Attack surfaces in the cloud are expanding at a breakneck pace. Cloud security has reached an unprecedented level of complexity — ranging from misconfigurations and vulnerabilities to advanced threats and compliance challenges, all while malicious actors are increasingly using generative AI to target your cloud infrastructure.
At Sysdig, we understand these challenges better than anyone. As cloud adoption accelerates and organizations embrace increasingly complex architectures, security teams are grappling with a diverse set of issues, from runtime threats to ever-shifting infrastructure and cloud-native applications. With our November 2024 launch focused on cloud security posture management (CSPM), we’re giving you the tools to stay ahead of these challenges.
1. Custom risks: Take back control of risk management
One-size-fits-all security doesn’t work, especially in the cloud. Whether you’re working with containers, Kubernetes, or multi-cloud environments, each organization has a unique security posture — and a set of threats that requires a tailored approach.
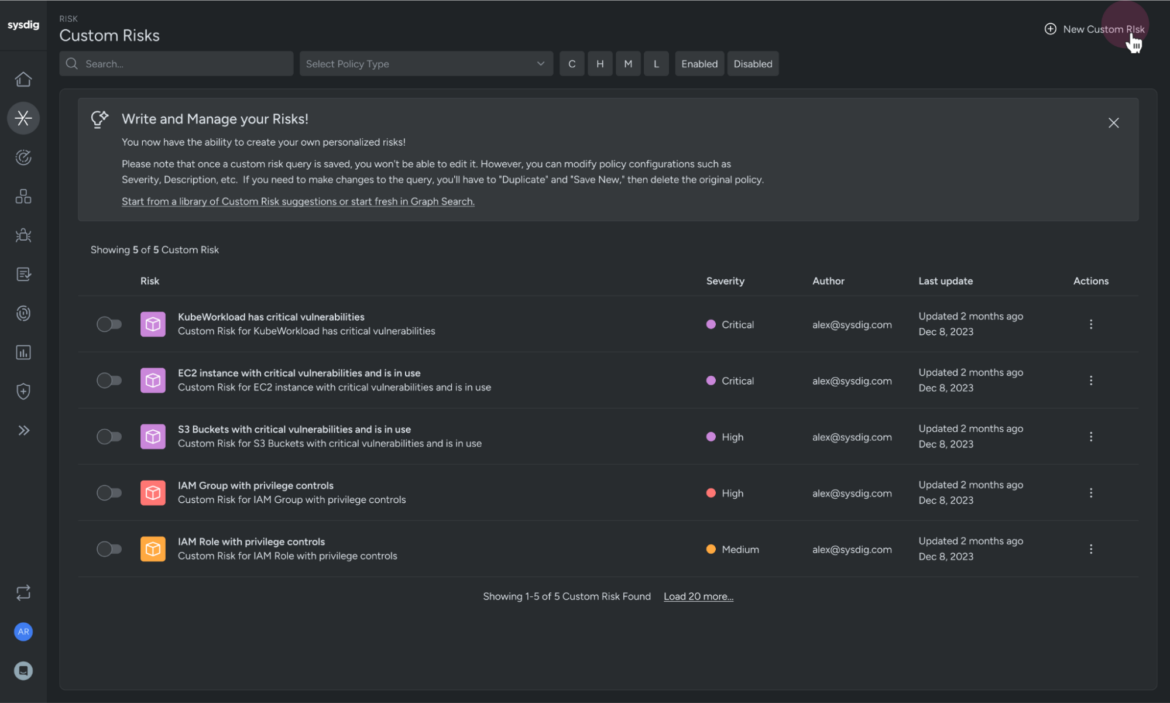
Sysdig’s Custom Risks feature was built with this in mind. It allows security teams to define, write, and execute on their own custom risk patterns — a level of flexibility and control that gives you the ability to create adaptive queries tailored to your environment and your specific risk appetite. For example, if your team is working with high-risk workloads on AWS cloud in a regulated industry like finance, you can tag them with relevant labels and create a custom query for such risk markers. We give you back the power to customize your risk management strategy.
