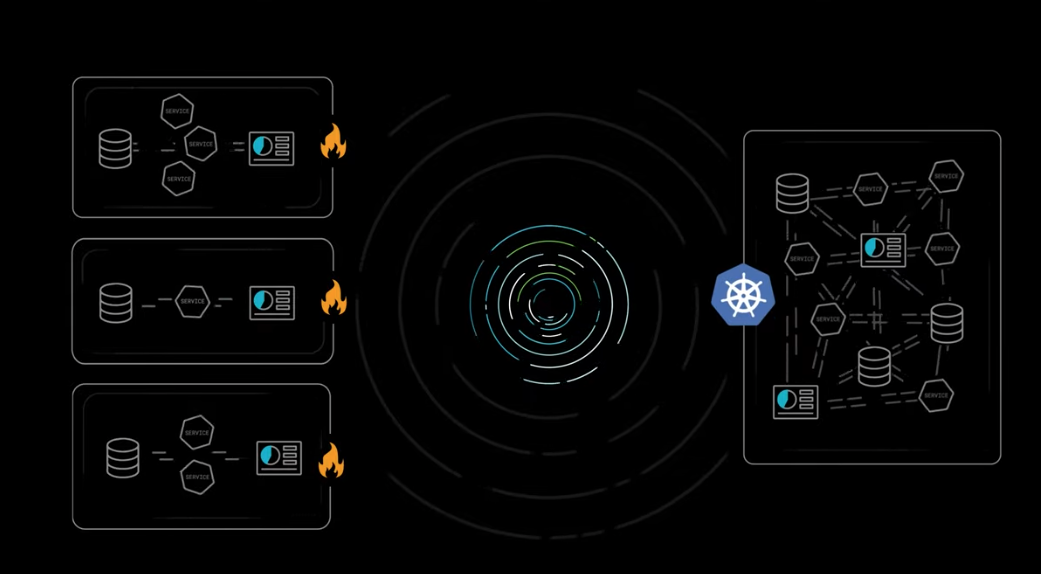
Prevent Lateral Movement in Kubernetes
Enforce microsegmentation and stop lateral movement threats with a cloud-native network security tool like Sysdig Secure.
Kubernetes Network Monitoring
See all network activity in and out of a particular