What is Threat Hunting?
There are two ways to handle cybersecurity threats. One is to sit back, wait for threat actors to start exploiting vulnerabilities in your systems, and then take action to mitigate the attack.
The other, better approach is to perform threat hunting. Threat hunting means proactively searching for threats before they create serious risks for your business.
It’s not always feasible to detect every threat proactively using threat hunting. Still, threat hunting should be a pillar of your broader cybersecurity strategy because it helps you to get ahead of cybersecurity risks and minimize their impact on your systems and operations.
Keep reading for a deep dive into what threat hunting means, how it works, and which threat hunting techniques deliver the greatest benefit.
What Is Threat Hunting?
Threat hunting is a proactive security strategy used to detect and investigate threats that may have evaded traditional detection mechanisms. It involves the use of manual and automated techniques to identify malicious activity, uncover threats, and detect malicious actors. It is the process of searching through network and system data to identify malicious actors and malicious activity that may have evaded traditional security defenses.
Threat Hunting and the Threat Lifecycle
To understand what threat hunting means in practice, it’s useful to think about what’s known as the threat lifecycle.
Typically, threat actors don’t launch major breaches overnight. Instead, they follow a process – the threat lifecycle – that involves multiple steps:
- Reconnaissance of your systems to find weaknesses or vulnerabilities that could be exploited.
- The initial compromise of a vulnerable system in order to create a backdoor or beachhead into your IT estate from which threat actors can continue to probe your resources and expand their operations.
- The escalation of the attack to affect other resources beyond the one that allowed the initial compromise.
- The identification of a key target (or targets) to breach, such as sensitive data.
- The execution of the major breach against the key target.
In many cases, businesses don’t detect threats until step 3 or later within the threat lifecycle – and according to IBM, it takes about nine months, on average, for detection to occur. That’s because reconnaissance activities and small-scale initial compromises by threat actors tend to go unidentified.
However, when you actively hunt for threats, you increase your chances of detecting threats as early as possible in the threat lifecycle. By extension, you can remediate threats sooner, before they cause any significant breach or compromise.
Threat Hunting Example
As an example of a common threat hunting scenario, consider a situation where attackers are using portscanning software to check which ports are open on public-facing servers that you operate. The portscanners can also detect the services running on open ports and the type of operating system running on each server.
Portscans don’t involve an active breach of resources; they simply entail attempts to connect to servers using different ports and protocols. For that reason, port scans are not likely to trigger major alerts from your cybersecurity tools, which will instead focus on active breaches. This means that if you don’t actively search for the portscanning activity, you’re not likely to detect it until the point where the attackers have already found a vulnerability that they can exploit to gain access to a system.
But if you employ threat hunting, you could detect the portscans by closely analyzing network logs, or possibly by using canary tokens to detect unauthorized activity that attackers are able to undertake using the information identified through portscanning. In most cases, it’s possible to identify specific requests and packets associated with portscans, as well as the host from which the portscans originate. Using this information as part of a threat hunting technique, you could identify the portscans and the IP addresses associated with them. Then, you could block those IP addresses in order to stop the malicious activity before it leads to an active breach. You could also audit your ports and services to make sure that they don’t contain vulnerabilities, which would help to harden your network further.
Benefits of Threat Hunting
The main benefits of threat hunting include:
- The ability to detect more risks before they translate to breaches or compromises.
- Enhanced capacity to respond quickly to threats and risks.
- The ability to mitigate risks with fewer resources – since threats are usually easier to remediate when they are in the early stages, compared to when threat actors have already established a major presence within your IT estate.
Put simply, threat hunting gives you the advantage of being able to take a proactive stance toward cybersecurity threats. That beats being passive and waiting for damage to occur before you take action.
How Threat Hunting Works
To work in practice, threat hunting requires both tools that are capable of detecting threats in their early stages and techniques that surface threats – even ones that have not yet left major fingerprints inside your systems.
The threat hunting process typically involves using specialized tools and methodologies to detect and analyze anomalous activity and suspicious events. This may include reviewing endpoint logs, network traffic, and system activity for suspicious behavior. Additionally, threat hunting may involve reconnaissance and data-gathering activities such as reverse engineering malicious code, identifying indicators of compromise, and correlating events across multiple systems.
Once a threat has been identified, the hunter will work to determine the scope and impact of the threat, then develop a plan to remediate or mitigate it.
