In the new cloud-native world, ephemeral services like containers make security a challenging task. As enterprises start adopting containers in production, they suffer from a great deal of variance in the software, configuration, and other static artifacts that exist across their organization’s container image set. Especially with the advent of continuous delivery and deployment, frequent updates and changes to code occur at a rapid pace, which introduces a suite of image software/configuration with potential vulnerabilities in production.
Hence, it is critical for enterprises as a first step to bake in security early in their software development lifecycle. Sysdig Secure prevents vulnerable images from being pushed through your CICD pipeline or run in production. Leveraging Anchore, an open-source vulnerability management engine, Sysdig and Anchore provide image security, compliance assurance and reliability best practices for both native or custom-built images.
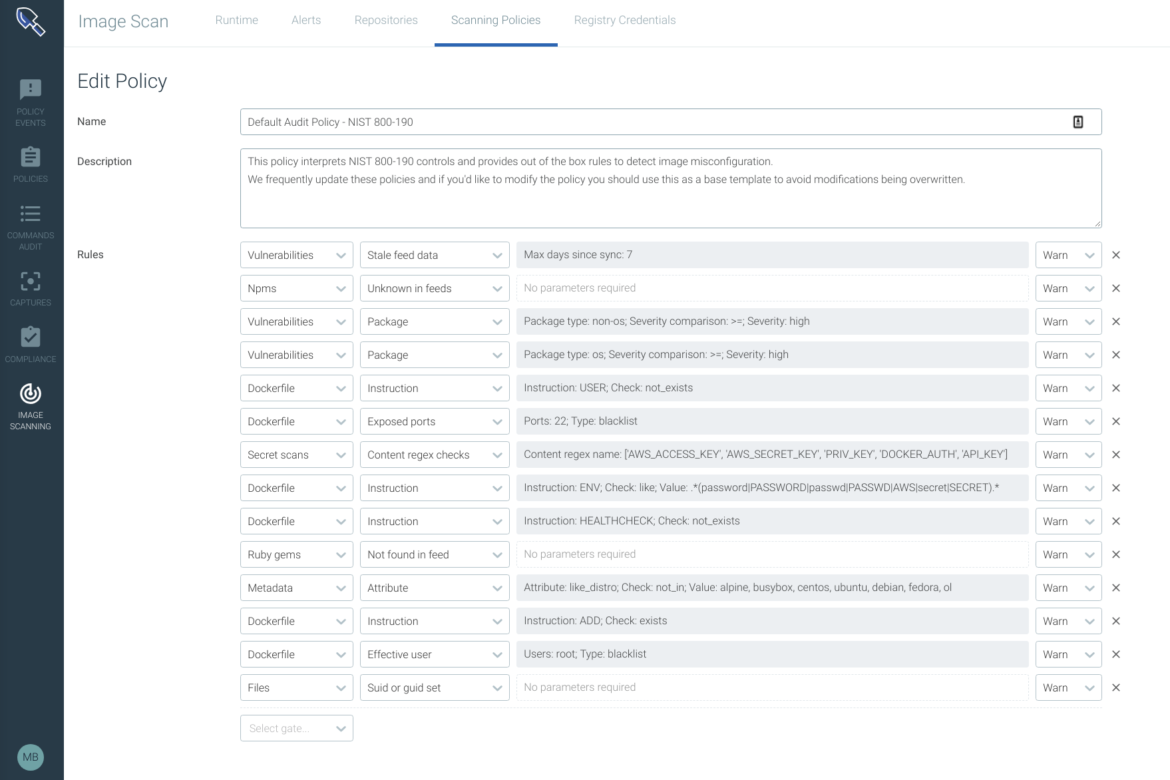
Sysdig now provides support for new out of the box image compliance checks (NIST 800-190, PCI)
Sysdig Secure 2.3 was recently released this week at RSA. The release introduces new scanning policies for NIST 800-190 and PCI compliance frameworks along with improvements to existing CIS and Dockerfile Best Practices. These out of the box policies allow customers to enforce and adhere to various container compliance standards and provide additional checks for their container images running in Kubernetes and Openshift environments.
