Container Forensics and Incident Response
Streamline container, Kubernetes, and serverless incident response, and conduct forensics even after containers are gone.

Container Forensics and Incident Response Solutions
Conduct forensics and incident response solutions for containers, Kubernetes, and serverless to understand cloud security breaches, meet compliance requirements, and recover quickly.
Container Forensics Data
Use a detailed forensics report to quickly answer the questions of “when,” “what,” “who,” and “why” for your incidents.
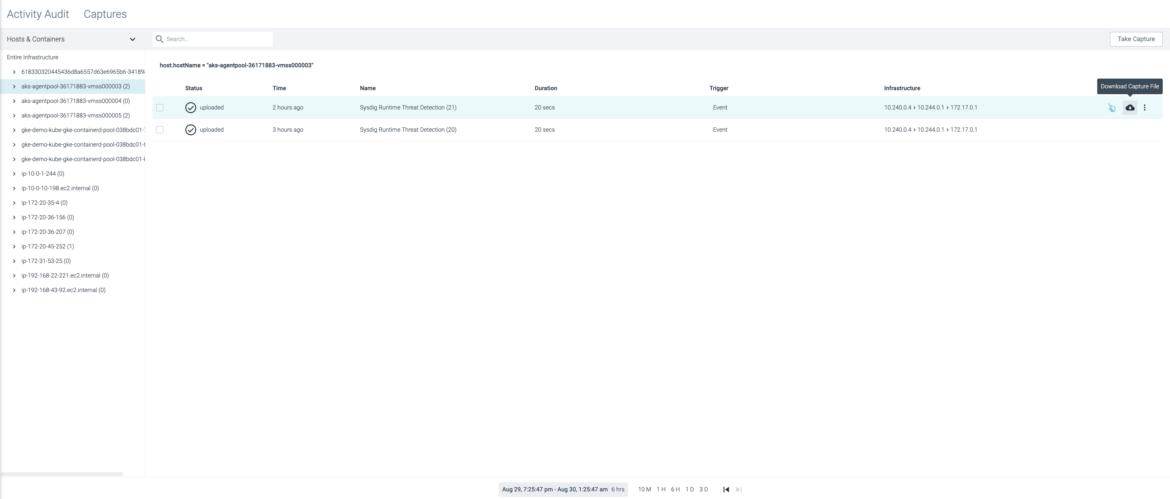
Real-Time Activity Audits
View a real-time stream of user and system activity in an event timeline to quickly learn what happened.
Post-Mortem Analysis
Recreate incidents and understand impacts by analyzing all system activity, even for long-gone containers.
"We need to be able to count on the security and integrity of containers that may be online for a few seconds, maybe a few weeks, and then disappear. With Sysdig, we have real-time visibility across the whole FIS environment. Then if something happens, we still have that data to investigate with.”
– Natnael Teferi, Lead DevSecOps Cloud Security Architect, FISContainer and Kubernetes Incident Response
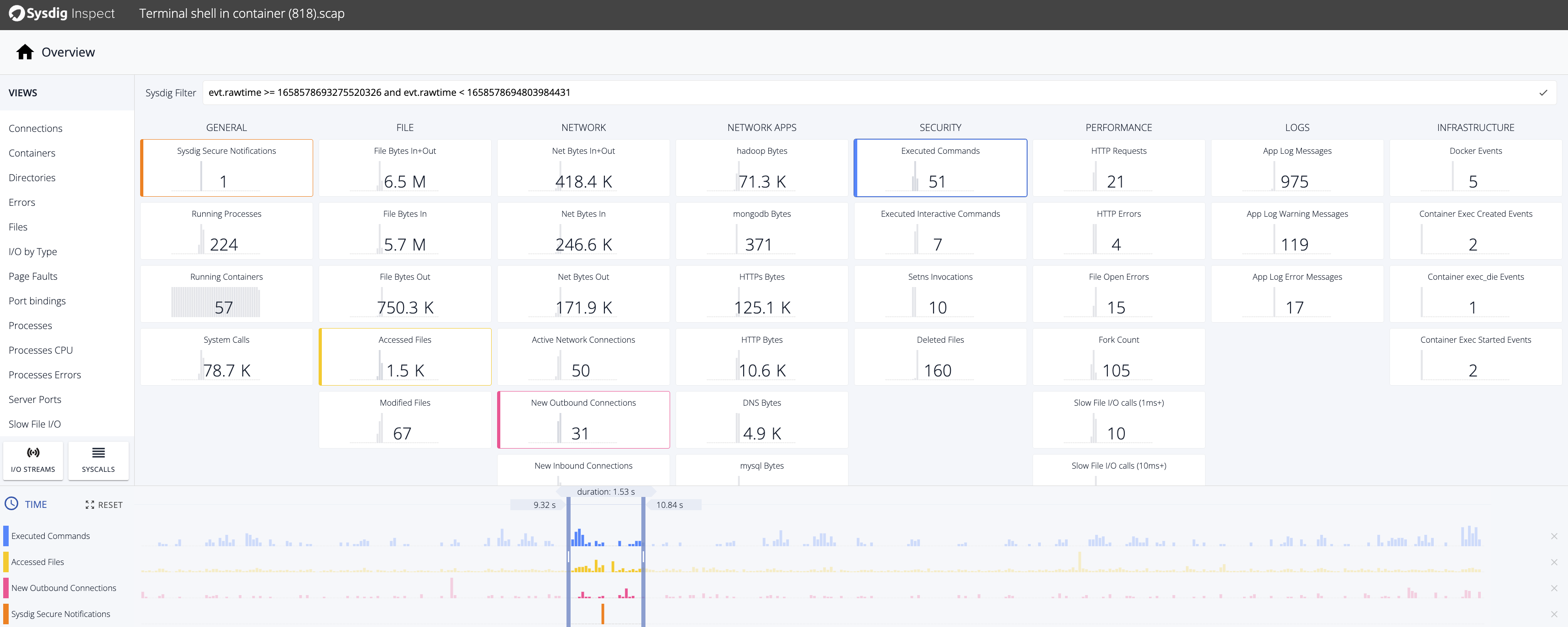
Granular Data Collection
Capture system calls as a source of truth for container forensics and incident response. Gain deep insights into process, file, and network activity before, during, and after an incident.
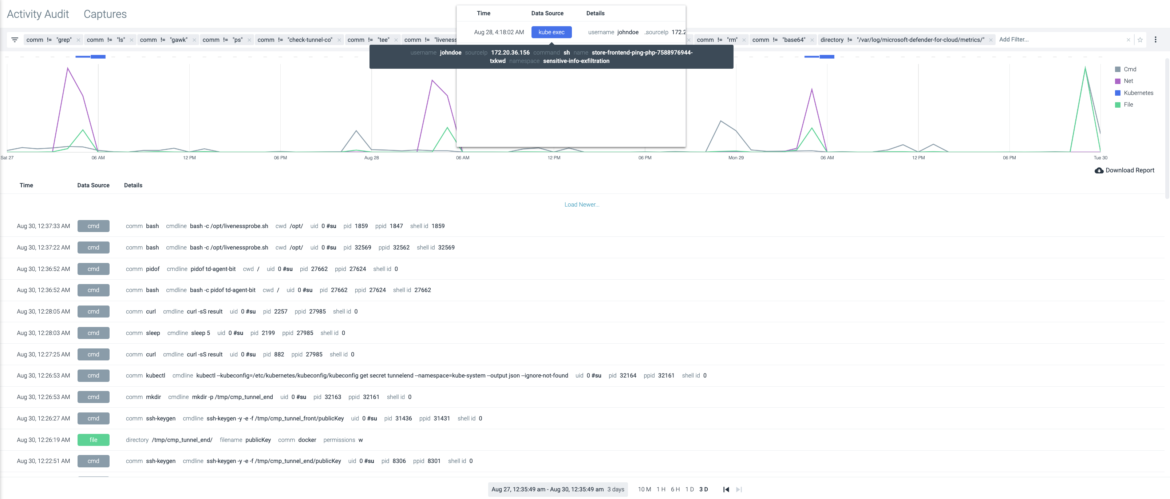
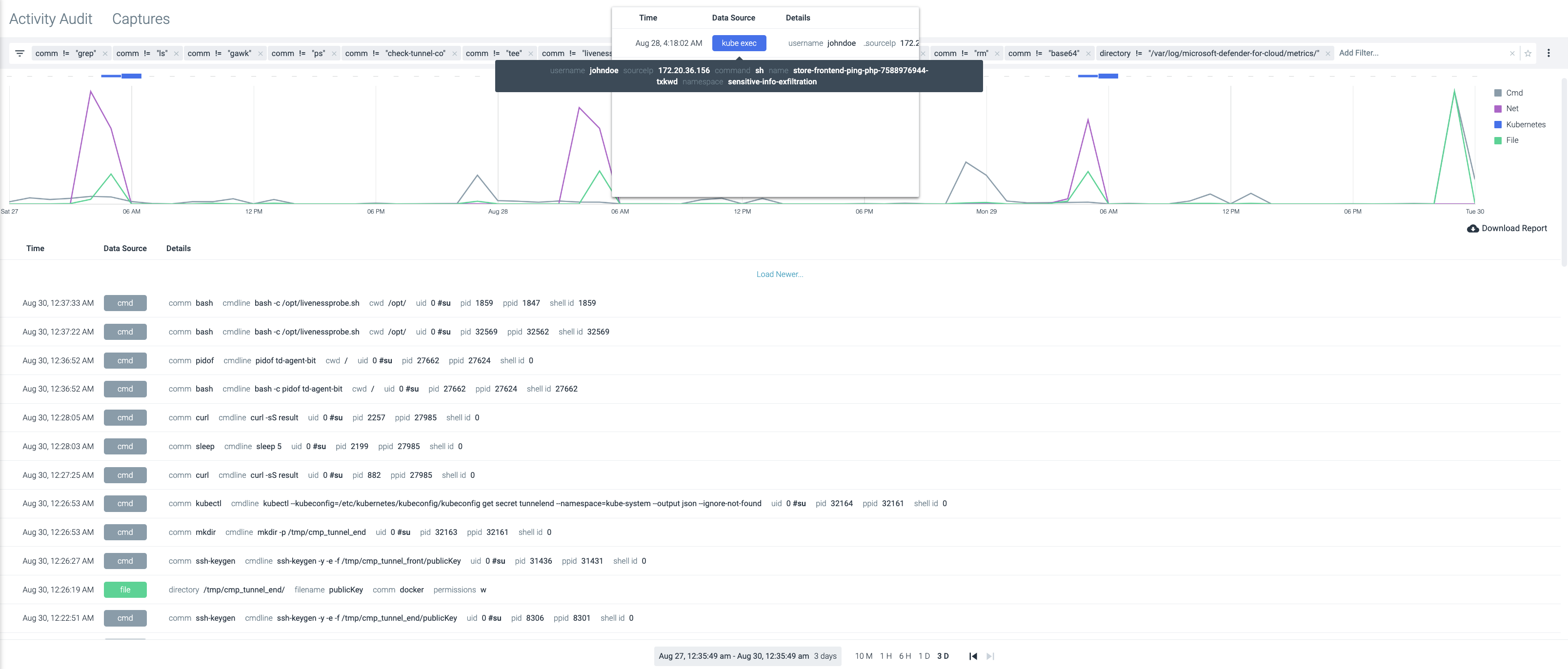
Detailed Activity Audit Trail
See the entire action sequence of malicious actors. Identify incident root causes by analyzing activities correlated with metrics across the stack (Kubernetes, containers, hosts, networks, and files).
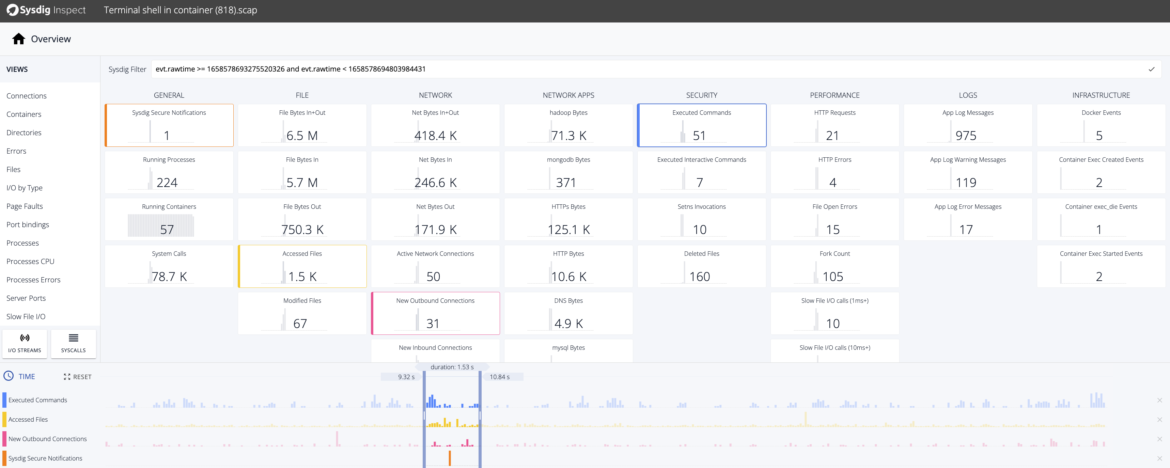
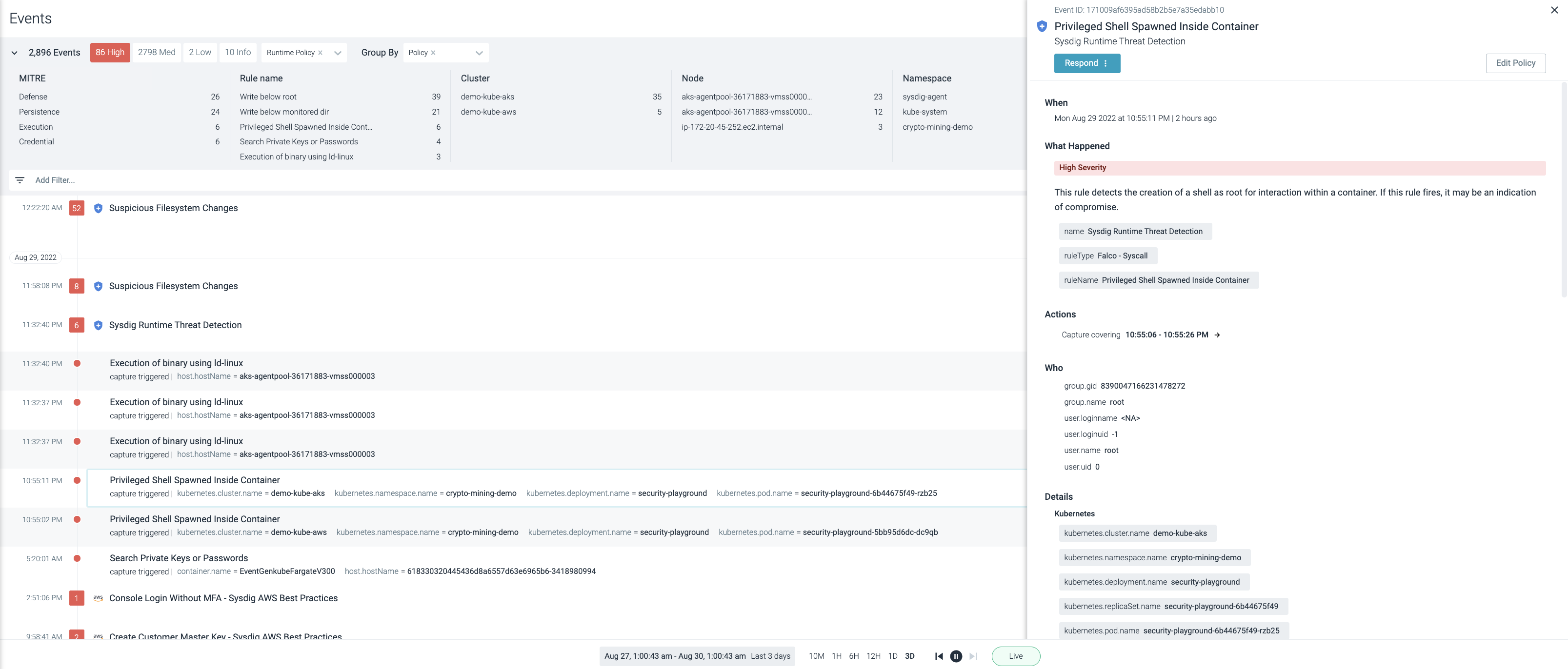
Security Event Timeline
Zoom into an incident from the event timeline and understand “why” and “what.” Apply out-of-the-box highly granular rules based on Falco to check for malicious behavior, identifying exactly what happened (e.g., cryptojacking or sensitive information leaks).
