AWS CloudFront Security
AWS CloudFront is a powerful Content Delivery Network (CDN) that provides fast and secure delivery of static and dynamic web content to end users worldwide. With features such as SSL/TLS certificates, Origin Access Identity, Origin Shield, and Web Application Firewall integration, CloudFront is designed to keep your data and content secure while delivering it to your customers at lightning speed.
Whether you’re delivering sensitive financial data, personal information, or mission-critical software updates, AWS CloudFront provides a secure and scalable platform for delivering your content. In this article, we will explore the security features and best practices that make AWS CloudFront a top choice for businesses and organizations looking to protect their data in the cloud. Get ready to discover how CloudFront can help secure your content and ensure the safe and reliable delivery of your data to end users.
What Is AWS CloudFront?
Amazon CloudFront is a Content delivery network (CDN) service offered by Amazon Web Services (AWS). It is used to distribute content (such as web pages, images, videos, and other files) to end users with low latency and high transfer speeds.
CloudFront works by caching content at edge locations around the world, so when a user requests a piece of content, it is delivered from the nearest edge location instead of the origin server. This reduces latency and improves the overall performance and user experience.
CloudFront is a powerful and versatile web service that can be applied to various use cases, including content delivery, media streaming, security, and load balancing. It is commonly used to deliver static content, such as images, videos, and style sheets, as well as dynamic content like APIs and web applications. It can also be used to stream videos and other media content with high-quality, low-latency video delivery as well as to secure content delivery.
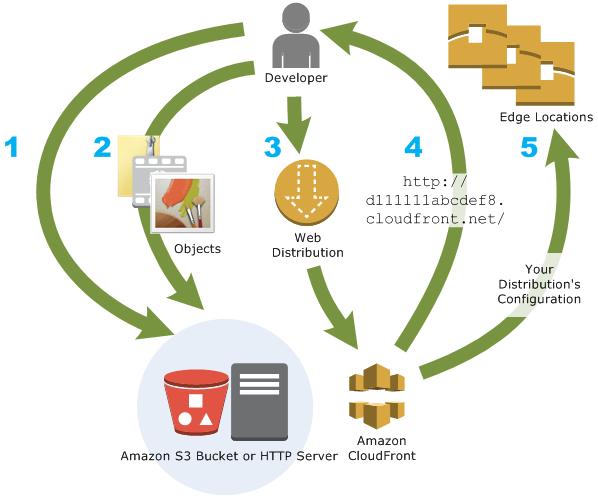
Key CloudFront Security features
AWS CloudFront is a game changer in content delivery and data protection. With its advanced security features, CloudFront provides an unparalleled level of protection for your online content and data. From SSL/TLS certificates to Origin Access Identity and Origin Shield, CloudFront offers a comprehensive security framework that protects your data from known and unknown threats.
Some key security features of AWS CloudFront include:
- SSL/TLS encryption: CloudFront supports HTTPS connections to securely transmit data between a user’s browser and the edge location.
- Origin protection: CloudFront allows you to restrict access to the origin server to only CloudFront, which helps protect the origin from unauthorized access.
- IP allow/block lists: CloudFront allows you to configure allow and block lists based on IP address to control access to your content.
- Field-level encryption: CloudFront allows you to encrypt specific fields in HTTP cookies and query strings to help protect sensitive data.
- DDoS protection: CloudFront automatically mitigates DDoS attacks at the network and application layers.
AWS CloudFront security comprises two key aspects: network security and configuration security. Let’s take a closer look at each of these.
AWS CloudFront Network Security
When you’re using AWS CloudFront, your data is traveling through a global network of Points of Presence (PoP). These are physical data centers that are used to store and serve content from the CloudFront network. These PoPs are connected to the internet, so your data can be delivered quickly to your customers no matter where they are in the world. But with this global reach comes a greater risk of security threats. That’s why it’s important to understand the ways AWS CloudFront protects your data.
AWS CloudFront applies network security in the following ways:
DDoS Protection and Network Edge Security
AWS CloudFront automatically mitigates DDoS (Distributed Denial of Service) attacks at the network and application layers. This is done by using a combination of techniques such as traffic filtering, traffic throttling, and traffic redirection. CloudFront also uses Amazon’s global network infrastructure to provide an additional layer of protection at the network edge.
