Microsoft Azure is a great choice for enterprises looking to quickly build and deploy apps to the cloud. However, cloud teams must simultaneously consider how to implement DevSecOps practices to reduce, manage and avoid risks. Sysdig is collaborating with Microsoft to simplify cloud and container security and deliver robust SaaS-based solutions for the Azure ecosystem.
Sysdig and Microsoft Azure: Securing Cloud and Containers
Today, Sysdig announced the general availability of the Sysdig Secure cloud capabilities for Microsoft Azure. With it, we’ve introduced a number of new cloud security and compliance controls, including:
- Cloud Security Posture Management (CSPM): Based on CIS benchmarks tailored for your assets.
- Cloud Threat Detection: Identify threats in your Azure environment using Falco rules for Azure.
To quickly get started, checkout how to deploy Sysdig Secure for cloud on Azure. We will now explore Sysdig’s capabilities to tackle the challenges of security for containers, Kubernetes, and cloud services on Microsoft Azure below.
Threats to Microsoft Azure Infrastructure
Protection of your Azure infrastructure and workloads from misconfigurations and attacks cannot be a one-size-fits-all approach and you need a detailed and well-crafted strategy. There are a wide range of tactics and techniques employed today by threat actors. Beyond malicious activity, you can also face risk from the actions of well-meaning employees who simply don’t know to follow best practices.
