With the constant threat of malware weighing on cloud teams, AWS is introducing new ways to identify malicious software with Amazon GuardDuty. Amazon GuardDuty Malware Protection, a fully managed malware detection service launched today at Re:inforce by AWS, provides agentless scanning to identify when suspicious activity occurs.
Along with the launch of the malware detection service, AWS has collaborated with partners like Sysdig to enable 3rd-party security solutions to take advantage of GuardDuty malware findings to help customers implement workflows to understand and contain the threat. In this blog, we’ll look at some of the details of the GuardDuty Malware Protection service and its use case as well as how you can tap into these findings using Sysdig Secure.
What is Amazon GuardDuty Malware Protection?
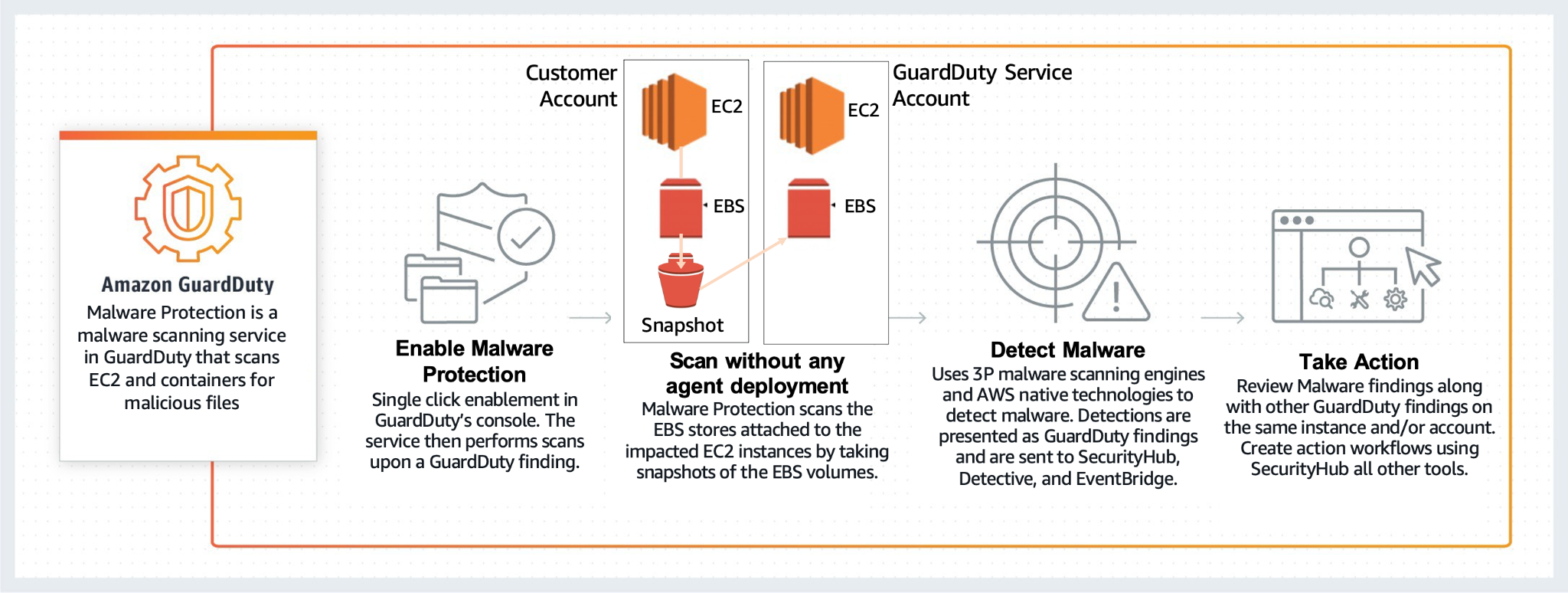
Amazon GuardDuty is a threat detection service that continuously monitors your AWS accounts and workloads for malicious activity. It delivers detailed security findings for organization-wide visibility into possible threats. Amazon GuardDuty Malware Protection adds the ability to scan EC2 workloads for malware.
