Introducing Kubernetes 1.33: Cloud-native improvements for dev and security teams
The Kubernetes 1.33 release continues the project’s momentum in delivering scalable, secure, and developer-friendly enhancements to cloud-native infrastructure. As Kubernetes evolves, so do the expectations from engineering and security teams who depend on it to run critical workloads with precision and control.
The Kubernetes 1.33 enhancements include meaningful improvements that simplify workload management, enhance identity controls, and improve observability in production. From in-place pod resource scaling to OCI image volumes and better lifecycle tracking, this release packs features that balance power with practicality.
In this blog, we’ll break down what’s new in Kubernetes 1.33, explore what these changes mean in real-world environments, and share insights on how to prepare for what’s coming next.
Let’s dig in.
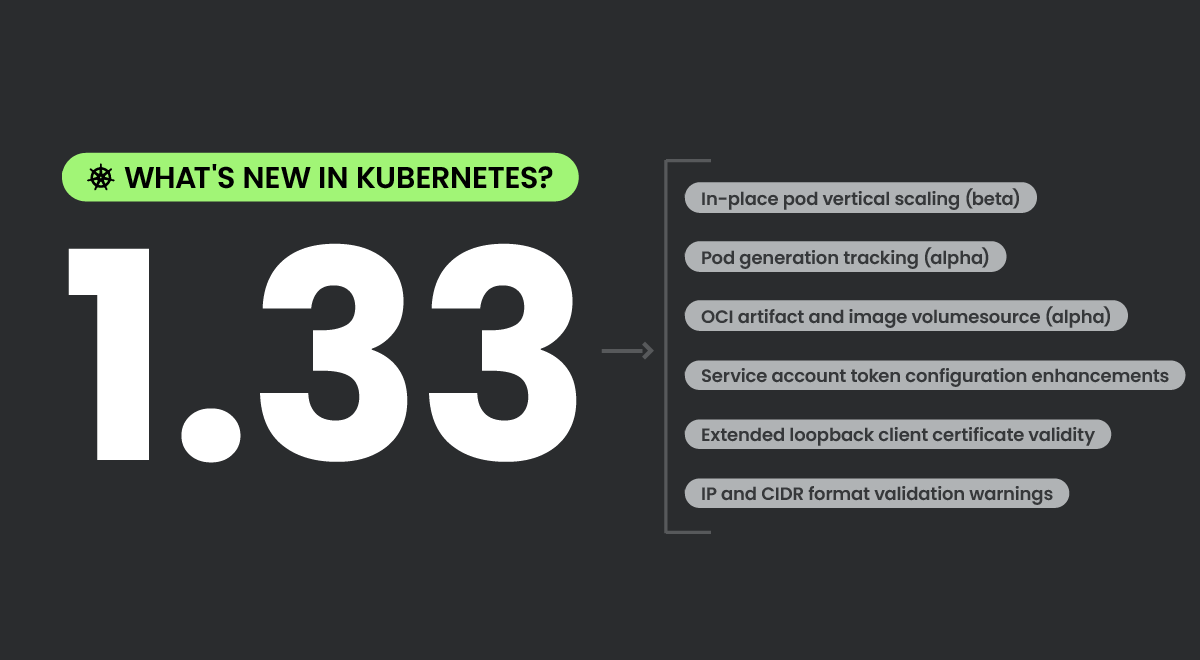
Kubernetes 1.33 enhancements at a glance
| Feature | What it does | Why it matters |
| In-place pod vertical scaling (beta) | Adjust CPU and memory of running pods without restart. | Minimizes downtime, supports dynamic autoscaling, improves performance tuning. |
| Pod generation tracking (alpha) | Adds a generation field to pods to track spec changes. | Improves lifecycle observability and enables smarter automation. |
| OCI artifact and image volume source (alpha) | Mount container images directly as volumes. | Simplifies artifact delivery and supports modular architecture. |
| Service account token configuration enhancements | Customize token audience and account name for kubelets. | Supports least privilege, multi-tenant security, and better RBAC alignment. |
| Extended loopback client certificate validity | Increases loopback client certificate validity to 14 months. | Reduces renewal burden and aligns with Kubernetes support cycle. |
| IP and CIDR format validation warnings | Warns on non-standard IP or CIDR formats in configs. | Encourages best practices, prevents subtle misconfigurations, and boosts future compatibility. |
In-place pod vertical scaling (beta)
One of the most anticipated Kubernetes 1.33 enhancements is support for in-place pod vertical scaling. This long-requested feature gives platform teams the ability to adjust the CPU and memory limits of a running pod—without requiring a disruptive delete-and-recreate cycle.
For DevOps and SRE teams, this means smoother scaling experiences and fewer headaches when fine-tuning resource allocations in production. In autoscaling scenarios or under unpredictable load conditions, workloads can now adapt more gracefully without downtime or orchestration lag.
Why this matters
- Improves availability: Applications stay running while their resources are adjusted dynamically.
- Supports elasticity: Enables smarter automation for performance tuning and reactive scaling.
- Streamlines operations: No more custom workarounds to resize pods on the fly.
This Kubernetes 1.33 release enhancement reduces toil and unlocks more flexible scaling strategies, especially for teams managing high-traffic or stateful workloads.
Pod generation tracking (alpha)
The Kubernetes 1.33 release introduces a subtle but powerful change: a new metadata.generation field for pods. This field tracks updates to the pod spec by incrementing its value whenever a mutable field changes—bringing pod behavior in line with existing workload resources like Deployments and StatefulSets, which already support this mechanism.
Previously, Kubernetes pods lacked a built-in way to indicate if their spec had changed over time. For operators and custom controllers, this often meant relying on indirect signals or workarounds to detect configuration drift. With pod generation tracking, tools can now respond more reliably and accurately to pod updates.
