
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

After a year of cyber attacks making headlines worldwide, many organizations, such as MGM Resorts, Clorox, and T-Mobile, have taken a reputational hit similar to SolarWinds. Sysdig's 2024 Cloud-Native Security and Usage Report provided some informative key takeaways that CISOs can hone in on to improve their security posture. As a CISO, you do not want to catch your organization on that list; mitigating reputational risk is a part of your job.
This seventh-annual report is based on real-world data. It isn't skewed by opinions, so it provides factual information regarding the current state of cloud security. As such, this blog highlights a few of the key takeaways from the report and provides suggestions for security risk reduction measures that you can implement immediately in your organization. Critically, we are not keeping pace with the speed of our adversaries, and we need to up our game. Live by this mantra as you level up your cybersecurity posture over the next several months.
Come to terms with attack, response, and disclosure speeds
Do you know how quickly the workloads that power your applications live and die? 70% of containers live for 5 minutes or less. Looking through rose-colored lenses, this means an attacker only has 5 minutes to make their move laterally if they enter through a vulnerable container before it dies and they are booted out. Unfortunately, though, they know they'll get another chance if they fail the first time. If the attacker is successful in moving past that container in 5 minutes, your security team may miss out not only on quick containment but also on collecting that forensic data for incident response actions.
So how do you counteract the concept of short-lived workloads being no match for the speed of cloud attacks? First, prioritize mitigation of vulnerabilities in use at runtime. Do not leave known vulnerabilities open and available to attackers! The report indicates that over the last year, runtime prioritization has reduced critical and high vulnerabilities in use by nearly 50%. This prioritization reduces the opportunities an attacker has in the first place by closing open doors. Fix what matters most in your organization's environment, not what others might deem the most important.

- Prioritize vulnerabilities running in your environment, specifically those that are being actively exploited, which could be found on CISA's website. Addressing vulnerabilities that are not in your production environment wastes precious time that could be spent on those that actually put your organization at risk, and vulnerabilities without an active exploit are less risky than those that are being exploited by bad guys.
- When there is a new critical, exploitable vulnerability in the wild, and it's all over the news, and there are CISA and FBI alerts, don't panic. Oftentimes security leaders will overreact after reading the news, and it turns out that the vulnerable tool, image, whatever it may be, is nowhere in your environment. At this point, count your blessings and ignore the media frenzy. If it does impact you, follow guidance, and your security team and developers should know what to do.
Next, you need to have robust real-time detection of potential attacker behaviors. An attacker can be in and moving in 5 minutes, less than the amount of time it probably takes to finish your first cup of coffee or read your emails at the beginning of the day. The only way to combat this is to act on an alert as soon as the attacker makes their first move.
In the 2023 Global Cloud Threat Report and through Sysdig's 5/5/5 Benchmark, the Sysdig Threat Research Team (TRT) provided multiple examples of cloud attacks going from zero to cryptominer, data exfiltration, or worse in an average of 10 minutes thanks, in part, to the use of automation. This benchmark sets an aspiration and offers prescriptive recommendations for your security program to operationalize with respect to detection, data correlation, and response. Challenge your security teams to work against a clock by using a cloud attack where time is of the essence, such as ransomware or a SCARLETEEL attack. This will provide you with a baseline with which you can use to modify tools, applications, and processes to improve your detection and response times.