2. Customizable controls: Tailored to your needs
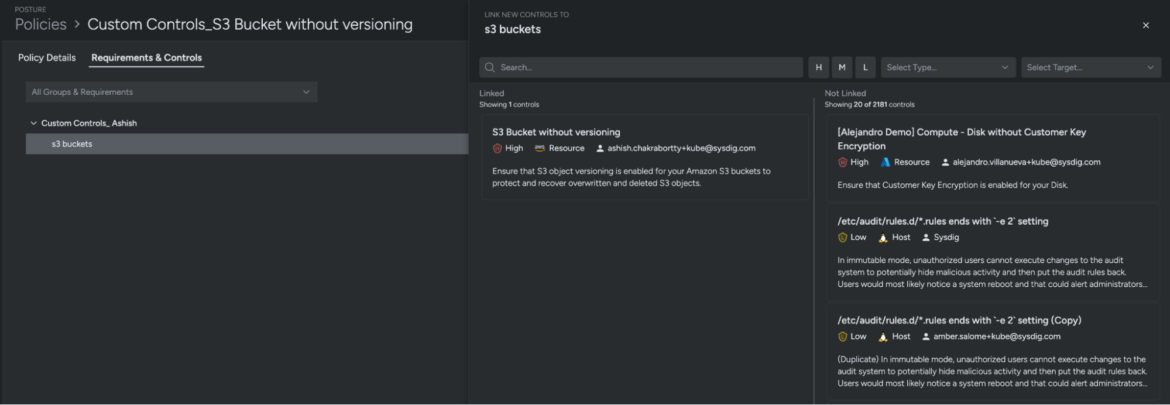
Cloud security is not static, and your controls shouldn’t be either. With Sysdig’s Custom Controls, security teams can tailor security policies and compliance checks to their organization’s unique needs:
- Define your own security policies and controls leveraging OPA, Rego and Terraform that align with the specific risks of your cloud environment.
- Stay compliant with regulatory frameworks while simultaneously ensuring the security of your cloud resources.
3. Graph Search: Proactive and adaptive, not reactive
Due to the dynamic nature of cloud infrastructure, security teams are often in the position of reacting to threats after they’ve already taken root. A much-loved feature within our Sysdig platform is our ability to identify evolving threats in real time.
We have built on top of this capability with Sysdig’s Graph Search, so that you can proactively search for risky patterns before they become full-fledged threats. Imagine this: A new development team launches an application, and in the process, they accidentally expose sensitive cloud assets to the internet. With Sysdig’s Graph Search, you can spot these risky configurations before a potential breach or misconfiguration escalates.
