The cloud revolution has firmly taken hold, and businesses of all sizes are adopting cloud-native technologies. This new paradigm has also created newer attack surfaces for cybercriminals, who are eager to exploit known security gaps in cloud environments. Sysdig is collaborating with Docker to deliver a more efficient process for identifying risks and opportunities for accelerated remediation in Docker Scout using runtime insights.
“Shift left” security aims to help companies prevent and remediate security issues during the early stages of software development. In this blog, we’ll highlight how Sysdig Secure and Docker Scout help users avoid security issues and significantly reduce risk in production environments.
Sysdig runtime insights and Docker Scout
In a joint effort between Docker and Sysdig, we’ve enabled the connection between Sysdig Secure and Docker Scout in order to provide context collected from running containers. With this information, Docker Scout users have an additional filter that highlights the packages loaded at runtime. Developers can make more informed decisions and save time as they triage software supply chain insights.
What is Docker Scout?
Docker Scout is designed to generate actionable insights for the software supply chain. It offers a layer-by-layer view of image dependencies, vulnerabilities, comparisons, and remediation paths. Docker announced the general availability of Docker Scout this week at DockerCon. You can check out their announcement here.
What are Sysdig runtime insights?
Sysdig’s deep runtime security visibility uses system calls at the kernel level to identify container activity. This is critical for threat detection but also enables Sysdig Secure to identify running containers and the packages loaded at runtime. Often, containers include packages to accommodate potential dependencies that are never used. Runtime insights help you clearly see what’s in use and what’s not.
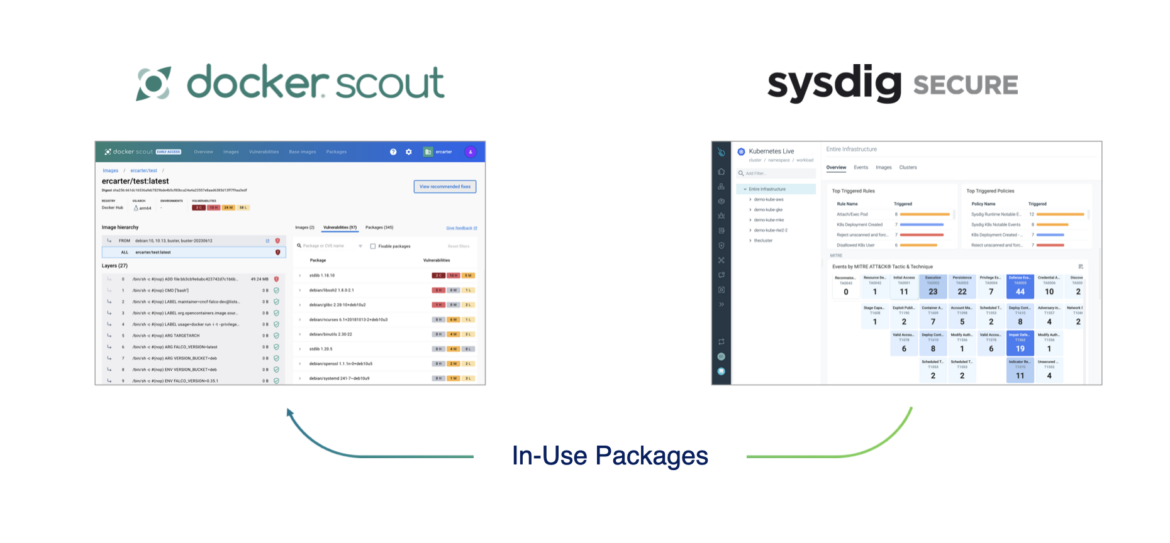
Prioritize risks using SBOMs and runtime insights
What is SBOM?
A Software Bill of Materials (SBOM) is key when shifting security left. SBOMs provide an artifact that contains a comprehensive list of software assets and dependencies that make up a piece of software. SBOMs are also handy for knowing details such as the licensing covering each package.
In terms of security, an SBOM is key for staying on top of security risks. It helps maintain an accurate and updated correlation between package dependencies, which makes the detection task easier. A complete and accurate SBOM will help with the task of identifying and correlating software dependencies with vulnerabilities and their potential security risks.
Using Sysdig runtime insights with Docker Scout
Docker Scout comes with a number of features that help Docker users manage container security. It provides a unified software analysis view to help you understand your image composition, correlates security risks with your image’s SBOM, and gives contextual remediation advice.
Let’s see some of the use cases where Sysdig complements the utility of Docker Scout.
Integration use case 1: CVE data and in-use vulnerabilities
One of the most basic and important features of Docker Scout is the ability to get CVE information from the SBOM. CVE data is pulled right away, along with the correlation of which packages are impacted by specific vulnerabilities. These are ordered and summarized by priority, from the highest (CRITICAL) to the lowest (LOW). With the Sysdig integration, developers also get information about whether a vulnerability impacts in-use packages or not.
