Developers are frequently tasked with working with multiple tools in the cloud-native era. Each of these tools plays a crucial role in the application life cycle, from development to deployment and operations. However, the sheer variety and diversity of these tools can increase the likelihood of errors or the accidental inclusion of critical vulnerabilities and misconfigurations.
To tackle this problem Backstage provided a comprehensive developer portal that offers an integrated perspective on all software resources, documentation, and tools. It’s a one-stop-shop that helps developers manage, monitor, and document the entire software development lifecycle (SDLC). In 2023, the Cloud Native Computing Foundation (CNCF) declared Backstage as the third most rapidly expanding project of the year.
Backstage as its own, already stands out as a robust resource for developers and DevOps teams. However, its utility is greatly enhanced when integrated with Sysdig, which layers additional real-time insights into active vulnerabilities, misconfigurations, and runtime behaviors.
By embedding Sysdig’s security insights directly within Backstage, developers gain immediate visibility into security concerns, significantly accelerating the time to detect and respond to issues. This integration aligns with the cloud-native ethos of agility and efficiency, bringing critical security information to the forefront of the development process.
As we delve deeper into the benefits and workings of the Sysdig-Backstage integration, we will explore:
- How the integration speeds up issue detection by consolidating all relevant information in one place.
- How runtime insights can assist developers in prioritizing vulnerable packages that are currently in use.
- How developers can gain comprehensive visibility into the complete software development lifecycle (SDLC) using runtime insights.
- How this integration streamlines the process of vulnerability management, facilitating collaboration between developers and security teams.
- How the integration empowers developers to take proactive responsibility for application security, minimizing the need for security operations (SecOps) teams to intervene in identifying and communicating vulnerabilities for remediation.
Let’s get started!
Backstage and Sysdig: Pillars of Modern Development
Backstage has emerged as a developer portal, offering a one-stop-shop for developers to access tools, services, and information crucial to their daily tasks. It was created at Spotify, and then donated to the CNCF.
Before Backstage, developers were forced to use many different tools from code repositories, continuous integration and delivery (CI/CD) pipelines, monitoring and observability platforms, to security scanning and compliance tools.
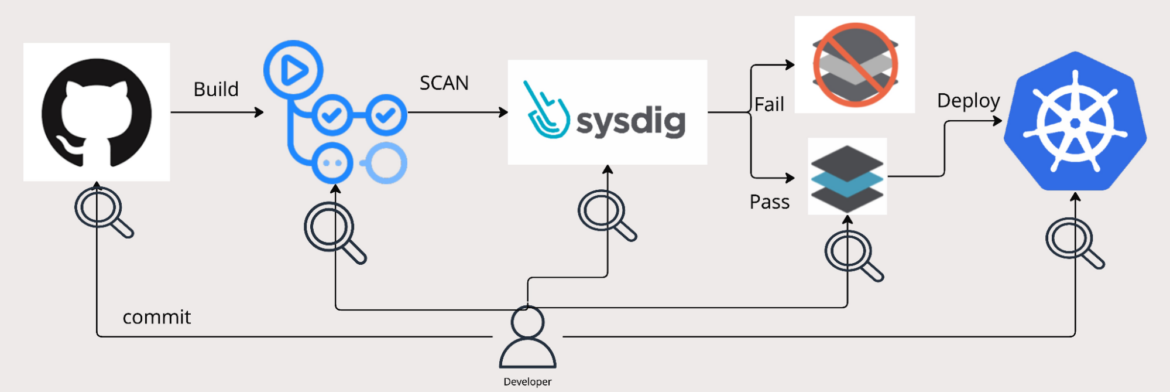
The sheer number and variety of these tools complicate the development landscape and lead to complex, frequently manual processes. This complexity heightens the risk of errors or oversights, significantly increasing the chances that vulnerabilities or misconfigurations might inadvertently make their way into production.
Backstage introduces a single-pane-of-glass that aggregates information and controls from various tools. However, the deep security aspect at build, deploy, and runtime is necessary to enhance its power.