With GuardDuty Malware Protection, AWS aims to provide malware detection across your environment with minimal operational overhead. When GuardDuty detects suspicious activity on an instance, GuardDuty Malware Protection triggers a scan of the EC2 instance to identify malware that may be causing the suspicious activity.
To scan without any agent deployment and without impacting the performance of your account and applications, GuardDuty Malware Protection scans the EBS stores attached to your impacted EC2 instances by taking snapshots of the Amazon Elastic Block Store (EBS) volumes.
In addition, the service is “container-aware.” This means it will scan containers running on EC2 that are Amazon Elastic Kubernetes Service (EKS), Amazon Elastic Container Service (ECS), or customer managed, attaching to EBS.
The diagram below depicts the malware service workflow.
Bringing GuardDuty Malware findings into Sysdig Secure
Malware analysis is a fundamental factor in the improvement of the incident detection and resolution systems of any company. Given the staggering cost of a data breach – estimated by IBM’s Cost of a Data Breach Report 2021 to be $4.24 million – applying more layers of security is always a good option.
One of the ways that GuardDuty malware findings are accessible to external providers is via Amazon EventBridge. EventBridge is a serverless event bus that delivers a stream of real-time data from event sources. Using the event stream conduit, Sysdig will pull the malware event details into Sysdig Secure to use as a security data source.
Knowing that malware is present is one step in the chain. Also understanding what the damage malware is doing in your environment is key. What makes having the malware findings interesting is that these events can be correlated with insights about other suspicious activity taking place on the same system(s) as detected by the our threat detection engine, based on open source Falco. Using this approach, not only can you understand the presence of malware, but also visualize its “blast radius” – meaning you’ll be able to see the activity and telemetry surrounding the malware event such as:
- Read/write activity such as accessing sensitive files or writing in disallowed locations
