Earlier today,
CVE-2019-5736 was announced regarding a runC container breakout. Given the high CVSS rating of 7.2, it is imperative to quickly patch your systems.
What is CVE-2019-5736?
runC is the underlying container runtime beneath infrastructure such as Docker, cri-o, containerd, Kubernetes and others. This new vulnerability allows a compromised container to overwrite the host runC binary and gain root-level execution and underlying file access. As a result, an attacker can run any root level command within a container when:
- Spinning up a new container based on the attacker’s image
- Attaching (docker exec) into an existing container which the attacker had previous write access to.
Detecting exploits of CVE-2019-5736 using Sysdig Falco
While the first step anyone should take is scanning the images to find vulnerabilities and run compliance checks to make sure best practices are applied across the environment, there is still a need to cover containers currently running in the environment that are not easy to remove or fix. Fortunately, Sysdig Falco can be used to identify an attempt to exploit the vulnerability.
Sysdig Falco is an open source, container security monitor designed to detect anomalous activity in your containers. Sysdig Falco taps into system calls to generate an event stream of all system activity. Falco’s rules engine then allows you to create rules based on this event stream, allowing you to alert on system events that seem abnormal. Falco’s rich language, allows you to write rules at the host level and identify suspicious activity.
Update #1
As new information comes to light, we are updating the rule to better capture potential exploits. We are closely tracking this issue and will update as more data becomes available.