Sysdig’s Cloud Native Application Protection Platform (CNAPP) is designed to reduce the time it takes to detect and investigate risks, and respond to incidents. By integrating Sysdig with Backstage, developers can gain access to Sysdig’s insights on vulnerabilities, misconfigurations, and runtime behaviors directly within their primary workspace. This makes it easier for developers to identify and address potential issues in their applications earlier in the devops cycle.
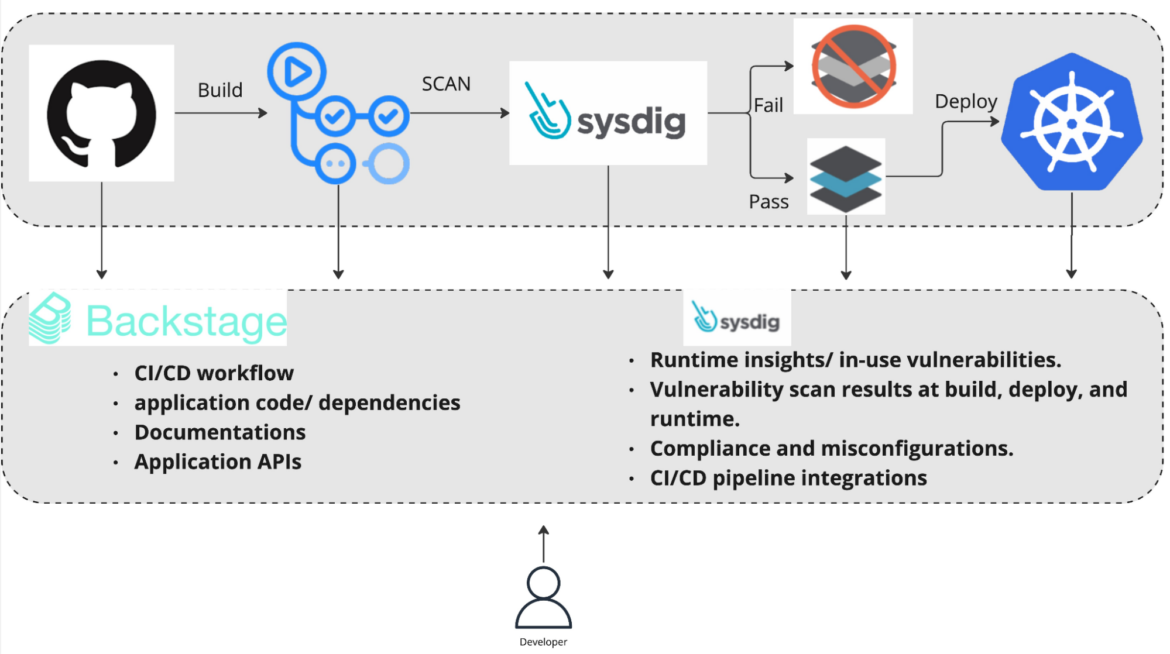
The integration of Sysdig with Backstage significantly enhances this ecosystem by bringing visibility into application behavior, security vulnerabilities, and potential misconfigurations directly to the forefront of the developer workspace. Enriching Backstage with Sysdig’s run-time insights improves developer efficiency by allowing them to identify and remediate the highest priority issues while avoiding the need for multiple tools, logins, and context changes which reduces the chances of errors or vulnerabilities being missed.
Integrating Sysdig with Backstage
Sysdig released an official plugin for backstage. The plugin interacts with the Backstage backend and frontend through APIs which leverages annotations in the ‘catalog-info.yaml’ files of components.
APIs: Sysdig plugin extends Backstage’s backend via APIs to perform various operations, such as fetching vulnerability scan results from sysdig backend.
Annotation: Annotations are a key concept in the Backstage Catalog, used to attach metadata to entities defined in ‘catalog-info.yaml’ files, such as links to documentation, system dependencies, and integration points with tools like Jenkins for CI/CD, or Sysdig for security insights.
To install the Sysdig plugin, please follow the steps on this GitHub page.
