Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Artificial intelligence has taken over almost every aspect of our everyday lives. In cybersecurity, generative AI models with natural language processing are commonly being used to predict, detect, and respond to threats. But AI security assistants, although an upgrade from traditional machine learning, only provide very basic queries and summarization, which is insufficient to fully comprehend modern cloud attacks. As part of an ongoing effort to improve the cloud detection and response (CDR) experience, Sysdig has announced Sysdig Sage™, which makes it easier than ever to uncover active breach scenarios in real time.
Sysdig Sage for CDR combines AI with security analysis as part of our ongoing mission to protect our customers in the cloud. Sysdig Sage observes your cloud data and generates responses that enable you to stop attackers. This revolutionary new AI assistant can also execute a variety of use cases, including contextual analysis of cloud and workload data, summarized event overview, and suggested remediations to contain an adversary.
Here are just a few of the key new capabilities Sysdig Sage offers to enrich your CDR workflows:
- Statistics on security events: Streamline analysis and proactively address breach scenarios by identifying critical events that need immediate attention.
- Explanation of security events: Bridge skill gaps within security operations with detailed explanations of runtime events.
- Suggested next steps: Reduce response timelines and improve compliance with behavioral details of relevant events at a broader level.
- Contextual awareness: Contextualize the data a user observes to answer questions more precisely and move them across the platform to better visualize threats.
Let's take a look at how Sysdig Sage can help you with a few key use cases.
Use case 1: Elevate skill gaps across operations
With Sysdig Sage, cybersecurity becomes easier for everyone. It refines your investigation journey as your team trawls through volumes of mundane tasks and events on a daily basis. It also helps foster collaborative workflows and motivates the team to stay vigilant for threats.
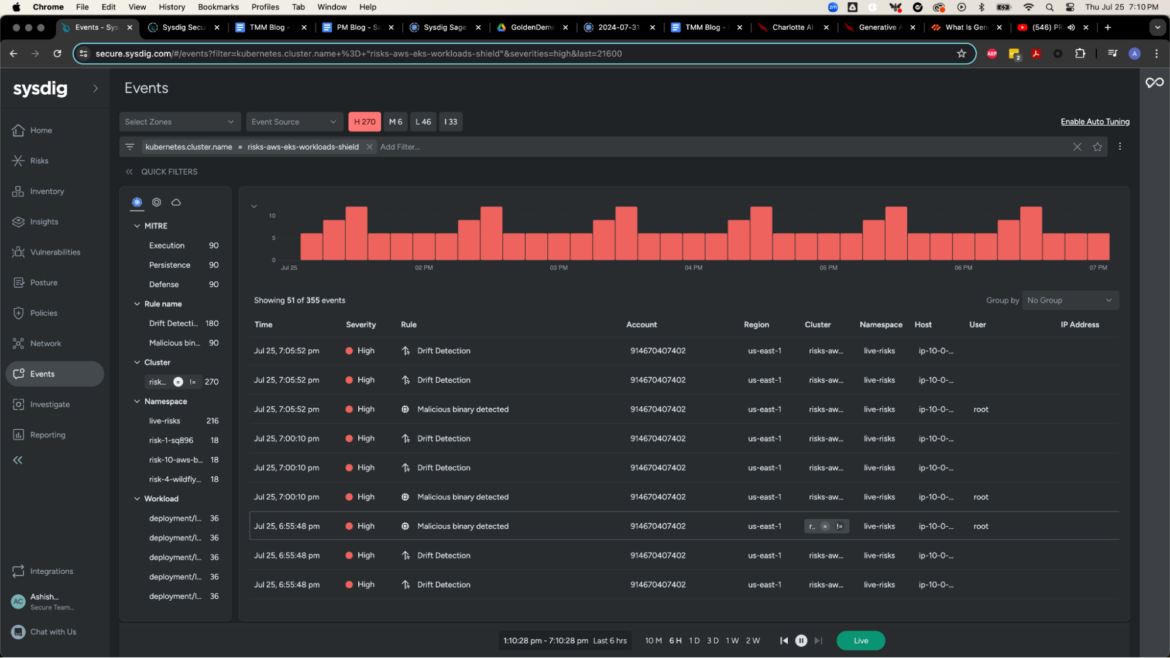
To demonstrate this, let's narrow our scope and search for High severity logs from a specific cluster. Use the Search bar to type the below query.
kubernetes.cluster.name=risks-aws-eks-workloads-shieldSysdig Secure applies this query across volumes of cloud data and filters the events relevant to the chosen timeline and cluster name. At a glance, we have over 300 exclusive events. Even for mature security operations, this volume of events could be overwhelming. Somewhere, somehow, it's likely that a critical blindspot will be missed. These missed details will negatively impact response strategies and may leave an opening for an adversary to walk right in through the front door.