Your best defense is to ensure you’ve doubled down your detection and security protocols in place from development to production. By working with Microsoft Azure, Sysdig is helping DevOps, cybersecurity, and risk teams follow cloud security best practices to meet their organizational goals.
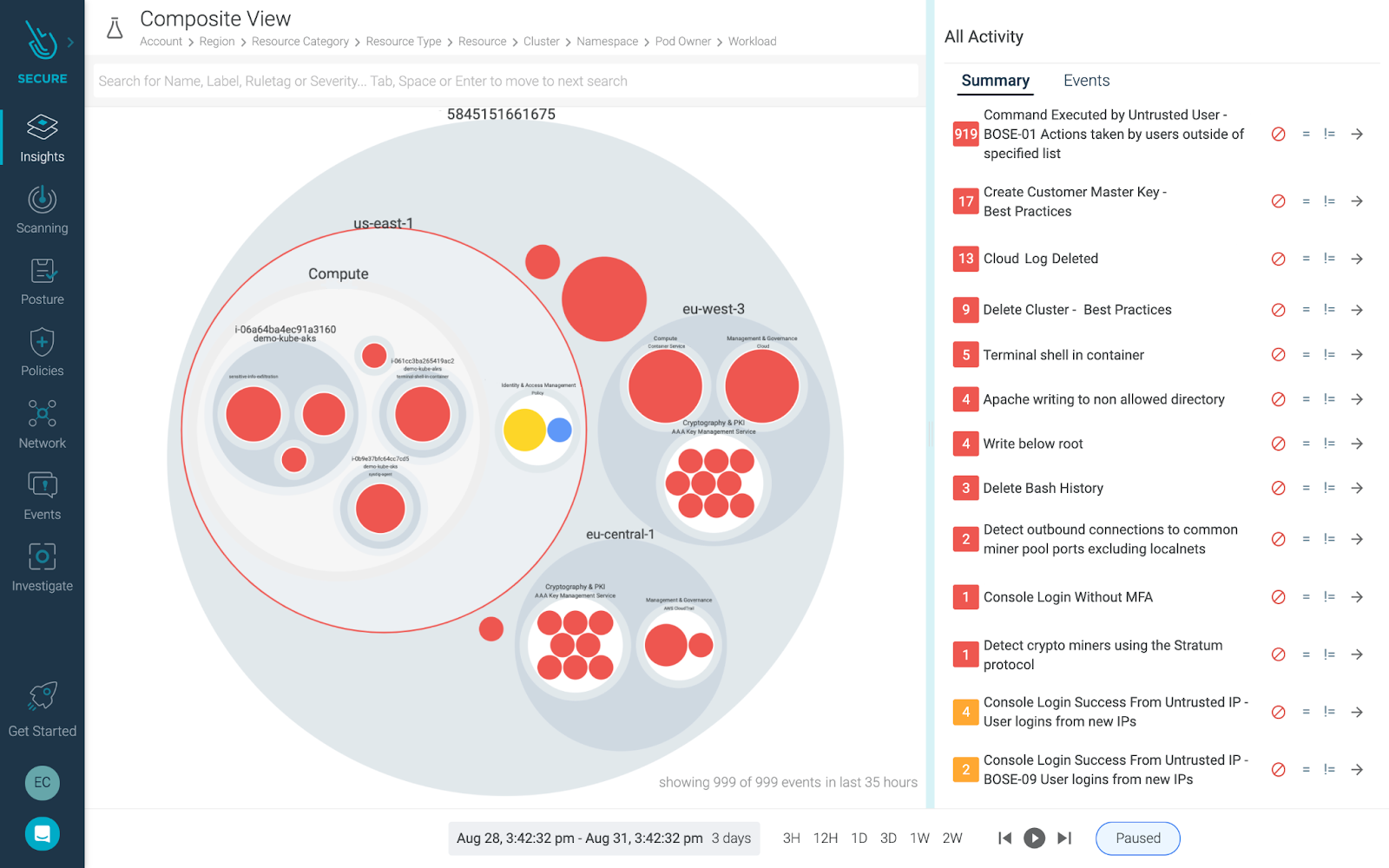
Unified posture management & threat detection for cloud & containers on Azure
Threat detection for Microsoft Azure requires visibility into all of your cloud services and containers. There is a lot to secure! App delivery requires a number of elements, including hosts, virtual machines, containers, clusters, stored information, and input/output data streams. How can you ensure you are properly securing it all?
The good news is that Microsoft Azure takes responsibility for the security and maintenance of its cloud services. This goes a long way to ensuring you can operate confidently in the cloud. However, the reality is that you, as a user, also must put the right protections in place.
By pairing the Sysdig cloud security capabilities announced today with our container security features, you’ll be able to more effectively follow security best practices for your Microsoft Azure accounts, apps, and services.
