Adversaries often use complex, multi-stage cloud attacks that evade traditional security measures, which struggle to fully visualize, prioritize, and respond to threats. Multi-domain correlation addresses this by analyzing data across diverse domains — including networks, applications, databases, and storage — to uncover potential weaknesses and attack paths across interconnected resources.
This approach enhances security posture, providing holistic threat detection and response capabilities in today’s complex cloud environment.
Challenges for multi-domain correlation
A good balance between security, compliance, and operational efficiency is needed for multi-domain correlation. However, a few challenges prevent organizations from achieving this end-to-end visibility across their cloud estate.
Distributed infrastructure
Larger and hybrid cloud environments need more expensive technologies. Processing and correlating vast amounts of data across domains like identity, endpoints, services, data sources, network, and applications is computationally expensive. For example, non-native integrations produce logs with varying data formats and semantics. If poorly configured, the integrations may fail to ingest the right data that enrich cross-domain detections, speed up investigation metrics, and prioritize risks.
Siloed technologies
Siloed technologies operate across different domain types and prevent a comprehensive view of an organization’s cloud estate. These fragmented features apply inconsistent security policies across the cloud, thereby increasing the overall risk profile. For example, a misconfigured identity may assign excessive permissions and inadvertently allow an insider threat actor to bypass security rules, operate in plain sight, and move laterally across cloud accounts. When an incident is detected, security teams are forced to waste valuable minutes correlating data from multiple alerts, dashboards, and logs.
Compliance and governance
Compliance requirements can be complex and nuanced. Certain regulations have strict requirements around data privacy and handling of sensitive information. These regulations may restrict moving or combining data from different geographic regions or business units. For example, varying data protection laws like NIS2, DORA, GDPR, and HIPAA limit the ability to freely correlate data across domains. Many organizations find it difficult to keep pace with the changing frameworks, audit every correlation rule, and ensure their compliance checks are up to date across all domains.
Secure Your Cloud in Minutes – Your Checklist for Meeting the 555 Benchmark
Measure how fast your security team can counter attackers with Sysdig’s 555 Benchmark for Cloud Detection and Response.
Building blocks for multi-domain correlation
Multi-domain correlation requires a systematic approach to integrate data from various sources – such as network logs, identity and access management (IAM) logs, application events, and endpoint behaviors – in order to detect security threats, enforce compliance, and streamline incident response.
Centralized platform
Organizations often rely on a mix of cloud-native and third-party services to collect, aggregate, and analyze data from various cloud environments. There are several benefits of a unified platform:
- Enables security teams to collect data, analyze it, and correlate key data points to identify and address risky combinations
- Enhances multi-domain correlation by providing a clear, interactive view of security events and patterns as they unfold
- Facilitates continuous tuning and optimization of correlation rules to ensure their accuracy, reduce false positives, and improve the system’s ability to detect true security incidents across diverse cloud domains
- Consolidates features that are innately compatible and seamlessly integrates them without overhead costs
- Fosters a coordinated response to incidents across teams, improving communication and collaboration
Cloud APIs for data ingestion
Cloud APIs for data ingestion are essential because they provide a structured, scalable, and real-time method for aggregating data across multi-domain infrastructure, allowing for a centralized view across hybrid or multi-cloud setups. Through APIs, security teams can extract, normalize, and analyze data from multiple sources to achieve comprehensive visibility and detect complex, multi-stage security incidents early in the attack chain.
Agent and agentless monitoring
For robust multi-domain correlation, both agent-based and agentless monitoring provides comprehensive coverage and insights into security events that span across multiple cloud domains. For example, an agent may detect a privilege escalation on an endpoint, while agentless IAM monitoring detects a change in user role. Together, they suggest potential insider threats or lateral movement.
Artificial intelligence for anomaly detection
Leveraging AI or machine learning for anomaly detection in the cloud enables more accurate and efficient identification of complex threats. For example, well-trained machine learning models are tuned to differentiate between true threats and benign anomalies, detect unusual patterns that traditional rule-based methods might miss, and accelerate incident response with context-rich insights for every detected incident.
Automate response and mitigation
Automated response and mitigation eliminates the risk of human errors in threat investigations and ensures that the response actions are consistent, repeatable, and reliable across all domains. In multi-cloud or hybrid infrastructures, these automated responses allow for scalable operations, reducing the time it takes to address potential incidents.
Secure Your Cloud in Minutes – Your Checklist for Meeting the 555 Benchmark
Measure how fast your security team can counter attackers with Sysdig’s 555 Benchmark for Cloud Detection and Response.
Achieve multi-domain correlation with Sysdig
Sysdig offers a centralized platform to perform multi-domain correlation in the cloud, integrating data from various sources and domains across cloud infrastructure, applications, and container environments. This technology focuses on multi-cloud, cloud-native, and containerized environments to offer visibility across multiple layers, such as network, workload, application, and user access.
