Remember asking your teachers when you would need to know history facts outside of school? They probably said that learning history is important in understanding our past and how society has changed and progressed over time, and that we can learn from past experiences and mistakes.
They were right, of course (even if it might not have felt like it then). And that’s all equally true when it comes to the history of security. How did we evolve to the modern state of cybersecurity, and what does that tell us about the best path to take going forward?
Luckily, when it comes to cloud security, there’s no need to dig through archeological ruins for scattered clues — this history is recent, accessible, and ready for us to learn from. So let’s dive right in.
Where we came from
The development of endpoint security
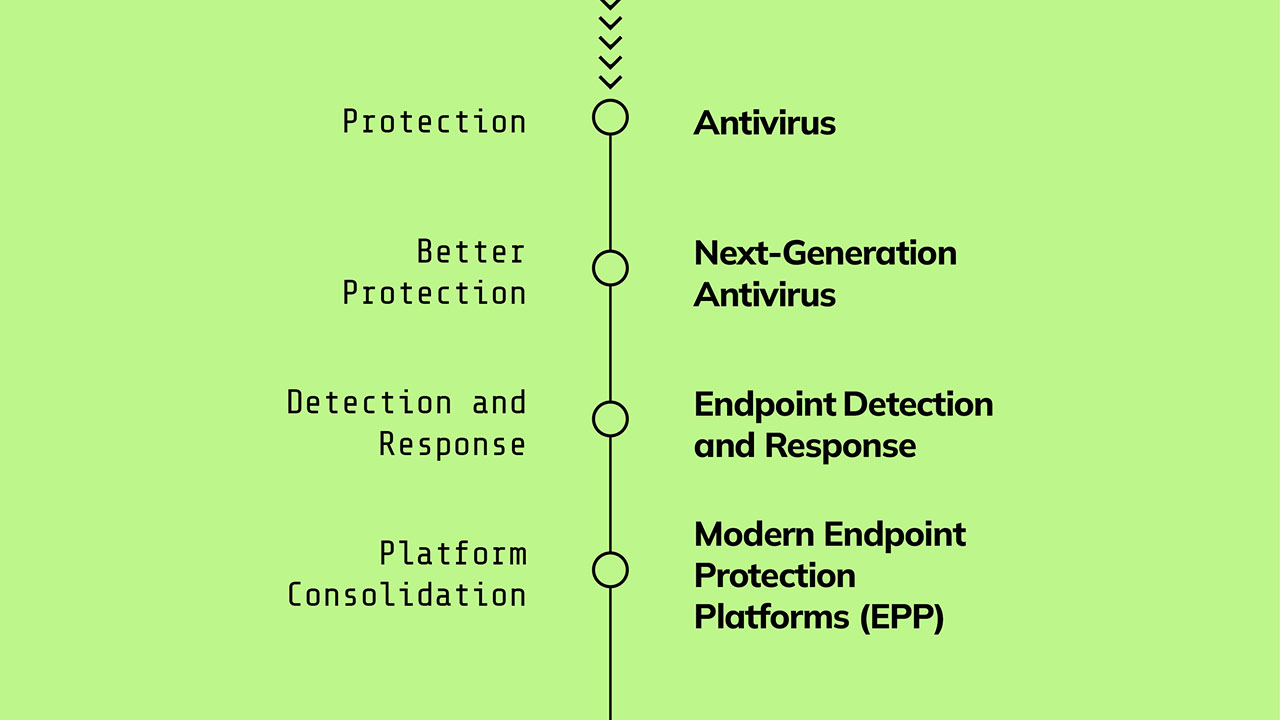
The journey from the first antivirus product offerings to today’s endpoint protection platforms (EPPs) started in the 1980s and went through a wild ride of progression and consolidation over the past 40 years. By the late 1990s and early 2000s, computer viruses like the ILOVEYOU worm and the Anna Kournikova virus had begun spreading across the globe, taking advantage of skyrocketing internet use.
To combat these threats, the first antivirus software (including notable examples like Anti-Virus eXpert and ClamAV) sprang up, using signature-based methods to shield systems against a database of known viruses. These products would hunt for threats inside a system by looking for indicators of compromise (IoCs), or artifacts in a system that tend to suggest the presence of an intruder, like suspicious IP addresses, hashes, filenames, and more.
In response came polymorphic malware, which could modify its code to evade signature-based detection. Now, attackers could change their hash for every attack, and the same attack might involve different IoCs — even against the same victim. Traditional antivirus couldn’t keep up. So instead, next-generation antivirus (NGAV) solutions were developed, using machine learning and behavioral analysis to sniff out threats regardless of whether they were known or unknown.
But this approach to security still relied entirely on blocking threats at the perimeter of a system, with no way to detect attacks that successfully infiltrated a network. To fill this gap, endpoint detection and response (EDR) software was created, with the ability to monitor, detect, and respond to threats in real time. Over the years, EDR software has been greatly refined and expanded, and for a time, it seemed all we would have to do was continue improving our EDR and endpoint solutions, and we’d all be safe from cyber attacks.
The great cloud migration
Then came the next great big bang of cybersecurity: the migration to the cloud. From a security standpoint, the cloud is an entirely different type of attack surface — one that is orders of magnitude larger and faster-moving than anything that exists on-premises.
Operating in the cloud armed with nothing but on-premises endpoint protection and EDR security left organizations open to cryptojacking, cloud data breaches, abuse of human and machine identities, and many more types of attacks. Add in the speed of cloud attacks and the limited visibility many organizations have into their cloud environments, and it’s no wonder that news stories about successful cyber attacks seemed to be mounting by the day.
Relying on security tools and processes built for on-premises environments clearly wasn’t going to cut it. And so came the introduction of new breeds of security software, built expressly for the cloud.
Just like the early days of endpoint security, the initial approach to cloud security was all about prevention. This meant turning to cloud security posture management (CSPM) and cloud infrastructure entitlement management (CIEM) to enforce security controls and monitor for vulnerabilities, misconfigurations, and potential threats. These solutions have been game-changers, and today they’re an essential part of every organization’s security stack. But like purely preventative endpoint security before, they’re not enough.
Where cloud security needs to go next
There’s a logical next step in this story. In the days before the cloud, we needed EDR to detect and respond to threats that made it past the initial lines of defense and into an organization’s network. Today, the industry is realizing that we now need detection and response in the cloud for the same reasons.
Unfortunately, many organizations are still opting for a makeshift cloud security strategy by expanding their current EDR solutions to cover their cloud environments. This seems to be the simplest solution at first glance, but the reality isn’t so straightforward. EDR solutions and their cousins, extended detection and response (XDR) solutions, are fundamentally unsuited for the cloud.
EDR and XDR lack the visibility necessary to monitor cloud environments, creating huge security gaps that attackers know they can squeeze through. These tools are also unable to match the breakneck speed at which threats can move in hybrid and multi-cloud environments, or to meet the 555 Benchmark for Cloud Detection and Response.
The unique nature of the cloud demands purpose-built detection and response capabilities, and thankfully, the security market is evolving to deliver just that with true cloud detection and response (CDR) solutions. CDR software offers advanced detection and response across a wide array of cloud technologies: containers, Kubernetes, serverless computing, cloud logs and trails, and both Linux and Windows servers.
A good CDR solution can detect known and unknown threats across your cloud estate in real time, accelerate investigations, and automate threat response. These are the core capabilities that make a CDR distinct from an XDR. Where XDR provides siloed, fragmented data on cloud environments, a proper CDR solution should automatically correlate information across events, vulnerabilities, and identities, providing the rich context analysts need to investigate threats at the speed the cloud demands. And the flexible, automated response options CDR solutions offer empower teams to respond faster than threats can act in clouds or containers. With these end-to-end capabilities, CDR ensures that security teams can match the rapid pace of cloud environments, tackling cloud threats head-on and in real time.
So let’s learn from the past. Now that we’ve got the prevention piece of the puzzle in place, it’s time to make use of cloud detection and response to truly guard cloud environments from the inside out — and to make our way to a more secure future.
Want to learn more? Read the full ebook, The Evolution of Cloud Security: From Prevention to Detection and Response.