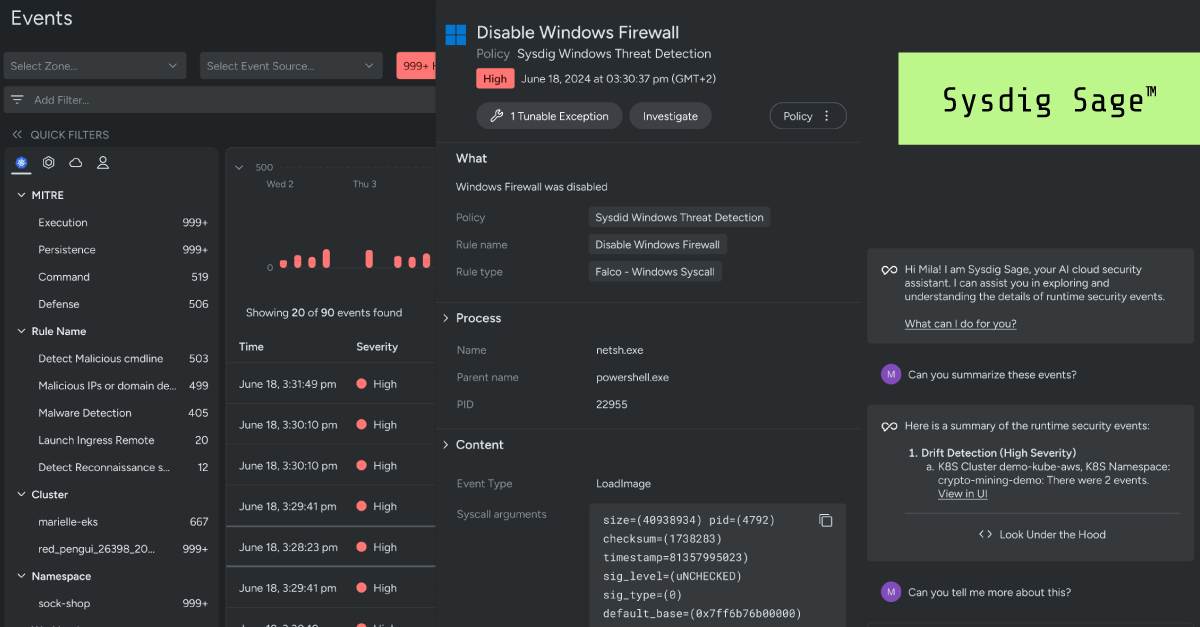
Sysdig Sage alleviates some major operational pain points by enabling users to ask questions in a natural language format, swiftly derive a quick summary of the situation, and deploy prescriptive response strategies to throw a wrench in the adversary's plans.
For example, let's launch Sysdig Sage and ask it to summarize our filtered results.