In this case, we are trying to target overwriting of the runC executable from a container. Below is an example of how we can use Falco to detect a potential exploit. Since process names may vary in different OSs, some tweaking to the rule might be needed. Please proceed with caution.
Disclaimer: The falco rule is tested on Ubuntu 18.10 with Docker Server (Version 18.09.1). The exact details of the vulnerability are yet to be released and minor changes may be needed.
Running processes inside a container as root when the PID namespace is mapped to the host is obviously risky and should be avoided. One option worth exploring is user namespace isolation.
The output would be something like:
01:25:51.733287089: Warning /proc/self/fd/3 is open to write by process (test-cve, /test-cve )
This highlights the powerful ability of the Falco engine to not only detect host level activity, but also target container focused actions to accurately identify malicious activity.
How Sysdig can Mitigate CVE 2019-5736
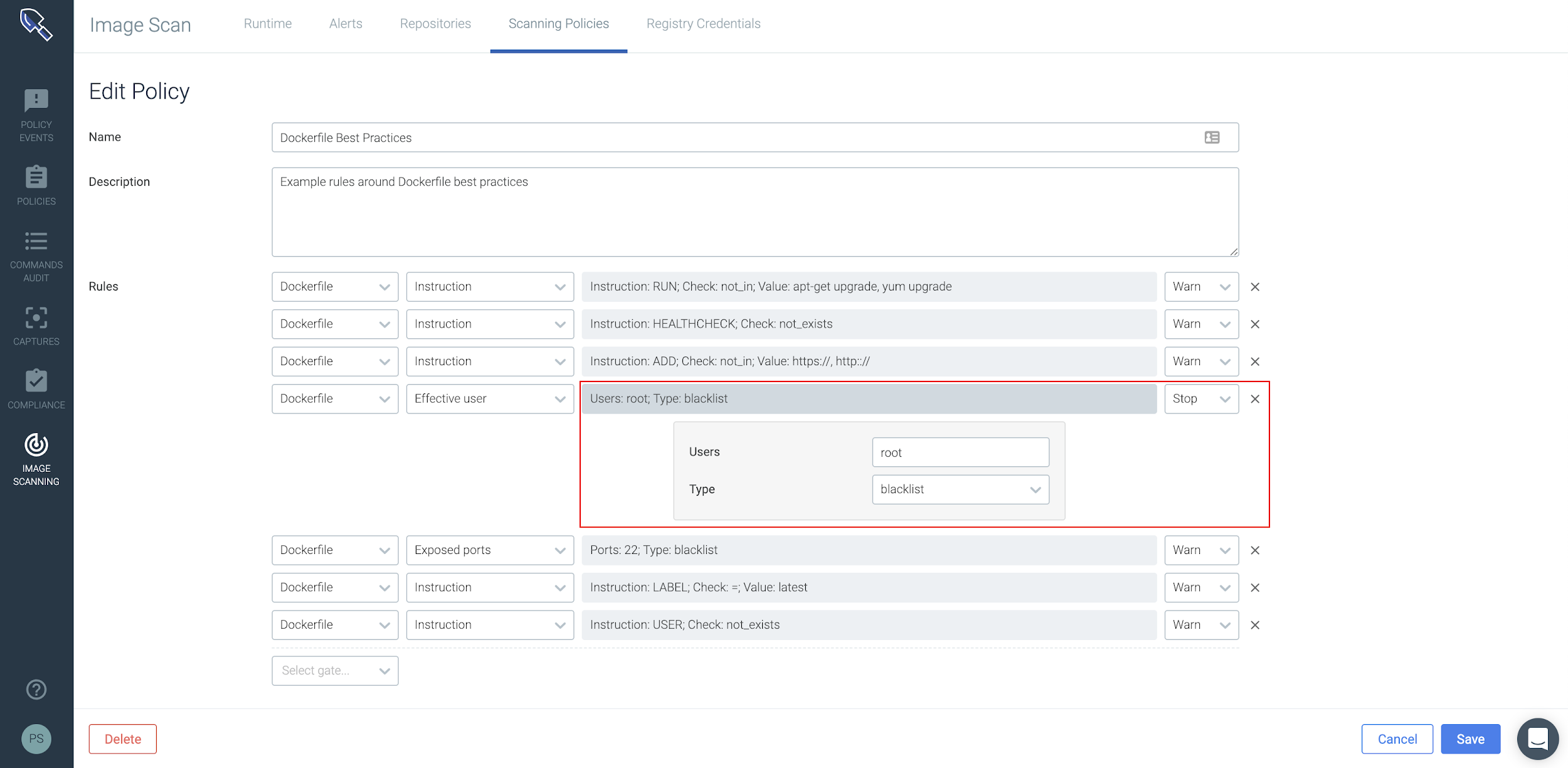
Image Scanning
Sysdig Secure prevents misconfigured images from being pushed through your CICD pipeline or run in production. Scanning policies can be used to scan for any known vulnerabilities in your application and OS/non-OS packages, ensure secrets are not present in your image, analyze Dockerfile contents, etc.
Container Visibility & Compliance
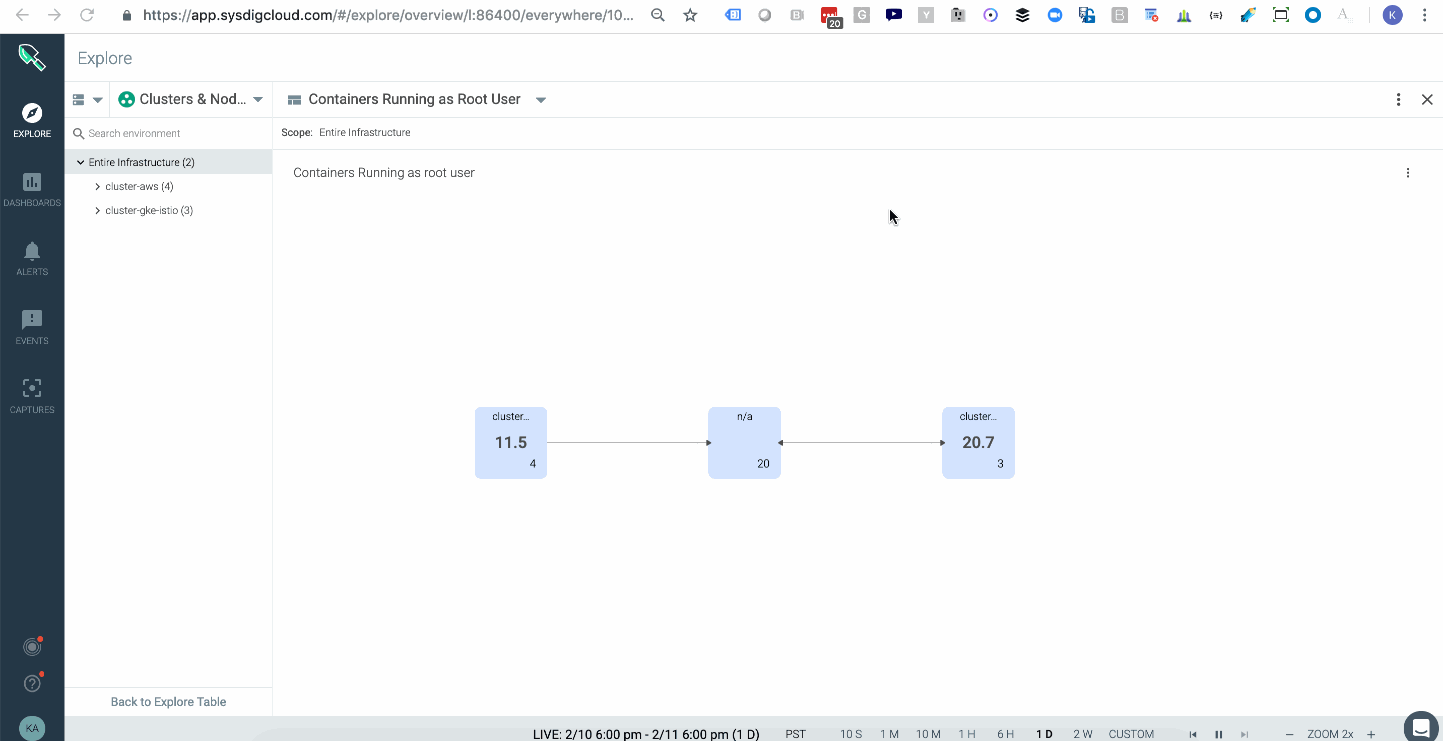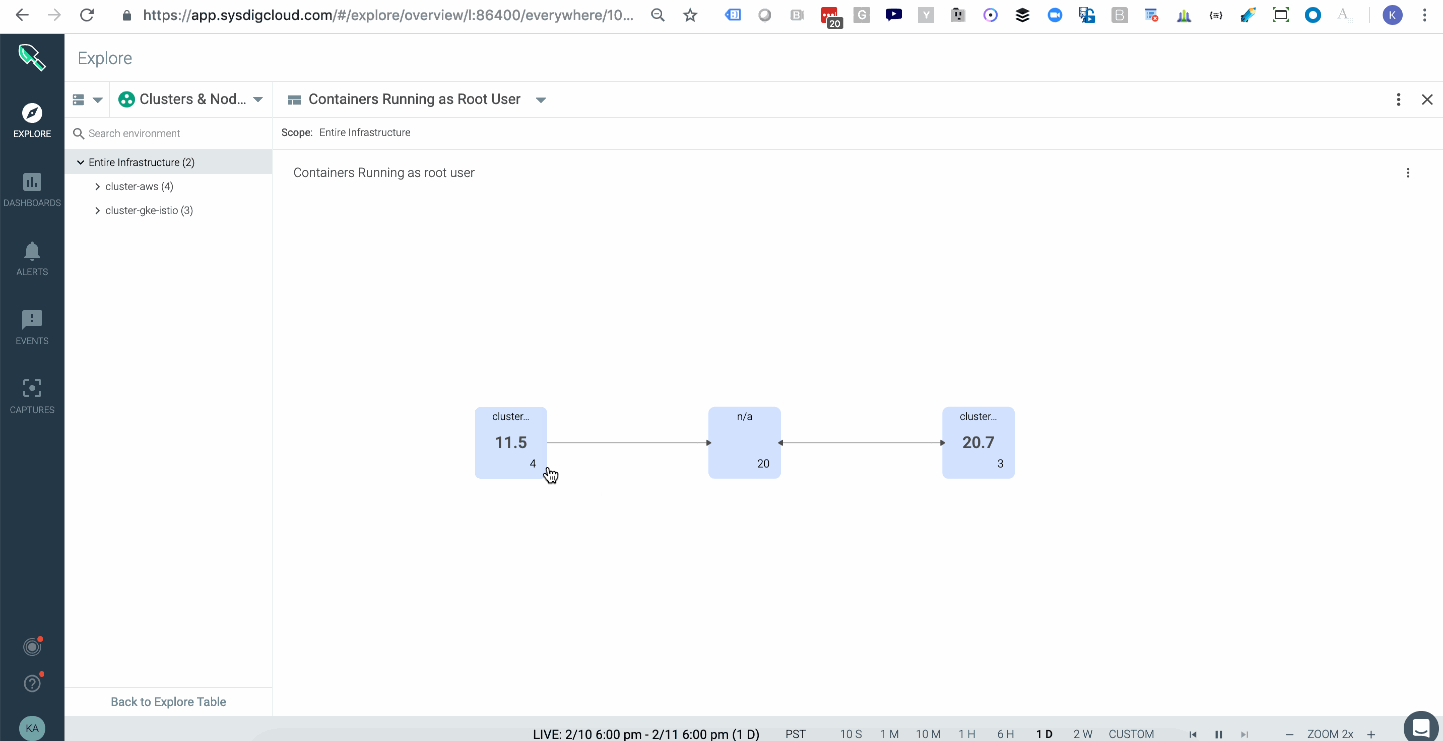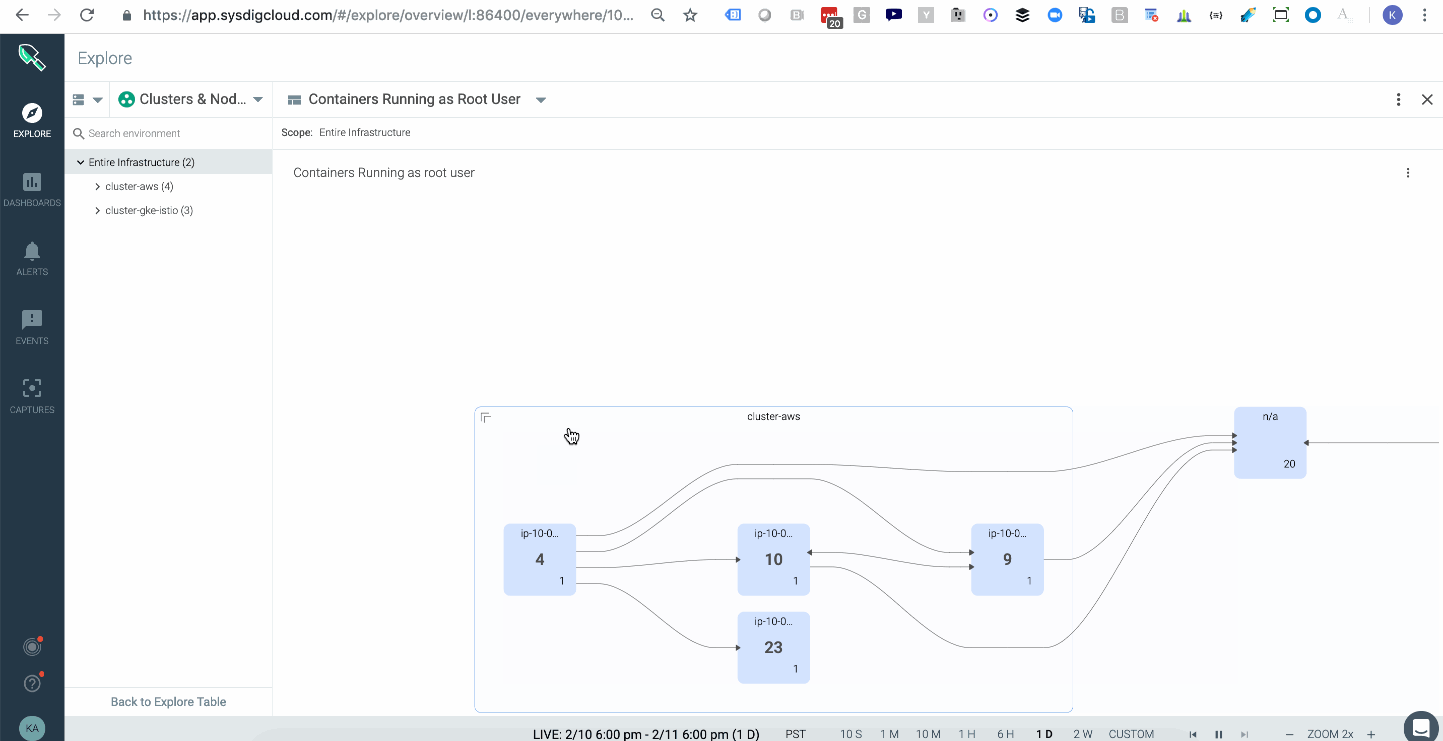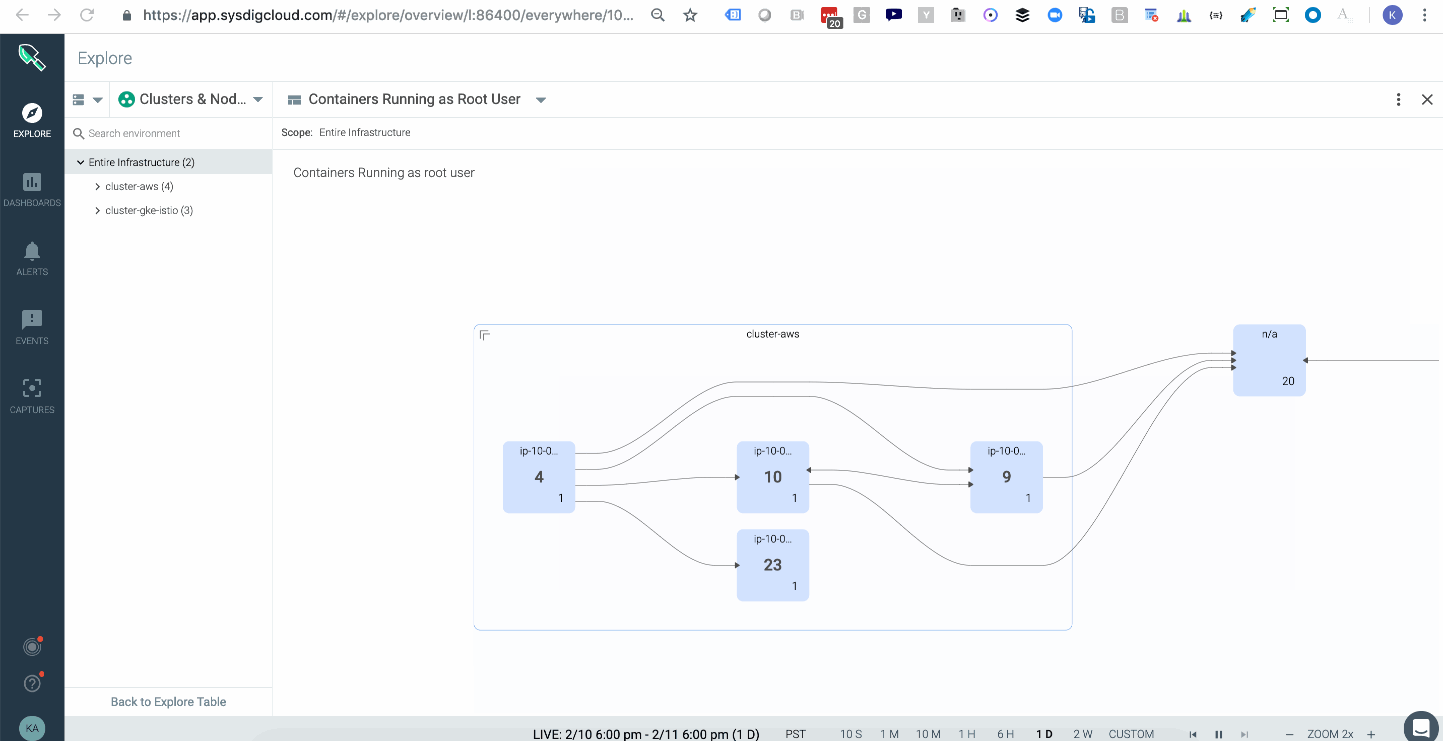
Sysdig Monitor ingests metrics from our agents which run CIS Docker Benchmark and the CIS Kubernetes Benchmark to check images against 