As the adoption of cloud-native technologies like containers, Kubernetes, and microservices have evolved, traditional security solutions have struggled to keep up. According to the Sysdig Threat Research Team (TRT), the average time it takes an attacker to perform reconnaissance and complete an attack is just 10 minutes. To help teams outpace attackers, cloud-native application protection platforms have emerged. This space includes both established security vendors pivoting to the cloud and specialized providers, like Sysdig, who have delivered solutions purpose-built for the cloud’s ever-growing attack surfaces.
Today’s cloud-native application protection platforms (CNAPPs) need to go beyond basic posture assessments, by providing real-time detection, and response while offering the flexibility to meet the specific security needs of different organizations. Multiple businesses adapted solutions that were posture-centric and left runtime protection as a problem to be solved for later. By contrast, we at Sysdig are strongest in runtime protection and detection and response for the cloud, and have gradually added stronger CSPM and risk-oriented features in the last few years. Companies that neglect runtime and detection and response are setting themselves up for failure, because it’s not a matter of if they will be attacked in the cloud; it’s a matter of when. With so many options available, the real challenge is finding a solution that not only keeps pace with the speed of the cloud but effectively secures cloud environments.
Sysdig rated top CNAPP
in Customers’ Choice category in Gartner® “Voice of the Customer” report
Critical requirements for a complete CNAPP
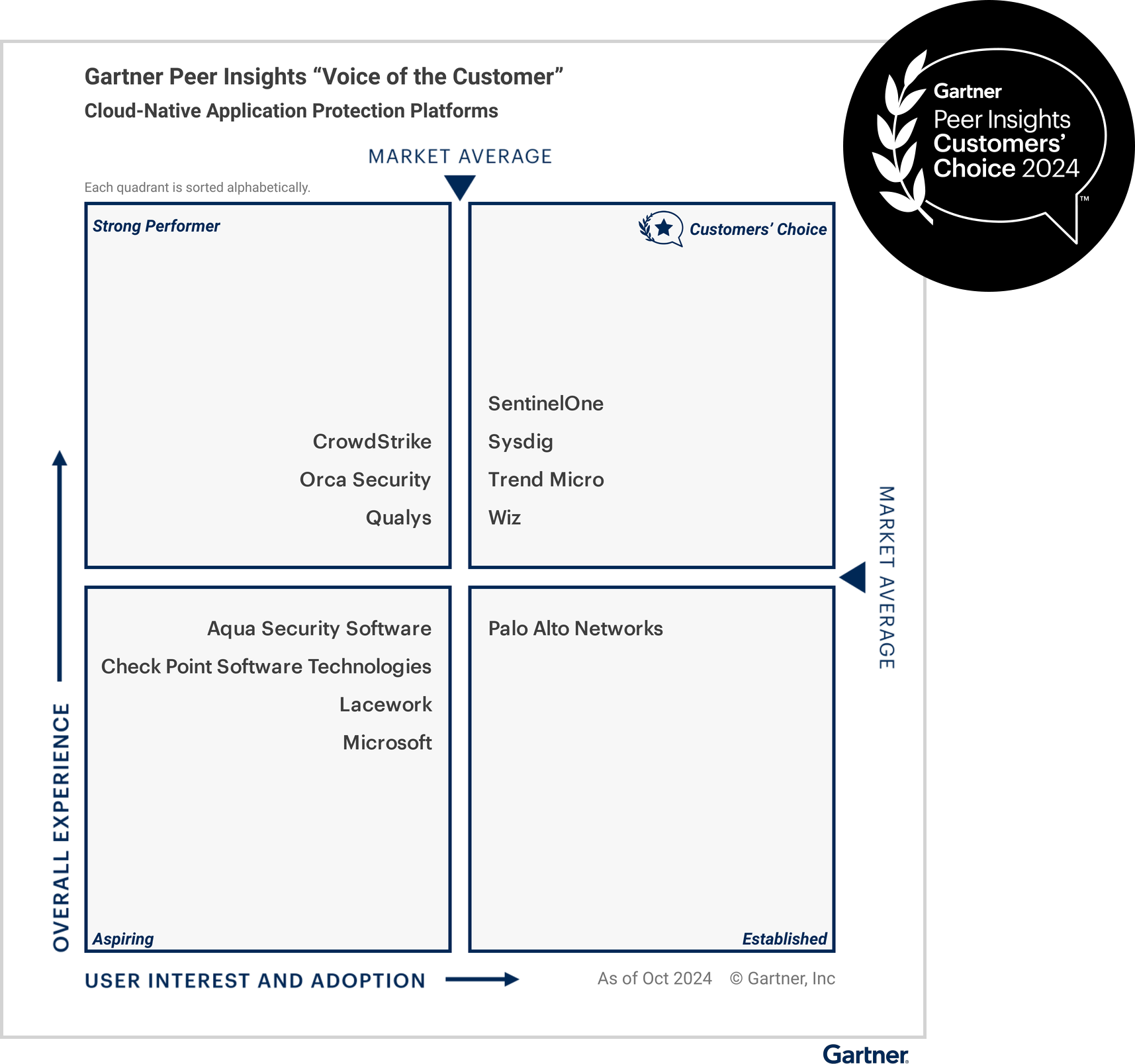
Gartner Peer Insights™ is a valuable resource for organizations looking to evaluate security vendors because it reflects the voices of real customers who use these platforms daily. These reviews focus on the actual experiences organizations have with cloud security vendors. Gartner published their latest “Voice of the Customer” report for cloud-native application protection platform tools.
