Runtime Insights are Required in the Cloud
To secure innovation in the cloud, you need runtime insights to prioritize the most critical risks and stay ahead of evolving threats.
Shift Left the Right Way
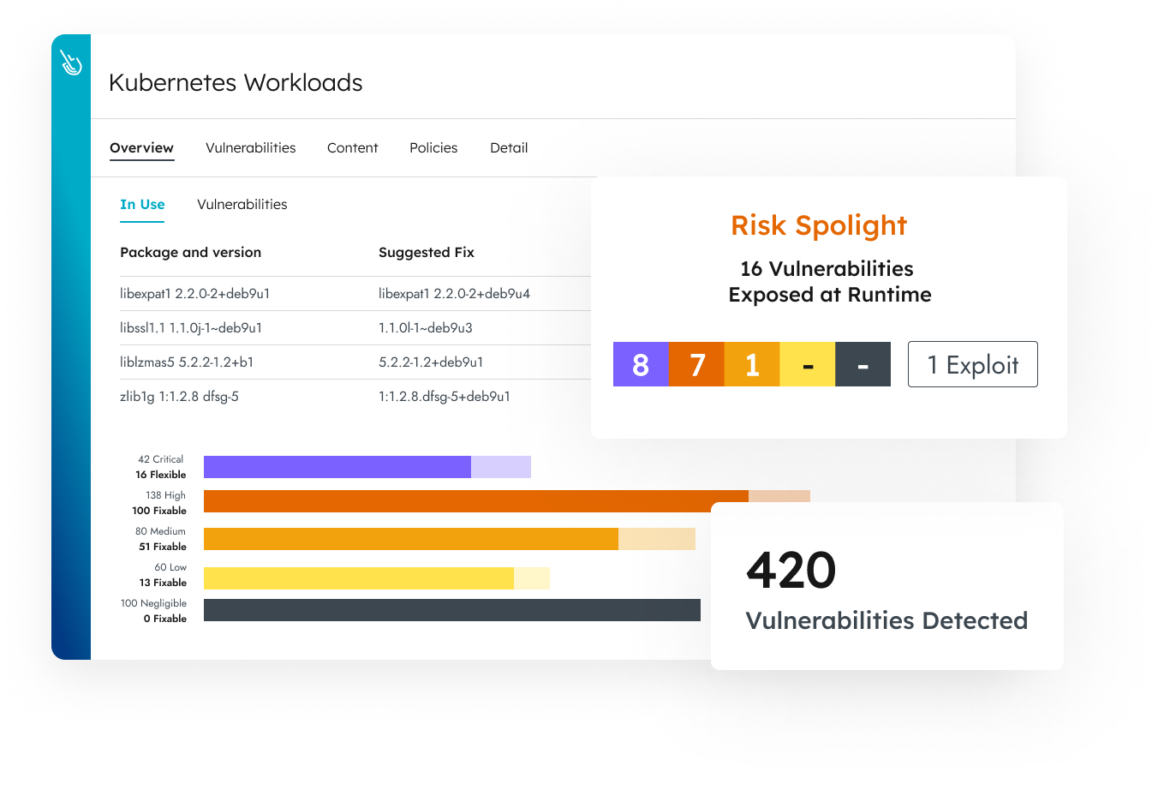
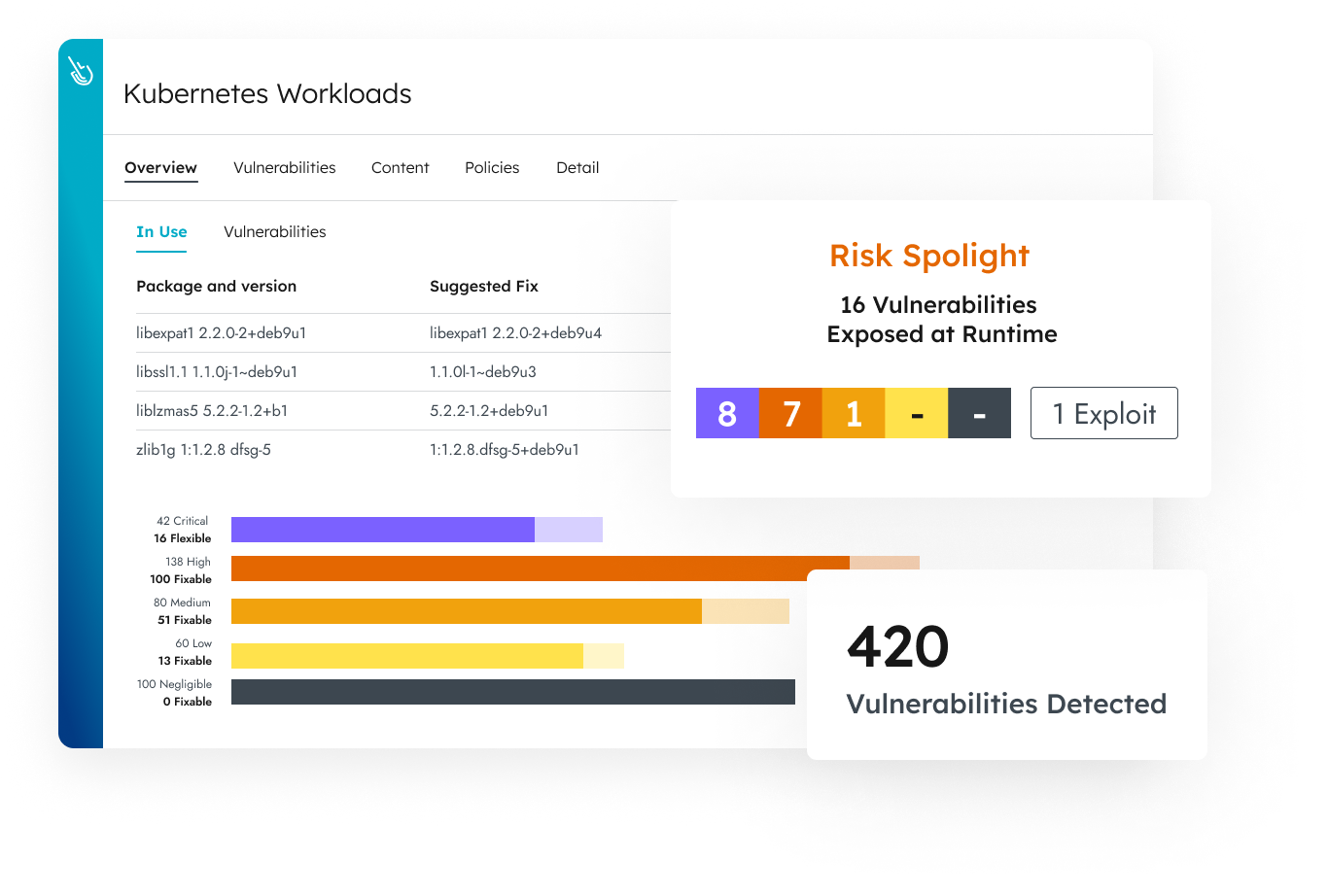