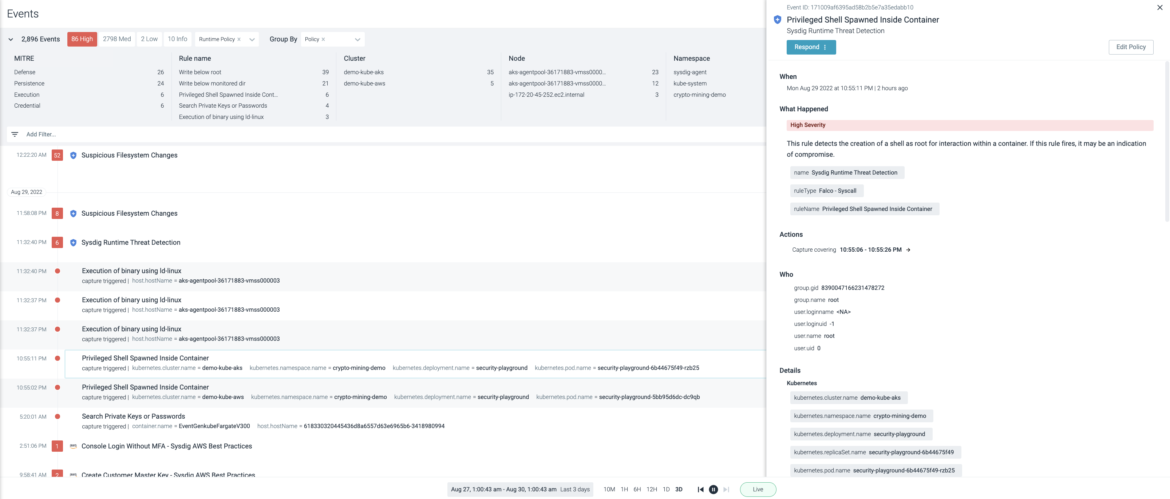
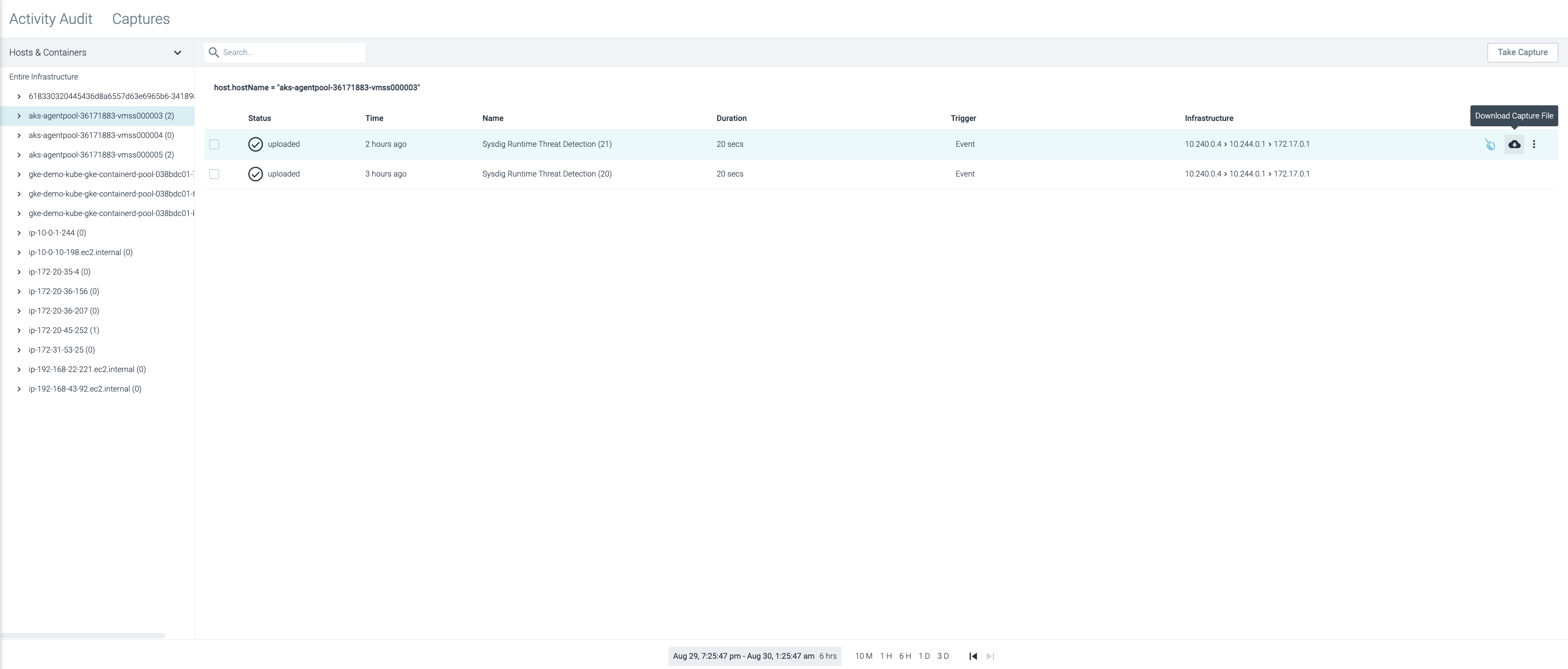
Forensic Capture Files
Maintain a record for a full forensics analysis. Identify incident root causes by analyzing activities correlated with security events, performance metrics, and logs across the stack (Kubernetes, containers, hosts, networks, and files). Recreate even the file contents in the event of a malicious incident.
Take the Next Step!
See how you can secure every second in the cloud.