Example Workflow
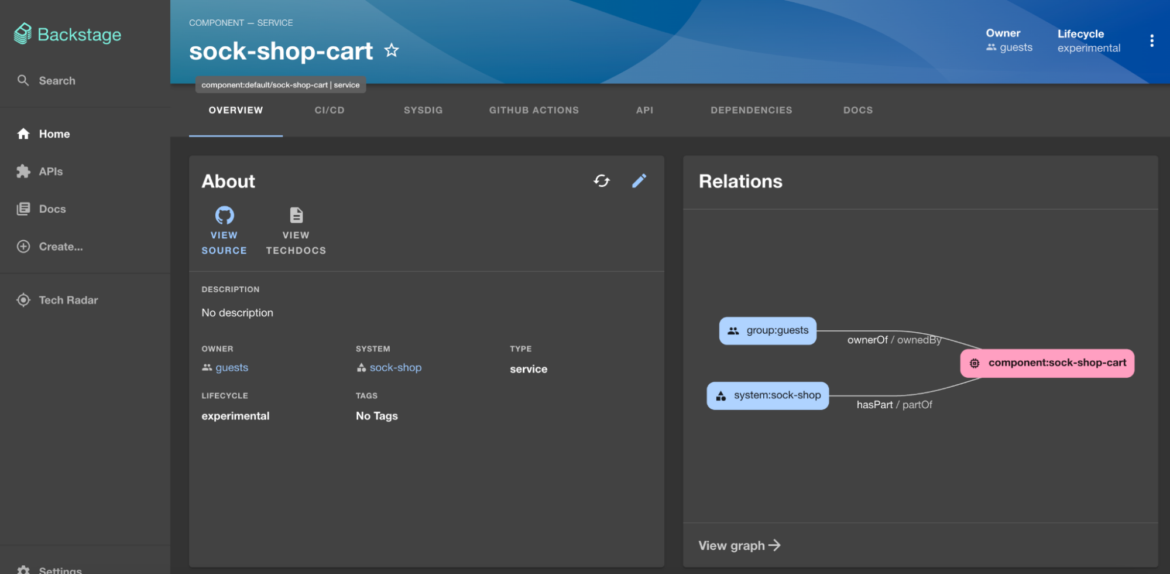
A service is registered in the Backstage Catalog with a catalog-info.yaml file, which includes annotations linking to its source code repository and other integrations.
Adding service to backstage
Here is an example of a ‘catalog-info.yaml’ for a service called “sock-shop-cart”. It is linked to the source code on GitHub repository using annotation “github.com/project-slug”.
apiVersion: backstage.io/v1alpha1
kind: Component
metadata:
name: sock-shop-cart
annotations:
github.com/project-slug: JosephYostos/secure-inline-scan-examples
spec:
type: service
lifecycle: experimental
system: sock-shop
owner: guestsCode language: Perl (perl)Once the service is added to the catalog, the sock-shop-cart can be managed from Backstage.
Scanning Images with GitHub Actions and Sysdig
Sysdig and Backstage also integrate with Github Actions. Every time a commit changes to the code, a pipeline action will be triggered. And the image will then be scanned for vulnerabilities and misconfigurations by Sysdig to ensure its security before being pushed to the registry or rejected if it does not pass the predefined security policy. You can read more about Sysdig and GitHub Actions integration here.
