
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Recently, Sysdig published a blog post about the ways businesses can harden their LLM-based AI applications using the OWASP Top 10 for Large Language Models. So why are we writing about MITRE ATLAS, and how is this any different from the OWASP Top 10 for LLMs?
The well-known MITRE ATT&CK project is a globally-accessible knowledge base of adversarial tactics, techniques, and procedures (TTPs) based on real-world cybersecurity observations. ATLAS is one of the many matrices managed by the team at MITRE. ATLAS is actually an acronym which stands for Adversarial Threat Landscape for Artificial-Intelligence Systems. Like MITRE ATT&CK, this is a globally accessible, living knowledge base of adversarial TTPs specific to Al-enabled systems, again, based on real-world attack observations and realistic demonstrations from Al red teaming and security group activity.
How does this differ from OWASP Top 10 for LLMs
Sysdig's Learn Cloud Native page states that the OWASP Top 10 project is designed as "a prioritized list of the most common threats that should be addressed by developers, data scientists, and security experts who have now been tasked with designing and building applications and plugins which leverage LLM-based AI technologies." This is great when enforcing best practices from the beginning of application development to improve security posture and ultimately reduce the blast radius associated with insecure AI web applications.
Though understanding the various real-world adversary behaviors in MITRE ATLAS can also aid in mitigation pathways, it is most often used to enable post-incident threat assessments and other internal red teaming activities — context the OWASP Top 10 project doesn't include. For example, as part of your threat detection and response strategy, you can create Falco rules in Sysdig for "unsecured credentials." According to the MITRE ATLAS project, the ATLAS Technique ID AML.T0055 is matched with the existing MITRE ATT&CK Reference ID T1552.
- rule: Find AWS Credentials
desc: Detects attempts to search for private keys or passwords using the grep or find command.
condition: >
spawned_process
and ((grep_commands and private_aws_credentials) or
(proc.name = "find" and proc.args endswith ".aws/credentials"))
output: Detected AWS credentials search activity (proc_pcmdline=%proc.pcmdline)
priority: WARNING
tags: [maturity_stable, mitre_credential_access, unsecured_credentials, T1552, AML.T0055]ATLAS Matrix
Like other familiar ATT&CK matrices, the ATLAS matrix shows the progression of the attack kill chain from left to right. Usually starting with Reconnaissance (environmental discovery) and ending with Exfiltration (stealing of sensitive PII data) from the organization. Since AI workloads differ from traditional web applications, there are new Tactic columns such as ML Model Access and ML Attack Staging which don't apply to other ATT&CK matrices.
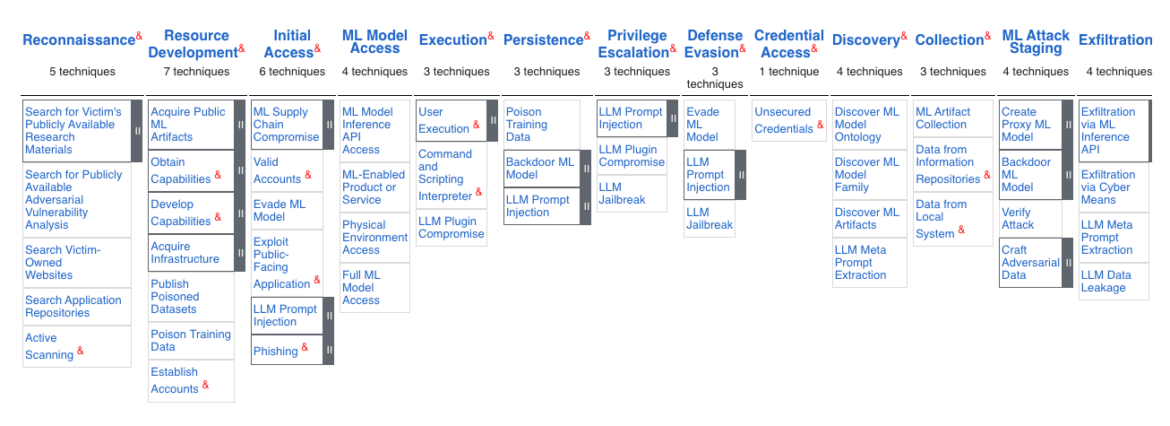
Businesses can view the ATLAS matrix highlighted alongside the relevant Enterprise ATT&CK techniques via the ATLAS Navigator. The ATLAS Navigator can help organizations better scope their existing Linux or Windows runtime detection rules around the uniquely-scoped context of AI workload threats. Also, by aligning existing detection rules with a popular open-source project like MITRE, security teams can better improve threat mitigation with community-contributed insights, while also removing the bias associated with unique findings from proprietary software solutions.
Conclusion
The Sysdig Threat Research Team is constantly updating the managed Falco Feeds with rule tags to ensure the cloud, Kubernetes and AI workloads are compliant with evolving regulatory requirements. Falco and the Sysdig agent allow users to add custom labels to address compliance standards that might be unique to your organization, while also providing the option of receiving automated rule updates with tags that apply to tactics and techniques across the entire MITRE ATT&CK framework as well as security compliance controls such as PCI DSS, NIST, GDPR, DORA, FedRAMP and more.