pod, service, or application. Investigate suspicious traffic and connection attempts.
Kubernetes-Native Microsegmentation
Enable microsegmentation using Kubernetes cloud-native network policies with rich context. Apply Kubernetes network security without breaking the application.
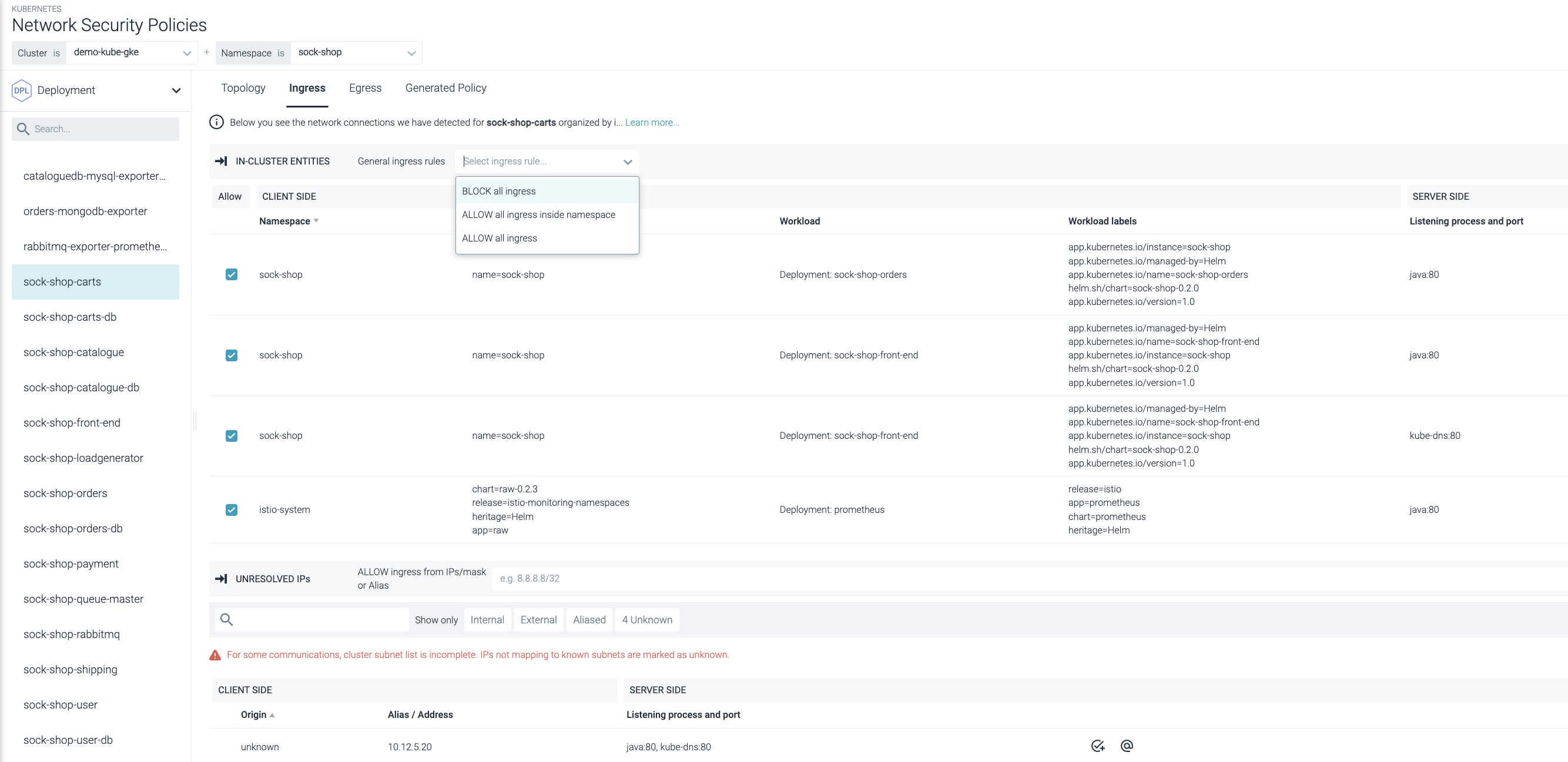
Automated Network Policies
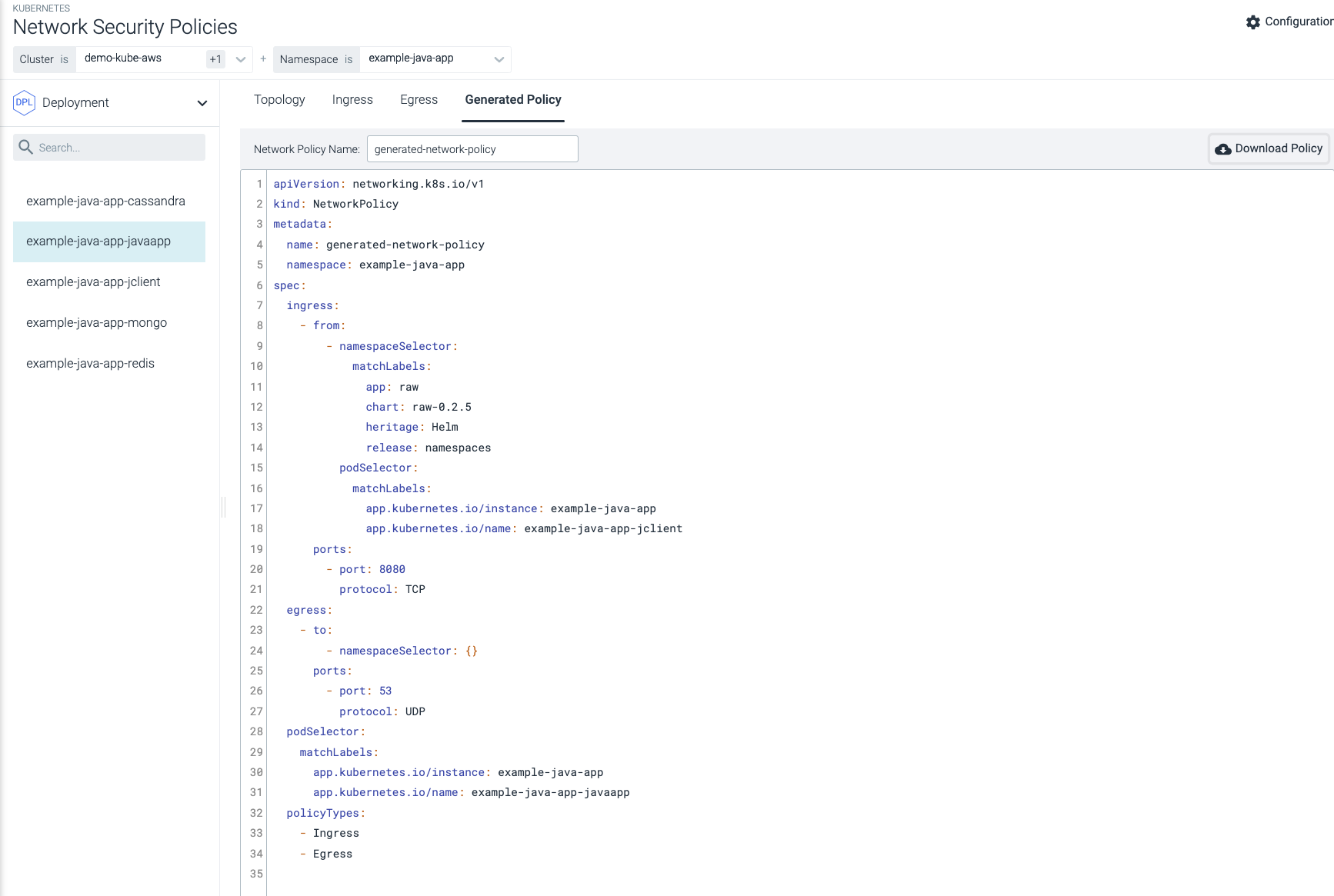
Save time by automating Kubernetes network policies. Use a simple graphical software interface to modify policies without manually changing the YAML.