Integration with AWS WAF for Application-Level Protection
CloudFront can be integrated with AWS WAF (Web Application Firewall) for application-level protection. AWS WAF allows you to create rules that check incoming HTTP/HTTPS traffic for common web exploits, such as SQL injection and cross-site scripting. This provides an additional layer of protection to your content beyond the network-level protection provided by CloudFront.
IP Address Allowlisting and Blocklisting
CloudFront allows you to configure allow and block lists based on IP address to control access to your content. You can use this feature to block or allow traffic from specific IP addresses or ranges. This can be useful for controlling access to your content from specific locations or for preventing unwanted traffic from reaching your origin.
Configuring CloudFront Security settings
There are several ways of configuring AWS CloudFront security settings, including the following:
Setting up an SSL/TLS Certificate for HTTPS Connections
To set up an SSL/TLS certificate for HTTPS connections in CloudFront, you need to follow these steps:
- Obtain an SSL/TLS certificate from a trusted certificate authority (CA) or use AWS Certificate Manager (ACM) to create one.
- In the CloudFront console, create or update a distribution and choose to use the certificate for the distribution.
- Update the DNS settings for your domain to point to the CloudFront distribution.
- Test the HTTPS connection to your domain.
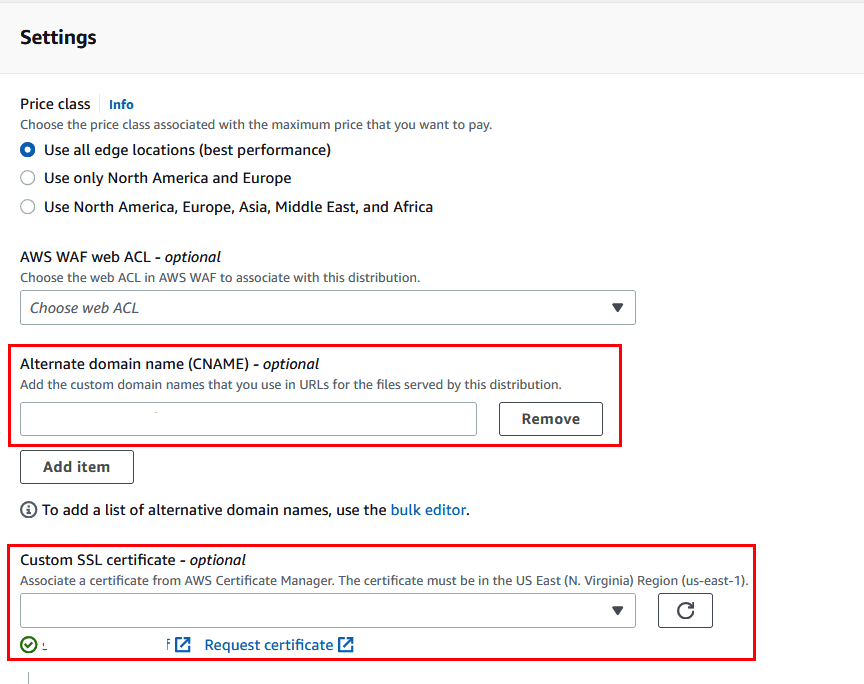
Configuring CloudFront origins
In the AWS CloudFront console, go to the “Origins” section of your distribution. Then follow the steps below:
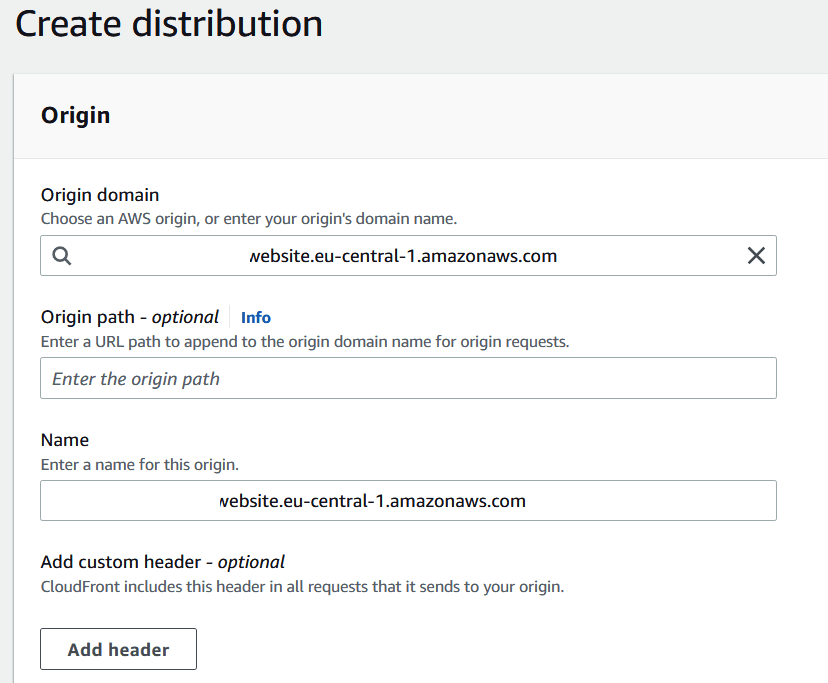
- Click on the origin that you want to configure.