Summarize events for this cluster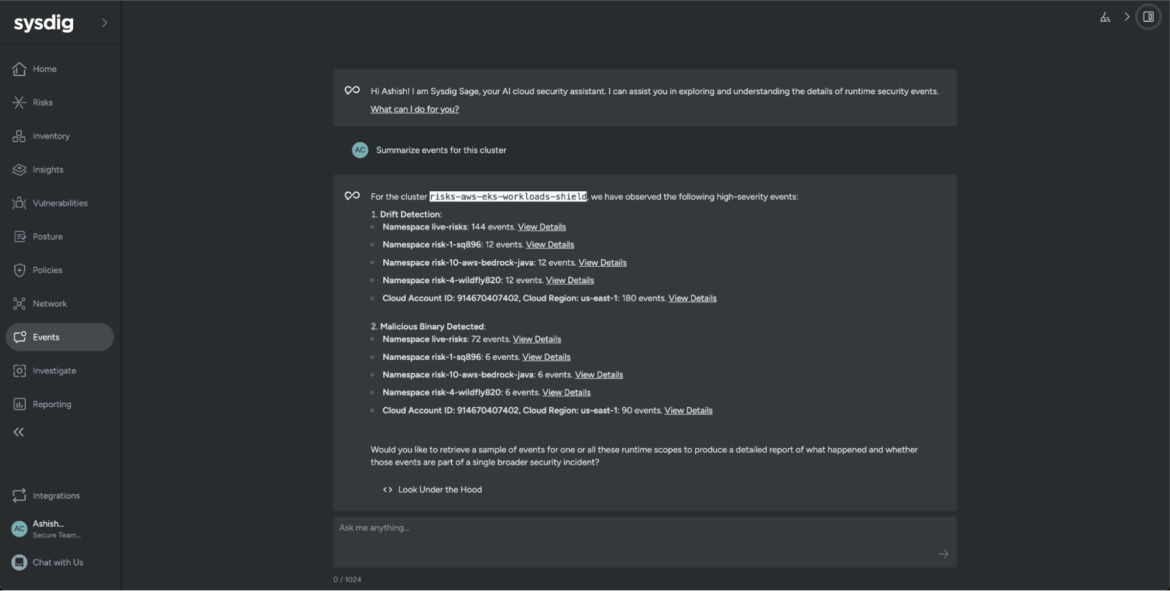
Sysdig Sage for CDR categorized the events under two distinct headers, namely Drift Detection and Malicious Binary Detected. Without any previous context of what the issue is, we now understand that the threat actor has managed to launch a malicious binary on several Kubernetes workloads, and we know that the Drift Detection policy (curated and maintained by our Sysdig Threat Research Team) prevented the listed workloads from being compromised.
This information is enough to alert our security teams so they can deploy their established response strategies and mitigate the risk of a breach scenario.
With Sysdig Sage, every user becomes a security investigator.
Use case 2: Leverage AI to power your investigation
Sysdig Sage for CDR can respond to multiple queries in a row by correlating context from previous responses. This helps your teams uncover additional details relevant to an attack.
During a breach, you have very little time to do the necessary due diligence. We need to collect enough context at speed so the responsible teams can jump in and prevent the adversary from causing further damage.
As an example, let's use Sysdig Sage for CDR to perform a detailed analysis of all the events and generate an investigation report.
Generate detailed investigation report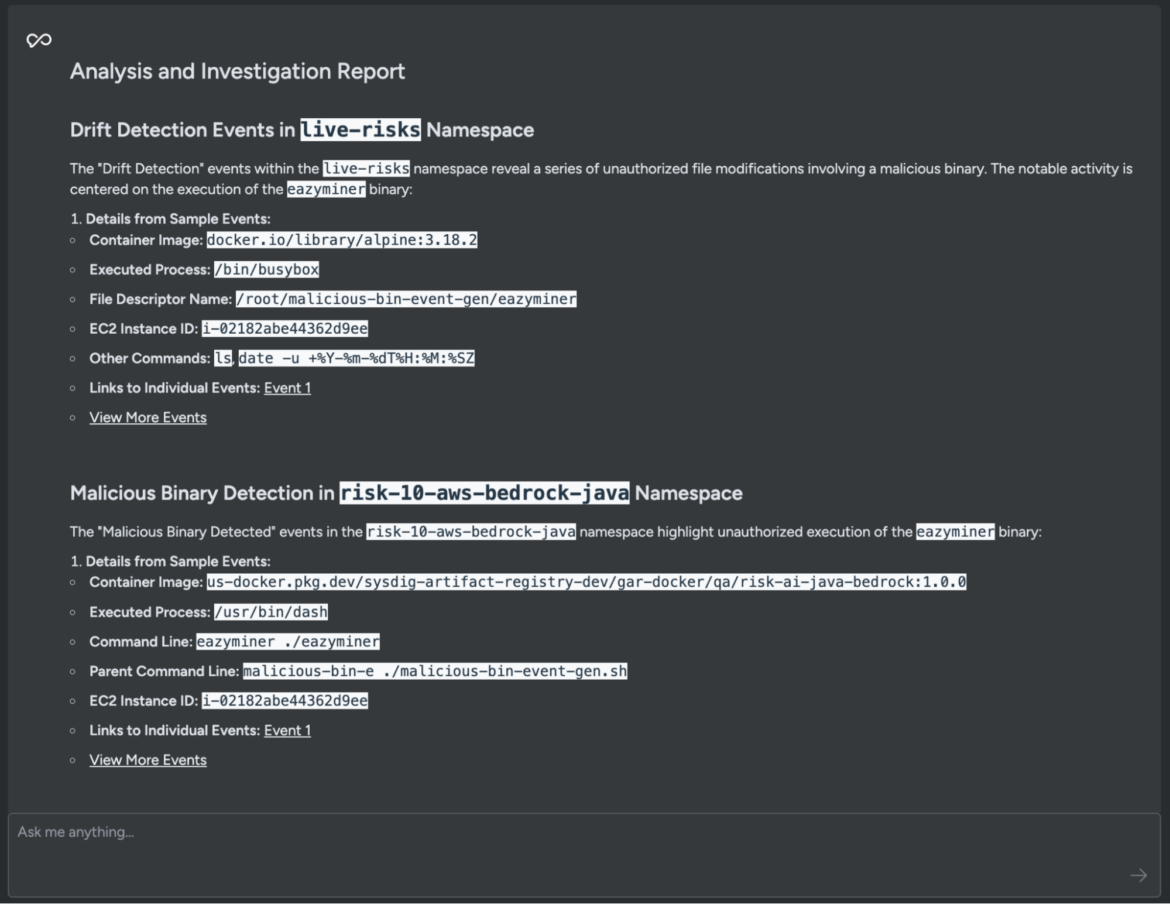