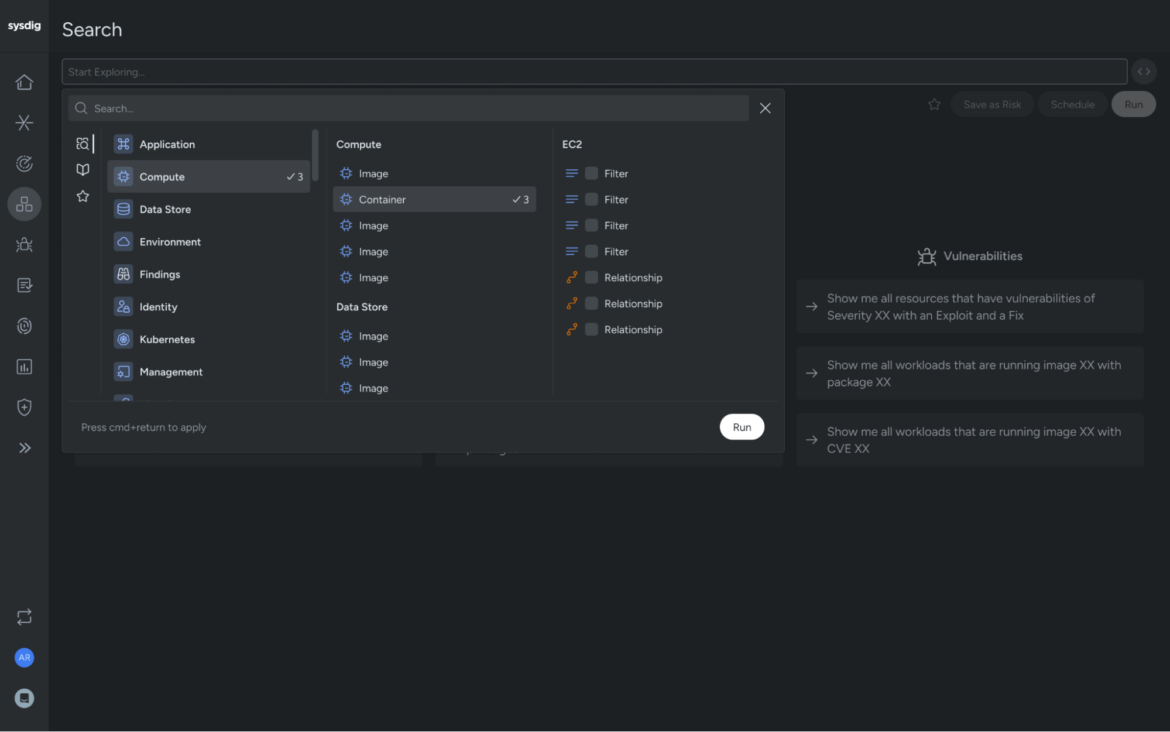
By leveraging a graph database enhanced with runtime context, Sysdig’s Graph Search doesn’t just let you track vulnerabilities; it empowers you to find and prioritize evolving patterns of risk in real time. This is the kind of proactive security that every CISO wants to build into their organization’s DNA — catching issues early, staying ahead of threats, and minimizing risk exposure.
4. Clear reporting for your leadership team: Show the security impact
One of the greatest challenges product leaders encounter is communicating the value of complex security programs to executives. Security teams understand the intricacies of risks, but executives and key stakeholders need clear, actionable insights they can compare with business value to make informed decisions.

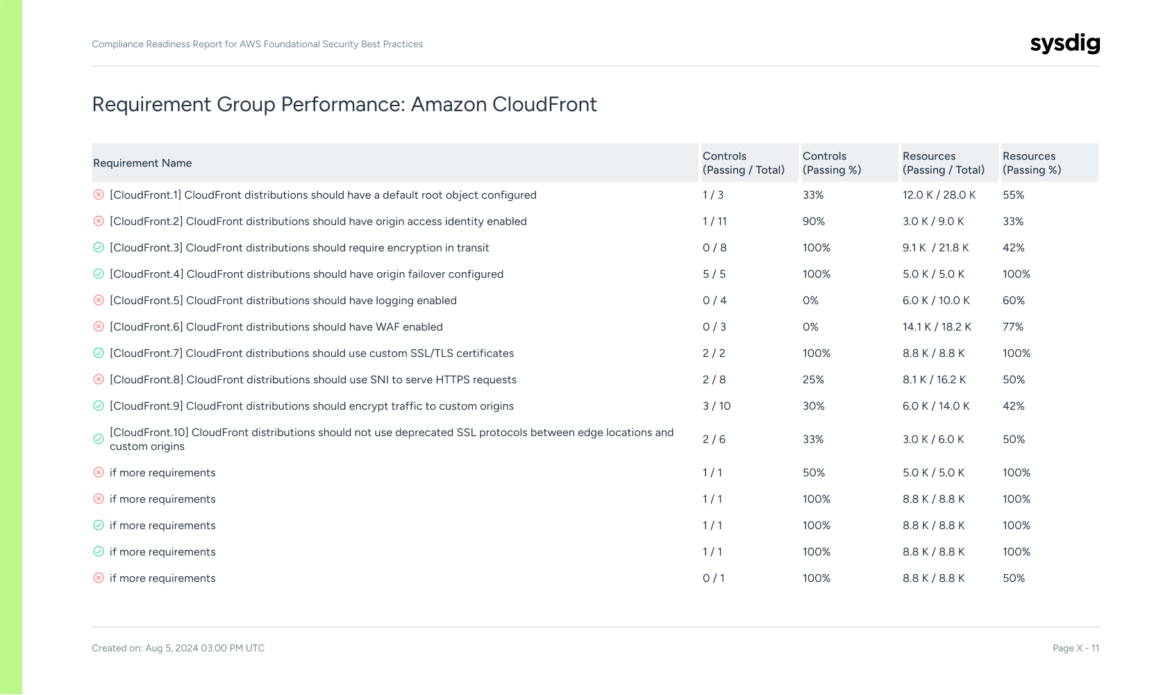
Sysdig’s CSPM Reporting feature solves this problem by providing clear, concise reports that communicate the impact of your CSPM initiatives in terms everyone can understand. With real-time insights into your security posture, key risks, and ongoing mitigation efforts, you can demonstrate the effectiveness of your security program to leadership and other stakeholders — ensuring that security is always aligned with business goals.