Below are some popular use cases:
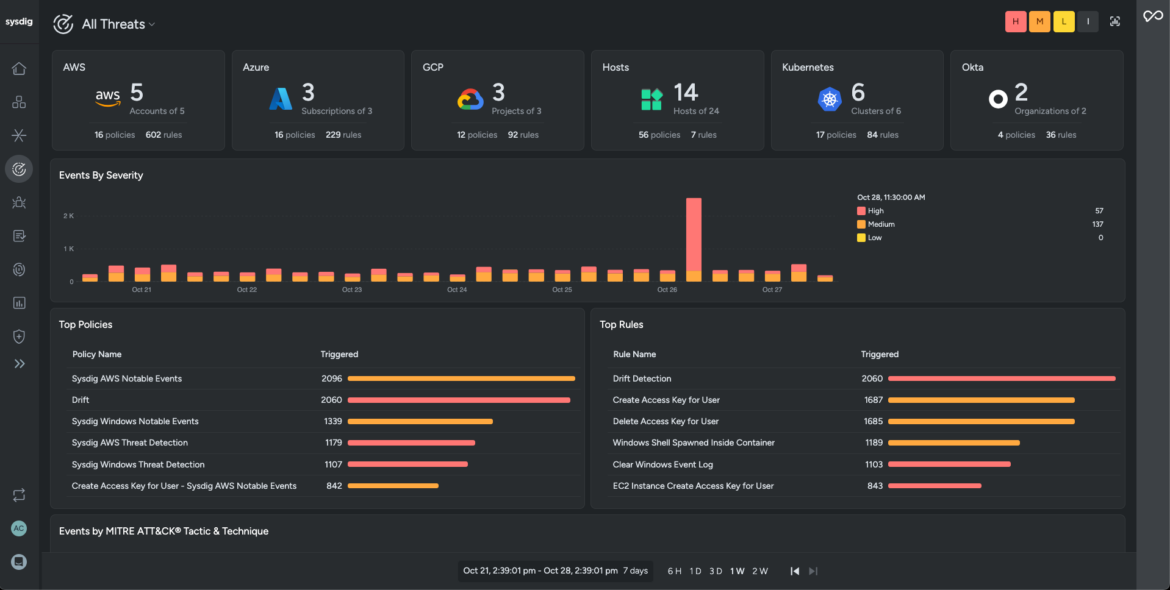
- The Sysdig platform ingests, aggregates, and analyzes security data in a centralized location to provide a single pane of glass view of your multi-cloud or hybrid infrastructure.
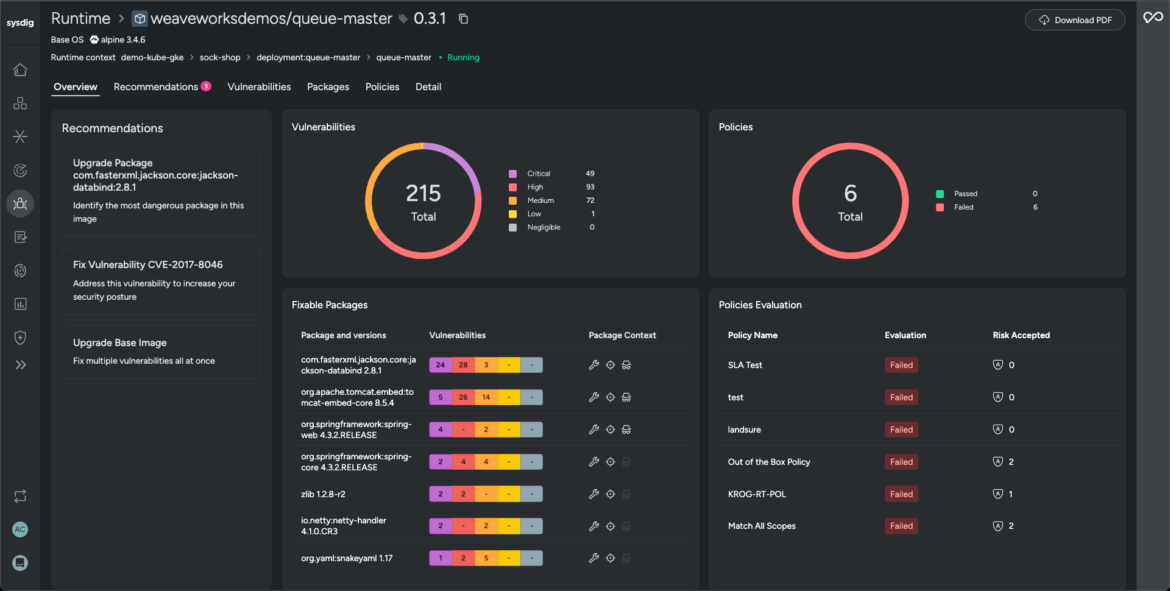
- Sysdig’s layered analysis strengthens security posture by providing a granular view of your container images down to the OS level. It helps organizations to visualize pre-existing gaps, manage vulnerabilities, and address them with guided recommendations.
