
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Sysdig continues to evolve this May with major advancements in cloud exposure analysis, broader serverless coverage, simplified identity insights, and developer-focused integrations. Let’s dive into the highlights.
Advanced Network Exposure
Graph-powered, multi-path, and continuously expanding
Why it matters:
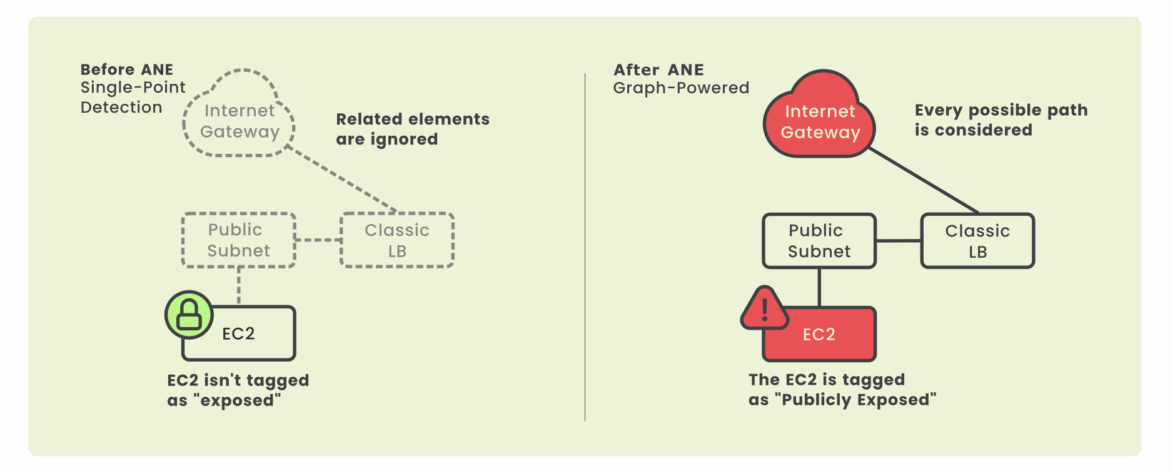
Imagine you have an EC2 instance in AWS. Previously, our system might have primarily checked if its Security Group directly allowed traffic from the internet (0.0.0.0/0). With Advanced Network Exposure (ANE), we look much deeper.
ANE uses an intelligent ‘map’ (a graph) of all your interconnected cloud resources. So, for that EC2 instance, ANE might find one potential exposure path directly via its Security Group settings and an Internet Gateway. But it could also discover another: perhaps the EC2 is behind a Classic Load Balancer, which itself is configured to be public via its own Security Group, in a public Subnet with a Route Table pointing to an Internet Gateway. ANE uncovers all such configured pathways.
This is powerful because it gives you a complete picture of potential exposures based purely on how your cloud resources are configured. Then, if you have Validated Exposure enabled, we can actually test these identified paths (like a cautious ‘ping’) to confirm if they are truly reachable from the public internet. This means more accurate, comprehensive risk assessment, adapting as we continuously add support for more resources like NLBs, ALBs, and Kubernetes services.
Customer impact:
Security and cloud operations teams gain deeper visibility and higher confidence in their risk posture. ANE eliminates blind spots by uncovering every valid path to exposed assets, dynamically adapting to changes in infrastructure. It runs by default, requires no manual configuration, and evolves over time, delivering a future-ready foundation for exposure management.
Serverless Agent GA for Google Cloud Run & Azure Container Apps
Why it matters:
Sysdig’s Serverless Agent now fully supports Google Cloud Run and Azure Container Apps. That means the newest serverless services get the same strong security checks as the rest of your cloud, ready to use out of the box. It also sets the stage to retire the older Orchestrator Agent before July 2025, so teams can move forward on a single, modern solution.
Customer impact:
Security and platform teams can protect workloads that used to be hard to see, without extra effort or new tools to learn. Everything works with the policies and alerts you already have, so you gain wider coverage, simpler operations, and greater peace of mind in one quick upgrade.
