The number of detected common vulnerabilities and exposures (CVEs) has significantly increased in the past decade. In the last five years, security researchers reported over 100,000 new CVEs. The highest reported annual figure was in 2022, with over 25,000 new CVEs. This number can overwhelm any security team if it’s not managed correctly between assessment, reporting, remediation, and monitoring.
The best approach to handle vulnerabilities in cloud-native space is to adopt risk-based vulnerability management, the concept Sysdig introduced last year to leverage Runtime Insights and focus on the in-use packages.
This approach will help security teams prioritize mitigation based on in-use exposure or risk, avoiding fatigue or stress caused by the accumulation of priority alerts.
Security and compliance teams can maximize vulnerability management operational efficiency if they can rapidly identify, track, and report risk trends.
Sysdig Risk-based vulnerability overview
Sysdig Secure now offers a trend analysis dashboard, providing insight into how vulnerability scanning metrics varied over time. This level of information is strategic in the following ways:
- Providing high-level executive reports showing the vulnerability risk trends in the environment.
- Facilitating the risk data-driven decisions to maintain an acceptable level of risk.
- Increase success in compliance programs by reducing vulnerability management policy failures.
Risk trends powered by Runtime Insights
Risk trends are the changes over time as new vulnerabilities are discovered and old vulnerabilities are remediated or excluded. Tracking risk trends helps you assess threats to your environment and make decisions to lower the risk level in your environment.
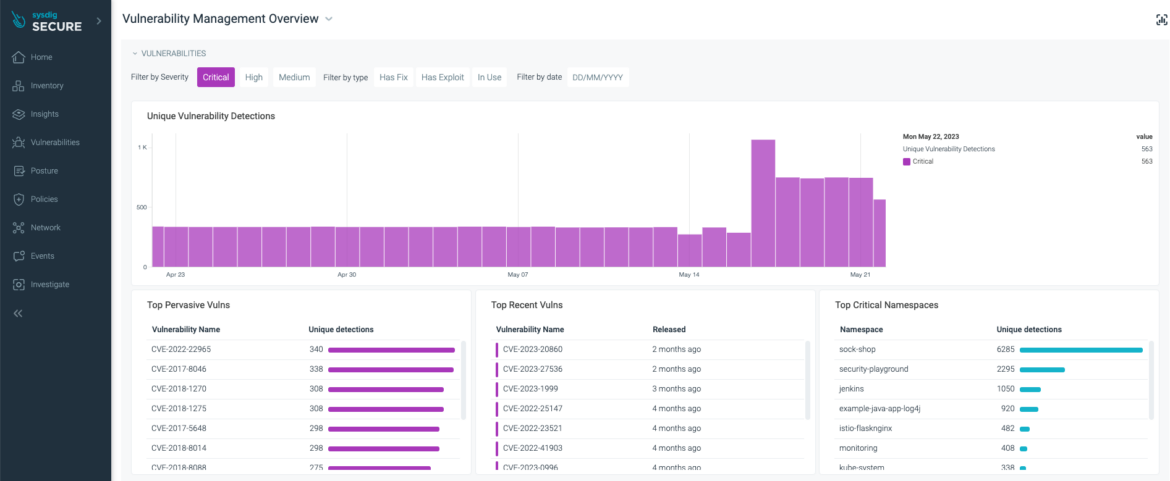
The new vulnerability management dashboard displays changes in the number of vulnerabilities over time, making it easy to identify problematic periods and dig deeper to address their potential causes.
For example, if you want to know if there has been any change in critical vulnerabilities in the last 30 days:
- Review the metrics graph to see trends
- Filter by severity: select only critical
Suppose you see a significant change on a specific day. In that case, you can click on that day and see if a new vulnerability popped into your environment or if a new workload was added that introduces new vulnerabilities.
When you click on a particular day, the following dashboard widgets will be updated:
- Top Pervasive Vulns
- Top Recent Vulns
- Top Critical Namespaces
Filtering and scoping of data
In many cases, you may have a namespace or an application and want to see if it is trending in the right direction.
In this scenario, you can customize the dashboard to focus on a particular namespace or cluster.
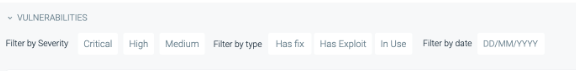
With the risk-based vulnerability management concept in mind, you can lower the number of actionable vulnerabilities in your dashboard by adding the following filters:
- Has Fix: Identifies if a fix is available to address the vulnerability.
- Has Exploit: Indicates if there is a known path for exploiting the vulnerability.
- In-Use: Vulnerable packages that are actually in use.
Reporting results
Reporting this data and showing how the security team’s effort leads to trending down the vulnerability risk is very important. Sysdig can provide that through the following:
- Export Widget data to csv or pdf.
- Any data viewable in the dashboard is available via a Public API.
- Schedule reports based on CVE with affected asset information.
Stay compliant
Compliance is not a one-time job. You set the baseline policies to define expectations and the accepted level of risk, but you keep maintaining and reassessing these policies.
Imagine you have some policies you created for either SLAs or compliance programs like PCI or GDPR. The vulnerability management dashboard will help you to understand what policies are failing the most, where they’re failing, and which controls are failing inside those policies.