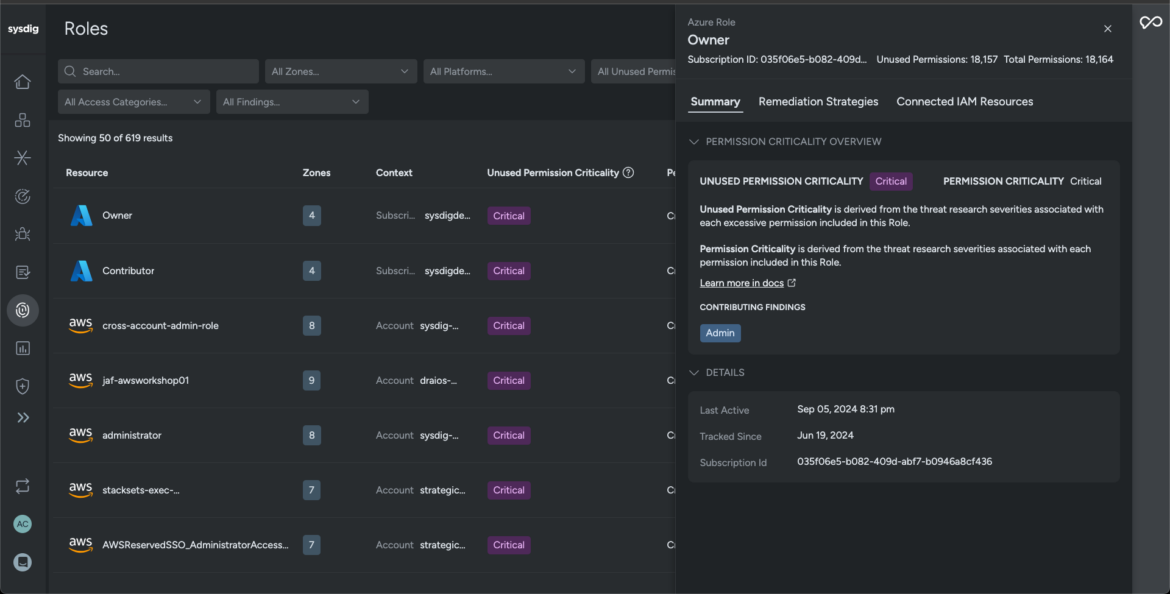
- Sysdig’s context-rich insight helps security teams identify and remediate compromised identities, groups, and user roles responsible in the event of a security breach.
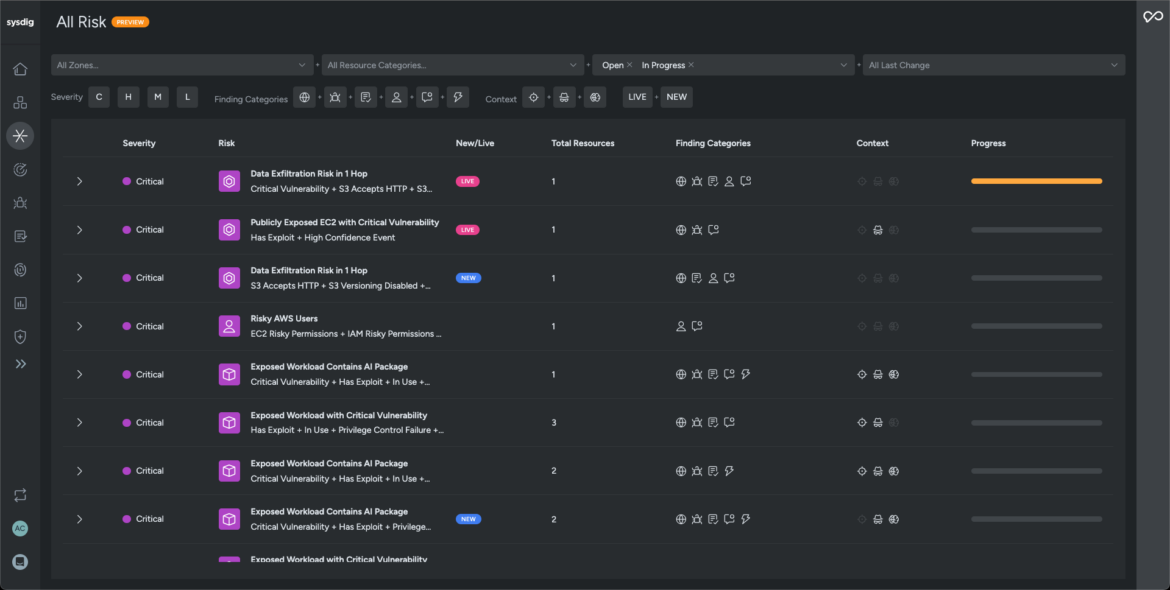
- Sysdig helps visualize and understand potential risks across compute, identity, Kubernetes, and storage resources, correlate those risks with real-time events, and pinpoint critical paths that malicious actors might take to breach their systems. These risks are periodically reevaluated and re-prioritized based on the findings in your infrastructure.