Azure Container Apps deployment guide
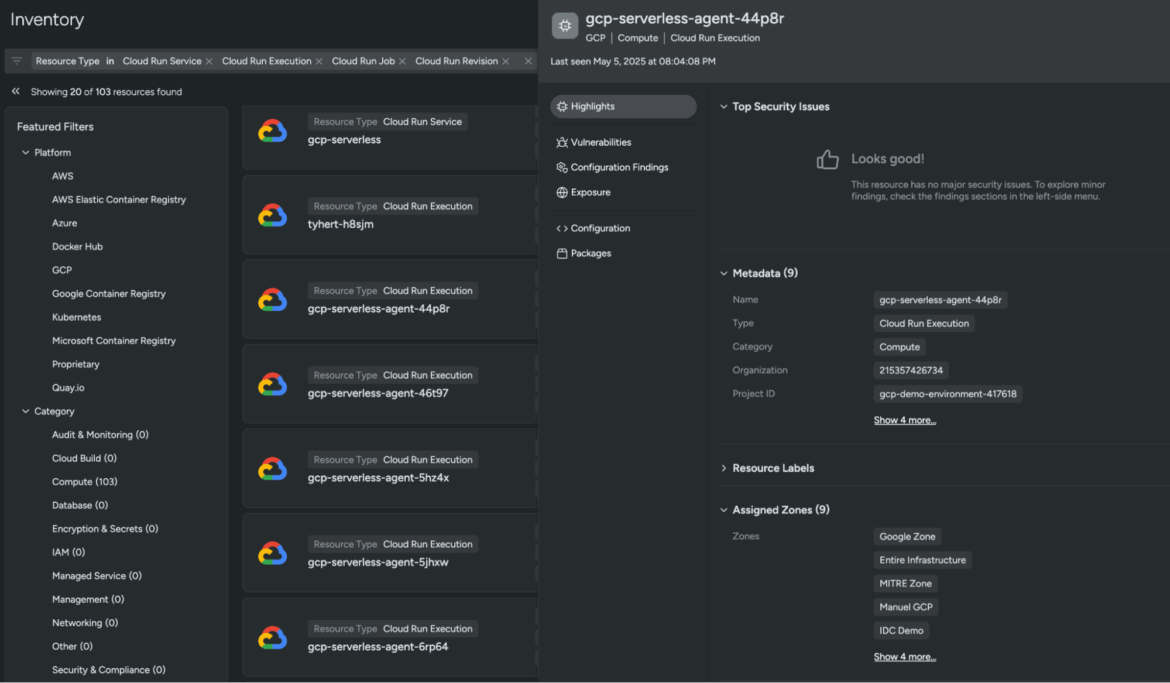
Foundational CIEM capabilities now standard with CSPM
Why it matters:
Core identity security (CIEM) now ships automatically with Sysdig’s cloud‑posture (CSPM) checks. For example, where previously you might have needed to set up complex log ingestion from services like AWS CloudTrail or Azure Monitor just to identify basic risks (like an admin account lacking MFA or a service principal with overly broad permissions), now there’s no log plumbing and no extra setup. Just switch on CSPM, and you instantly see who can do what in AWS, Azure, and GCP, immediately spotting those same critical issues (like accounts without MFA or roles with excessive permissions) without that upfront delay. By removing the log‑ingestion hurdle, Sysdig makes identity risk analysis faster and easier for everyone, from first‑time trials to full‑scale deployments.
Customer impact:
Security teams get an immediate snapshot of risky permissions and misconfigured roles (even in small PoCs) without extra costs or delays. Faster onboarding means quicker evaluations, broader coverage, and a clearer path to least‑privilege access, all delivered through the same console you already use for posture management.
Learn more in the release notes and documentation.
Honorable mention: Cortex XSOAR
Why it matters:
Customers using the Cortex XSOAR platform will have a new official Sysdig integration in the marketplace that will provide interaction with our APIs. The XSOAR marketplace will soon feature a new, officially supported Sysdig integration. This integration will empower XSOAR platform users with seamless interaction with Sysdig’s suite of APIs. This will enable a wide range of security and visibility use cases (the first one, response actions), allowing users to leverage Sysdig’s cloud-native security insights directly within their existing XSOAR workflows.
Customer impact:
XSOAR users managing security events can now leverage a suite of commands to initiate asynchronous incident response actions on agents. These actions include the ability to terminate, pause, or stop containers, quarantine files, and create and download forensic captures.
