Is your team drowning in container vulnerability noise? Are you spending a lot of time figuring out where to focus resources on and still missing dangerous vulnerabilities? Know that you are not alone.
Container environments revolutionized app development by enabling unprecedented velocity, but not without a price. The use of readily available container images of third-party and open-source code enabled much faster cycles, but also facilitated the introduction of vulnerabilities in the application. One single container could have hundreds of vulnerabilities; more complex application environments can reach tens of thousands.
Container vulnerabilities overload is growing as a challenge
Things are not getting any better. Since 2016, new vulnerabilities reported each year have nearly tripled, and as reported by US cybersecurity authority CISA, software vulnerabilities remained in the top three initial infection vectors for ransomware incidents in 2021. So, timely finding and fixing vulnerabilities are critical to prevent breaches.
Managing vulnerabilities in containers has become a complex equation of balancing risk, limited resources, and impact on development. Fixing everything is unrealistic and also unnecessary. Not all vulnerabilities incur risk, but finding the ones that cannot wait feels like looking for needles in haystacks.
DevOps and security teams know that handing a long list of vulnerabilities is a non-starter to developers. But leaving the applications exposed to attackers is not an option either. Effective prioritization is required to identify which vulnerabilities require immediate action.
Existing prioritization approaches are not effective
It is common to try to reduce the vulnerability load by focusing on the severity aspect as defined by the CVSS score. But this approach has critical flaws. First, it doesn’t reduce the load to a manageable size. Even just counting critical and high severity vulnerabilities, the number is still beyond what teams can handle, so further prioritization is still required. But it’s also important to realize that CVSS scores can be misleading.
As Miguel Hernández, security researcher, explains so well in his blog, vulnerabilities with high scores may not pose any actual risk to your application, they could be just noise. On the other hand, a medium vulnerability could provide an entry point to attackers, which could evolve to a broad and harmful impact. So, prioritization based only on CVSS scores is inefficient and ineffective.
Other prioritization methods try to apply additional risk factors but similarly fail to address overload because they don’t remove the noise from vulnerabilities that don’t pose any actual risk.
Risk Spotlight eliminates noise and automatically finds the vulnerabilities that really matter
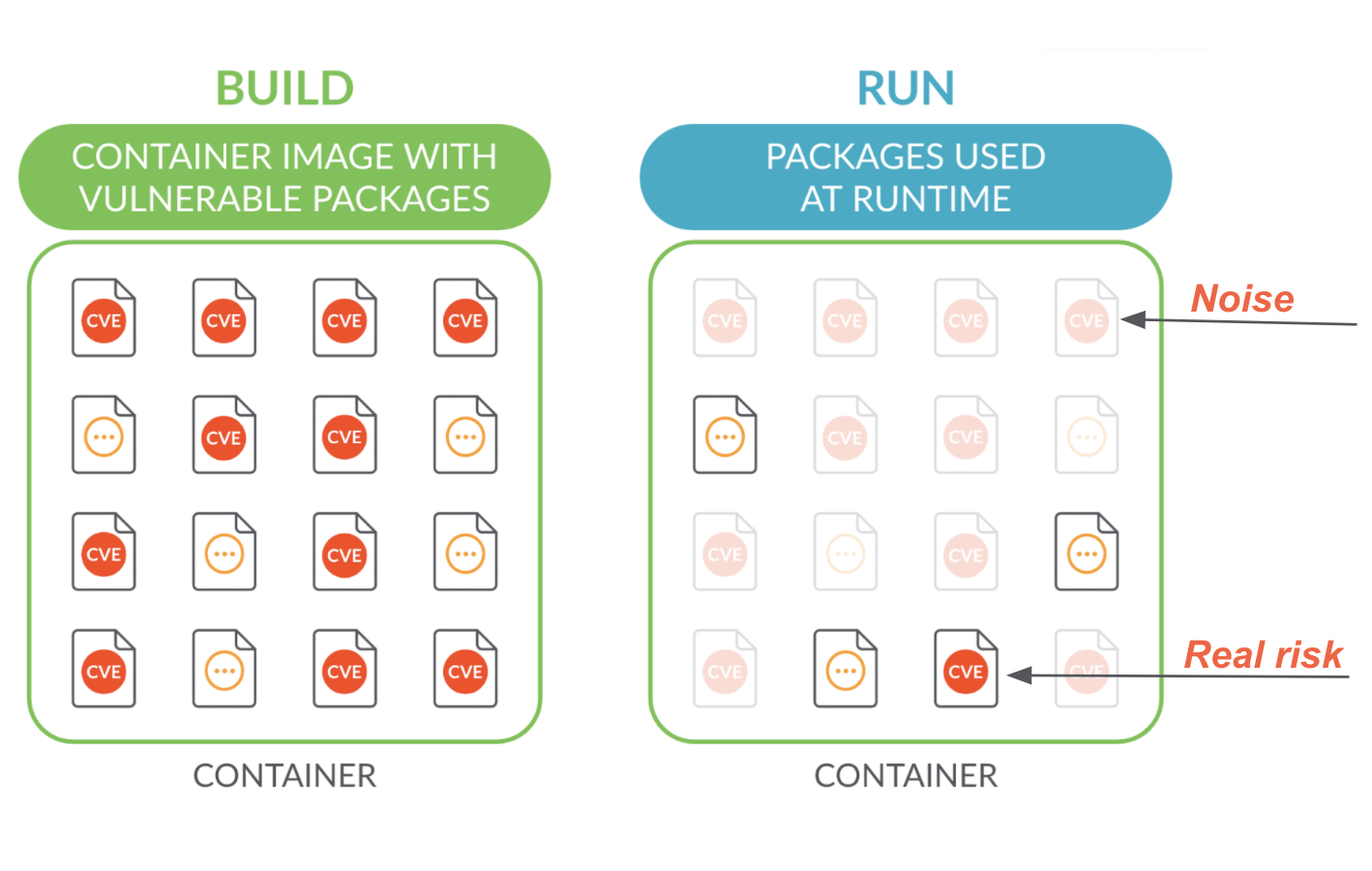
Most of the vulnerabilities reported in container environments are actually noise. Containers are loaded with packages that are never used. Even though they are not used, their vulnerabilities are still reported!