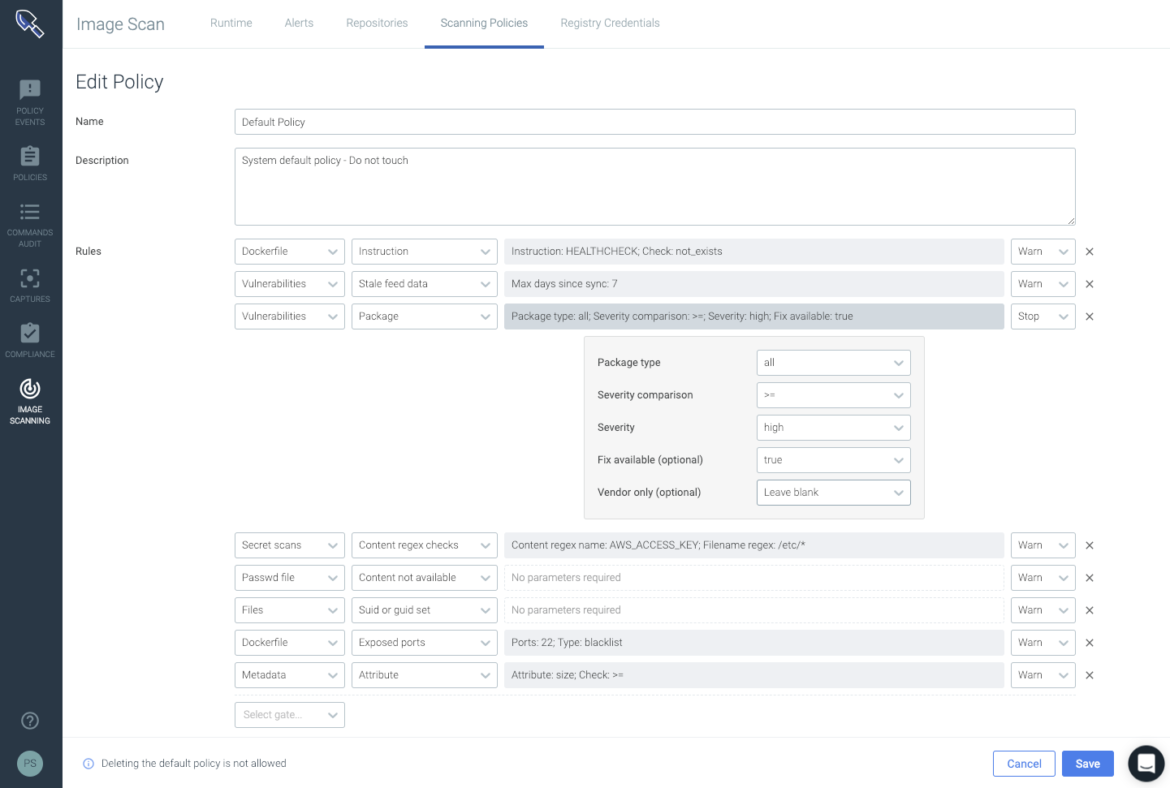
Beyond out of the box checks, you can easily create customized rules for your own organizational security and compliance requirements. With customizable policies, users can create policies based on what suits them best. These policies can scan for vulnerabilities in packages, exposed credentials, missing Dockerfile instructions and even best practices reliability use cases (such as checking for a excessive image size).
These container image scanning policies can be easily leveraged in your CICD pipeline (Jenkins, Bamboo, CircleCI, etc) to prevent vulnerable images from pushing into production. Sysdig Secure can also scan your Dockerv2 registries (ECR, GCR, Artifactory, etc) to ensure pulled images do not contain vulnerabilities.
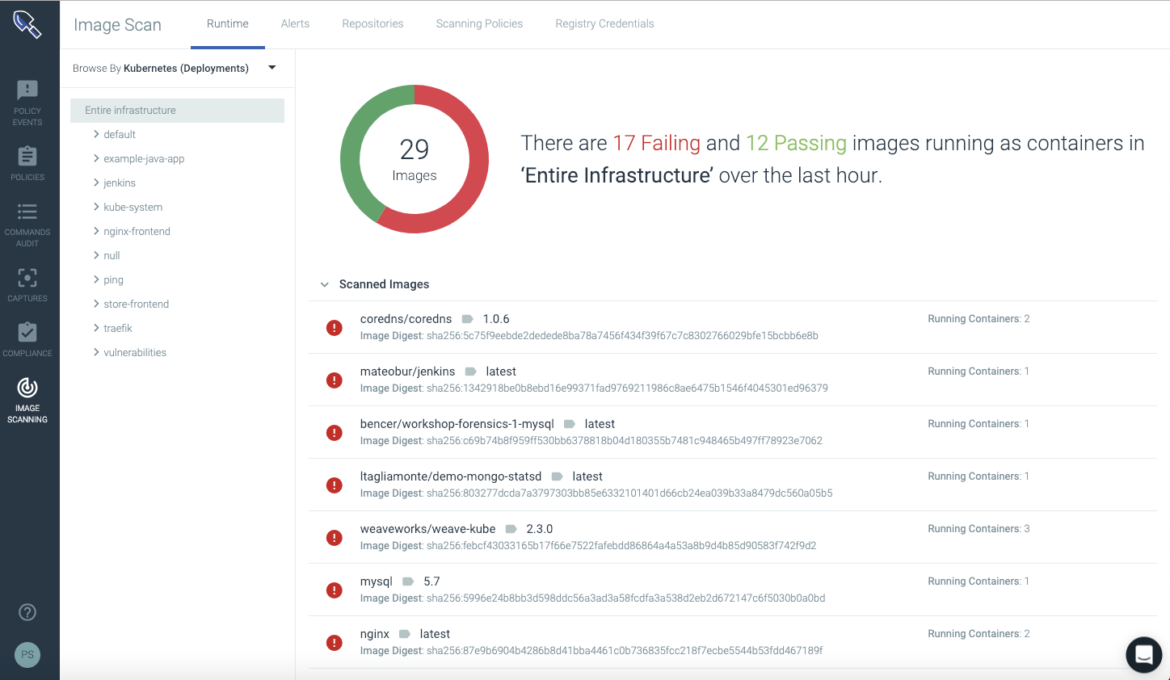
During runtime, these scanning policies can be used to check the status of images running in production. If a new CVE comes out, it is reflected immediately within the Sysdig Secure console without the need for periodic 24 hour re-scans. Combined with Sysdig’s service vision capabilities, a developer can easily scope their images running in their infrastructure and identify any vulnerabilities associated with any particular service or namespace.