"The Sysdig Secure DevOps platform not only provides the underpinnings of a cloud-native system, but also serves as the point where all container security begins.”
– Yoshihiko Ishikawa, Group 1, Department of Middleware 2, IT Engineering Division, SCSK2Kubernetes-Native Network Security
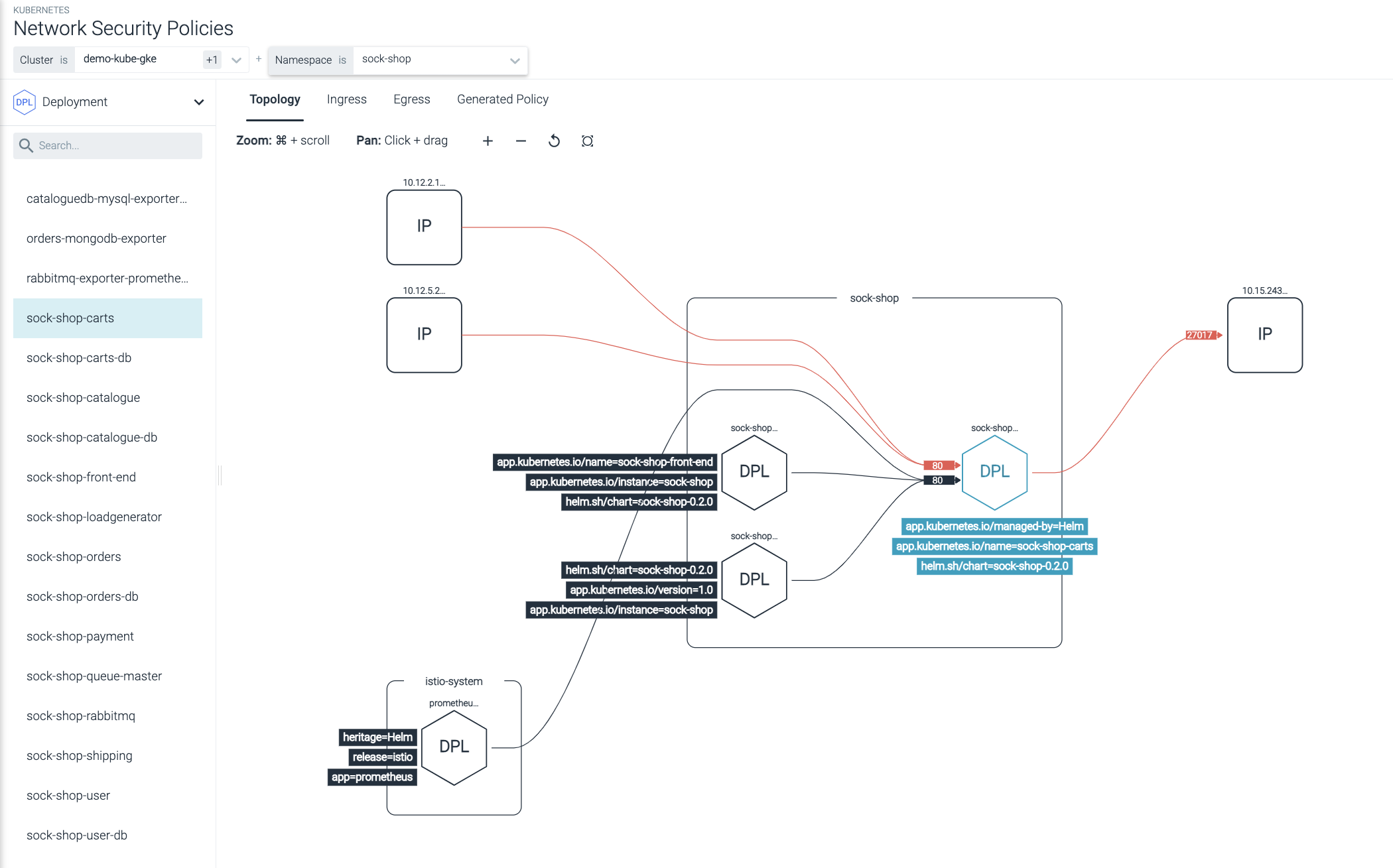