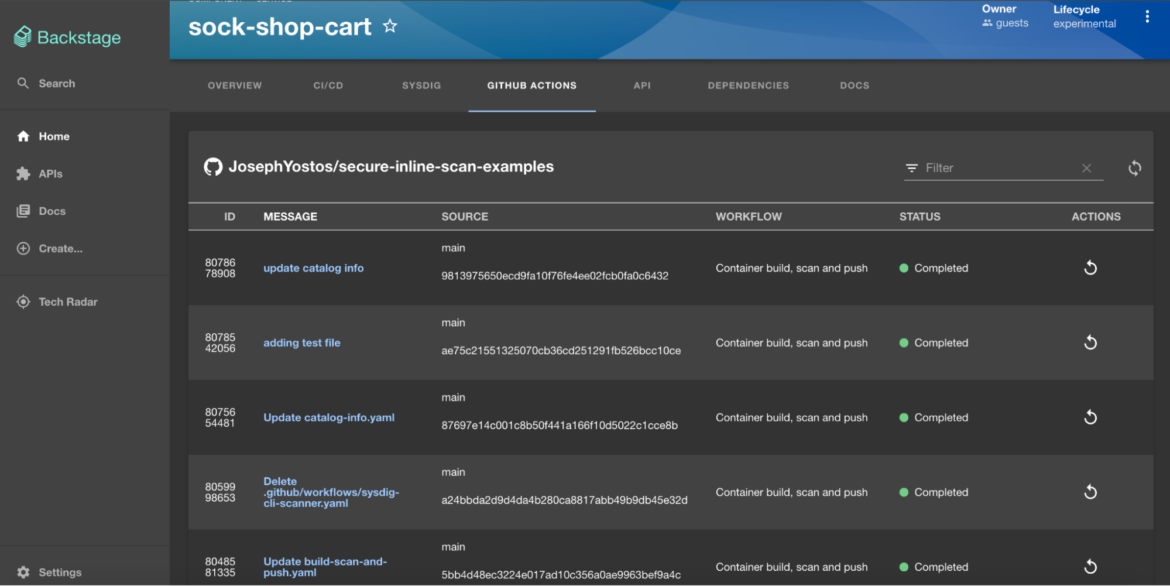
Pipeline scan
Now, after the changes have been committed and the pipeline workflow results verified, the scanning results need to be checked. To facilitate this, the following annotation is added to the service.
sysdigcloud.com/image-freetext: docker.io/josephyostos/testactionsCode language: Perl (perl)“sysdigcloud.com/image-freetext” is a free text query that can be used to search for anything in the pipeline scan results. In the given example, the registry and image name are defined to obtain the image scan results for vulnerabilities and misconfigurations that has been conducted during the image build time.
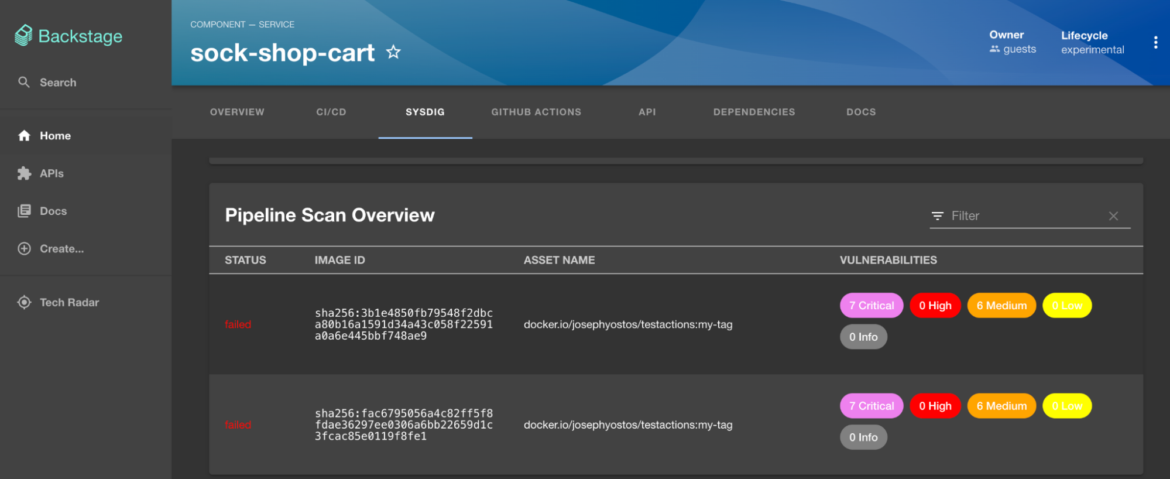
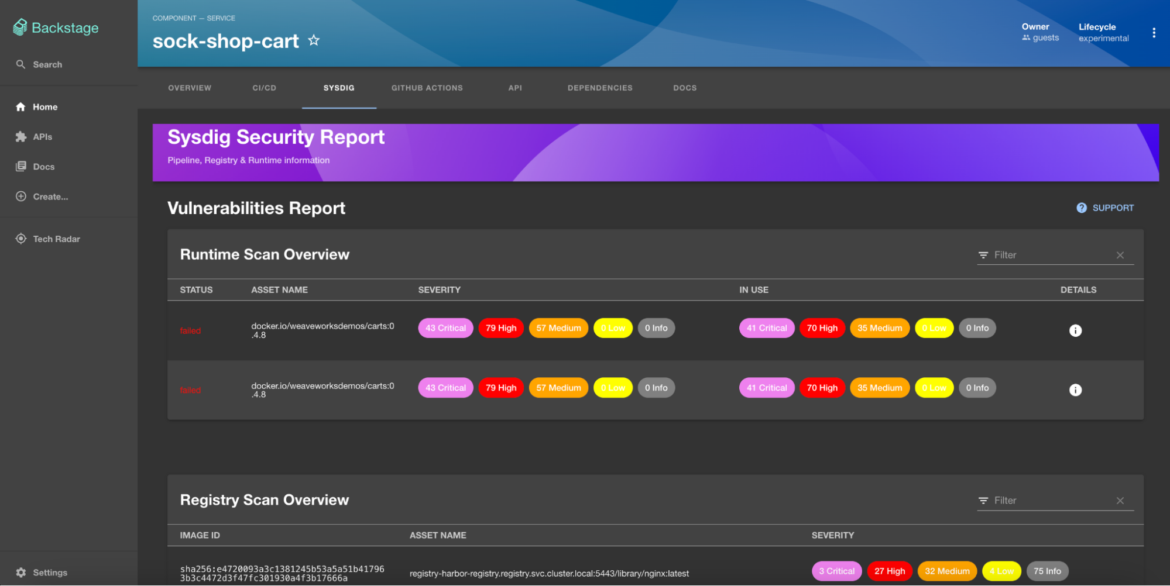
Runtime Insights
As developers now become responsible for the full application lifecycle, it became very important to be aware of vulnerabilities at runtime and also what vulnerable packages are in-use. For this purpose, the following annotation can be used to fetch the runtime scan results of the sock-shop-cart application.
sysdigcloud.com/kubernetes-namespace-name: sock-shop
sysdigcloud.com/kubernetes-workload-name: sock-shop-carts
sysdigcloud.com/kubernetes-workload-type: deploymentCode language: Perl (perl)In-use information helps developers prioritize fixes for packages that are actually loaded in memory and pose a high risk.

Secure more
Sysdig provides curated annotations allowing developers detailed views into the potential risks associated with their current build. For example, in addition to what we have mentioned, application owners can fetch registry scanning results, compliance reports, and more.