Why this matters
- Improves pod state management: Controllers and GitOps tools can track pod spec changes natively.
- Enhances automation: Smarter update logic for pipelines, reducing unnecessary restarts or redeployments.
- Boosts observability: Simplifies debugging and change auditing across dynamic environments.
This Kubernetes 1.33 enhancement is especially useful for teams automating pod operations at scale or building advanced observability tooling.
OCI artifact and image volume source (alpha)
A standout Kubernetes 1.33 enhancement is the ability to use OCI artifacts and images as volume sources. This alpha feature allows container images—like tools, binaries, or config bundles—to be mounted directly into pods as volumes, eliminating the need to unpack or bake them into traditional container images.
For platform engineers and DevOps teams managing large-scale workloads, this simplifies content distribution and supports use cases like sidecar injection, custom CLI tooling, and secure artifact delivery. It also complements workflows where workloads need dynamic, versioned resources mounted at runtime.
Why this matters
- Reduces container image sprawl: Move shared content into reusable artifacts instead of duplicating it across images.
- Simplifies tooling delivery: Mount utilities or config sets into containers without rebuilding or redeploying.
- Improves flexibility: Supports more modular and scalable architecture patterns in Kubernetes.
As image volumes become more common, this feature aligns with the broader movement toward cloud-native modularity—and opens new doors for secure, efficient workload composition in future Kubernetes releases.
Service account token configuration enhancements
The Kubernetes 1.33 release continues to strengthen identity and access controls with new capabilities that give more flexibility to how service account tokens are requested and used. Specifically, kubelets can now dynamically configure the service account name and token audience they request tokens for—making it easier to support complex multi-tenant environments or fine-tune permissions.
For teams managing Kubernetes RBAC at scale, this change supports stronger separation of duties and aligns with best practices like least privilege. It also benefits security-conscious teams who need to tightly scope service account access across clusters, workloads, or teams.
Why this matters
- Improves flexibility in token usage: Define exactly what identity and audience each token is intended for.
- Enhances least-privilege controls: Reduce overexposure by aligning token scopes to actual usage needs.
- Supports multi-tenant security: Tailor service account behavior across namespaces, teams, or applications.
Best practice: Strengthen your RBAC with scoped service accounts
As Kubernetes adoption grows, so does the complexity of managing access. Use scoped service accounts with well-defined audiences to limit access to only what’s needed—nothing more. Pair this with namespace-level policies and regularly audit permissions using tools that provide runtime visibility (like Sysdig).
Need a refresher? Check out our Kubernetes RBAC overview to learn how to implement fine-grained access controls that support both security and developer agility.
This is one of the more security-centric Kubernetes 1.33 enhancements, and it signals a continued investment in refining the Kubernetes identity model to keep up with modern cloud and compliance demands.
Extended loopback client certificate validity
Another quiet but meaningful update in the Kubernetes 1.33 release is the extension of the default validity period for the kube-apiserver loopback client certificate—from one year to 14 months. This update brings it in line with Kubernetes’ support cycle, reducing the administrative overhead of certificate rotations.
While the loopback client certificate is primarily used for internal communication between the API server and itself, expired certificates can cause unexpected issues—particularly in high-availability or air-gapped clusters. By aligning the validity period with the release lifecycle, Kubernetes reduces friction for cluster operators and streamlines the upgrade path.
Why this matters
- Reduces manual maintenance: Fewer cert renewals to worry about during normal upgrade cycles.
- Improves stability for production clusters: Helps avoid misconfigurations and runtime errors due to expired certs.
- Aligns with Kubernetes lifecycle: Ensures better consistency between security controls and operational best practices.
If your team relies on automated tooling for Kubernetes upgrades and certificate management, this Kubernetes 1.33 enhancement helps smooth the path—especially for enterprise or regulated environments with stricter uptime requirements.
IP and CIDR format validation warnings
Rounding out the Kubernetes 1.33 enhancements is a change that focuses on improving configuration hygiene and reducing ambiguity: the Kubernetes API server now issues warnings when IP addresses or CIDRs are specified in non-standard formats (for example, 192.168.000.005).
While these formats may still technically work in some contexts, they can cause subtle issues—such as routing inconsistencies, failed parsing by external tools, or even unexpected behavior in network policies. These warnings are Kubernetes’ way of nudging users toward better practices before such formats are disallowed in future releases.
Why this matters
- Improves security hygiene: Prevents misconfigured IPs from creating hidden vulnerabilities.
- Protects portability: Ensures IP formatting won’t break when moving workloads between environments.
- Supports stronger automation: Makes it easier to validate infrastructure-as-code (IaC) using tools like KubeLinter or kubectl validators.
This is a heads-up for teams using templated configurations, legacy IaC patterns, or tools that auto-generate CIDRs. Now’s a good time to clean house and normalize your IP and subnet definitions before future Kubernetes releases enforce stricter validation.
Final thoughts: Kubernetes 1.33 continues the momentum
The Kubernetes 1.33 release delivers a well-balanced mix of performance, security, and usability improvements that will resonate with both platform engineers and cloud security teams. From flexible pod scaling and smarter resource management to stronger identity controls and improved configuration hygiene, this release keeps Kubernetes evolving to meet the demands of cloud-native environments at scale.
As always, staying ahead of Kubernetes enhancements means more than just tracking version numbers—it’s about understanding how these changes affect your operations, automation, and risk posture. At Sysdig, we help teams embrace the speed of innovation without sacrificing security. Whether you’re securing CI/CD pipelines, enforcing least privilege, or detecting threats in real time, we’ve got your back.
Want to see how runtime insights and real-time threat detection can harden your Kubernetes environments?