From this report, we notice there's an active miner (easyminer) running within the risk-10-aws-bedrock-java namespace. A quick online search reveals that the detected binary is a legitimate open source mining software. However, the presence of it within our environment is suspicious.
The report indicates that the adversary, after compromising the workload, downloaded and launched a cryptominer to serve its objectives.
Let's ask Sysdig Sage to help us understand the root cause of the detected event.
what was the root cause for the malicious binary detected on risk-10-aws-bedrock-java?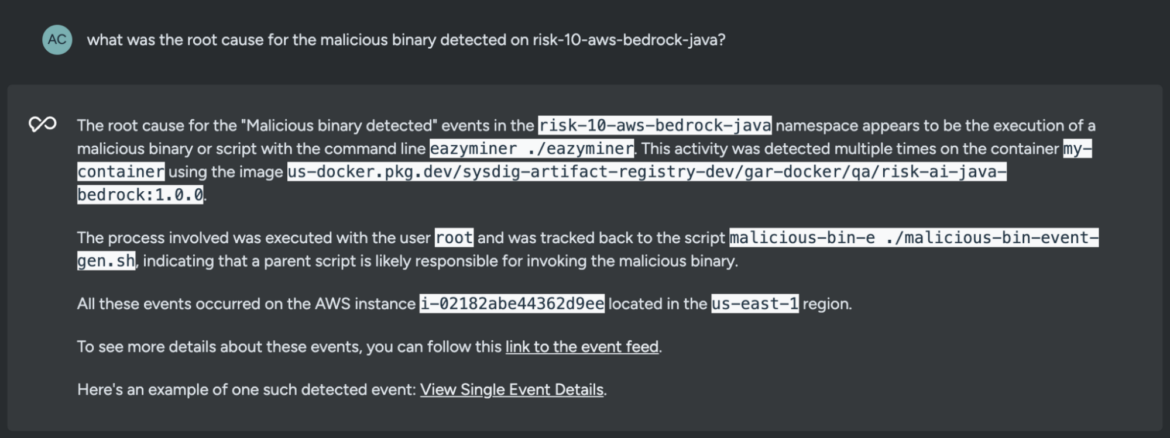
Sysdig Sage for CDR understood our query in natural language and identified that the root cause responsible for triggering the detection event was a shell script malicious-bin-e ./malicious-bin-event-gen.sh
Within seconds, we have enough useful context about the detected malicious binary. Sysdig Sage for CDR has helped us answer the "what" and "why" of the event and saved valuable investigation time. However, our investigation is far from complete.
Our next goal should be to understand the adversary methods used to breach the perimeters and access our workloads. Let's ask Sysdig Sage to enlist the tactics and techniques used by the threat actor according to the MITRE ATT&CK framework.