All the available annotations from Sysdig are available in this source file
Here is an example of how the ‘catalog-info.yaml’ will look like at the end.
apiVersion: backstage.io/v1alpha1
kind: Component
metadata:
name: sock-shop-cart
annotations:
github.com/project-slug: JosephYostos/secure-inline-scan-examples
sysdigcloud.com/image-freetext: docker.io/josephyostos/testactions
# VM Runtime
# sysdigcloud.com/kubernetes-cluster-name: sock-shop-cluster
sysdigcloud.com/kubernetes-namespace-name: sock-shop
sysdigcloud.com/kubernetes-workload-name: sock-shop-carts
sysdigcloud.com/kubernetes-workload-type: deployment
# VM Registry
sysdigcloud.com/registry-vendor: harbor
sysdigcloud.com/registry-name: registry-harbor-registry.registry.svc.cluster.local:5443
# Posture
sysdigcloud.com/resource-name: sock-shop-carts
spec:
type: service
lifecycle: experimental
system: sock-shop
owner: guestsCode language: Perl (perl)Conclusion
The integration of Sysdig with Backstage marks a pivotal advancement in the cloud-native development landscape. With this integration, software developers now have a centralized hub to manage, track, and protect their applications. By making vital security information readily accessible, it empowers developers to proactively manage application security, reducing the dependency on Security Operations teams to identify and relay vulnerabilities for resolution.
Consequently, this integration not only enhances developer efficiency but also accelerates the identification and mitigation of potential issues, reinforcing a culture of security and agility in cloud-native application development.