100s of configuration best practices. These metrics help organizations spot trends and overlay compliance data on top of operational data to better identify operational and security risk from a single view. Below you can see a topology that shows the average of all images running with a root user across your multiple kubernetes clusters either on-prem or in the cloud. In this case AWS & GKE
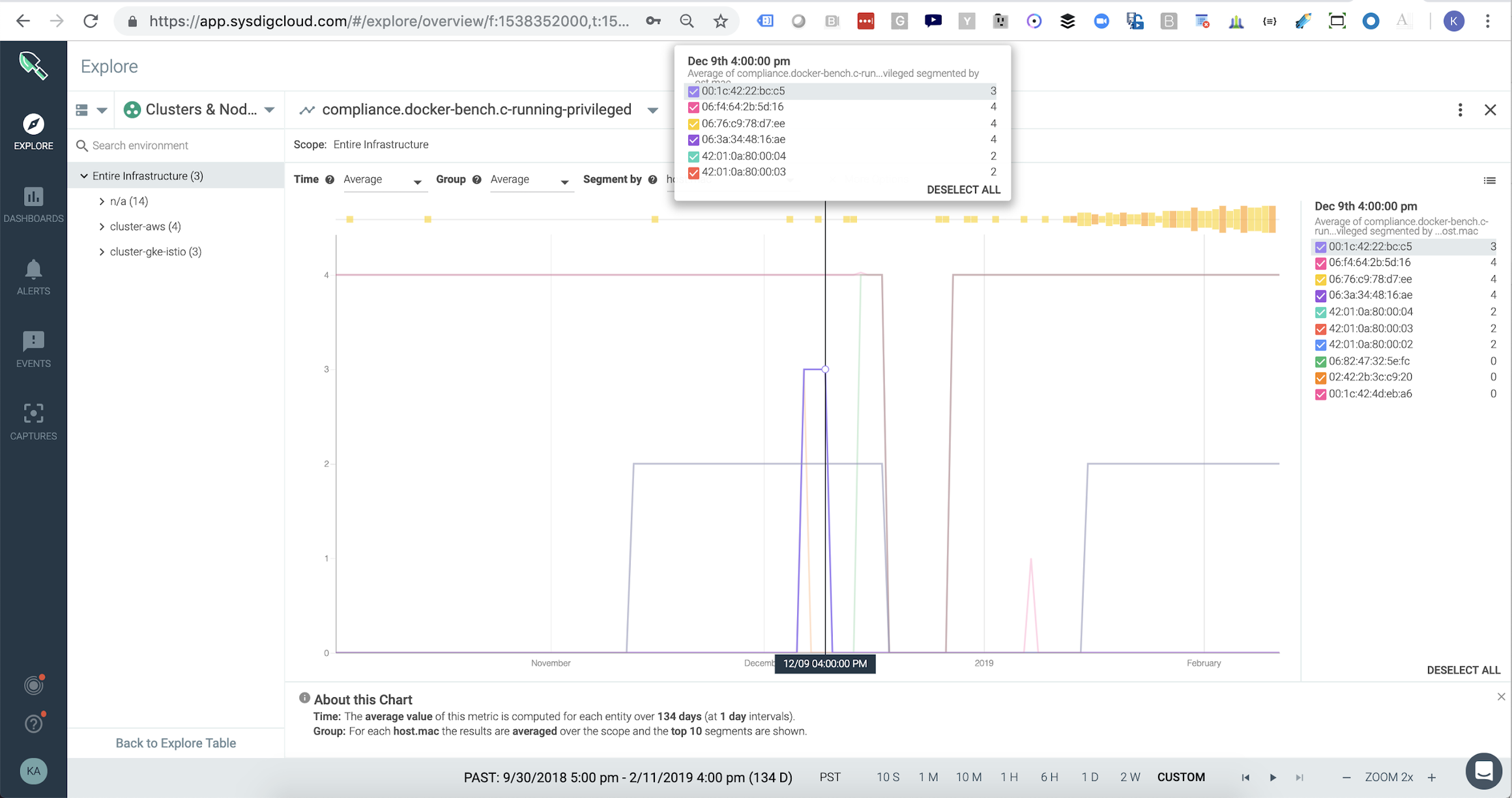
Other CIS metrics like the number of privileged containers can be viewed as time series metrics so you can visualize the risk status of any area of your infrastructure over time. In this example we’ve segmented the metric based on host to easily identify which report I should drill into to figure out how to remediate different non compliant images. Sysdig Monitor handles metric retention and aggregation so you can report on your compliance status for any point over the last few years.