What is clear from the reviews is that a complete cloud-native application protection platform (CNAPP) must integrate several key security solutions to provide comprehensive protection across cloud environments, including:
- Cloud workload protection platforms (CWPP): CWPPs provide visibility and control over various workloads — including physical machines, virtual machines, containers, and serverless environments across public, hybrid, and multi-cloud deployments.
- Cloud security posture management (CSPM): CSPM solutions enable continuous monitoring, identification, and remediation of compliance risks and misconfigurations within cloud infrastructure.
- Cloud detection and response (CDR): CDR solutions deliver advanced threat detection, real-time incident response, and continuous monitoring tailored to the cloud. CDR solutions leverage cloud-native security controls for in-depth visibility into cloud assets, configurations, and activities.
- Vulnerability management (VM): VM solutions scan for weaknesses across cloud environments, identifying and prioritizing potential threats before they can be exploited. It helps manage, remediate, and mitigate vulnerabilities in apps, workloads, and infrastructure.
Besides the above core components, we recommend (and analysts also concur) that a strong CNAPP solution include cloud infrastructure entitlement management (CIEM), data protection, and identity and access Management (IAM). These capabilities work together within a CNAPP to safeguard sensitive data and prevent unauthorized access. CIEM continuously monitors permissions and activities in public cloud environments to minimize the risk of breaches, while data protection capabilities classify, inspect, and monitor data to prevent exfiltration from threats like phishing or insider attacks. IAM ensures that only authorized users have the appropriate access, playing a critical role in reducing vulnerabilities and securing your organization’s resources.
Customers rate our CNAPP 4.9 out of 5 stars
Sysdig was one of only four vendors placed in the top-right quadrant in Gartner Voice of the Customer for Cloud-Native Application Protection Platforms and recognized as a Customers’ Choice.
We believe Sysdig is recognized for its ability to offer not only comprehensive posture management, but also deep, real-time runtime insights that drive continuous protection across dynamic cloud environments. In our opinion, being recognized in this report underscores Sysdig’s commitment to delivering solutions that meet the needs of security professionals in the real world — from simplifying risk management to enhancing visibility and reducing noise.
“With Sysdig CNAPP, we have an exceptional, data-driven solution that eliminates blind spots and ensures time-effective use for our business. Making informed decisions confidently, streamlining operations, and maximizing productivity have never been easier.” [Read the full review here]
– Manager, IT Security and Risk, Banking
What do our customers think of our CNAPP solutions?
What does it mean for us to receive the highest overall rating in a report like the Voice of the Customer? In addition to an overall customer rating of 4.9 out of 5, Sysdig’s ratings by category were 4.8 out of 5 for product capabilities and sales experience, 4.7 out of 5 for deployment experience, and 5 out of 5 for support experience. And we were recommended by a whopping 99% of our customers.
“I’m particularly impressed with Sysdig CNAPP for its comprehensive end-to-end security approach and standout features. It delivers a holistic solution that eliminates the need for multiple security tools.” [Read the full review here]
– VP Security Operations, IT Services
“I’m genuinely impressed with the level of real-time security posture checks [Sysdig] brings to our cloud infrastructure. The solution has proven to be an invaluable asset in ensuring the safety of our cloud-native application and data.” [Read the full review here]
– Director of Strategic Initiatives; Software Company
Why do customers choose our CNAPP?