Cloud security posture management and compliance
To help you keep up with your use of Microsoft Azure services, Sysdig Secure allows you to perform static configuration analysis of your cloud infrastructure based on benchmarks like CIS. This helps you see where things are misconfigured. Plus, we provide guided remediation steps within the user interface to help you take action to achieve compliance.
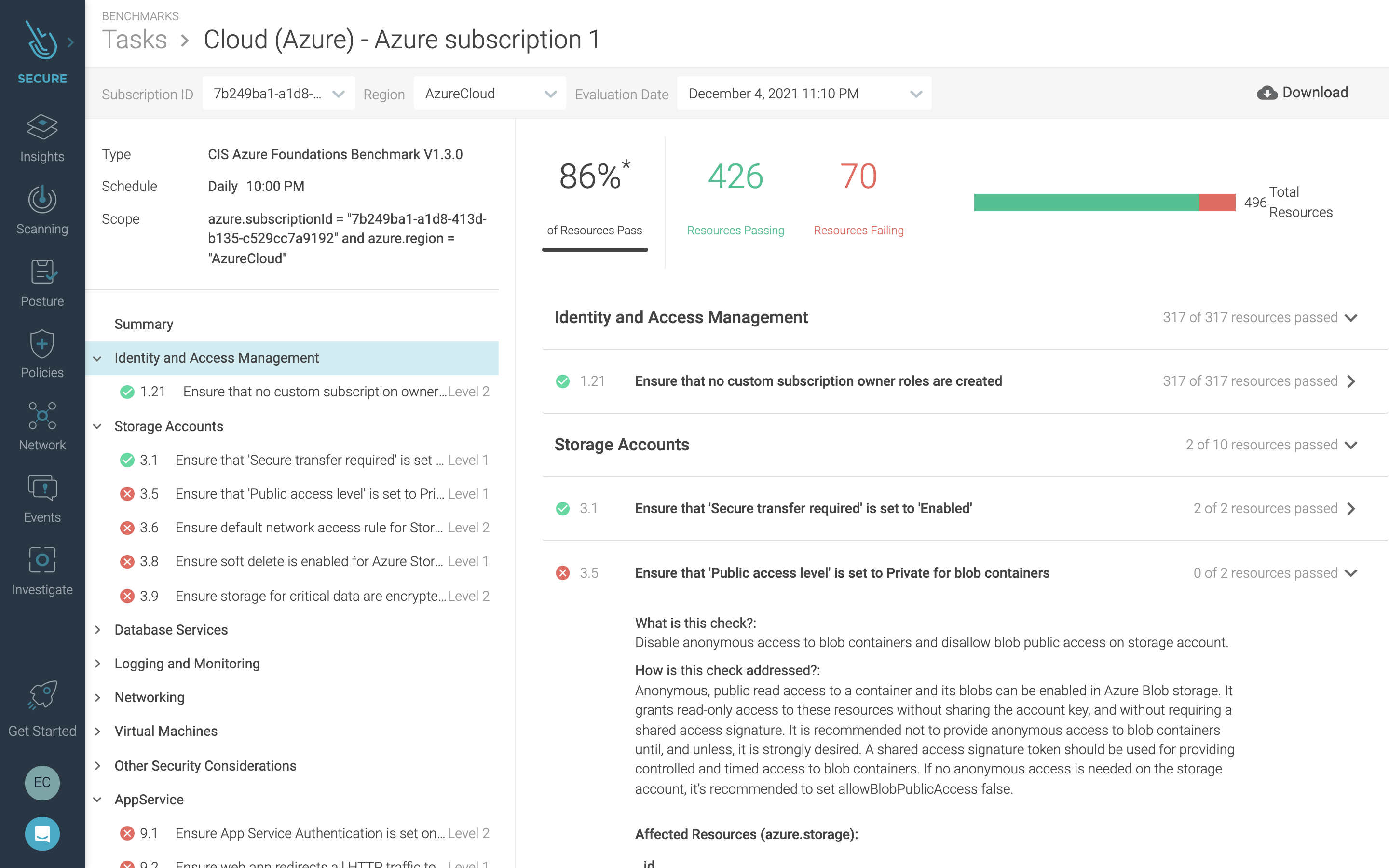
By checking the configuration of your environment, you will know if your IAM policies are secure, see what cloud storage buckets in your account are exposed to the public, and understand things like which VPCs allow ingress traffic, etc.
Cloud threat detection using Azure Activity Logs
As your use of Microsoft Azure services grows, the amount of activity can reach a point where manual analysis isn’t manageable. Failure to react to a threat in a short time can have major consequences.
Azure Activity Logs provide an always-on audit trail for Microsoft Azure that records both administrative events and user access to your cloud data. Sysdig performs threat detection for Microsoft Azure by analyzing this log data against a rich set of security rules based on open source Falco. This provides real-time analysis of activity so you can respond to threats faster.