In the following example, I’ve activated a predefined policy called “Sysdig Best Practices.” This policy will alert for any image with a critical vulnerability that has a fix for more than 30 days. Check how the Rule is predefined.
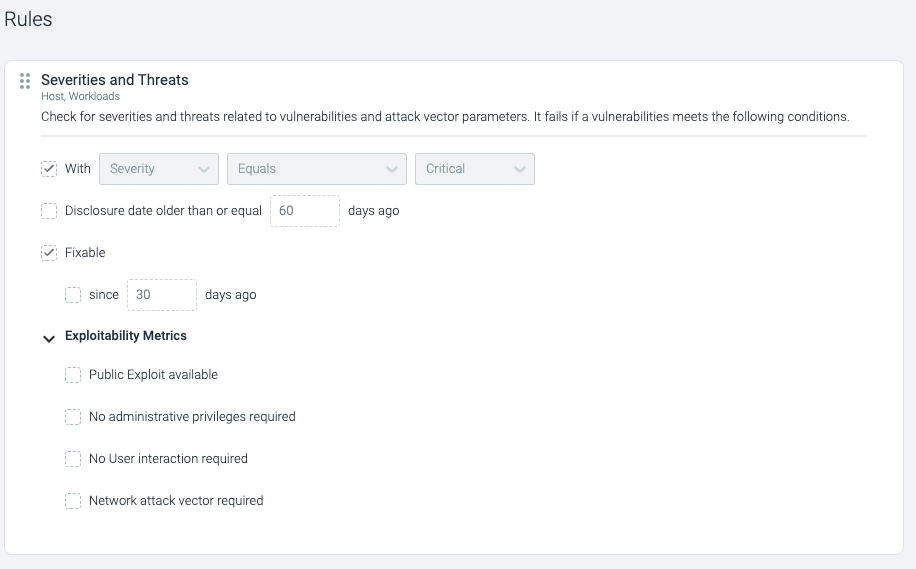
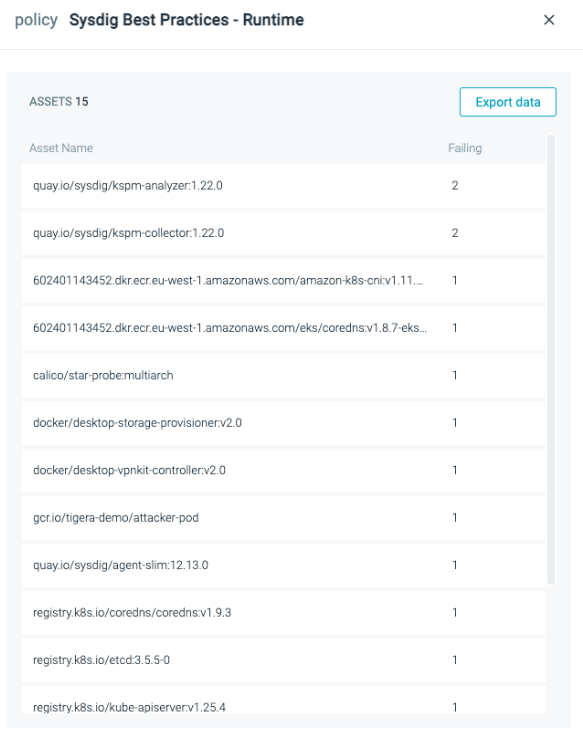
From the dashboard in the following screenshot, you can quickly tell that 15 assets are failing to comply with this policy. In other words, 15 assets have vulnerabilities with fixes available for more than 30 days.
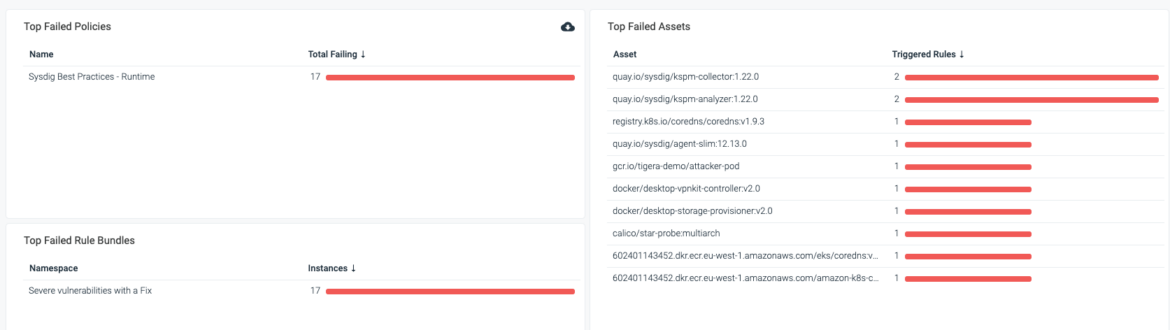
You can export this list of assets to CSV and attach it to a Jira ticket to get addressed quickly.
Conclusion
The number of discovered CVEs is increasing massively year after year. However, adopting a risk-based vulnerability management approach and tracking the risk trends in the environment helps security teams to maintain the risk at the accepted levels.
The Sysdig vulnerability management dashboard is your day-to-day tool to identify the riskiest areas in your cluster, detect policy failures as early as possible, and generate reports showing the vulnerability risk trending.
To learn more about risk trends, visit our documentation page.