is centered on Incident Response, as specified for example in control IR-4(12): “Analyze malicious code and/or other residual artifacts remaining in the system after the incident.”
- Risk Assessment: The whole vulnerability scanning feature for containers and hosts revolves around Risk Assessment as described for example in control RA-5: “Monitor and scan for vulnerabilities in the system and hosted applications and when new vulnerabilities potentially affecting the system are identified and reported.”
- System and Services Acquisition: Having Sysdig container image scan integrated in a CI/CD pipeline and an Admission Controller policy to reject non-compliant images are features related to this, as seen for example in control SA-10e: “Require the developer of the system, system component, or system service to perform configuration management […] and track security flaws and flaw resolution.”
- System and Information Integrity: 52 Falco rules, like “Modify binary dirs” tagged also for controls CM-5, SI-7, SI-4.
- System and Communications Protection: 23 Falco rules, like “Detect outbound connections to common miner pool ports” tagged also for controls to CM-7(1), AC-17, SC-7(3), SI-4(4).
Implementing NIST 800-53 rules with Anitian
Anitian offers compliance as a service for companies with an emphasis on NIST 800-53/FedRamp. By embedding Sysdig into the Anitian solution, customers will be able to meet their regulatory compliance requirements.
“As adoption of container technology increases within the Federal space, the need for container and Kubernetes security and compliance has become obvious. Sysdig is a pioneer in providing an open source based policy engine that allows both flexibility and granularity to address the wide breadth of NIST controls securing these environments.”
Emily Cummins – Principal Security Architect, Anitian
Conclusions
NIST 800-53 guidelines were created to heighten the security of the information systems used within the federal government. The controls apply to any component of an information system that stores, processes, or transmits federal information.
Use container security tools that have already mapped the relevant controls to containers and Kubernetes, and provide out of the box checks, dashboards and reports that save you time.
To dig deeper into how Sysdig Secure can map and address many more NIST 800-53 controls, check out some of these resources below:
- Watch our on demand webinar: NIST 800-53 compliance for containers and Kubernetes.
- Sign up for Sysdig Secure free trial!


