The Sysdig Threat Research Team (TRT) has discovered a critical vulnerability in the GitHub repository gluestack/gluestack-ui, designated as CVE-2025-53104, which was recently involved in a supply chain attack involving compromised NPM packages. This CVE has been assigned a CVSS v3.1 base score of 9.1.
By exploiting this new vulnerability, an attacker can craft a malicious GitHub Discussion title or body and execute arbitrary commands on the GitHub Actions (GHA) runner. These malicious actions can result in secret exfiltration, unauthorized changes to repository contents, and the compromise of related NPM packages.
To better understand the Sysdig TRT’s initial discovery and the vulnerability’s impact, which could affect other CI/CD security products, let’s explore the team’s findings.
Unpacking the gluestack-ui vulnerability
Gluestack is a modern, cross-platform UI framework for building React and React Native applications, offering a utility-first styling system designed for native environments. Its core component library, gluestack-ui, provides customizable, themeable UI components like inputs and modals that work seamlessly across iOS, Android, and the web.
While analyzing the early June supply chain incident involving different NPM packages compromised in this repository, the Sysdig TRT examined the repository to identify possible root causes. The cause of the previously reported compromise was a stolen personal access token of one of the developers. However, we found an additional possibility in the GHA workflow discussion-to-slack.yml.
It’s worth mentioning that this newly identified vulnerability, CVE-2025-53104, is unrelated to the recent incident, in which attackers’ initial access was associated with stolen maintainer keys. However, this vulnerability found by the Sysdig TRT can cause the same result.
on:Add commentMore actions
discussion:
types: [created]
jobs:
notify-slack:
runs-on: ubuntu-latest
steps:
- name: Checkout code
uses: actions/checkout@v3
- name: Get discussion details
id: discussion-details
run: |
echo "title=${{ github.event.discussion.title }}" >> $GITHUB_OUTPUT
echo "body=${{ github.event.discussion.body }}" >> $GITHUB_OUTPUT
echo "url=${{ github.event.discussion.html_url }}" >> $GITHUB_OUTPUT
echo "author=${{ github.event.discussion.user.login }}" >> $GITHUB_OUTPUT
echo "category=${{ github.event.discussion.category.name }}" >> $GITHUB_OUTPUT
...Code language: YAML (yaml)The workflow above is triggered any time a GitHub Discussion is created. The information is then added to GITHUB_OUTPUT, which is then used to send a message via Slack. Because this workflow handles user-controlled inputs insecurely, such as title or body discussions, it is uniquely vulnerable to code injection.
An attacker can exploit this vulnerability by submitting a malicious payload as $(curl ...), in a new GitHub Discussion body or title. This action would trigger the workflow and execute arbitrary code in the GitHub runner instance. The attacker could then exfiltrate the GITHUB_TOKEN and other sensitive repository secrets available in the environment upon execution.
As illustrated in the screenshot below, the exfiltrated GITHUB_TOKEN had elevated privileges, allowing the attacker to make unauthorized changes to repository contents, releases, and workflows.
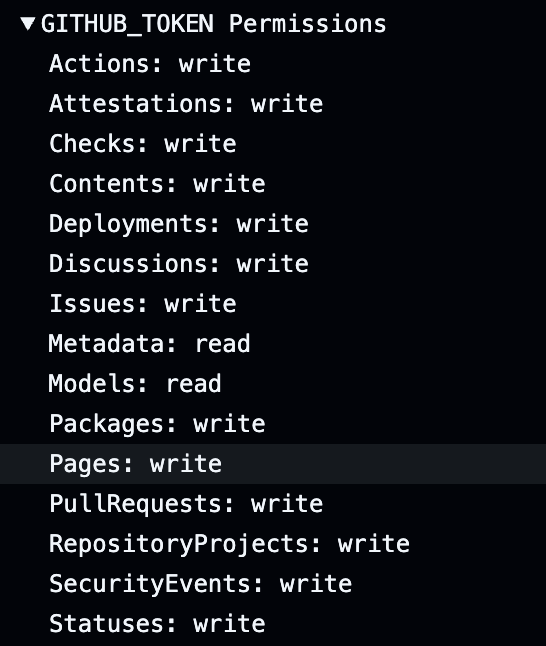
Manipulating existing releases or creating new ones could result in compromised NPM packages being published to the owner’s registry and open the door to a severe supply chain attack.
Impacts and mitigation
As noted above, CVE-2025-53104 has been assigned a CVSS v3.1 base score of 9.1. The integrity and confidentiality of a given repository are strongly impacted by this vulnerability:
- Integrity: By exploiting the vulnerability, the attacker can modify the repository’s content and create new releases and tags. This will also impact the integrity of both new and existing packages uploaded to the NPM repository.
- Confidentiality: The attacker can exfiltrate the repository’s GitHub token, along with other secrets in the repository.
CVE-2025-53104 has been mitigated with the release of a patch on June 13, 2025, which fixes the affected GitHub Actions workflow.
How to handle GitHub Actions inputs securely
It is crucial to manage inputs securely to avoid incidents like the NPM supply chain attack noted above. In GitHub Actions, it’s possible to handle user-controlled inputs using environment variables. We can associate an environment variable with each discussion part we want to hold in our workflow step.
env:
DISCUSSION_TITLE: ${{ github.event.discussion.title }}
DISCUSSION_BODY: ${{ github.event.discussion.body }}
DISCUSSION_URL: ${{ github.event.discussion.html_url }}
DISCUSSION_AUTHOR: ${{ github.event.discussion.user.login }}
DISCUSSION_CATEGORY: ${{ github.event.discussion.category.name }}Code language: YAML (yaml)Passing user-controlled inputs to env, such as title and body, ensures that they aren’t interpolated directly into commands, thereby avoiding command injections altogether. Additionally, all variables are quoted and used safely in logging and output.
Conclusion
Supply chain attacks and related threats are a top priority for modern security teams and developers, and they are quickly becoming a favorite tactic for attackers. By exploiting CVE-2025-53104, an attacker could inject arbitrary commands and potentially cause a serious supply chain compromise within NPM packages. To prevent such risks, it is essential to handle all user input securely and follow strict input validation practices.
Disclosure timeline
June 11, 2025 – The Sysdig TRT reported the security issue to gluestack maintainers
June 13, 2025 – gluestack maintainers acknowledged the reported issue
June 13, 2025 – gluestack released a patch to fix the security issue
June 30, 2025 – Public disclosure via GHSA with CVE-2025-53104