- Scroll down to the “Restrict Bucket Access” section and click “Edit.”
- Enable the option for “Restrict Bucket Access” and choose to either allow or block access based on IP address.
- Add the IP addresses or ranges that you want to allow or block.
- Save the changes.
Enabling DDoS Protection and Integrating with AWS Shield
In the CloudFront console, go to the “Behaviors” section of your distribution. Then follow the steps below:
- Click on the behavior that you want to configure.
- Scroll down to the “Advanced” section and choose “Edit.”
- Under “DDoS protection,” select “Enabled.”
- Under “AWS Shield Advanced,” select “Enabled.”
- Save the changes.
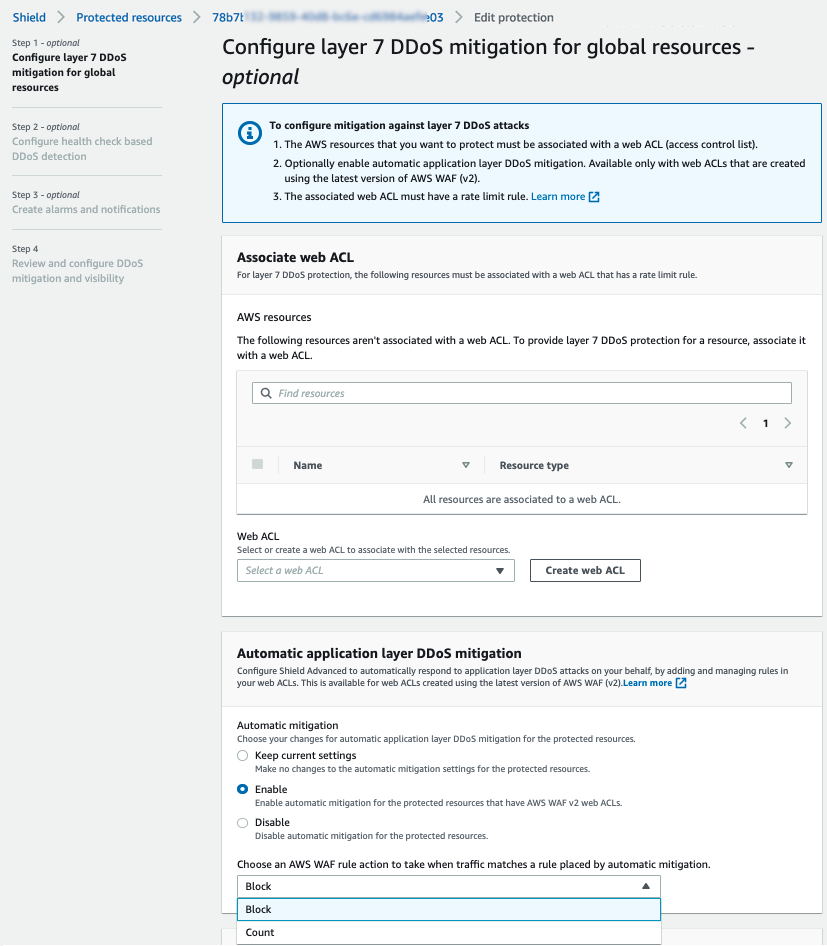
Setting Up an AWS WAF Web ACL
To setting up an AWS WAF web ACL to protect against common web attack, first go to the AWS WAF console and create a new web ACL. Then follow the steps below:
- Add rules to the web ACL to block common web attacks, such as SQL injection and cross-site scripting.