- Take a few hours (I hope it doesn't take any longer) and run a tabletop exercise with your security team in real time. Get all hands on deck and have your red team or a third party initiate an attack. This should give you a starting point for streamlining your security processes. Use the exercise to validate your preparedness to detect and respond to highly automated attacks.
When security incidents happen, speedy detection and response come in handy at the board level too. With the short timelines set forth by regulatory disclosure requirements, such as the SEC's four business days for material incidents, CIRCIA's 72-hour requirement to report to CISA, or EU NIS2's detect within 24 hours and disclose within 72 hours, the sooner you have an understanding of the incident, the better.
Review and validate these timescales with your team. Ask your team where they think automation can be introduced into the detect and respond processes.
- Consider automating security processes at this point. Note that I said automation and not AI (though this isn't a bad use case for an LLM either). Consider automating some of the data correlation processes so teams can jump right to data analysis. Automate response actions. If responses are not already automated, work with your team to determine where automation can be implemented. Drift control is a great example of an automated security response in which you can shut down workloads that are modified during runtime. You can read more about this in the full report.
Reel in your permissions
Identity management is a bane for most CISOs and security teams. Attacks generally begin with either an exploited vulnerability or an identity issue. Even exploited vulnerabilities still involve identity in some fashion, as attackers use account access and privileges to gather data and move through the network. The report noted that 98% of account permissions go unused. That is far too much unnecessary risk.
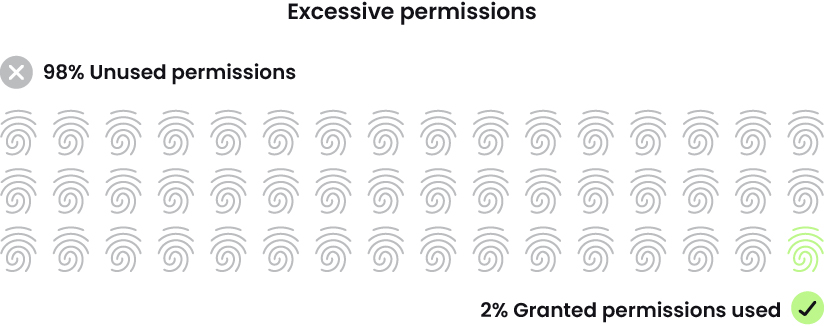
This year's usage report also noted that only 20% of our customers are using our Cloud Infrastructure Entitlement Management (CIEM) weekly. They could be using a different CIEM, but that still doesn't explain the rate of excessive permissions.
- Figure out where your organization stands with permission reviews. Is your organization reviewing permissions on a weekly, monthly, quarterly, or annual basis? Is there a standard in your organization for how these reviews are conducted? If not, consider implementing an identity management review process to minimize overly permissive human and machine identities.
Frankly, I'd like to say there is no excuse for this lack of attention, especially when it comes to machine (nonhuman) identities. However, due to its technical complexity, it is quite difficult to understand every permission a human user or machine needs at a given moment based on their positions, projects, and normal behaviors. The report stated that some machine users have thousands of unused and untouched permissions, essentially providing a free-for-all to the attacker who can access that identity. The fact that the numbers are so astronomical speaks to how difficult the problem is. There are approaches, however, that help address this complex challenge.
- Have conversations with your staff regarding the status of identity management in your organization. Determine what the cadence is for permission reviews and decide if current practices adequately reduce risk.
- Take and implement the guidance of reviewing nonhuman permissions upon initial provisioning and continuously afterward, following your set cadence.
- If these conversations have happened and your granted permissions are still running rampant, determine why and where communication is breaking down, and if your transparency is lacking. Security teams may very well be overloaded or simply lack adequate tooling or processes to support appropriate access controls.
- Determine and implement permission parameters. These might include users with specific job titles or on certain projects and timeline limitations, such as permission removal following no use for 90 days (consider using 60- or 30-day parameters for high-risk identities). These parameters can be automated, but should still be part of regular reviews.
Speed helps business, convenience hurts security
Do you know where your application packages come from or how they are stored? The report states that a majority of organizations (66%) rely on public sources for their images. These sources may be assumed either to be reasonably safe due to where they came from or scanned once and considered vetted from that point forward.
Yes, this use of public images is cheaper because you are not paying for vendor-managed services or dedicating employees and time to private registry maintenance. It is, however, important to acknowledge that these public registries come with reduced security control enforcement (it's out of your organization's hands) and therefore leave you vulnerable to software supply chain risk. If you are using public sources, make sure they are being scanned regularly and consistently at a pace that your organization deems manageable. Remember, you should not rely on an open-source entity to manage scanning and remediation.
- Consider using automated tooling called software composition analysis (SCA) to identify and analyze your open-source software and generate software bills of materials (SBOMs) for your applications.
- As suggested earlier, prioritize your vulnerabilities and risks and remediate them accordingly to reduce attack risks. Focus on known-exploited vulnerabilities and those that impact your workloads at runtime.
Another area where convenience may trump security is in your resource constraints. Unfortunately, many organizations do not set maximum limits or receive alerts on CPU and memory use. This is what attackers are counting on when they drop cryptominers in your environment and make you pay for their resource consumption. There's an opinion that limits hinder development and productivity, so limitless resources equals faster business operations and therefore more profit. However, that profit will be diminished if it's allowing cryptominers to use the resources you're paying for.
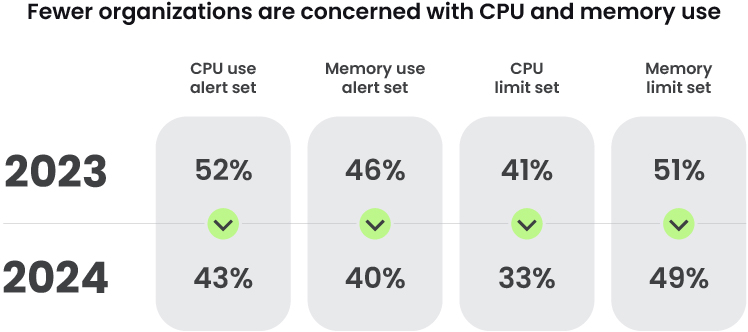
- Implement resource limits and turn on alerts for resource consumption to trigger at 80% (or whatever you deem appropriate), revisiting the limits as necessary.
- Establish a capacity plan and ensure availability by implementing resource parameters for specific workloads, projects, etc. to ensure built-in resiliency in the case of an incident. For example, compartmentalize environment's or workload's limits and, between two of them, set each limit to 40% so that if one side fails or must be pulled down, the other side can assume the workload with extra headroom.
Conclusion
The greatest CISO cloud security takeaway from Sysdig's recent report is that organizations routinely place operations and expediency ahead of governance and security. This can result in unanticipated risks and is, frankly, avoidable.
Security must operate at the speed of business to mitigate risks, and for CISOs, keeping pace with the business is a top priority. Time-sensitive disclosure requirements (think the recent SEC rules) and high-profile breaches now have executive and board-level attention. CISOs need to continually evaluate how timely they can detect and respond to risks. To operate at the speed of the business, CISOs and their teams need to be laser-focused on telemetry and automation.
As a CISO, it is your responsibility to bring security into the business no matter how much others may push back. You must ensure that your security activities are aligned with the business, so it's in your best interest to spend time with your business colleagues to better understand their priorities and initiatives so you can work to ensure that your security initiatives are aligned accordingly.
Capturing and mitigating risks early reduces the risk of distractions which may undermine corporate values. Remind others of the big breaches in the news, such as SolarWinds, T-Mobile, and Equifax. Does your CEO or CFO want to end up like them? The answer is likely "no," So it's up to your team to start putting security at the forefront of business and to take action.