what MITRE ATT&CK tactics & techniques were used?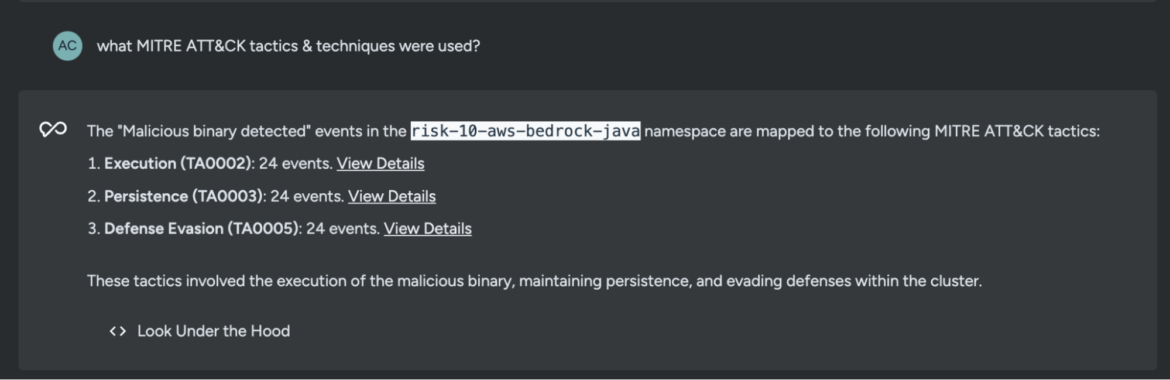
The results show that the threat actor used MITRE ATT&CK tactics to execute the malicious binary, maintain persistence, and evade defenses within the cluster.
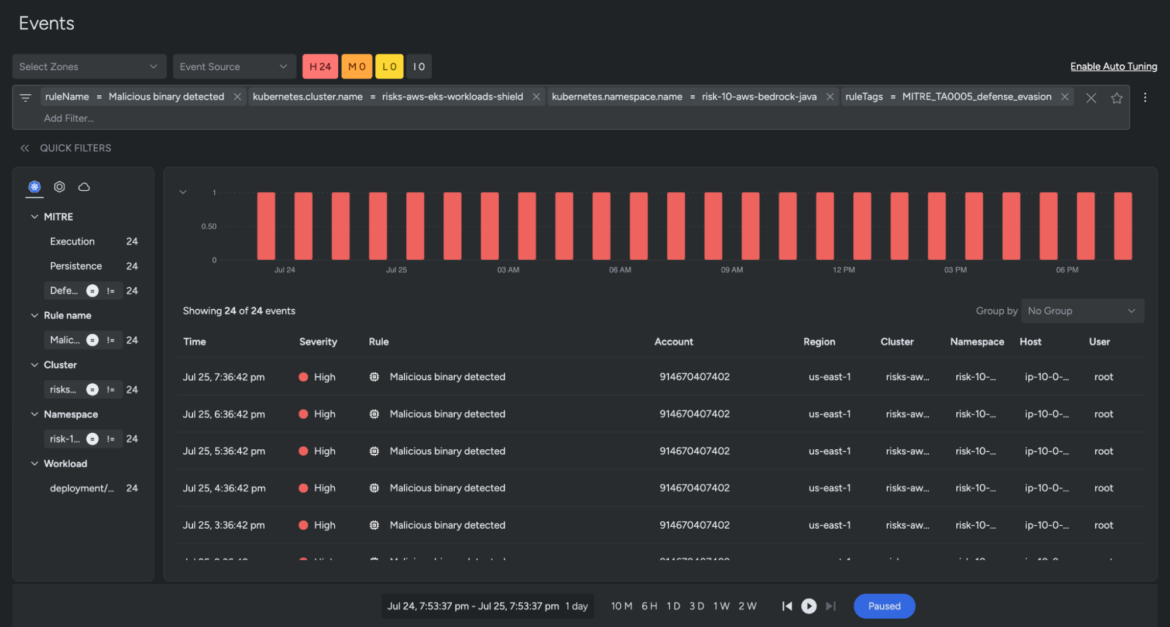
At this stage, if you are curious about what's going on under the hood, you can always use the accessibility options (top right) to pop into the Events Feed. Here, you'll notice filters are automatically applied, and there's a timeline of every malicious binary event detected within our defined cluster risk-10-aws-bedrock-java.