Sysdig continues to expand its scanning policy capabilities especially with the release of Sysdig Secure 2.3, to ensure security and compliance for container images pre-deployment and during production. As a perfect pair to Sysdig Secure’s scanning capabilities, Anchore’s open policy hub provides community-driven guidance around container image policies. This is a great place to get started and learn more about the security and policy around containers.
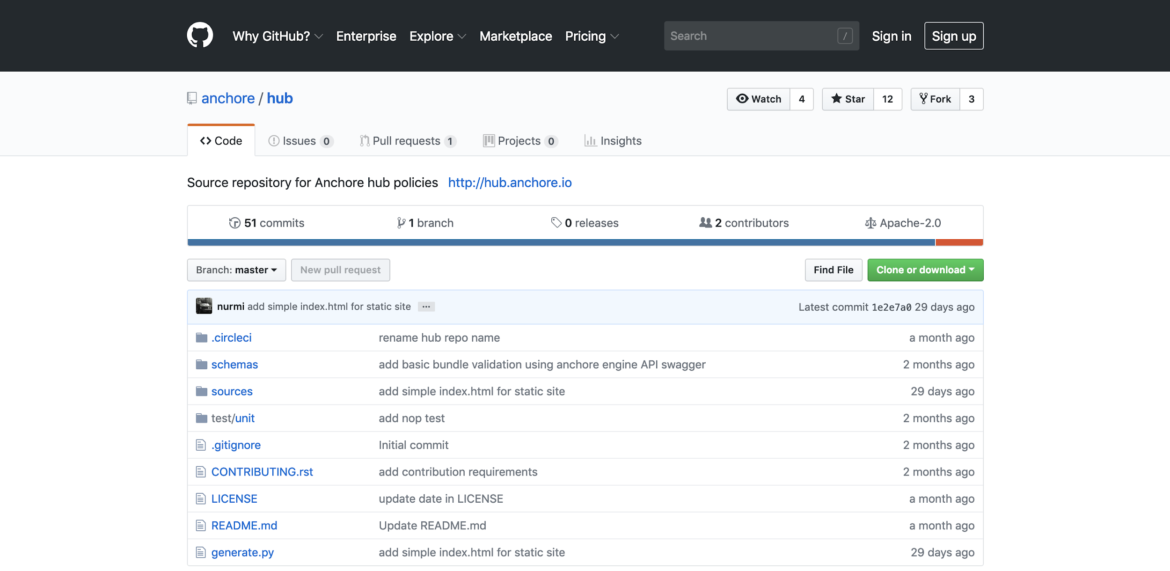
Anchore Policy Hub
As partners of Sysdig, Anchore shares this focus and belief that a preventative, policy-based compliance approach to container security compliance is one of the most effective ways to ensure vulnerable container images never make it into production.
We feel this is one of the most crucial pieces of any container security stance, and security and compliance policy should be an open and community driven initiative. We have built our new Anchore Open Policy Hub to help more users and organizations take advantage of this approach.
The Anchore policy hub provides a repository of pre-defined Anchore policy bundles, and additionally is intended to serve as a mechanism for container DevOps and SecOps user communities to discuss container security, compliance and best-practices topics, while demonstrating functional working expressions of these topics in the form of fully usable Anchore policy bundles, all in a public forum. We believe this is a necessary mechanism to educating the industry on best practices and facilitating stronger container security stances all around.
If you’d like to try the Anchore Policy hub and get involved in the conversation around container security and compliance, head over to our github repo by clicking here.
Conclusion
With the significant variance of compliance needs across development enterprises, it becomes a necessity for teams to incorporate tooling that allows for the creation of policy rules that are both granular and robust.
Adopting a true policy-based compliance practice is a multi-team approach that requires constant collaboration across development, testers, and security engineers.
The OOB policies in Sysdig Secure coupled with Anchore’s Open Policy Hub will not only unify container security and visibility across organizations, but provide any user involved in policy creation the platform and ability to discuss best-practices, container security, and compliance in a public, community-driven setting.
Resources: