Is cryptojacking draining your resources and exposing your organization to financial and reputation damage risk?
The rise in cryptojacking, which is an illegal form of mining cryptocurrency by the unauthorized use of someone’s computing resources, has reached alarming levels. According to the Google Threat Horizon report, 86% of compromised cloud instances in 2021 were used for cryptomining. That paints the picture quite clearly. So, going back to the opening question, it is wise to consider the possibility.
Cloud environments are attractive targets
Cloud environments are especially attractive to cryptojacking. They offer on-demand, auto-scaling resources for these computation-hungry invaders. While organizations struggle to implement effective security in the cloud due to the lack of visibility and control into what is going on with their cloud security settings, Kubernetes clusters, and inside their containers, threat groups like TeamTNT, WatchDog, Kinsing, among others, have been taking full advantage of this opportunity window. They have been feasting on cloud resources by exploiting cloud weak security controls, vulnerabilities in container workloads, as well as Kubernetes and Docker attack vectors.
Despite their prevalence in today’s cyber threat activity, cryptojackers are not easily detected. There are thousands of variations of cryptominers and they operate in stealth mode. Many organizations live with this kind of parasite oblivious of the danger that they truly represent. And although perceived as less dangerous than other types of attacks like ransomware, the risk incurred by cryptojackers goes way beyond scary unexpected six-figure bills.
Hefty bills are not the whole story
Cryptojackers can provide an entry point to the entire cyber threat landscape. While hijacking CPU and GPU resources, they also operate by disabling detection mechanisms facilitating the download and installation of other malware payloads, such as ransomware. The more sophisticated ones can look for credentials and SSH keys, spread to other systems like worms, and establish backdoors and connections to C2 sites, among other malicious activities. Attacks today have become multi-purpose, so waiting for the first spike in cost or application performance complaints to arrive to look for cryptominers in your environment, is late, more than you think. Time is of the essence.
Using machine learning to early detect cryptominers with 99% precision
Cryptominers are masters of evasion, that is their trade trait. But, as cryptominers, they have to fulfill certain operations necessary for mining coins, and that makes them recognizable from a behavioral perspective. By analyzing the behavior features of cryptominers, it is possible to detect even new variations of cryptominers throttling the use of cloud resources to stay under the consumption radar.
For this type of detection, which requires multiple data sources and the analysis of complex condition combinations to find a behavior match, machine learning offers the best approach. But, can all machine learning-based threat detection be effective to detect cryptominers? The short and truthful answer is no.
There is a lot of misleading information when it comes to machine learning. Anna Belak explains quite well in her article, The Beautiful Lies of Machine Learning in Security, how machine learning has been misrepresented as a security solution. But Anna also shows the benefits that machine learning can deliver when applied with focus.
How Sysdig does machine learning for cryptojacking detection
Sysdig’s machine learning solution to detect cryptominers stands out from other approaches to cybersecurity. Thus far, machine learning has been used to detect anomalies as an indicator of a potential threat. But, without a specific targeted use case, this leaves a large margin for false positives and also for missing more advanced stealthy threats, like cryptominers.
Sysdig solution is based on an ML model trained to recognize the anatomy of cryptominers from process activity in running containers. Sysdig uses deep visibility into containers at runtime to collect the necessary type data to be able to identify cryptominers behavior.
To know more about how Sysdig does it, check the blog Cryptominer Detection: A Machine Learning Approach by Flavio Mutti, Senior Machine Learning Engineer at Sysdig.
Enabling cryptominer detection with Sysdig Secure is very easy:
- On the Sysdig Secure platform, go to the Runtime Policies.
- Select Machine Learning Policy.
- Enable cryptominer detection in your environments.

Once the policy is enabled, the Sysdig machine learning pipeline will start detecting crytominers in running containers.