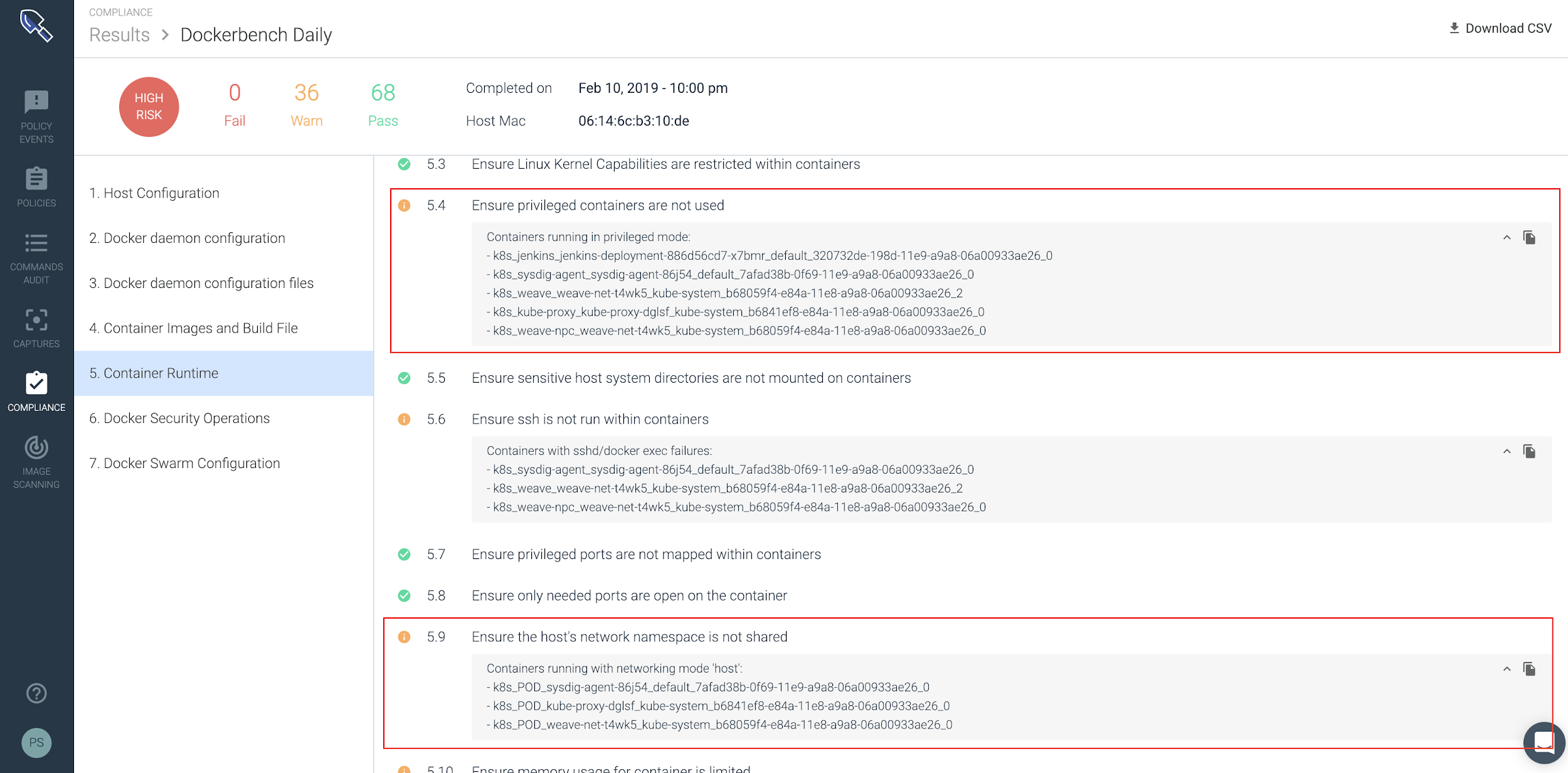
In this particular scenario, we’ll want to isolate containers that are either running in privileged mode or that are on the same host and are sharing the same namespace.
By applying scanning policies, enabling compliance and leveraging Falco, you can enforce strict security best practices and mitigate the risk of exposure to CVE 2019-5736.
Links
Ubuntu:
https://people.canonical.com/~ubuntu-security/cve/2019/CVE-2019-5736.html
Debian:
https://security-tracker.debian.org/tracker/CVE-2019-5736
Red Hat:
https://access.redhat.com/security/vulnerabilities/runcescape
AWS:
https://aws.amazon.com/security/security-bulletins/AWS-2019-002/
GCP:
https://cloud.google.com/kubernetes-engine/docs/security-bulletins#february-11-2019-runc
Rancher:
https://github.com/rancher/runc-cve
