The Rapidly Evolving Cloud Attack
Attackers are increasing their focus on the growing cloud playing field as it becomes more lucrative. They are refining their craft to further accelerate attacks with methods like artificial intelligence and automation. Slow response times, limited coverage, and visibility gaps, often exacerbated by inadequate and fragmented tooling, allow attackers to make quick work of vulnerable environments. In fact, the Sysdig 2023 Global Cloud Threat Report shows targeted cloud attacks only need an average of 10 minutes post credential discovery (five minutes of which are dwell time) to accomplish their goals, whether they be financial, espionage, or ideological.
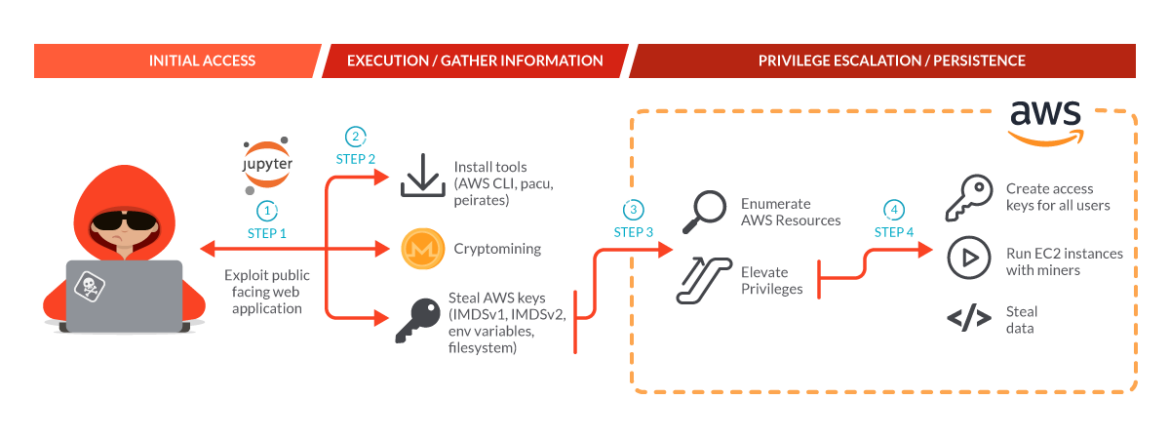
Compounding speed, attacks are also increasing in sophistication, as shown by the Sysdig Threat Research Team. SCARLETEEL 2.0 is an advanced threat actor operation, leveraging complex, multi-step attacks. After gaining initial access through exploitation of a public facing web application, attackers installed tools and cryptominers, potentially in an attempt to obfuscate their larger plans. Concurrently, the threat actors stole AWS keys to further exploit the victim’s AWS environment and establish a mechanism of persistence. The threat actors then enumerated AWS resources and elevated privileges to create access keys for all users, run EC2 instances with miners, and finally exfiltrate intellectual property. The speed and complexity of these actions highlight the urgency needed for teams to effectively detect, understand, and respond.
A Path Forward
To combat sophisticated attacks, analysts need a solution to augment their capabilities, streamline proactive mitigations, and accelerate detection and response workflows. These solutions need a high degree of automation to deliver forensic narratives derived from cross domain correlated detections. The ephemeral nature of cloud environments and speed of attackers render hourly or daily inspections insufficient. High confidence Runtime Insights give the analysts a fighting chance.
