Vulnerability management has always been a challenge, but today’s security teams are feeling the pressure more than ever. With thousands of new CVEs reported every month, the sheer volume makes it difficult to know where to focus. In-use vulnerability prioritization is one of the most effective ways to cut through the noise, focusing only on vulnerabilities that are actively loaded in runtime.
To focus on what really matters, security teams need better ways to prioritize risk. Instead of trying to fix every critical vulnerability, teams can concentrate on the small percentage that needs to be addressed immediately.
The problem: Vulnerability overload in the cloud
Security teams are drowning in vulnerabilities, with more than 250,000 known CVEs. Every scan uncovers additional issues, making it increasingly difficult to distinguish real threats from background noise. Without a more strategic approach to prioritization, managing these vulnerabilities becomes an unsustainable task.
Many companies have turned to shift-left security to simplify vulnerability management by catching issues earlier in development. In cloud environments, where scanning happens at every stage — design, code commit, build, and deployment — the same vulnerabilities may be flagged multiple times, which can slow down development. To stay ahead, organizations need a clear view of risk; however, balancing security with fast release cycles is a constant struggle.
Meanwhile, developers are stuck sorting through endless lists of vulnerabilities, trying to figure out what actually needs to be fixed. Security teams know they can’t ask developers to patch everything; however, without the right context, vulnerability management often ends up slowing down releases while still leaving critical risks unaddressed. This leads to alert fatigue and wasted effort fixing vulnerabilities that may never be exploited.
Why traditional prioritization frameworks fall short
Many organizations start with using severity scores to prioritize vulnerabilities, assuming that fixing all “critical” and “high” severity issues will reduce risk. While this may seem like a logical approach, it doesn’t scale effectively. Even after filtering out medium and low-severity vulnerabilities, teams are still left with more issues than they can realistically address.
The real problem is that not all vulnerabilities are equally dangerous, even when they are all “critical” severity. Severity alone doesn’t determine risk. Some critical vulnerabilities may exist in packages that are never actually used in production, meaning they can’t actually be exploited by attackers. Meanwhile, a lower-severity vulnerability that is actively exposed at runtime could provide an entry point for attackers. Without proper context regarding these vulnerabilities, relying solely on severity scores can lead teams to draw the wrong conclusions.
Secure your vulnerabilities – effectively
Vulnerabilities in the cloud are different – make sure your strategy is, too.
The solution: In-use vulnerability prioritization
A more effective way to focus on real risks is with in-use vulnerability prioritization — identifying vulnerabilities in packages that are actively running in production, as these are the only ones that can be exploited. By leveraging runtime insights to filter out unnecessary noise, this approach eliminates the guesswork from vulnerability prioritization, letting teams focus remediation efforts where they are most effective.
Sysdig’s vulnerability management solution enables users to identify in-use vulnerabilities with a single click. From there, teams can refine their focus even further with additional filters. They can prioritize vulnerabilities with known exploits, ensuring that actively targeted threats move up the list. They can also filter for fixable vulnerabilities, allowing security teams to spend time on issues they can actually remediate.