Now, to gain further context on each MITRE ATT&CK tactic, let's ask Sysdig Sage to list the attack path.
list the attack path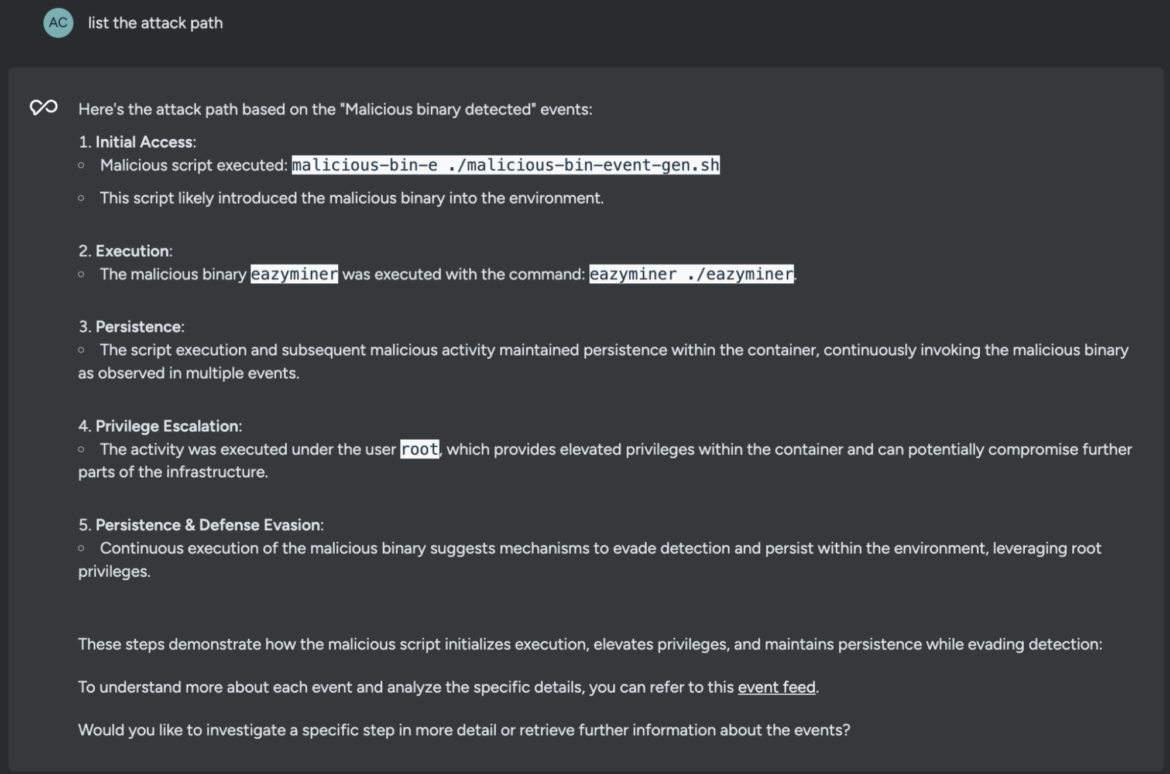
Within seconds, Sysdig Sage for CDR expands the process tree to align each detected event under a specific MITRE ATT&CK category. This helps discover all the possible entry points and the security gaps that were potentially exploited by the threat actor.
But now the real question is, how severe is this event? Let's ask Sysdig Sage to provide us with a blast radius, listing all the workloads that may have been impacted by the threat actor.
how many workloads were impacted?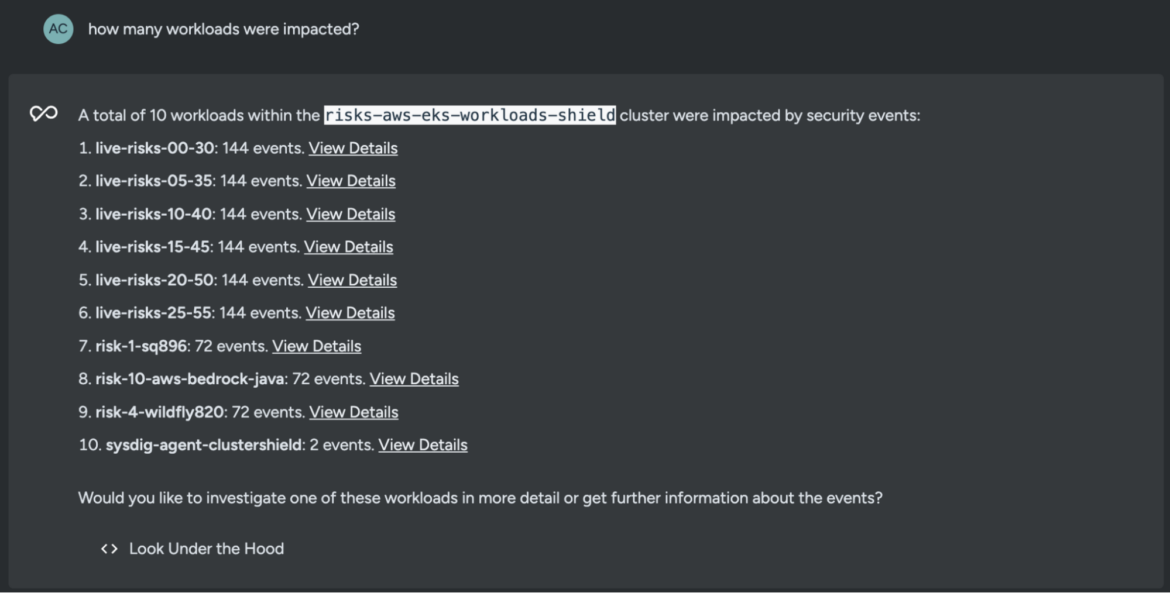
The results indicate that quite a lot of workloads were possibly impacted by the threat actor. After this, you should really be looking for the panic button and calling in the cavalry, aka your SecOps and DevSecOps teams.