5. Roadmap item – Resource 360: You cannot protect what you do not see
We also have further important features planned for the near future, like Resource360. One of the most pressing challenges security teams face is visibility. You can’t protect what you can’t see, and in cloud environments, resources are constantly being spun up, torn down, and changed in ways that make traditional security models ineffective.
Resource 360 is Sysdig’s answer to this challenge. It gives you a complete, real-time view of your cloud resources, allowing you to understand at a glance where risks are occurring, on a resource in one place.
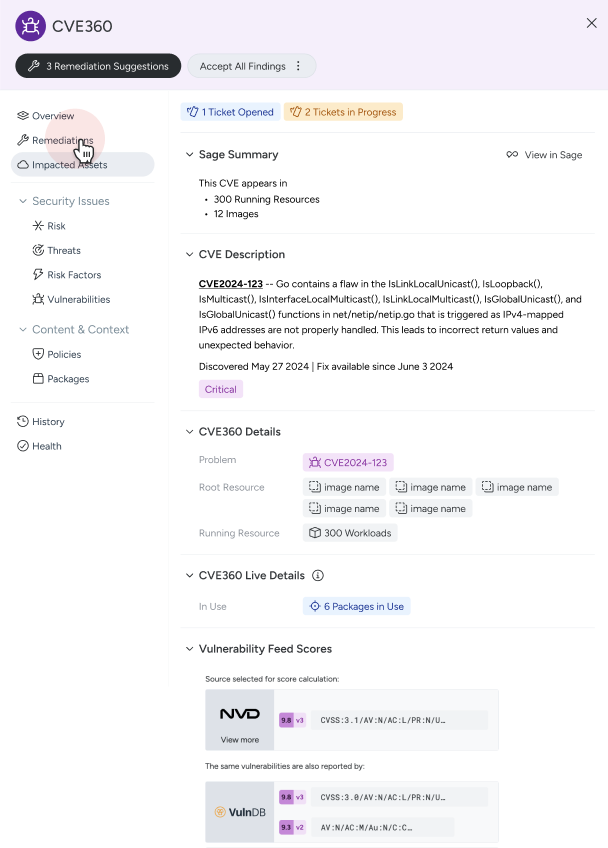

The real magic of Resource 360 is that it doesn’t just offer visibility; it ties that visibility to real-time security events and context. It helps in understanding the security posture of each resource at any given moment and having the context you need to make informed decisions.
For security teams who need to respond quickly to incidents or manage large, dynamic cloud environments, this level of visibility is indispensable.
A more proactive, flexible, and insightful approach to CSPM
We’ve designed our solution with one goal in mind: to help organizations take control of their cloud security posture in a way that’s both adaptive and actionable.
TLDR:
- Custom Risks: Fully customizable risk patterns to match your unique cloud environment.
- Graph Search: Real-time, graph-powered searches that let you proactively identify and prioritize evolving risks.
- Resource 360: Comprehensive visibility into your cloud resources, tied to real-time security events.
- Customizable Controls: Tailored security policies and compliance checks across Kubernetes, containers, and cloud infrastructure.
- CSPM Reporting: Actionable insights and clear reporting for leadership and key stakeholders.
At Sysdig, we’re committed to providing security teams with the tools they need to manage risks, enforce policies, and secure cloud environments — whether they’re on a journey to the cloud or already fully cloud-native. This is the future of cloud security, and we’re excited to help you take control.
Do you want to see these features in action? Click here to get a demo.