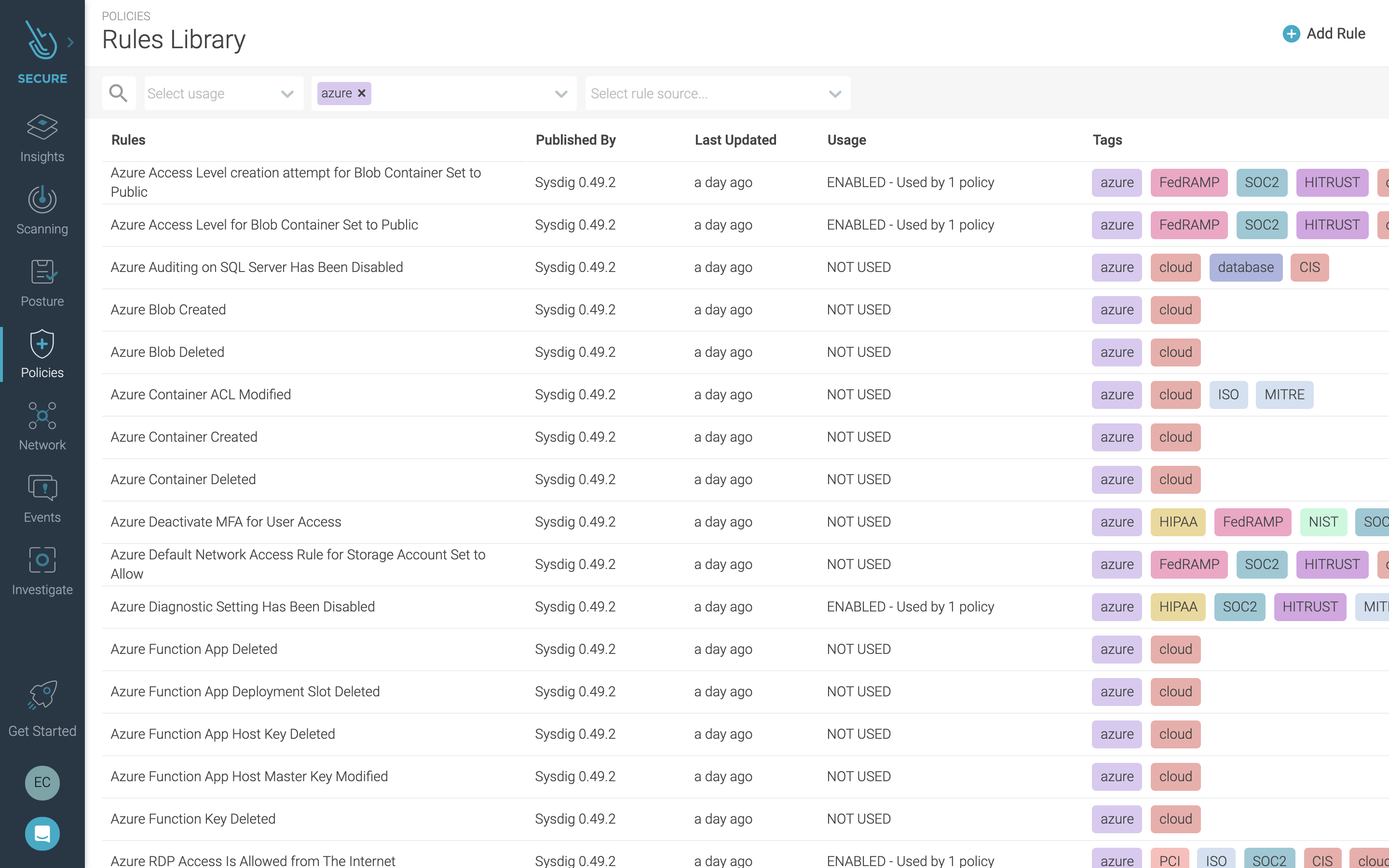
Sysdig provides out-of-the-box rules to help you secure your environment. This includes, for example, the following detections:
- Azure Auditing for SQL Server Enable/Disable
- Azure Function App creation, deletion and modification
- Azure SSH, RDP and User access Modification
- Azure Container Creation, Deletion and ACL Modification
- Azure Blob Creation and Deletion
Sysdig on Microsoft Azure Marketplace
Sysdig Secure DevOps Platform is available on Microsoft Azure Marketplace. This means you can purchase and get started right from Microsoft Azure.
Conclusion
We’re excited to partner with Microsoft Azure in helping our users more effectively secure their cloud services and containers. The new cloud security capabilities highlighted here build on our previous work to enable visibility, security, and compliance for Microsoft Azure. This includes image scanning, runtime security, compliance, and forensics for Azure Kubernetes Service, Azure Container Registry, Github Actions, and Azure Pipelines.
Having a single view across cloud, workloads, and containers will help you speed the time it takes to detect and respond to attacks. For a deeper look at best practices for Microsoft Azure security, check out the webinar Securing Microsoft Azure Cloud and Containers.