- Process activity such as traffic to an authorized server process and port
- Network activity such as unexpected inbound/outbound connections
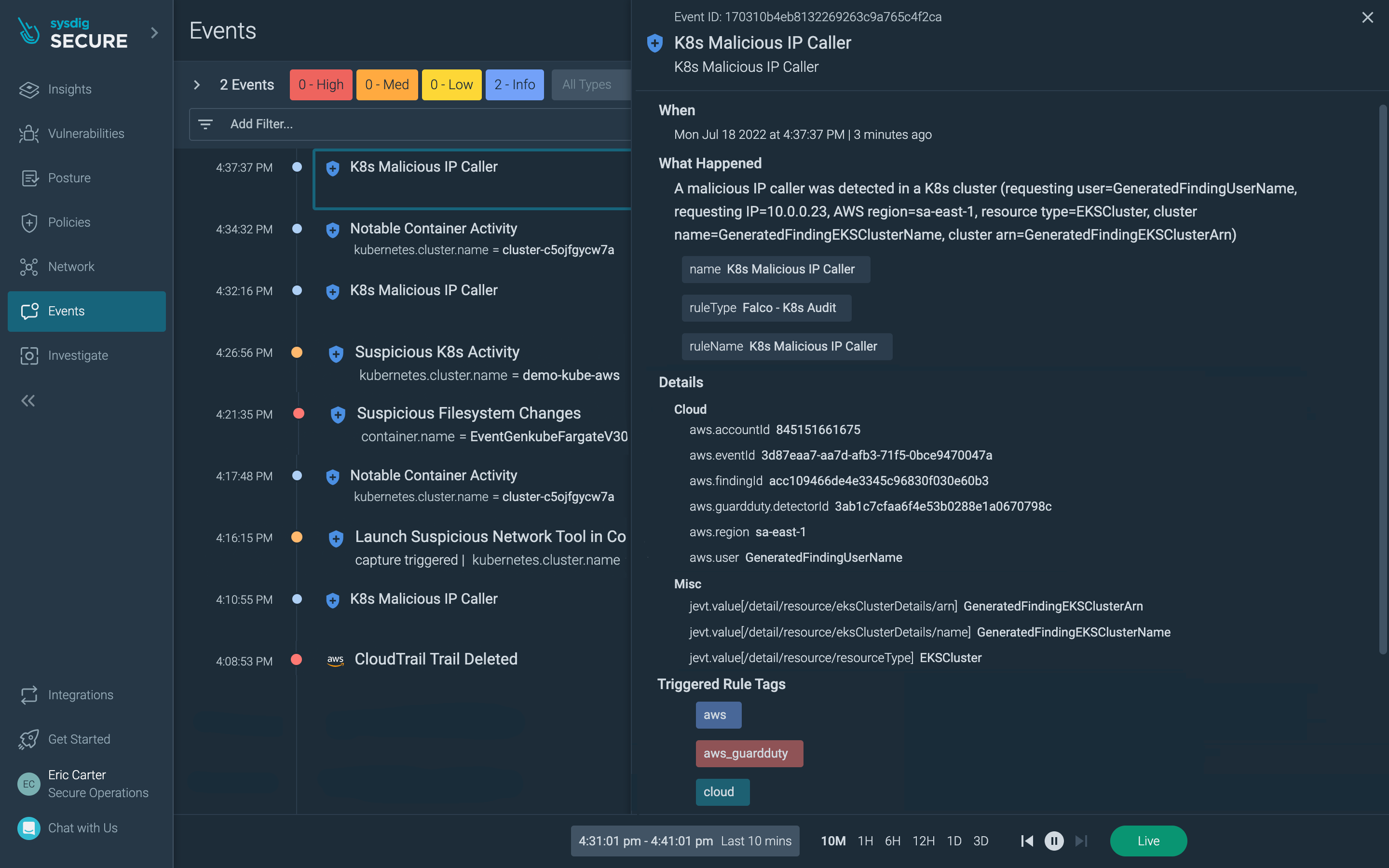
One of the advantages of using Falco as the threat detection engine in Sysdig Secure is that Falco is extensible with additional data sources. For instance, you can leverage Falco’s powerful and flexible rules language against data a number of activity sources such as system calls, CloudTrail logs, and Kubernetes APIs. to identify suspicious behaviors in order to generate alerts and capture information about events. While Sysdig Secure comes with a predefined set of rules to make it easy to get started, you can also customize Falco rules to best fit your needs.
In addition to Sysdig’s work to add additional data sources to Sysdig Secure, the Falco project earlier this year announced a new plugins framework to enable the community to do the same. The new capability provides set of shared libraries that the community can use to extend Falco functionality to new data sources and create new input events.
Extending GuardDuty findings with remediation and forensics
One of our goals with the new AWS project is to create a connection between the malware findings and the remediation and forensics capabilities available with Sysdig Secure. Sysdig is able to supplement the agentless GuardDuty model with a runtime agent that provides greater context and response actions. This enables enterprises to automate action to control the impact of malware and set themselves up with the right info to be able to investigate thoroughly what happened.
Consider this container use case for instance. When GuardDuty detects the presence of malware in a container, for the host running the infected container. by policy, Sysdig Secure can kill or stop the container to eliminate the immediate threat. This workflow is enabled by a Sysdig agent running co-resident on the EC2 instance hosting the container. In addition, the policy can trigger the creation of a capture file containing all of the system call activity on the EC2 instance before during and after the malware event triggered.
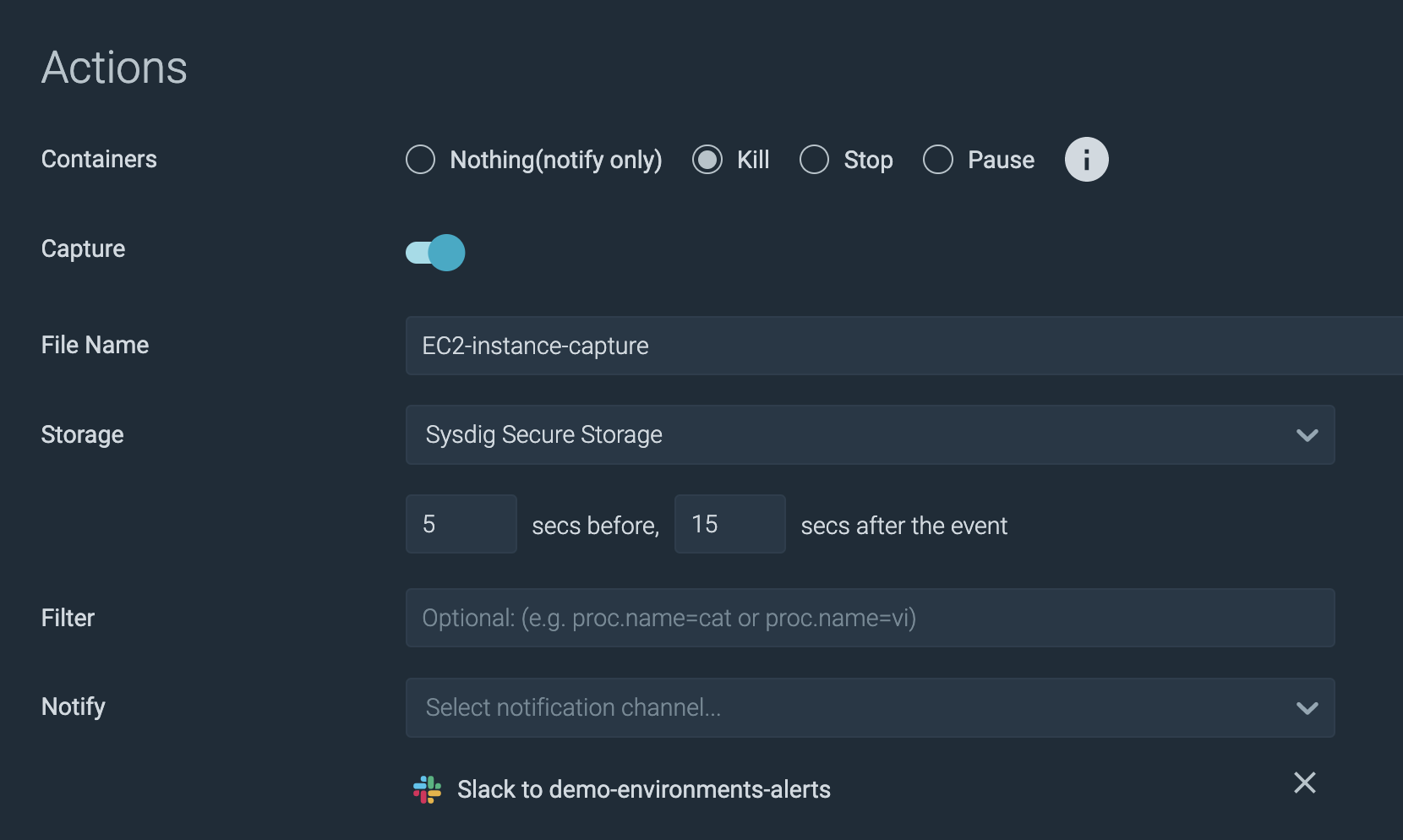
Malware attacks usually include running adversary code on the victim’s machines. Following the initial access, actors try to run scripts with embedded executables to continue an attack. Being able to identify which code doesn’t belong is fundamental to thwart attacks before they can cause damage. To this end, using Sysdig Secure’s newly announced drift control could also be enabled to detect and block new or modified code from execution.
Conclusion
Cloud teams need comprehensive security protection to safeguard their workloads and infrastructure. Without deep insight into activity across your cloud environment and help from a smart detection engine, it will be hard to detect – and recover – from attacks.
Malware is continuously mutating and targeting new services and platforms. We’re happy to support AWS as they launch the new GuardDuty Malware Protection service. Combining the strengths of AWS and Sysdig gives teams a more effective arsenal to fight the threat of malware.
Want to learn more? Here are a few resources to check out:
- Read AWS Cloud Security Best Practices on the Learn Cloud Native Hub
- Download the Anatomy of Cloud Attacks guide
- Get started with a free trial!