Runtime insights help prioritize the most critical security issues by focusing on what’s in use. Leverage context such as in-use vulnerabilities and in-use permissions to address the most exploitable risks immediately and reduce alert fatigue.
After using Sysdig, we have seen two hour time saving per vulnerability and 75% false positive alert reduction.
Security Analyst, Neo4j
Shield Right in Real Time
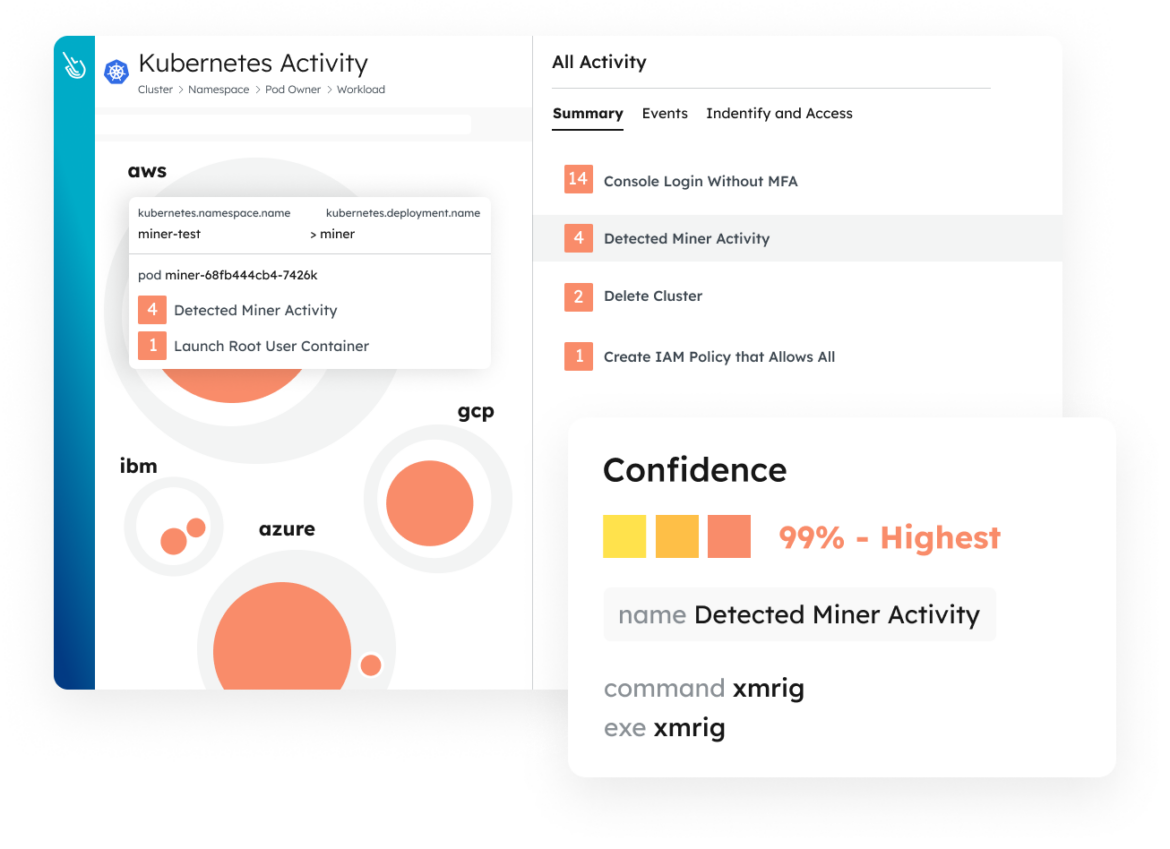
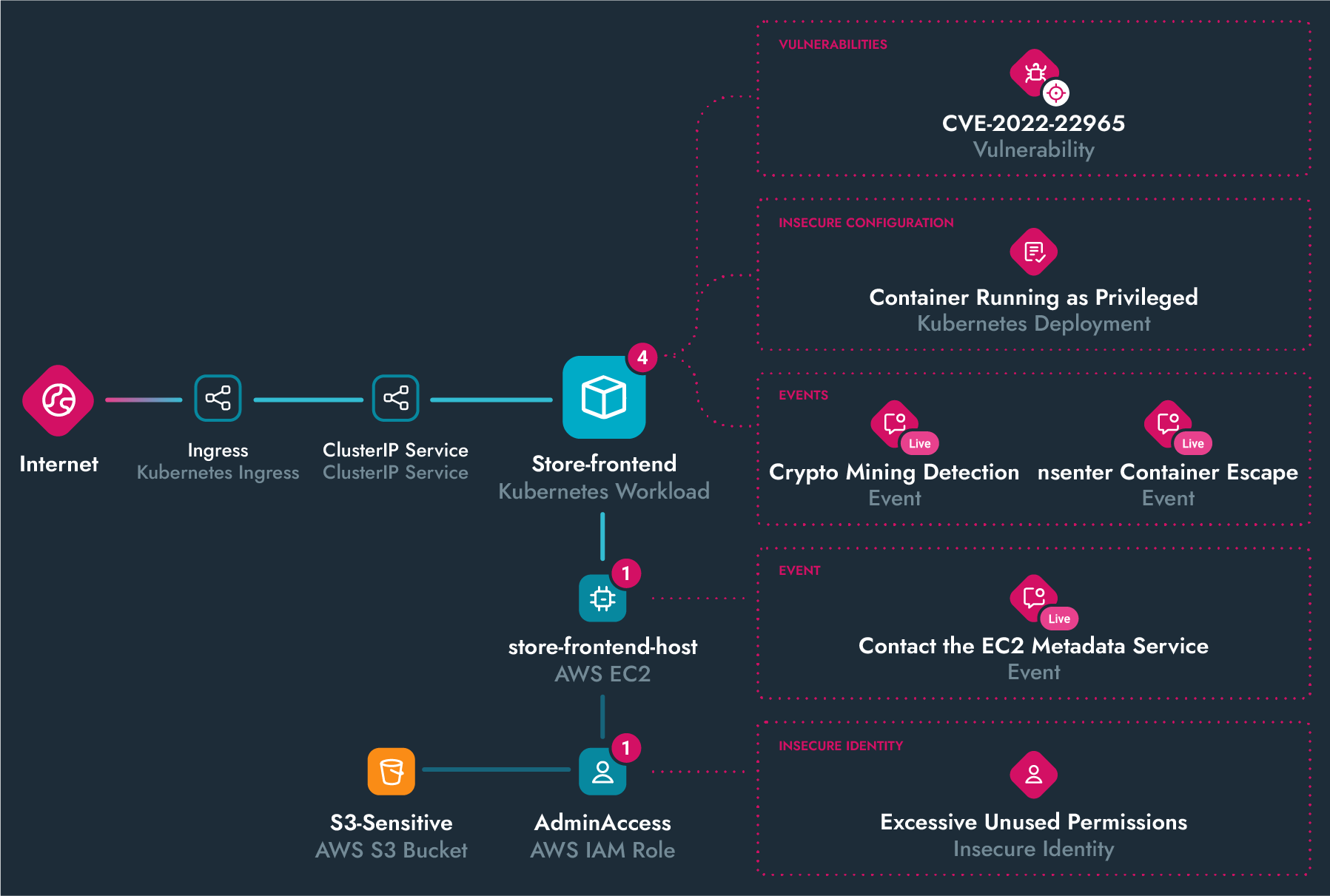
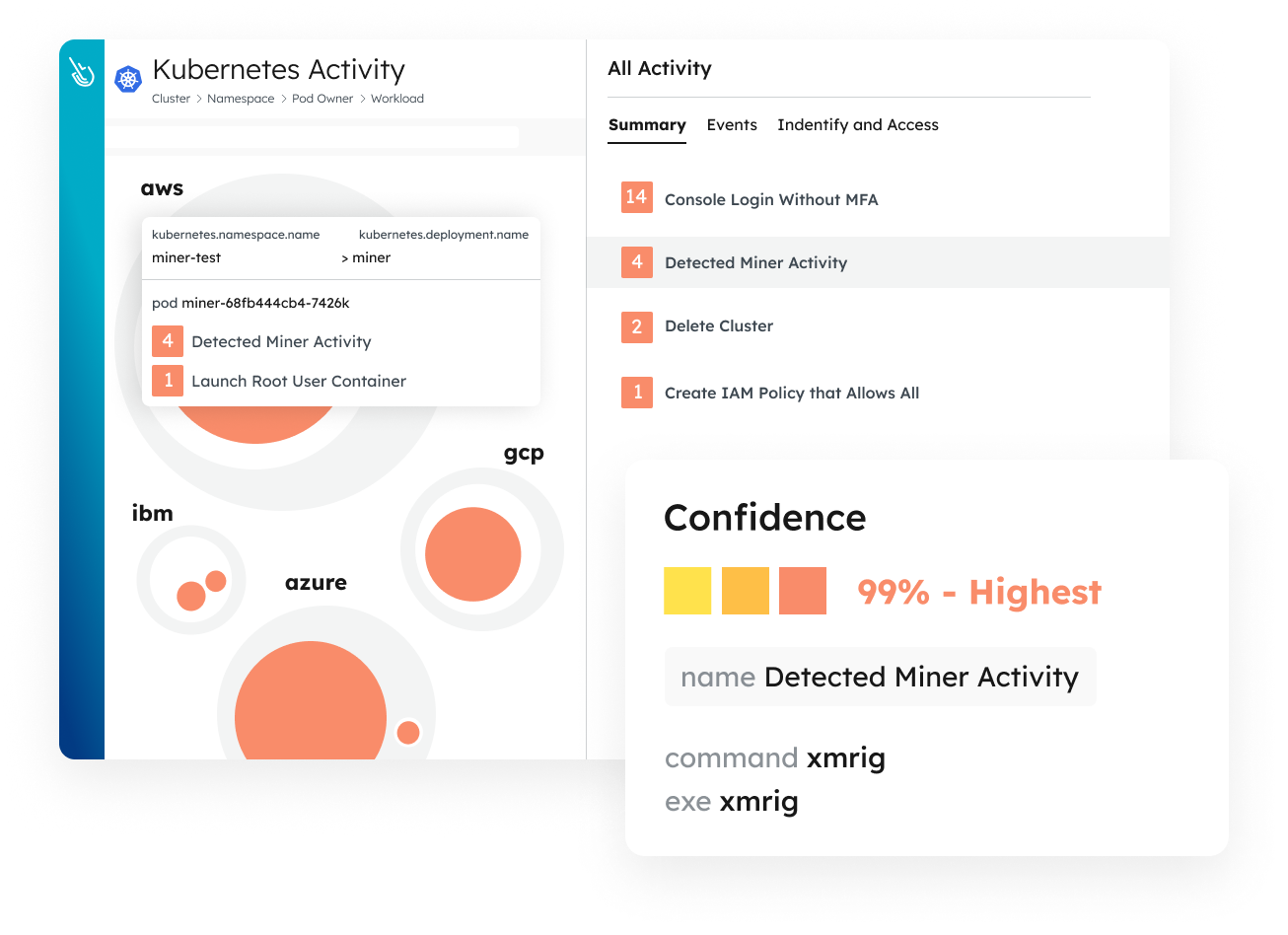
Runtime insights help you detect and respond to threats in real time. Correlate activity across containers, cloud services, servers, and identities to reveal active lateral movement. End-to-end detection combines drift control, machine learning, and Falco detections to combat the most advanced threats.

Sysdig enables us to quickly detect and respond to cloud attacks at cloud speed by knowing what is happening, the exact container or location in the cloud, and what is causing it, versus the hours it used to take to detect and understand what needs to be done.
Platform Tech Team Lead, Fuel50
Runtime Insights
are Built on Falco
Cloud-Native, Real-time Protection, and Open Source
Falco is the open source runtime security solution for real-time detection of threats and anomalies across containers, Kubernetes, and cloud services.
Through deep visibility of your entire cloud-native infrastructure, Falco enables cloud-native application protection platforms (CNAPP) with end-to-end detection and powers Sysdig’s prioritization based on in-use packages.
Learn moreConsolidate in a Single CNAPP
Security teams need an integrated tool that provides continuous visibility of your entire environment. Sysdig’s Cloud Native Application Protection Platform (CNAPP) uses runtime insights to stop attacks across the application life cycle.
Vulnerability Management
Reduce vulnerabilities by up to 95% and boost developer productivity with actionable runtime insights through visibility into critical in-use packages.
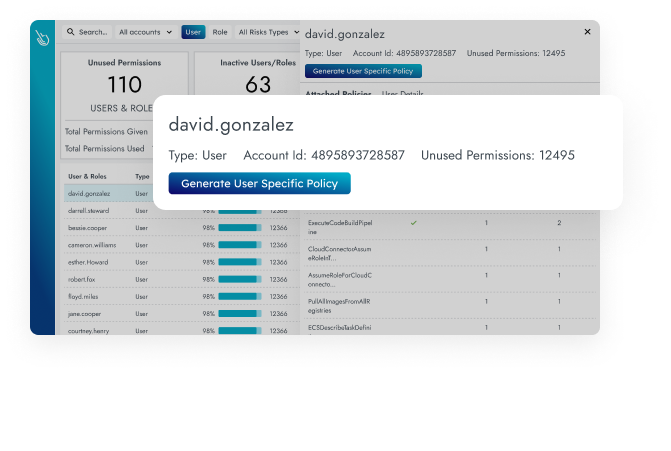
Permissions & Entitlement Management
Close permissions gaps in minutes by focusing on what’s in use. Grant least privilege access with a single click.
Posture Management
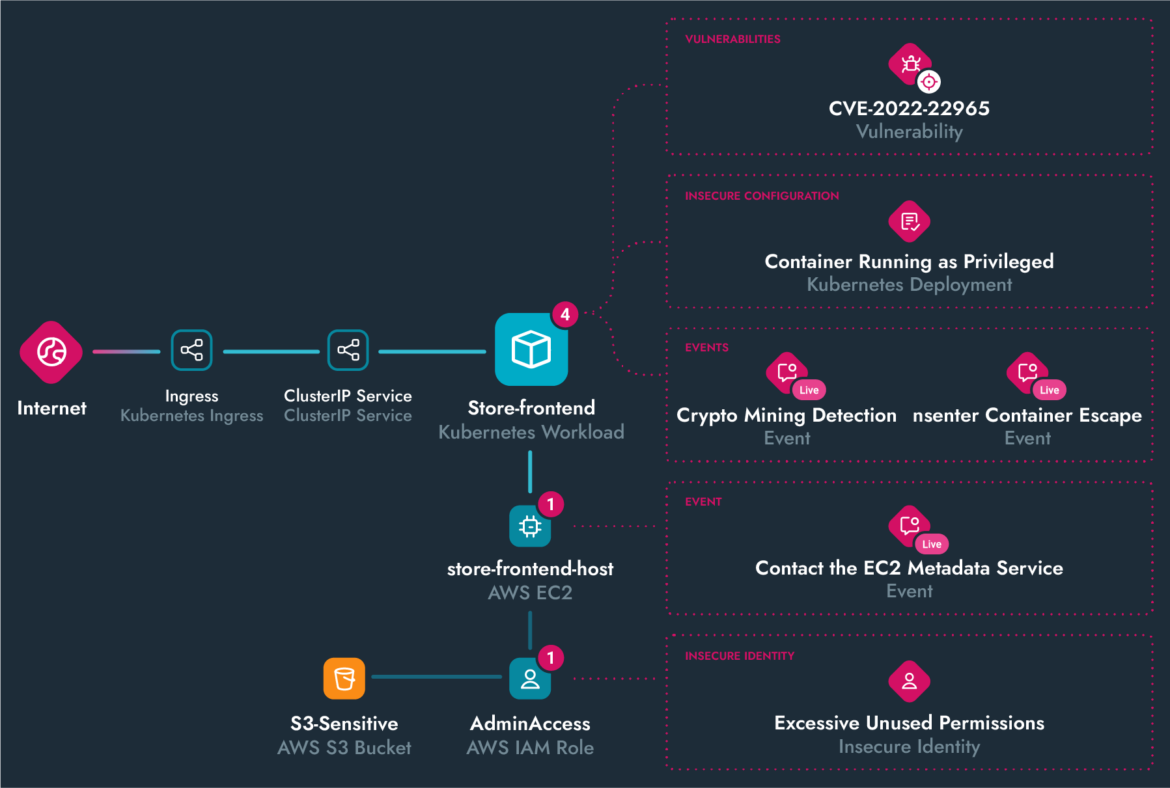
Prioritize and remediate misconfigurations at cloud speed. Uncover hidden attack paths and generate a list of all your riskiest findings to harden your defenses.
Cloud Detection and Response
Stop cloud breaches in real time. Detect threats in seconds and combat advanced attacks with multidomain correlation.
Eliminate Blind Spots with Real-time Visibility
Ditch the snapshot approach for detection. Level up your visibility with real-time streaming detection utilizing data and logs across multiple domains within your cloud infrastructure.
Learn More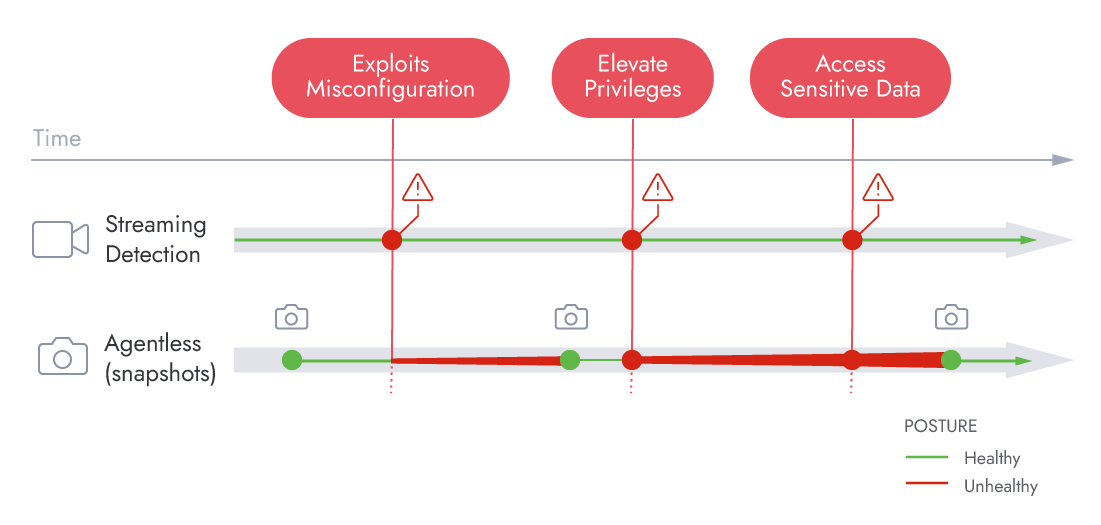
Take the Next Step!
See how you can secure every second in the cloud.