- In the CloudFront console, go to the “Behaviors” section of your distribution.
- Click on the behavior that you want to configure.
- Scroll down to the “Advanced” section and choose “Edit.”
- Under “AWS WAF,” select “Enabled.”
- Choose the web ACL you created and save the changes.
In order to set up an AWS WAF Web ACL to protect against common web attacks, you need to create the Web ACL in the AWS WAF console and specify the Web ACL parameters. You can then add rules to the Web ACL, such as rules that block requests from known malicious IP addresses or rules that block requests containing SQL injection strings. You can then associate the Web ACL with your CloudFront distribution.
For more information on configuring an AWS WAF Web ACL, please see the AWS documentation here and read more on how AWS WAF works with Amazon CloudFront features.
CloudFront Security Best Practices
To ensure the security of your data and protect your distribution from potential security threats, it’s important to follow best practices when using CloudFront. This includes encrypting data over CloudFront, implementing access controls to restrict access, and monitoring CloudFront logs and alerts for potential security issues. By following these security best practices, you can safeguard your data and minimize the risk of security breaches.
Encrypt Data Over CloudFront
One of the best practices for securing data over CloudFront is to encrypt sensitive data before it leaves the origin. This can be done by using HTTPS to encrypt data in transit, and by encrypting data at rest using server-side encryption. Additionally, CloudFront supports the use of custom SSL/TLS certificates, which allows you to use your certificate for encrypting data over CloudFront.
Access Controls to Restrict Access to Your Distribution
Another best practice is to use access controls to restrict access to your CloudFront distribution. This can be done by using CloudFront’s IP allow/block list feature, Origin Access Identity (OAI), and also using CloudFront signed URLs or signed cookies to limit access to your content.
Monitoring CloudFront Logs and Alerts for Potential Security Issues
Regularly monitoring CloudFront logs and setting up alerts for potential security issues can help identify and respond to any security breaches or vulnerabilities quickly. CloudFront logs contain information about requests made to your distribution and can be used to identify patterns of suspicious activity. CloudFront also provides metrics and alarms that can be used to monitor the security and performance of your distribution.
Troubleshooting CloudFront Security Issues
When using Amazon CloudFront, it’s important to be aware of potential security issues and to have a plan in place for troubleshooting and resolving them. Error messages related to such issues can be found in the CloudFront logs and alerts. Some of the common issues related to CloudFront security include:
- SSL/TLS certificate issues: This includes errors such as “NET::ERR_CERT_AUTHORITY_INVALID” or “Your connection is not private” when serving content over HTTPS on CloudFront. These errors are caused by an expired certificate or an incorrect domain name.
- Misconfigured security settings: Incorrect security settings can lead to unauthorized access or “Access Denied” errors on CloudFront.
- Malicious traffic: CloudFront can be targeted by malicious traffic, such as DDoS attacks or SQL injection attacks. These attacks can result in errors such as “Service Unavailable” or “Bad Request.”
- Incorrect permissions and unauthorized access: Unauthorized access to a CloudFront distribution can result in “Access Denied” or “Forbidden” errors and potentially lead to the theft of sensitive data or the manipulation of content.
To address and resolve security issues in CloudFront, you should follow these best practices:
- Verify the configuration of your SSL/TLS certificate and ensure that it is correctly installed and configured on your origin and in CloudFront.
- Monitor CloudFront logs and metrics for any signs of suspicious activity or potential security breaches.
- If a security issue is detected, take swift action to isolate and solve the problem. Then put extra security measures in place to stop it from happening again.
- Ensure that CloudFront and any associated services are always running the latest security patches and updates.
Additionally, regularly updating your software and systems as well as keeping your teams informed about the latest security threats can help prevent security issues from arising in the first place.
What’s next in CloudFront Security?
For more information on AWS CloudFront security and to stay up to date with the latest security best practices, consider the following resources:
- AWS documentation on CloudFront security
- AWS CloudFront security blog
- AWS CloudFront security best practices
- AWS Security Center
- AWS security and compliance whitepapers
- AWS security user groups