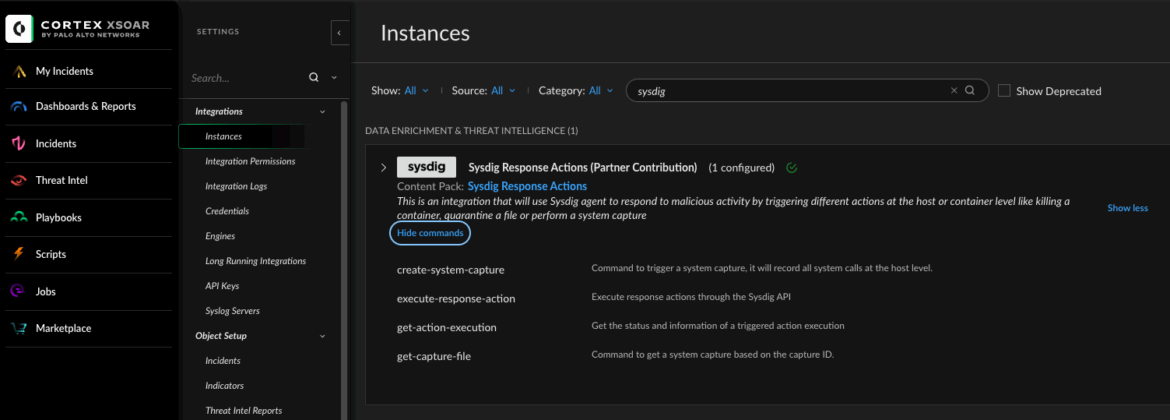
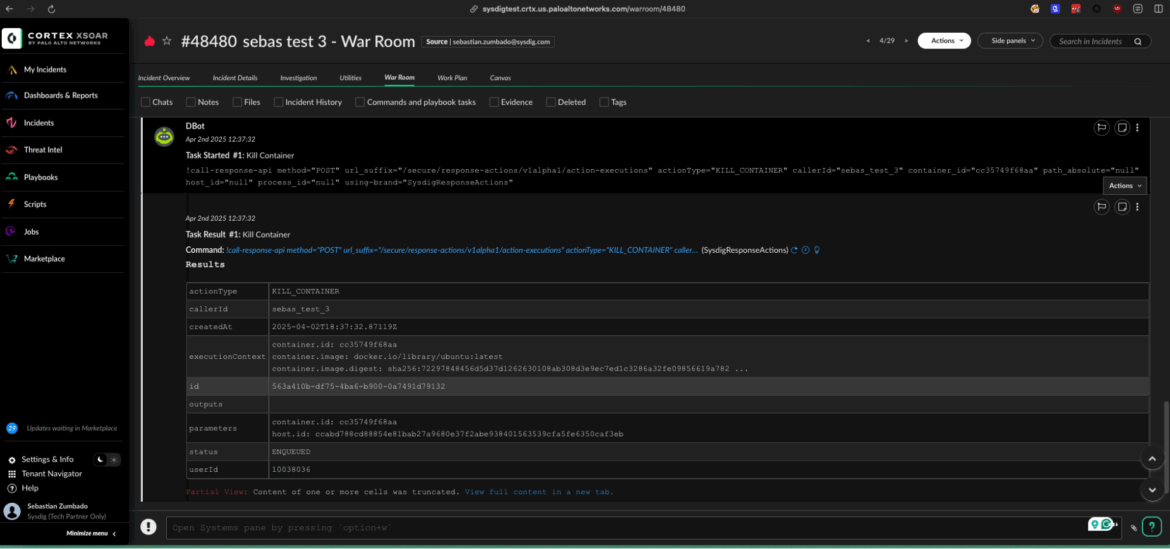
Kill a container Response Action (could be any of the supported response actions: kill, pause, stop, file quarantine)
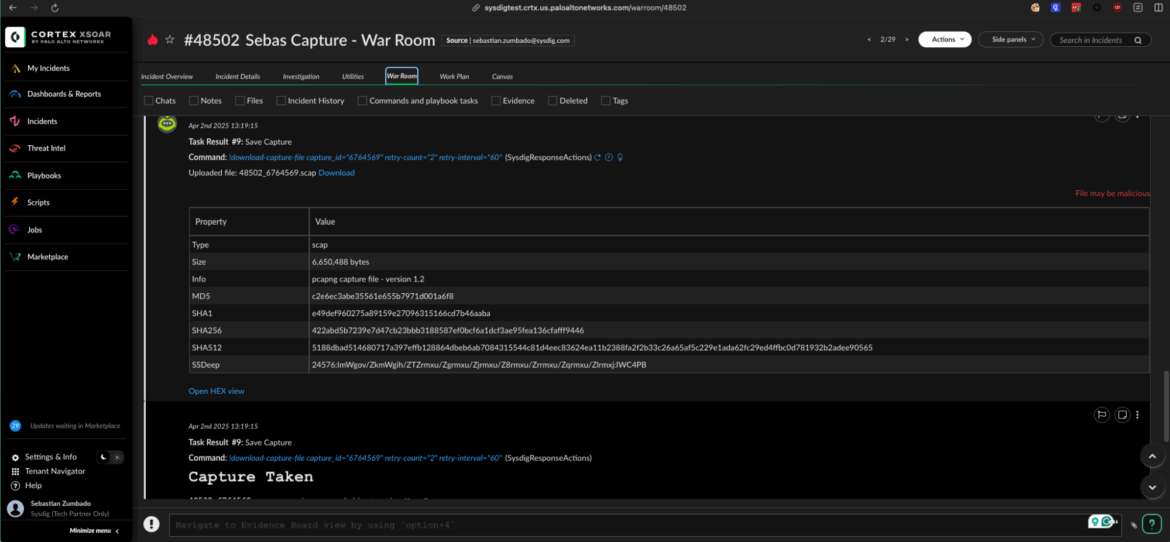
The response actions are used under the hood through the API.
Learn more:
• Full release notes – Secure
• Secure install guide
• Monitor install guide