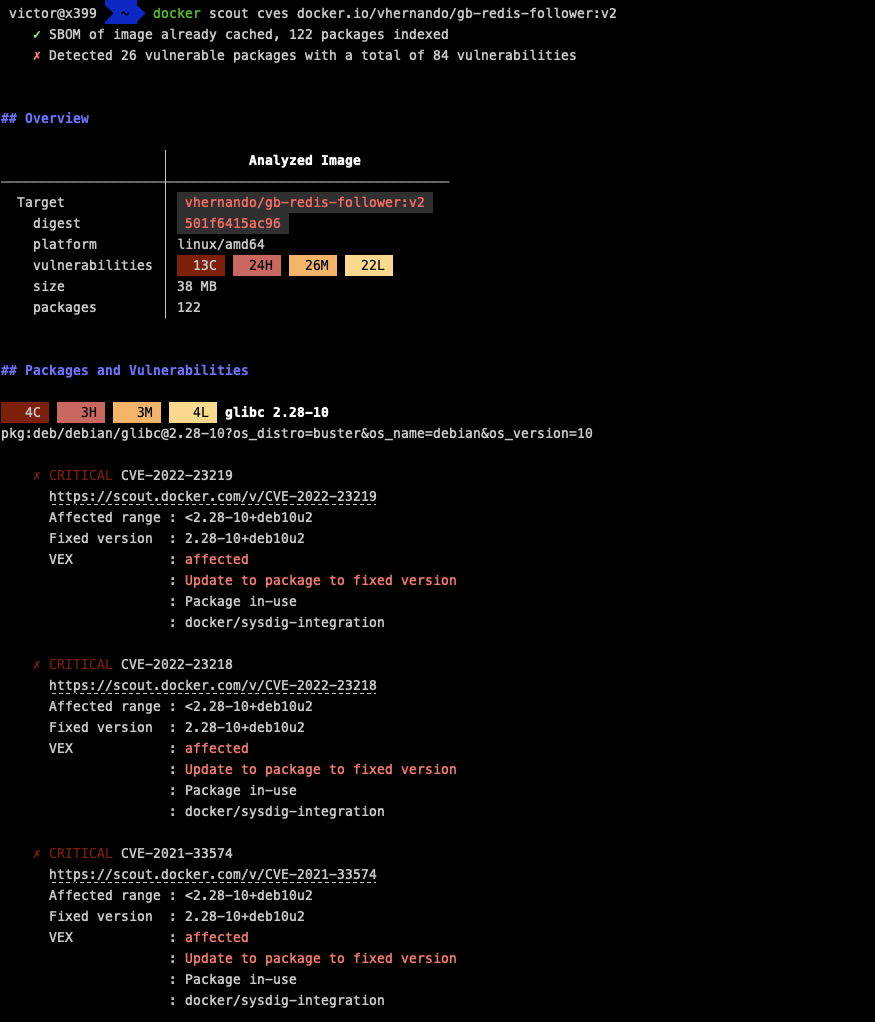
Prioritize software security risks that represent opportunities to improve application reliability and security.
Integration use case 2: Compare vulnerabilities between releases
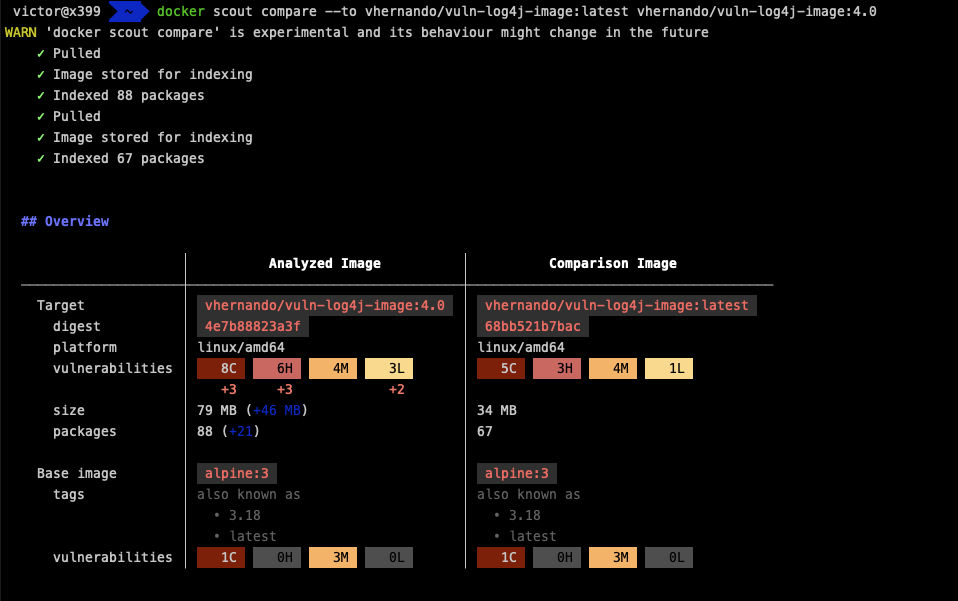
At software development time, it can be crucial to have visibility on what is being developed versus what is deployed on production, or other intermediate environments. With visibility into runtime, Docker Scout can compare a local image to an image currently running in a cluster and create a report to show the differences, including which packages are in use.