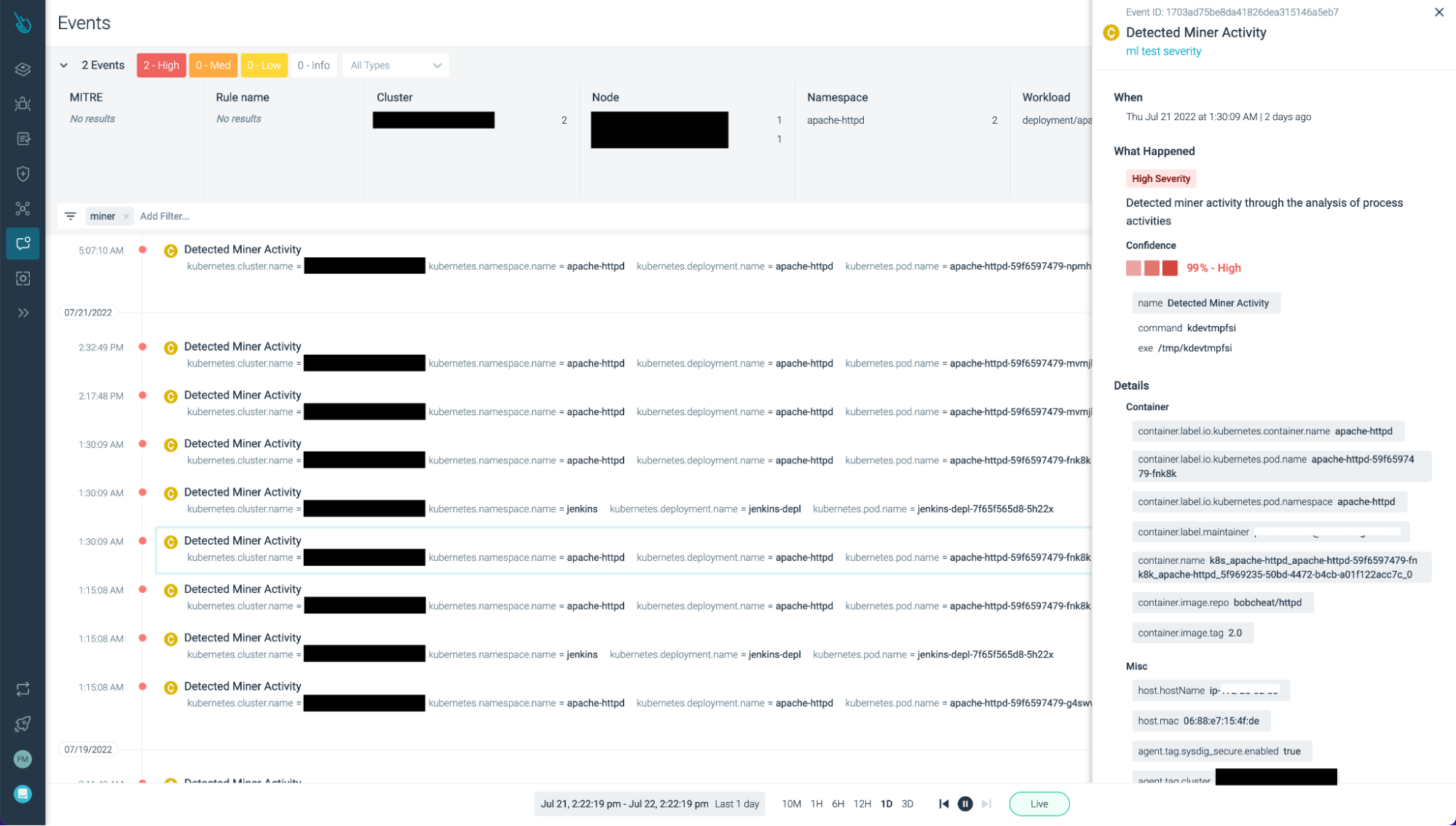
Real use case: Stealth cryptominer detection
On November 11, 2022, Sysdig received an alert that the machine learning miner detection system detected a potential threat. Our prior experiences indicate that classic miners usually provide us with a confidence probability above 96% and while it is still considered high confidence, this suspicious process alert had a probability of only 81%. The name of the suspicious process was associated with kernel activity workers. This was the first time a kworker process was detected as anomalous, so we decided to investigate further to determine if this was legitimate malicious activity or a false positive.
The alerted process was in fact a miner, it was even classified as such on VirusTotal! The toolchain within the process was quite complex, involving tactics from reconnaissance to defense evasion. While machine learning can provide the first evidence of unusual activity, this case also reiterated the importance of managing machine learning and providing human oversight to improve automated efforts.
This event proved useful in demonstrating the effectiveness of machine learning to detect malicious activity as a complement to traditional rule-based detectors.
Key Benefits of Sysdig’s Machine Learning for Cryptojacking Detection
- Detect cryptominers with 99% precision and enable a streamlined workflow to counter cryptojacking activities efficiently.
- Prevent unexpected costs, reputation damage, and exposure to additional malware by early detecting the cryptojacking attack.
- Strengthen security with a multi-layered approach to cloud detection and response by implementing rule-based detection and machine learning protection layers.
Conclusion
Sysdig took the approach of developing a machine learning solution that focuses on detecting cryptominers. And by doing so, it provides an effective detection mechanism with precision of up to 99%. The gains from a focused machine learning solution are multifold, from enabling fast detection and response to cryptojacking attacks to drastically reducing the number of false positives, which is very welcomed by security teams already stretched thin and dealing with alert overload and fatigue.
But machine learning is just one defense layer in Sysdig’s multi-layered detection approach. Sysdig’s rules-based approach based on Falco provides easily customizable out-of-the-box policies curated by the Sysdig Threat Research Team to maximize coverage. Other defense techniques, such as profiling, comprehensive indicators of compromise (IOCs), and Drift Control further strengthen security.