Docker:
https://docs.docker.com/engine/release-notes/
 Other CIS metrics like the number of privileged containers can be viewed as time series metrics so you can visualize the risk status of any area of your infrastructure over time. In this example we’ve segmented the metric based on host to easily identify which report I should drill into to figure out how to remediate different non compliant images. Sysdig Monitor handles metric retention and aggregation so you can report on your compliance status for any point over the last few years.
Other CIS metrics like the number of privileged containers can be viewed as time series metrics so you can visualize the risk status of any area of your infrastructure over time. In this example we’ve segmented the metric based on host to easily identify which report I should drill into to figure out how to remediate different non compliant images. Sysdig Monitor handles metric retention and aggregation so you can report on your compliance status for any point over the last few years.
 In this particular scenario, we’ll want to isolate containers that are either running in privileged mode or that are on the same host and are sharing the same namespace.
In this particular scenario, we’ll want to isolate containers that are either running in privileged mode or that are on the same host and are sharing the same namespace.
 By applying scanning policies, enabling compliance and leveraging Falco, you can enforce strict security best practices and mitigate the risk of exposure to CVE 2019-5736.
By applying scanning policies, enabling compliance and leveraging Falco, you can enforce strict security best practices and mitigate the risk of exposure to CVE 2019-5736.