Developers can thus easily spot vulnerabilities between releases and minimize security blind spots in production. Using the “compare” approach with in-use information also helps provide a picture of which packages may simply be “bloat.” and possible candidates for removal to build a leaner image. Leaner images help reduce the attack surface but also scale more quickly.
Integration use case 3: View image insights in your CI/CD pipeline
Docker Scout can be integrated into the CI/CD pipeline workflow with a few CI/CD tools like GitHub, GitLab, CircleCI, Microsoft Azure DevOps Pipelines, and Jenkins. Specifically for GitHub, Docker Scout is able to display helpful information through the popular Docker Build and Push GitHub Action.
By adding Docker Scout with Sysdig to the GitHub pipeline workflow, developers can get vulnerability and runtime insights when building/pushing images, and view the comparison between the new image and the current release in production.
Choose where you want to view and manage security issues
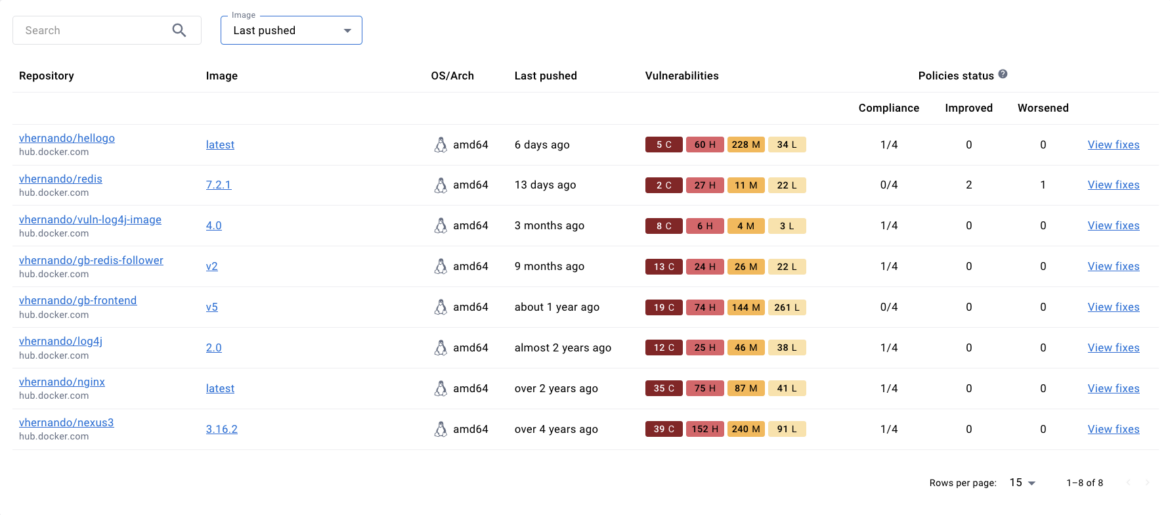
Docker has enabled the results from Docker Scout to be viewed across various interfaces. Container image vulnerability details with runtime insights are delivered and accessible from Docker Desktop, the Docker CLI, Docker Hub, and the Docker Scout Dashboard – in addition to GitHub as noted above.
The Docker Scout Dashboard web console gives developers a view into discovered vulnerabilities but also provides extended information about CVEs along with recommendations on how to bypass vulnerabilities by updating to a different base image.
Benefits of Sysdig runtime insights integration for Docker Scout
Throughout this blog, we’ve touched on the benefits of having runtime insights integrated with Docker Scout. Here’s the TL:DR of what we see as the most significant benefits of bringing the two solutions together.
Ship more secure images
The ability to compare images during the build phase with those running in production gives developers a new lens to help build better images. Beyond remediating in-use vulnerabilities, teams can see which packages are unused and consider if they can be removed to address “container bloat.” Leaner container images have a reduced attack surface with the added benefit of being able to scale more quickly.
Avoid shift-left security gaps
By reinforcing shift-left security with runtime insights, you can strengthen your security standards early in the software lifecycle. There are always potential risks at runtime that can be addressed with Cloud Detection and Response (CDR), however, those risks are significantly reduced when risky vulnerabilities are addressed pre-production.
Accelerate cloud-native application delivery
With runtime insights, software validation processes are faster. You’ll know quickly where there is an imminent risk that needs immediate remediation. In this way, runtime insights shorten software development time and help DevSecOps teams accelerate their cloud-native application delivery.
Reduce noise
There are tons of tools available in the market for identifying vulnerabilities in container images. The key challenge is knowing how to prioritize. Users tell us they are drowning in a flood of vulnerability noise and struggle to know what to fix first. Using runtime insights as an additional filter, we’ve seen teams reduce vulnerability noise by up to 95%.
Conclusion
Identifying, prioritizing, and fixing security issues across the software supply chain is crucial to avoid unnecessary security breaches when software is released into production.
Docker and Sysdig help teams more effectively “shift left” and “shield right,” providing real-time security information to help organizations build cloud-native applications, save time, and be more secure. The integration of Sysdig Secure and Docker Scout offer users new ways to stay on top of known CVEs and ensure the security of the software supply chain.