Use case 3: Achieve the 555 Benchmark for Cloud Detection and Response
We demonstrated in the previous use cases how you could use Sysdig Sage for CDR as your security assistant and gather the preliminary information crucial for any security investigation. However, if you are the only one holding the fort for your organization, you need to apply temporary fixes before alerting the specialists.
Let's ask Sysdig Sage for suggested steps that may help you to preempt any adverse events, like user credential compromise, SSH key exfiltration, process masquerading, and many more.
how do I fix this?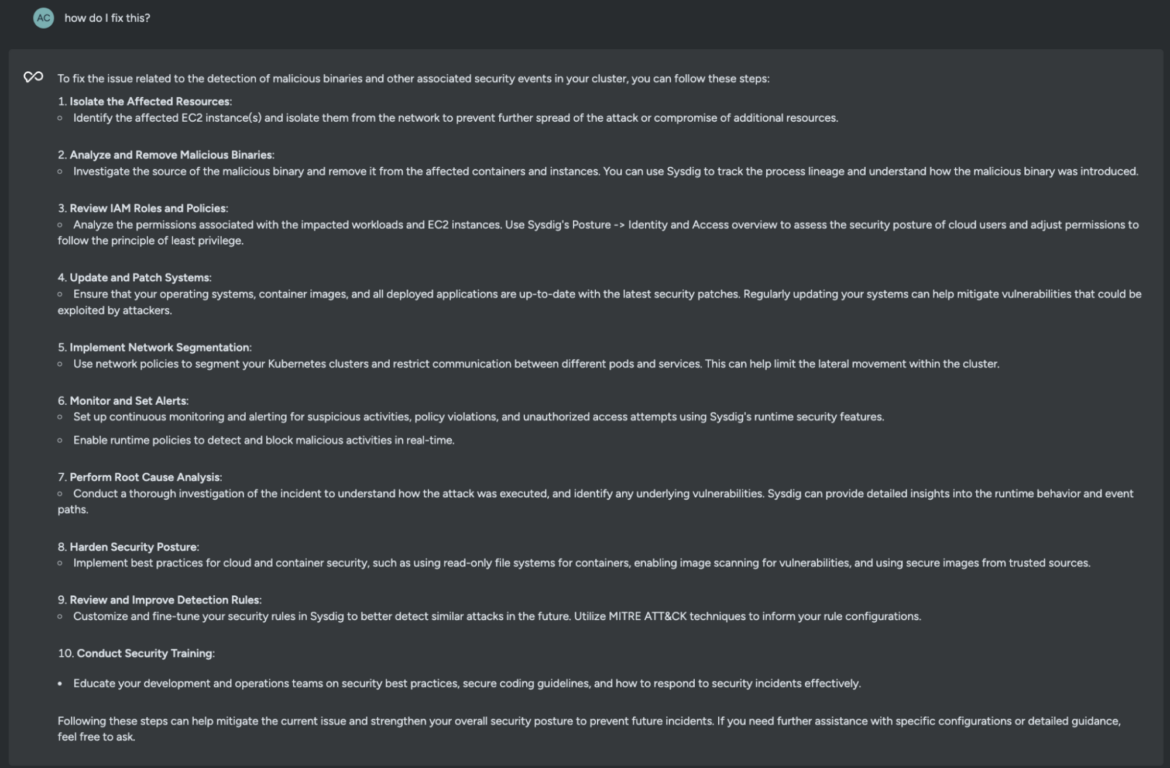
Sysdig Sage for CDR recommends a few best practices to mitigate potential risks and prevent further compromise of your environment. Here, isolating the affected resource seems like a good way to stop the adversary in their tracks.