Sysdig Evolves Faster
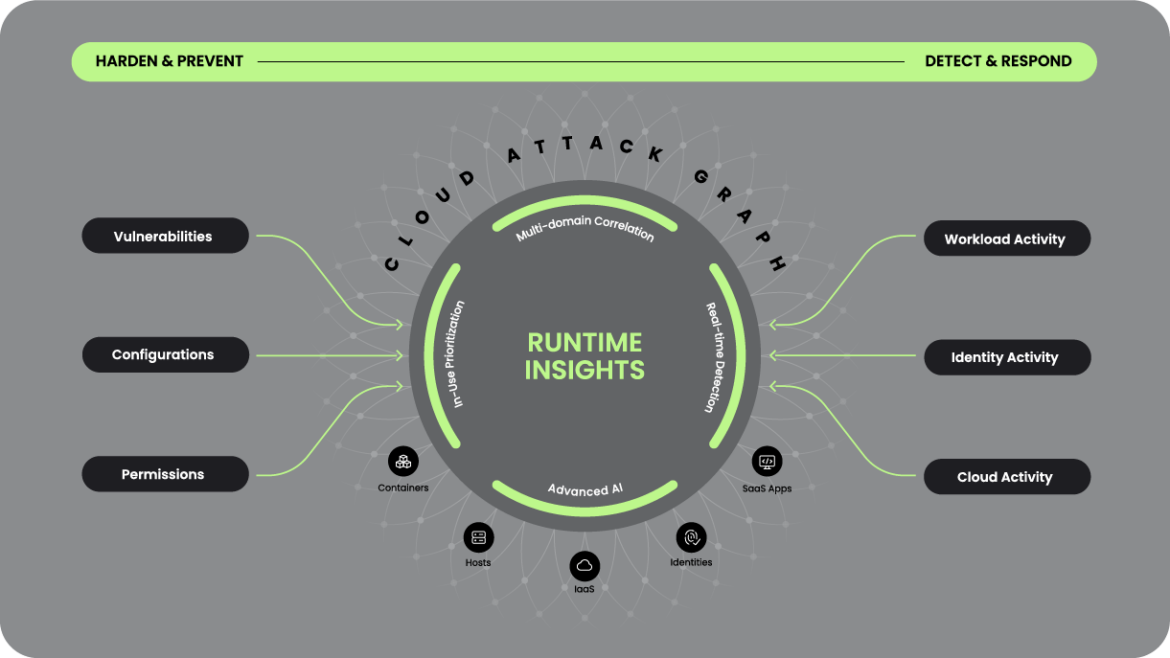
The new Sysdig Cloud Attack Graph is a significant leap forward in Cloud Native Application Protection Platforms (CNAPP). It integrates state-of-the-art machine learning (ML) algorithms and real-time analytics to accelerate and enhance security against the most sophisticated attacks. The Cloud Attack Graph functions as the neural center of the Sysdig platform. It leverages high-throughput, low-latency data processing pipelines to correlate cross-domain data points swiftly – spanning resources, user activity, suspicious behavior, network traffic, misconfigurations, and application vulnerabilities.
The Cloud Attack Graph is purpose built on a distributed architecture optimized for cloud-native environments which can easily accommodate rapidly expanding data volumes. The Cloud Attack Graph’s core functionality is driven by runtime insights, gathered through a combination of advanced monitoring techniques such as behavioral analytics, ML detections, and heuristic evaluations. These insights are synthesized with real-time threat intelligence feeds which scrutinize in-use vulnerabilities and excessive sensitive IAM (Identity and Access Management) permissions.
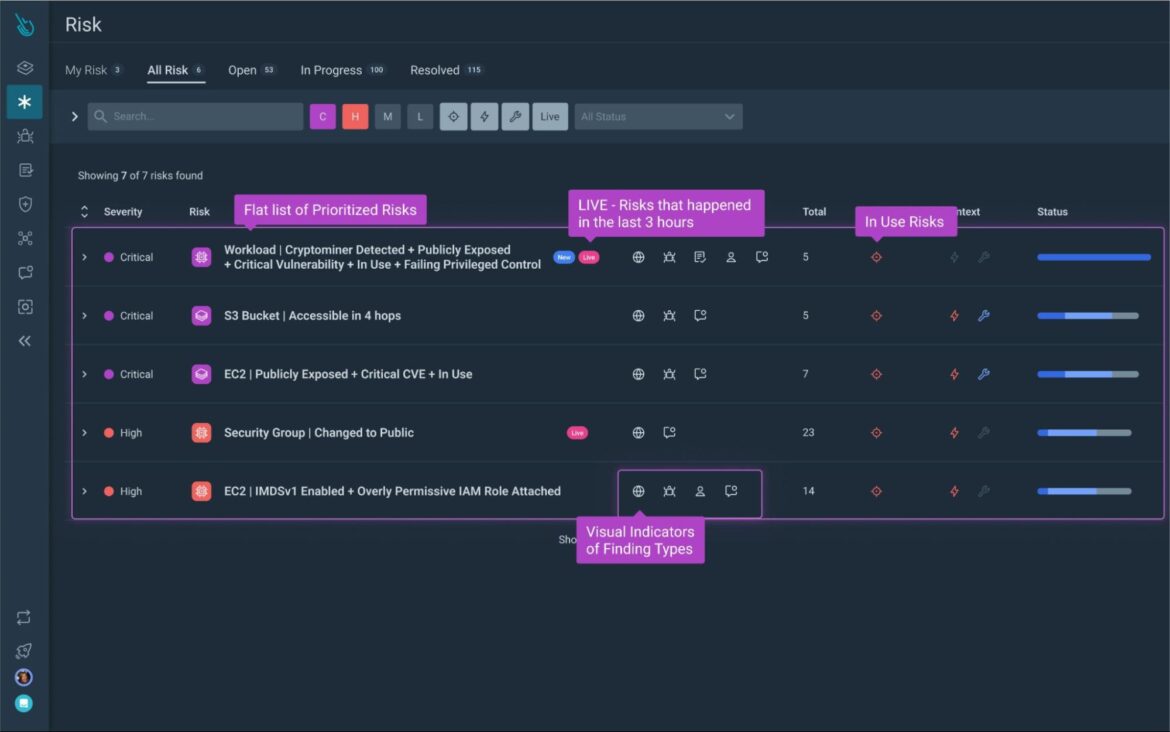
Weighted risk assessment algorithms empower the Cloud Attack Graph to prioritize the most critical risks and automate remediation workflows to stop sophisticated attacks in real time. The Risk Prioritization dashboard enables teams to proactively mitigate future cloud attacks. Risk prioritization combines context from runtime insights, such as in-use vulnerabilities and in-use permissions, with static checks, such as misconfigurations and known vulnerabilities.