- Sysdig customers identify and mitigate advanced threats across cloud environments by integrating real-time threat detection and customizable Falco rules, and leveraging machine learning policies for anomaly detection.
Recently launched cloud detection and response (CDR) features, like AWS Behavioral Analytics, Attack Chain Visualization, Cloud Identity Insights, and Sysdig Sage™, simplify security workflows by automating the prioritization of events, contextualizing risks, and suggesting actionable remediation steps.
Example scenario
Compromised container detection
Scenario: A containerized application exhibits unusual process activity, spawning a shell in a privileged mode and initiating an external network connection.
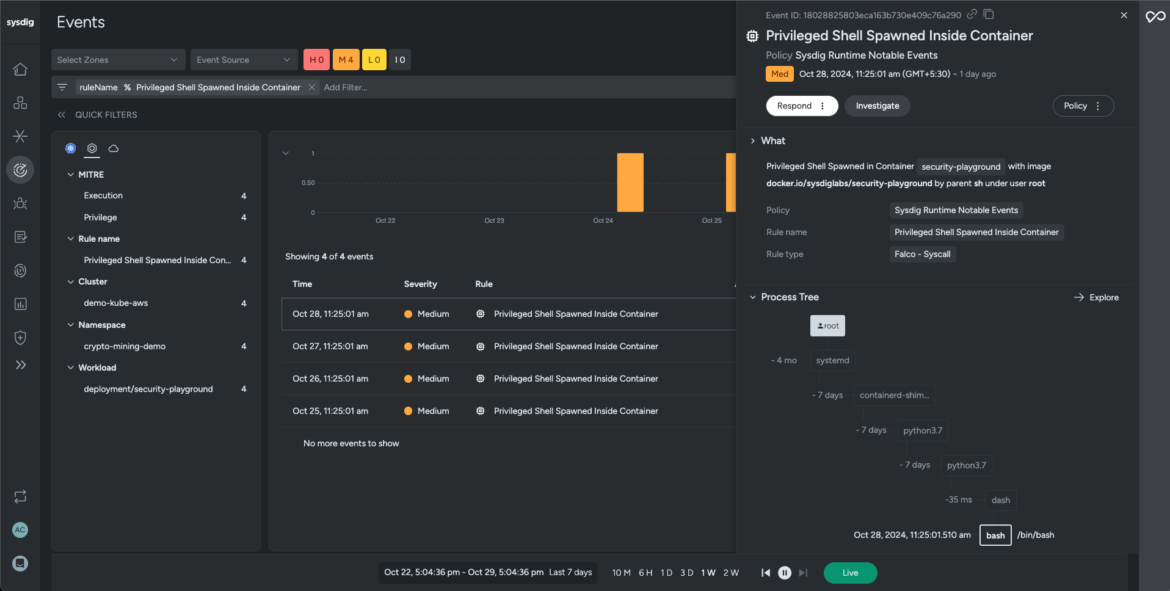
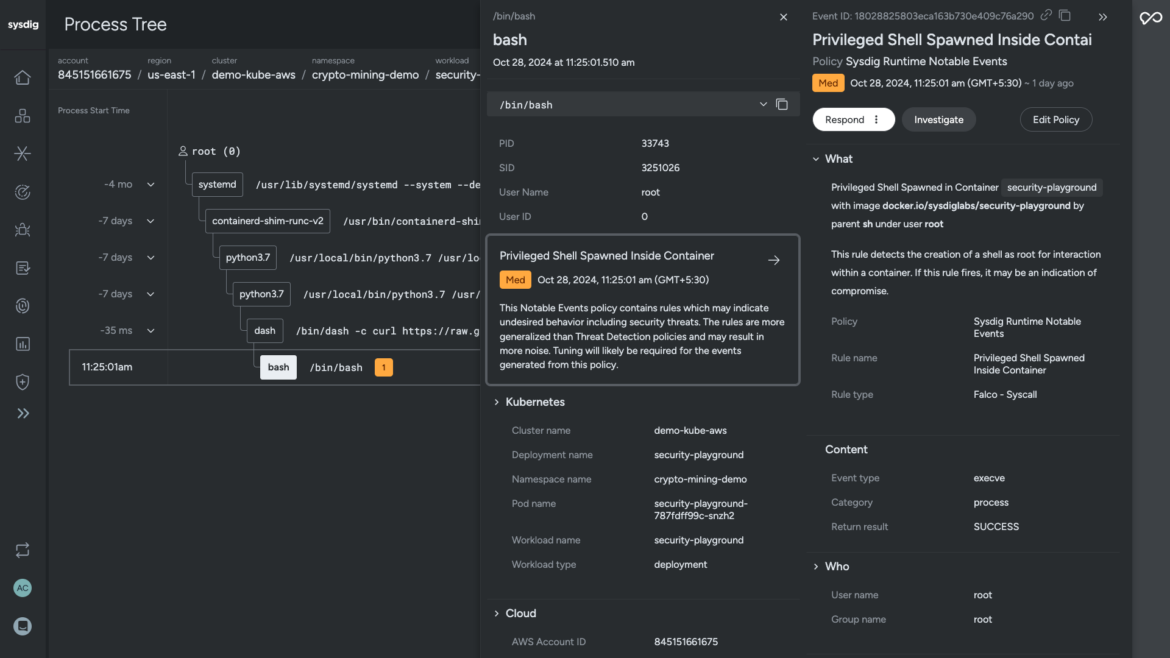
Sysdig’s Falco rule detects the shell spawned as root in the container (workload domain). The process tree traces out the timeline of executed command lines captured by the agent at runtime. It illustrates the kill chain from user to process, including process lineage, container and host information, malicious user details, and impact.
Sysdig provides a graphical overview of the attack path. It correlates and consolidates data from multiple sources — including posture misconfigurations, existing vulnerabilities, launched processes, and activity audits — to evaluate the impact of the ongoing threat. At a glance, you’ll gain critical understanding of the event’s context, such as:
- What was the root cause of the event?
- What other systems has the threat actor accessed that may be at risk?
- What processes and commands were run on the impacted workloads?
- What vulnerabilities or misconfigured permissions are in use?
- What permissions and identities were elevated?
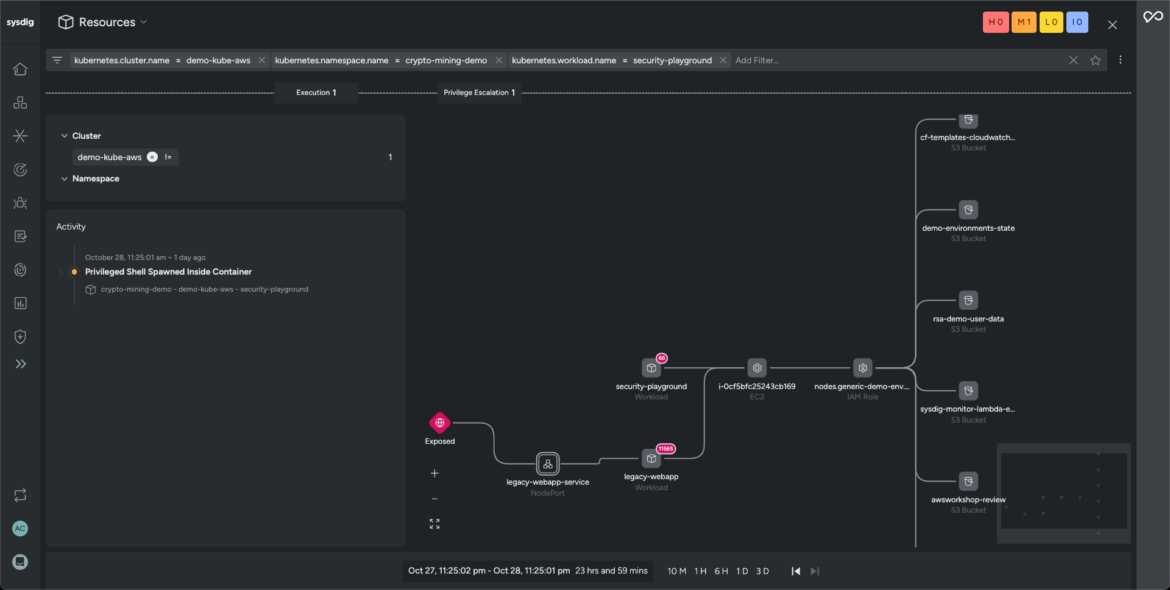
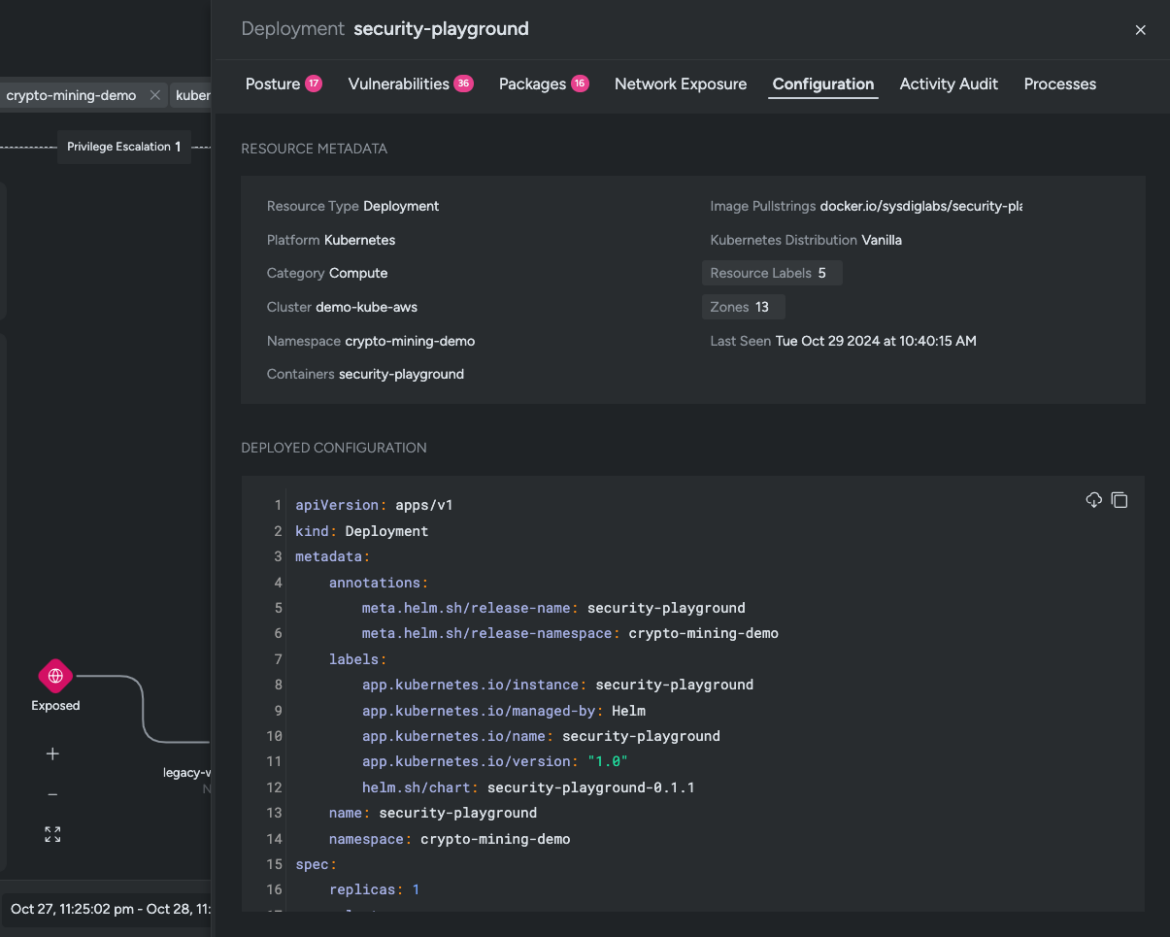
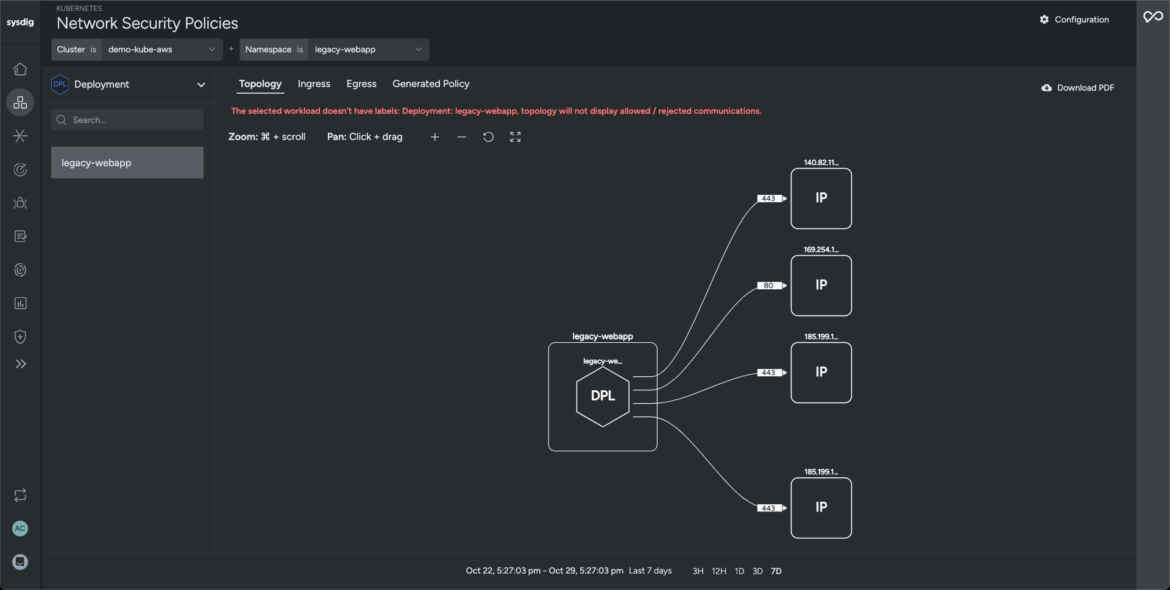
The attack chain uncovers an additional workload within our cluster exposed to the network. The network topology reveals several outbound connections to unrecognized IPs (network domain). Sysdig generates an optimized policy to stop adversaries from exfiltrating sensitive data from our network.