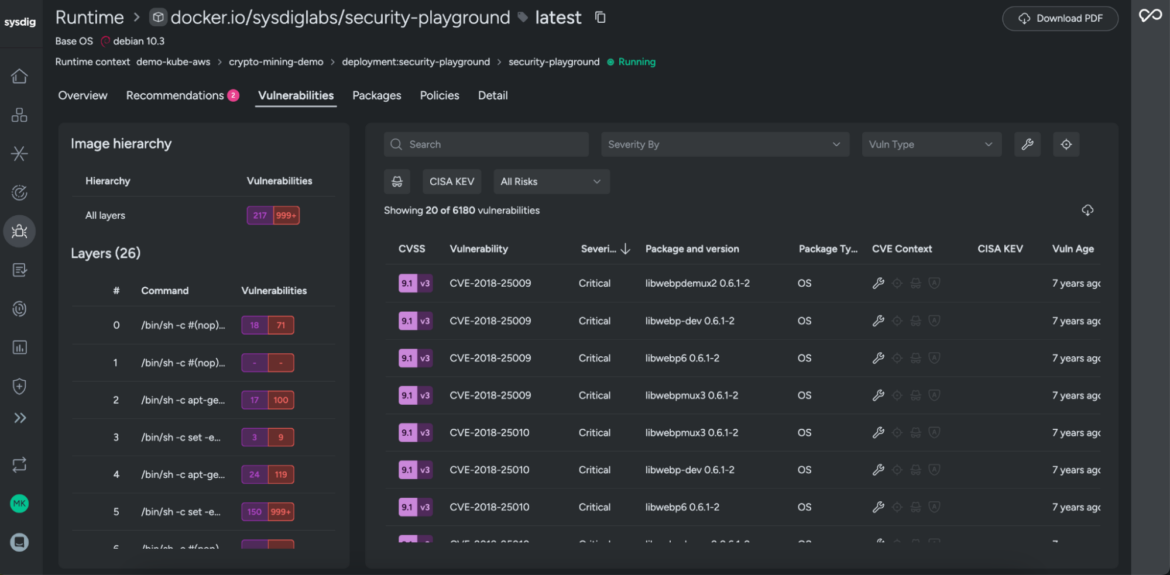
With the power of in-use prioritization, security teams can dramatically reduce the number of vulnerabilities they need to address. By isolating vulnerabilities that are in packages loaded at runtime, security teams can reduce their scope to a small fraction of their backlog, in some cases by over 95%.
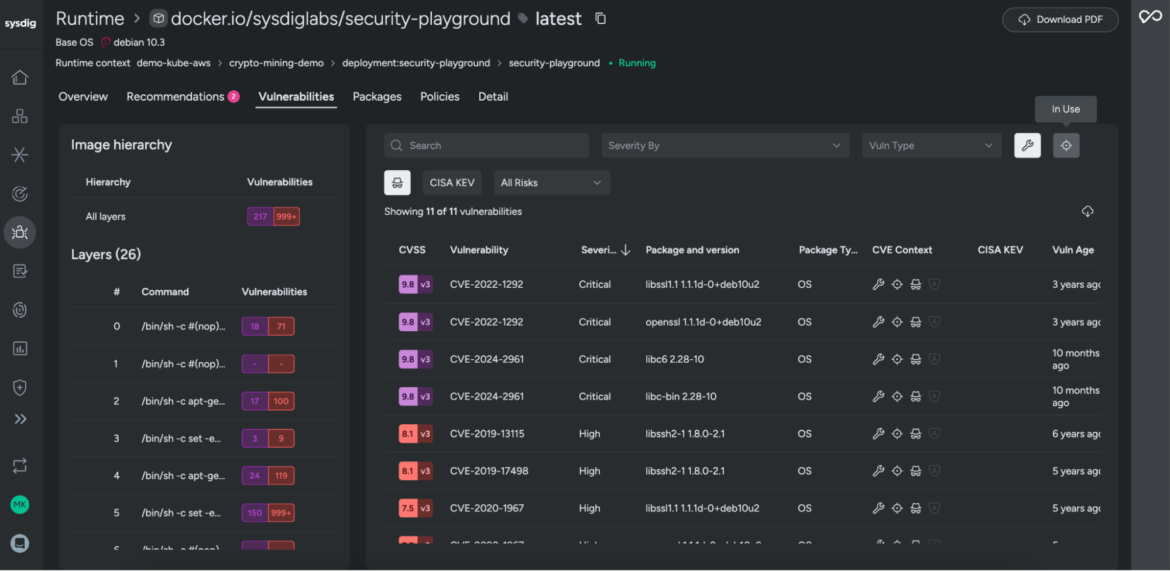
Instead of handing developers an overwhelming list of vulnerabilities, security teams can provide a targeted, actionable list. This helps them fix the most significant risks without slowing down innovation.
Conclusion
Trying to fix every vulnerability is not only unrealistic — it’s a massive drain on time and resources. Without a smarter way to prioritize, security teams and developers get stuck in an endless cycle of remediation work, burning out as they sift through vulnerabilities that are not huge risks.
In-use vulnerability prioritization helps cut through this noise. By using runtime intelligence to filter out non-exploitable vulnerabilities, security teams can eliminate unnecessary work, ease developer fatigue, and remediate vulnerabilities faster — strengthening security without getting in the way of development.
Ready to see how Sysdig can help you go from visibility to action? 👉 Request a demo to see how Sysdig works.