The Sysdig Cloud Attack Graph also enables teams to visualize and prioritize exploitable links across resources to uncover hidden attack paths proactively. The situational awareness spotlights difficult behaviors like lateral movement, helping organizations to stop sophisticated attacks, such as SCARLETEEL 2.0, earlier in the kill chain.
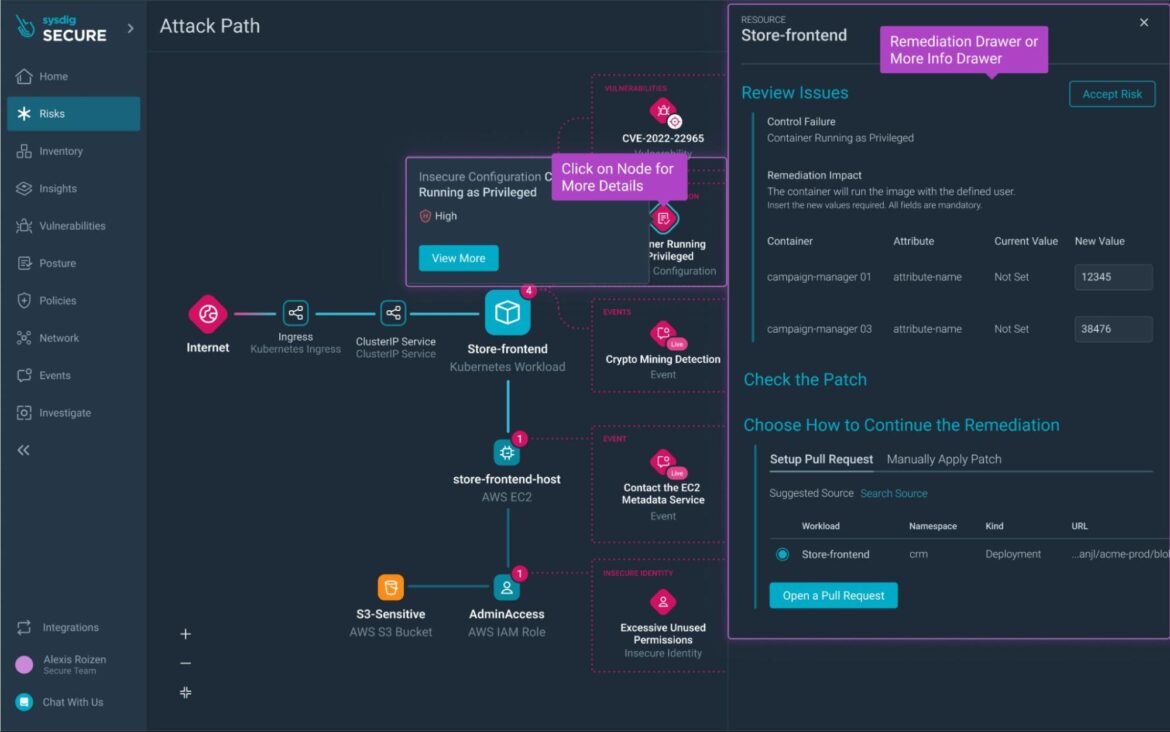
Further reducing the analyst workload, the Sysdig Cloud Attack Graph identifies excessive permissions and recommends Least Permissive Policies which include only utilized permissions.
Take Back Control with Sysdig
As attackers and cloud threats continue to evolve and increase in speed, time becomes a bigger challenge for security teams. With Sysdig, organizations gain the compounding benefits of the Sysdig Cloud Attack Graph, augmenting analysts’ capabilities to do more, faster. The Cloud Attack Graph’s real-time insights expedite accurate detection of complex attacks and accelerate incident response.
To see how the Sysdig Cloud Attack Graph can enhance and accelerate you security team, sign up for a demo today.