But in case we didn't know what to do in such a situation, let's ask Sysdig Sage to provide us with detailed guidance.
give me detailed guidance on isolating affected resources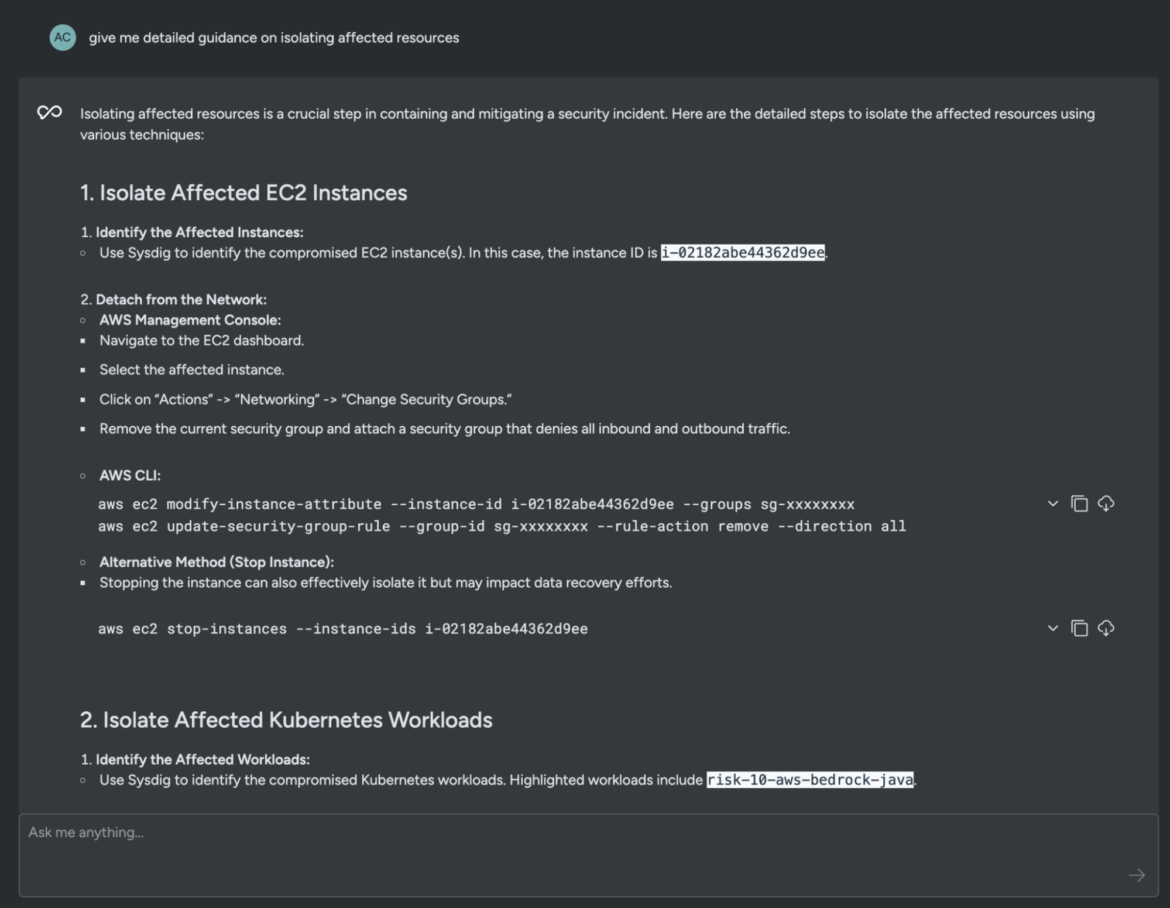
Stay ahead of threats with Sysdig Sage
Sysdig Sage for CDR is the handy security assistant that first, helps you stay calm during an incident, and second, guides you along each step to uncover all the necessary details required for a thorough investigation. It makes a security incident feel like a simple DIY project.
Sysdig Sage empowers security teams to capitalize on the real-time nature of the Sysdig platform and the cutting-edge discoveries of the Sysdig Threat Research team. With Sysdig Sage at your side, you can accelerate your response to threats without leaving the platform.
Join our upcoming seminar: AI-Powered CDR in Action for a technical demonstration of how you can leverage Sysdig Sage to detect, investigate, and respond to attacks in minutes.