Kubernetes Topology Maps
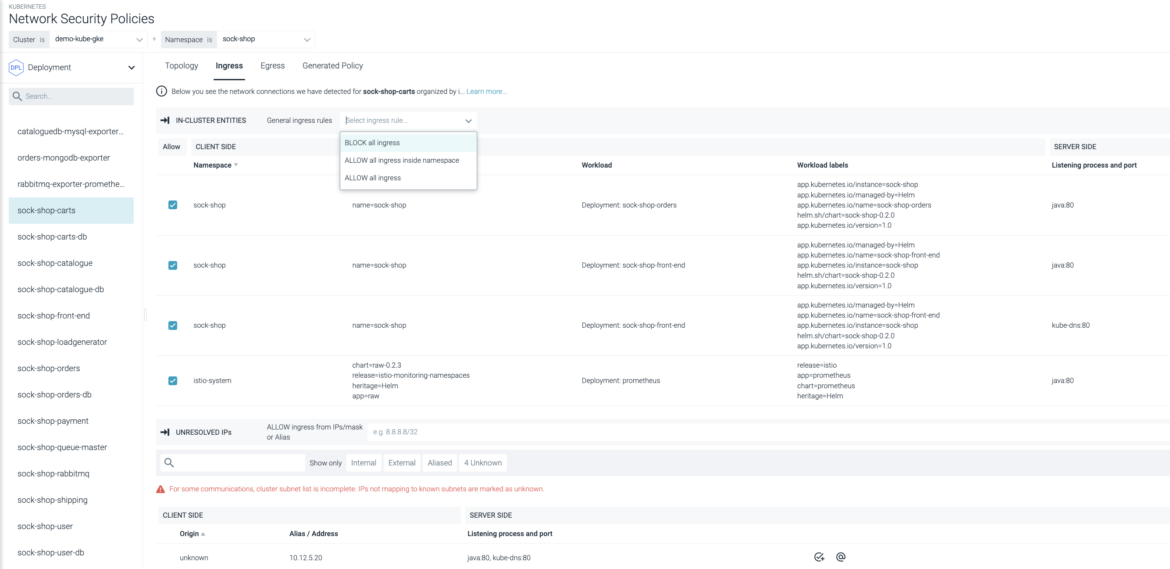
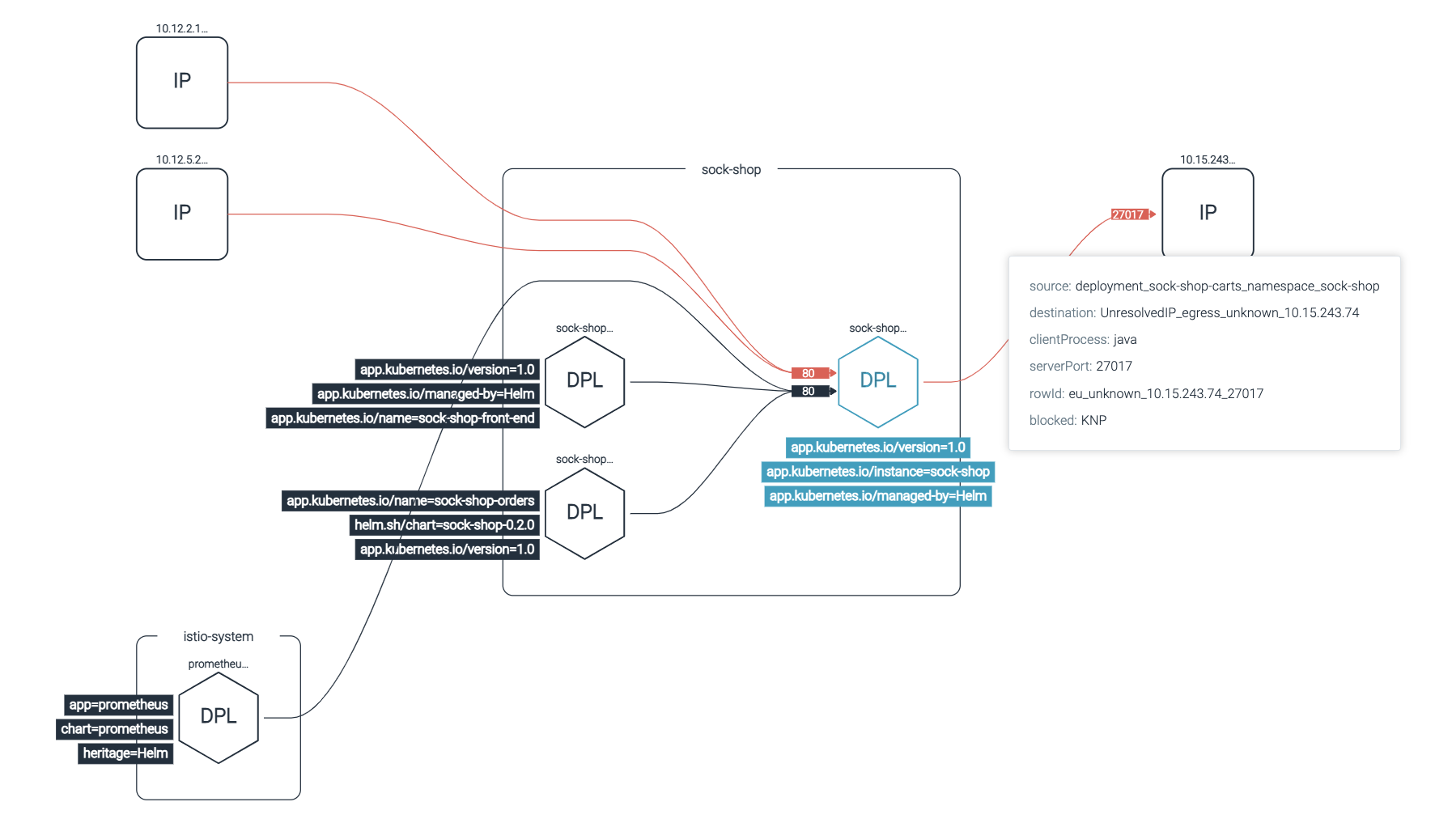
See all Kubernetes network communication between apps, pods, namespaces, and services with dynamic topology maps. Meet and validate compliance network requirements (NIST, PCI).