Exploitability is a key determinant of risk. If a vulnerability is never exposed, it doesn’t offer a chance of exploitation and, therefore, doesn’t incur actual risk. Vulnerabilities in packages not active at runtime are just noise.
So, how do you know which vulnerabilities are exposed and pose real risk? By using runtime intelligence.
Only vulnerabilities that are tied to packages used at runtime offer a real chance of exploitation. Sysdig’s deep visibility into system calls removes all the guesswork from container vulnerability prioritization by accurately identifying vulnerabilities in packages loaded at runtime.
By knowing what is exposed and what isn’t, Risk Spotlight removes the noise and prioritization guesswork so your team can focus on really important issues that can’t wait.
See how fast and easy you can identify which vulnerabilities pose a real risk with Sysdig.
Sending a report to DevOps and security teams listing hundreds of vulnerabilities in a container running in production is certainly not productive. Trying to prioritize them without eliminating noise is ineffective because just a handful offer a real chance of exploitation. So why overload your teams with vulnerabilities that pose no risk?
With Risk Spotlight, you can focus mitigation efforts on the vulnerabilities that pose an immediate risk. All the other vulnerabilities can be deprioritized, allowing developers to fix important issues faster with minimum resources.
No longer scrolling vulnerabilities line-by-line, struggling to estimate risk through an endless spreadsheet of issues. With Risk Spotlight, you can easily find, focus, and fix the vulnerabilities that matter to you.
If you want to learn more, sign up for our upcoming webinar or request a free trial of our Sysdig Secure DevOps Platform.
Key Benefits of Risk Spotlight
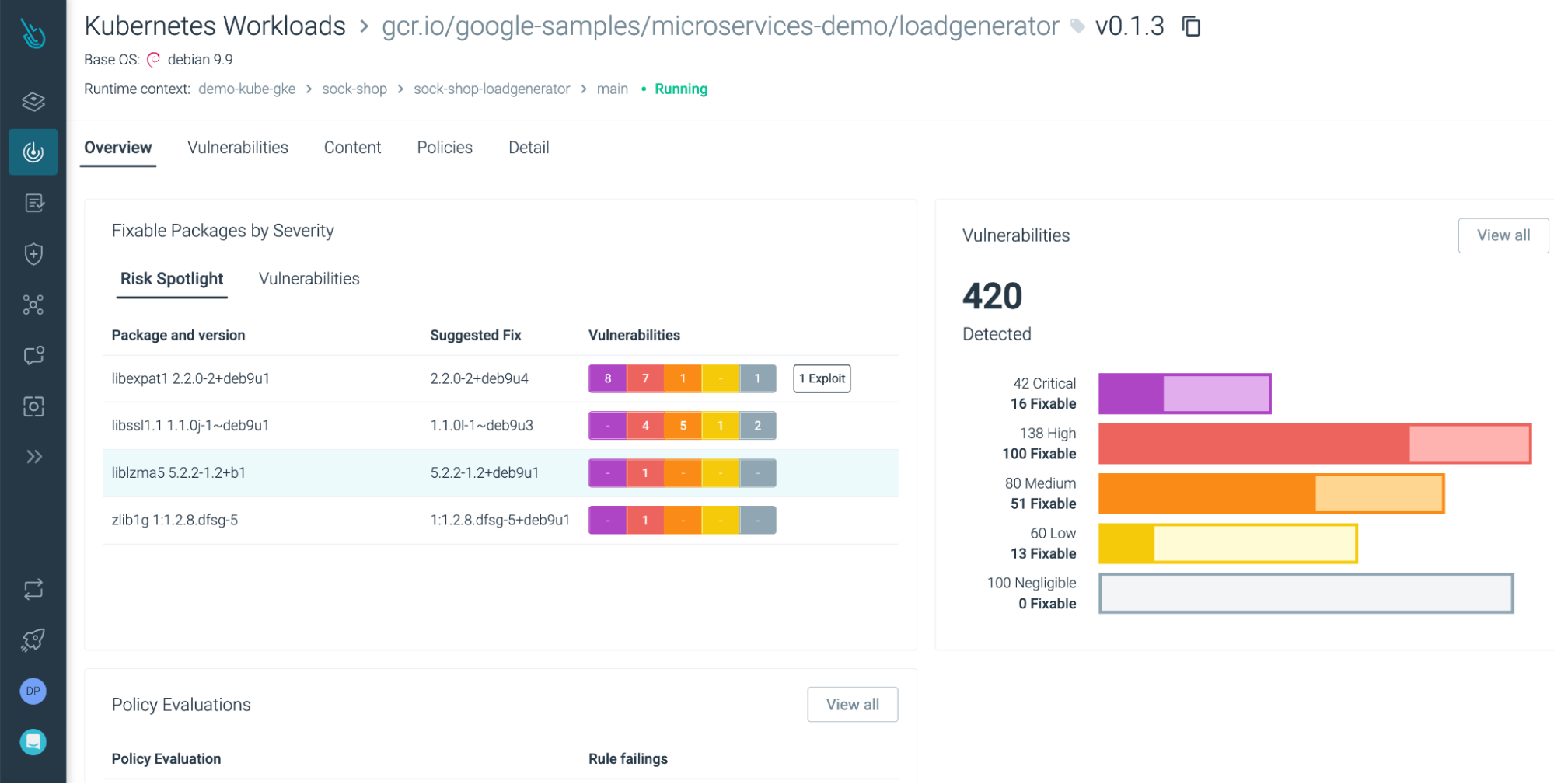
- Reduce vulnerability noise by up to 95%. Risk Spotlight eliminates the noise from vulnerabilities that pose no immediate risk by identifying the packages not used at runtime.
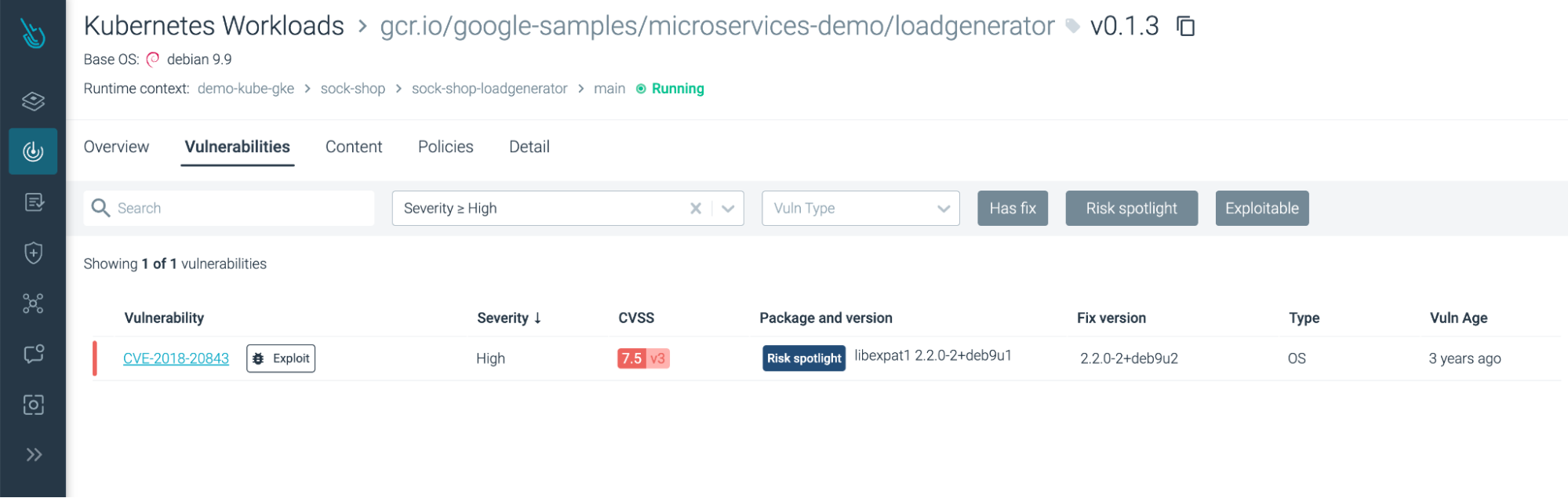
- Manage risk with actionable insights. Risk Spotlight delivers rich vulnerability details – such as the CVSS vector from multiple sources, the fix version, and link to publicly available exploits – and a package-centric view that facilitates remediation and managing vulnerability risk at scale.
- Comprehensive vulnerability management for containers from source to run. Risk Spotlight provides a single view of vulnerability risk across the container lifecycle, from build to runtime. Developers can take immediate actions to mitigate the few vulnerabilities that pose real risks and also apply security best practices early by removing unused packages during the build process.
No longer scrolling vulnerabilities line-by-line, struggling to estimate risk through an endless spreadsheet of issues. With Risk Spotlight, you can easily find, focus, and fix the vulnerabilities that matter to you.
If you want to learn more, sign up for our upcoming webinar or request a free trial of our Sysdig Secure DevOps Platform.