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: generated-network-policy
namespace: legacy-webapp
spec:
ingress: []
egress:
- to:
- namespaceSelector: {}
ports:
- port: 53
protocol: UDP
policyTypes:
- Ingress
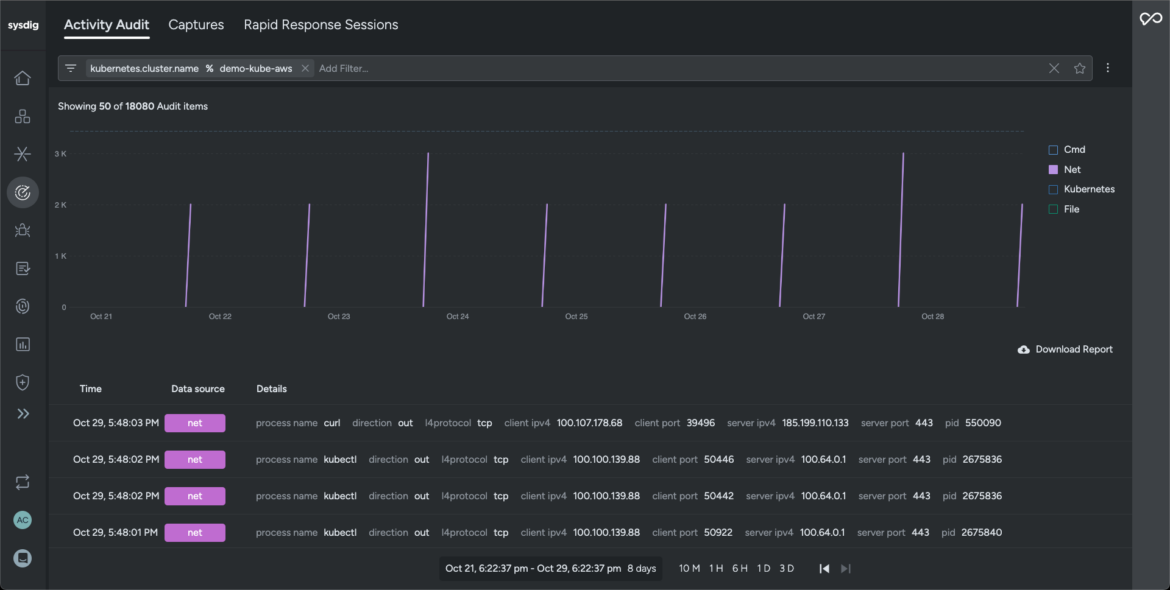
- EgressCode language: Perl (perl)Sysdig captures an audit trail in our Kubernetes cluster that pinpoints the detected anomaly and isolates all commands and network activity generated over the chosen time period. It helps security teams investigate logs long after the impacted workload is terminated, thereby adhering to compliance standards and governance frameworks (compliance domain).