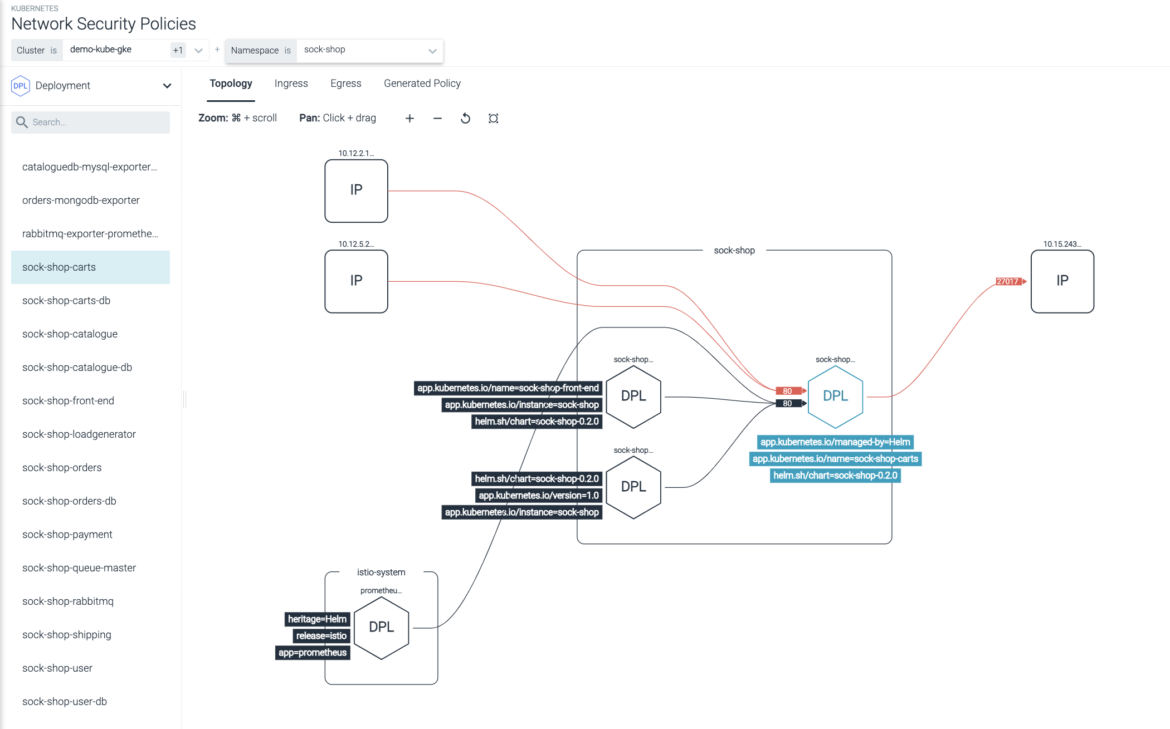
Kubernetes Microsegmentation
Implement least-privilege Kubernetes network security policies with rich application and Kubernetes metadata. Ensure that policies are not too permissive and don’t break the application.
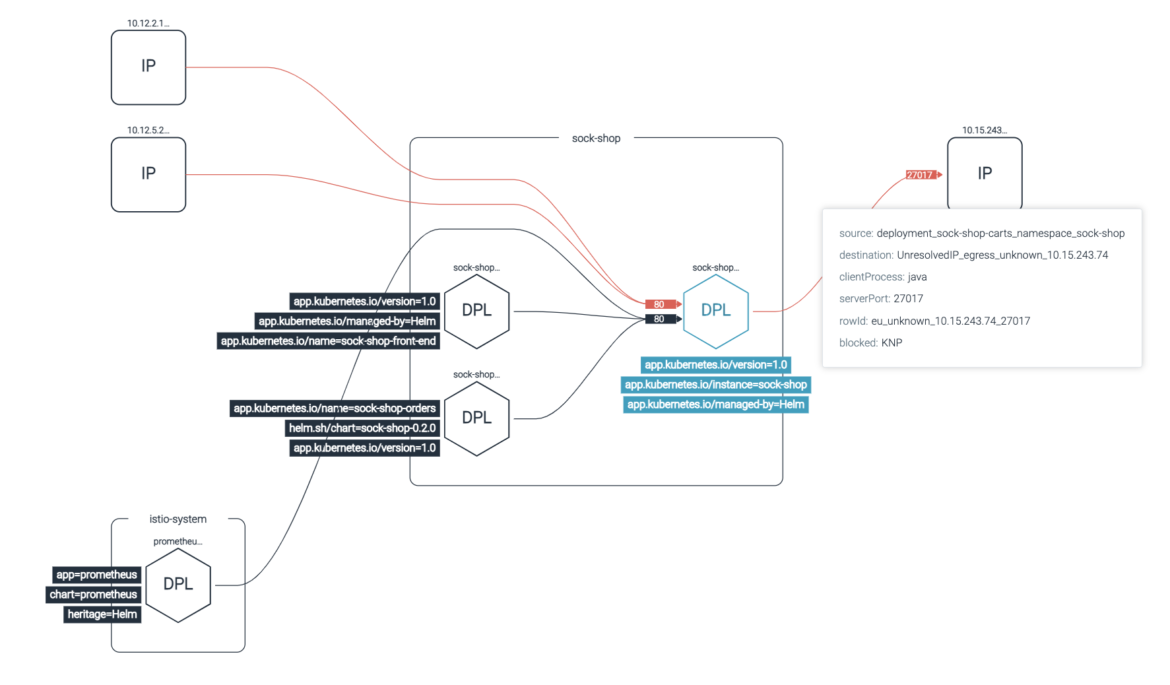
Network Behavior Anomaly Detection
Drill down into Kubernetes network traffic flow between a service, namespace, or pod over a particular time frame to easily verify anomalous container network behavior and investigate security events.