Sysdig is built on the trusted foundation of Falco, the standard for cloud detection and response. Falco is a graduated open-source CNCF project with 130 million downloads, and is also a part of the CNCF exam for CKS certification. Falco was incubated for seven years as a CNCF project, and it has a proven governance model offering maximum flexibility and visibility for runtime security. Sysdig is thus the go-to choice for container, Kubernetes, and workload security because of our open-source roots, our community-driven approach, and our scalable runtime-focused platform, which is a trailblazer for leveraging new technologies like generative AI.
Sysdig emphasizes the importance of runtime insights in its CNAPP. Runtime data allows security teams to see exactly what’s happening in real time — from active configuration changes to user behavior, vulnerabilities in use, and network exposure. This real-time visibility helps catch active threats before they escalate. Below are a few examples of the capabilities that make Sysdig different.
1. Runtime insights-powered graph
Cloud security posture management (CSPM) is no longer just about periodic assessments and passive risk identification. An approach that blends continuous posture assessments with real-time risk mitigation is needed. Here, Sysdig’s Graph Search interface layered with Active Risk insights allows you to proactively identify and mitigate emerging threats. For example, if a new development team accidentally exposes sensitive cloud assets or misconfigures permissions, Sysdig’s runtime-powered graph search allows them to spot these risks immediately — before they turn into a full-blown breach.
This proactive approach is further supported by attack path analysis, which enables security teams to visualize interconnected risks and find exploitable attack paths. By mapping out how risks relate to one another in real time, Sysdig makes it easier to prioritize the most critical threats and quickly remediate them.
2. Customizable posture setup for unique environments
Every cloud environment is different. Whether you’re running multi-cloud architectures, managing containers and Kubernetes, or working within specific regulatory frameworks such as PCI, HIPAA, or NIS2, your organization’s security needs are unique.
Sysdig knows that a one-size-fits-all approach to cloud security doesn’t work. That’s why our Custom Risks Insights and Custom Controls empower security teams to define and enforce security policies tailored to their specific environments. For instance, if you’re working in a highly regulated industry like healthcare or financial services, you can create custom queries and risk patterns that target the specific threats your organization faces for protected health information (PHI) or personally identifiable information (PII). This ensures that you’re not just reacting to generic threats, but actively managing risk based on your unique architecture and regulatory landscape. Sysdig gives security teams full control over their risk management strategy.
3. Sysdig equips organizations to meet the 555 Benchmark
Cloud attacks are fast. After finding an exploitable asset, malicious actors need less than 10 minutes on average to execute an attack. The 555 benchmark — 5 seconds to detect, 5 minutes to triage, 5 minutes to respond — challenges organizations to acknowledge the realities of modern attacks and match them in speed.
Sysdig provides real-time threat detection and cuts incident analysis time to 5 minutes by providing rich, automated context for events and a complete view of the entire attack kill chain, with unmatched coverage for cloud services, identities, and workloads wherever they run. Finally, Sysdig automates security response actions for cloud and containers, bringing organizations closer to meeting the 555 benchmark.
Sysdig is committed to accelerating the speed of response and is leveraging generative AI to assist human analysts. Sysdig Sage’s AI-powered event analysis uses multi-step reasoning and contextual awareness to help understand and stop attacks faster.
Conclusion
If you’re ready to take a more proactive, customizable, and runtime-informed approach to real-time cloud security, the customers have spoken: Sysdig is the platform you can trust. Let us help you secure your cloud environment and mitigate risks — no matter how dynamic or complex your infrastructure may be.
Read the full report here, or if you’d like to see Sysdig in action, check out a demo here.
Gartner Peer Insights content consists of the opinions of individual end users based on their own experiences, and should not be construed as statements of fact, nor do they represent the views of Gartner or its affiliates. Gartner does not endorse any vendor, product, or service depicted in this content nor makes any warranties, expressed or implied, with respect to this content, about its accuracy or completeness, including any warranties of merchantability or fitness for a particular purpose.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, PEER INSIGHTS is a registered trademark of Gartner, Inc. and/or its affiliates and both are used herein with permission. All rights reserved.