Threat Hunting Steps
The threat hunting process that we just described can be broken down into several distinct steps:
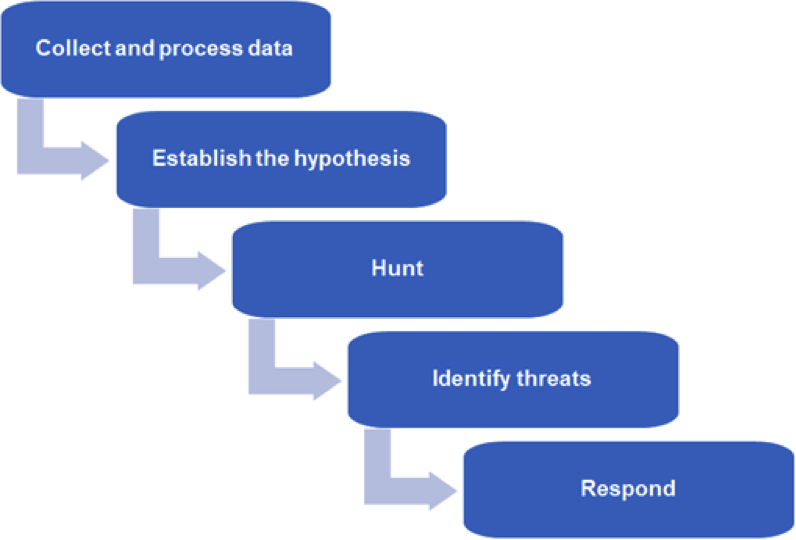
- Establish a baseline: Establish a baseline of normal activity for your networks and systems by collecting and analyzing data on network traffic and user activities.
- Identify suspicious activities: Identify suspicious activities by monitoring logs and reviewing data, then forming hypotheses about where potential threats may exist based on the data. For threat hunting purposes, it’s often necessary to look for subtle changes that may signal the earliest stages of an attack, such as connection attempts from a previously unknown host or requests to connect to non-standard ports (which could reflect efforts by threat actors to find vulnerable services that they can compromise).
- Investigate the threats: After identifying potential threats, investigate them further by gathering more information and analyzing the data to understand the scope and nature of the malicious activity. For example, if you detect requests from suspicious hosts, continue to monitor those hosts’ activities to assess whether they do in fact appear malicious.
- Take action: Once you’ve established confidence that a threat exists, take action by blocking the malicious activity and/or patching vulnerable systems.
- Monitor: Monitor the network or system for any further malicious activities or vulnerabilities. This is important to ensure that your remediation actions from the previous step were successful in blocking the threat fully.
Ideally, these steps should be performed on a continuous basis, creating a loop wherein the final steps feeds back into the second step. In other words, the insights gleaned from monitoring should drive the identification of new suspicious activities, which in turn triggers investigations, remediations and more monitoring. Since threats are constantly active and always evolving, continuous threat hunting is critical for staying a step ahead of attackers.
Threat Hunting Techniques and Models
Although all threat hunting processes can be broken down into the same basic set of steps, there are multiple threat hunting techniques that you can leverage to detect threats during early stages of the threat lifecycle.
Common threat hunting models include:
- Signature-based model: This model focuses on identifying known malicious activity and activity that matches pre-defined signatures. Signatures can be created from a variety of sources, including malware analysis, network traffic analysis, and threat intelligence.
- Anomaly-based model: With this model, you focus on identifying suspicious activity that does not match baseline activity. The model can use machine learning algorithms to detect anomalies such as sudden spikes in network traffic, unusual user logins, or other activities that are outside the norm.
- Behavioral model: Under a behavioral threat hunting model, you focus on understanding malicious actors and their behaviors. It looks at the techniques, tactics, and procedures used by attackers to gain access and move laterally within systems.
- Heuristic model: The heuristic model focuses on understanding the indicators of compromise and identifying potentially malicious behavior. It uses heuristics to detect suspicious activity, such as file names, registry entries, port connections, and other indicators.
You need not limit yourself to just one of these threat hunting models. In fact, it’s wise to employ multiple threat hunting techniques at the same time, because different approaches excel at identifying different types of threats. For example, signature-based threat hunting models work well for detecting known threats that are described in vulnerability databases, while anomaly-based models are best for detecting suspicious activity that may reflect efforts by attackers to break into your systems without relying on publicly disclosed vulnerabilities.
Threat Libraries and Resources
Although the data you collect and analyze from your IT estate is the basis for detecting threats, additional resources can provide important guidance during threat hunting.
These include threat intelligence libraries, which are databases that record information about known threats. Because threat actors often use similar techniques to target different organizations, information about a threat that was discovered at one business can be useful for helping other businesses to detect similar threats against them. You can find open source threat hunting libraries on the Internet, and in some cases security vendors offer access to proprietary threat hunting data.
Playbooks are also a useful threat hunting resource. Playbooks define how to respond to different types of threats. By establishing a response plan ahead of time, you increase your ability to mitigate threats as quickly as possible.