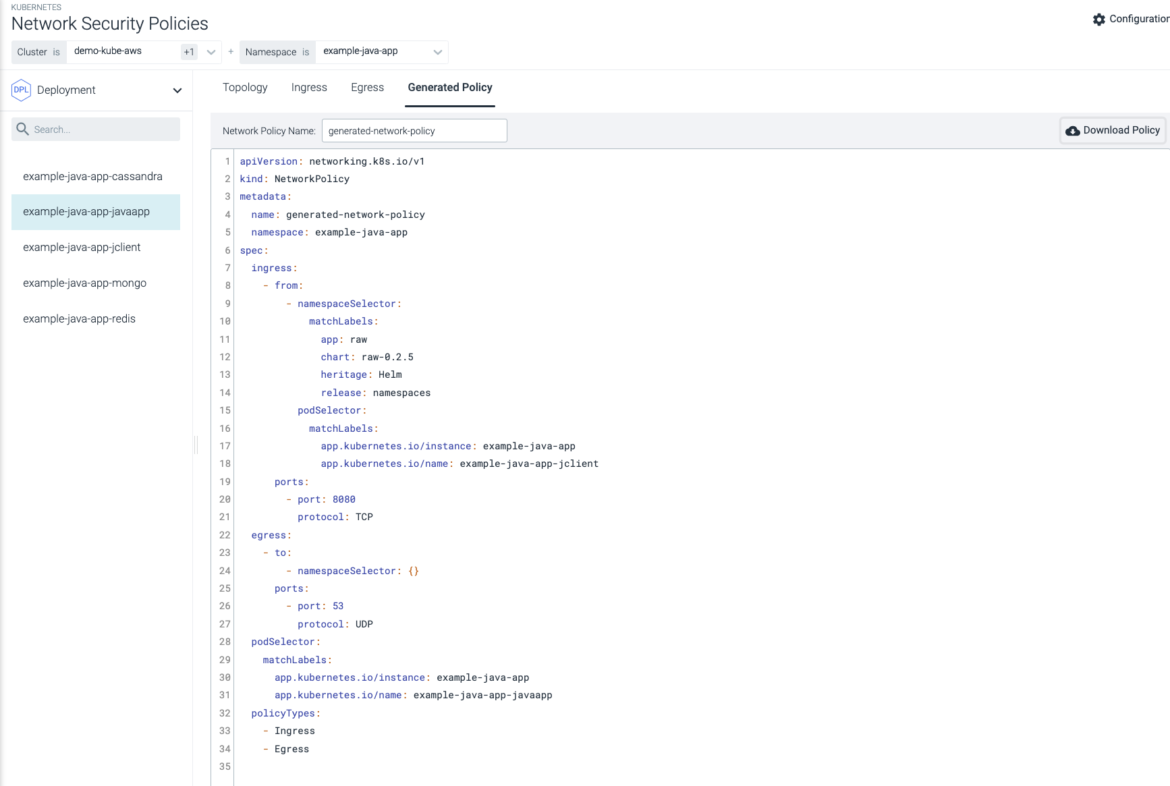
Automated Policy Generator
Use a friendly GUI editor to automate network policy creation without manually editing YAML files that often result in mistakes. Visually confirm the topology before applying in production.
Take the Next Step!
See how you can secure every second in the cloud.