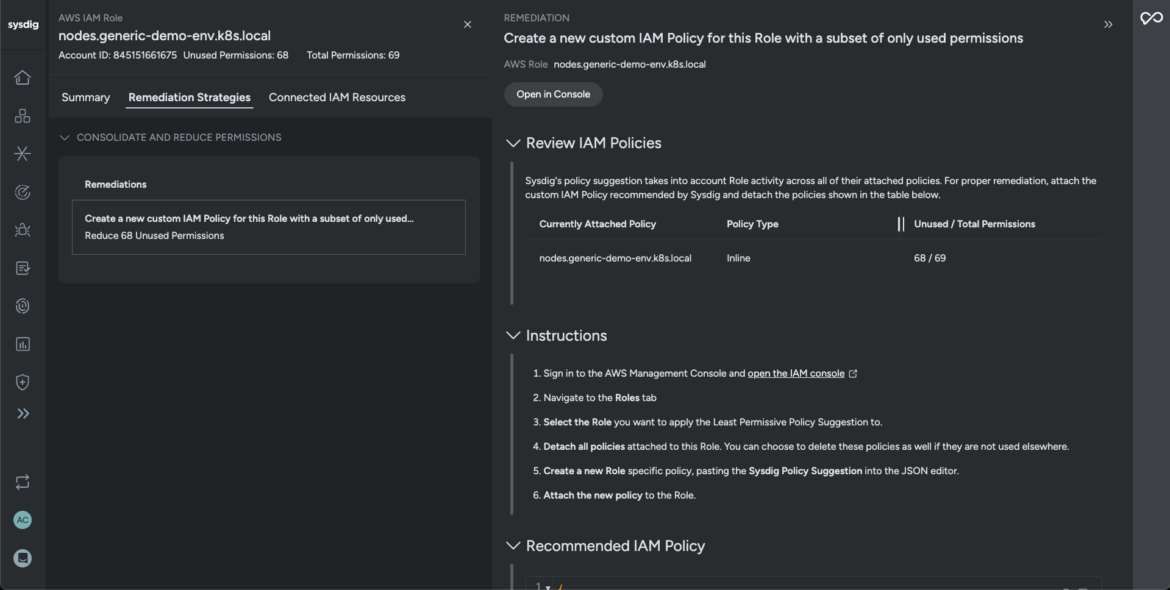
The unified platform correlates workload and network data to reveal the affected IAM resources (identity domain) and cloud accounts. Sysdig’s Identity Insights view expands the investigation to discover whether our adversary compromised any legitimate user accounts to execute itstheir objectives.
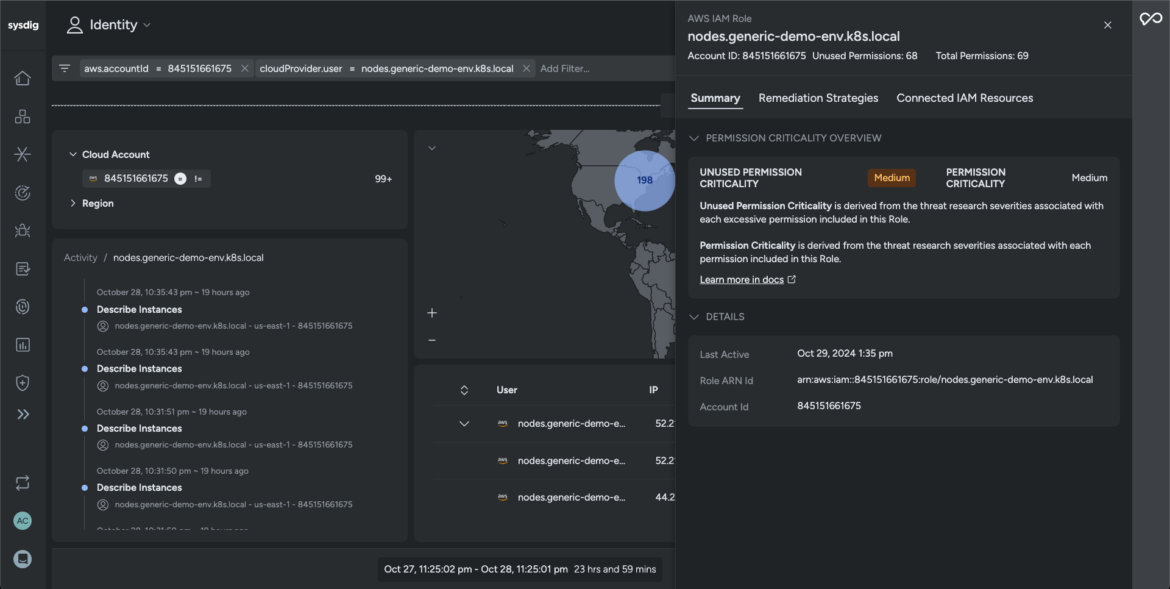
Sysdig correlates a timeline of events and brings forth all the responsible factors that allowed the adversaries access to your network. It monitors active permissions and recommends optimized configurations to reduce privileges and stop the adversary from exploiting the user account.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:describeinstances"
],
"Resource": [
"*"
]
}
]
}Code language: Perl (perl)This multi-domain correlation strategy, paired with actionable insights and efficient incident response, enables Sysdig to provide a robust defense so our customers can achieve the 555 benchmark in cloud security.
Secure Your Cloud in Minutes – Your Checklist for Meeting the 555 Benchmark
Measure how fast your security team can counter attackers with Sysdig’s 555 Benchmark for Cloud Detection and Response.


