A recent privilege escalation heap overflow vulnerability (CVSS 7.8), CVE-2021-3156, has been found in sudo.
sudo is a powerful utility built in almost all Unix-like based OSes. This includes Linux distributions, like Ubuntu 20 (Sudo 1.8.31), Debian 10 (Sudo 1.8.27), and Fedora 33 (Sudo 1.9.2).
This popular tool allows users to run commands with other user privileges. For example, you use a computer as an unprivileged user 95% of the time, then you “can” use sudo and gain root privileges for just the time it takes to install a given program, then go back to be a regular user.
The vulnerability affects all the following sudo versions:
- All legacy versions from 1.8.2 to 1.8.31p2
- All stable versions from 1.9.0 to 1.9.5p1
A successful exploitation allows any unprivileged user to escalate its privileges to root on the vulnerable host. Since it’s a privilege escalation vulnerability, it requires access to a local user on the vulnerable host in order to actually exploit it.
In this article, you’ll learn how this vulnerability can be exploited, and how to use Falco to detect any exploit attempts.
The CVE-2021-3156 issue
The fun fact is that the vulnerability has been available in clear for almost 10 years.
The researcher Baron Samedit discovered that:
- Executing sudo in “shell” mode (
shell -c command) - Using the
sudoeditcommand with the options-s(MODE_SHELLflag) or-i(MODE_SHELLandMODE_LOGIN_SHELLflags) - It’s possible to escape special characters in the command’s arguments using a backslash at the end.
A bug in the sudo code, related to the sudoedit command, permits to avoid the escape characters and overflow the heap-based buffer through a command-line argument that ends with a single backslash character.
From an attacker perspective, this buffer overflow vulnerability allows the attacker to control the size of the buffer, and control the contents (using null bytes if necessary) of the overflow itself. This is what enables the malicious user to execute custom code on the host with root privileges.
The impact of CVE-2021-3156
Due to the recent discovery and publication, there isn’t a public working exploit already available.
Being such an old bug, and being present in recent OS versions, there are plenty of vulnerable machines out there. Any device with a Linux or Unix OS on board may be affected, this goes beyond servers and desktops.
You can know if you are affected by checking if the sudo version is between 1.8.2 and 1.8.31p2, or between 1.9.0 and 1.9.5p1.
It is also possible to test if the machine is available using the following command:
sudoedit -s /
Based on the response, It’s possible to understand if the host is vulnerable or not:
- Vulnerable if responds an error starting with
sudoedit: - Not Vulnerable or patched if responds an error starting with
usage:
Detection CVE-2021-3156 using Falco
Detecting exploitation attempts of this vulnerability is fundamental.
If you cannot patch your systems immediately, you can detect and potentially prevent the attack. Even though you might have already upgraded your system and containers affected by the vulnerability, it is still extremely interesting to detect any exploitation attempts and catch malicious activities in your environment.
Falco is the CNCF open-source project for runtime threat detection for containers and Kubernetes.
One of the benefits of Falco is in leveraging its powerful and flexible rules language. As a result, Falco will generate security events when it finds abnormal behaviors as defined by a customizable set of rules. Meanwhile, Falco comes with a handful of out-of-the-box detection rules.
We can quickly and easily write new Falco rules to filter anomalous behavior. For example, the following rule will detect someone trying to exploit sudo‘s CVE-2021-3156:
- rule: Sudo Potential Privilege Escalation (CVE-2021-3156) desc: Privilege escalation vulnerability affected sudo. Executing sudo using sudoedit -s or sudoedit -t command from an unprivileged user it's possible to elevate the user privileges to root. condition: spawned_process and user.uid!= 0 and proc.name=sudoedit and (proc.args contains -s or proc.args contains -i) and (proc.args contains "\ " or proc.args endswith \) output: "Detect Sudo Privilege Escalation Exploit (CVE-2021-3156) (user=%user.name %container.info parent=%proc.pname cmdline=%proc.cmdline)" priority: CRITICAL tags: [filesystem, mitre_privilege_escalation]
When the rule detects the exploit attempt, Falco will trigger a notification:
20:34:21.211306349: Critical Detect Sudo Privilege Escalation Exploit (CVE-2021-3156) (user=ec3-user host (id=host) parent=bash cmdline=sudoedit -s 12345678901234\)
Sysdig Secure extends the open-source Falco detection engine to provide comprehensive security across the Kubernetes workloads lifecycle.
The very same rule can be used within Sysdig:
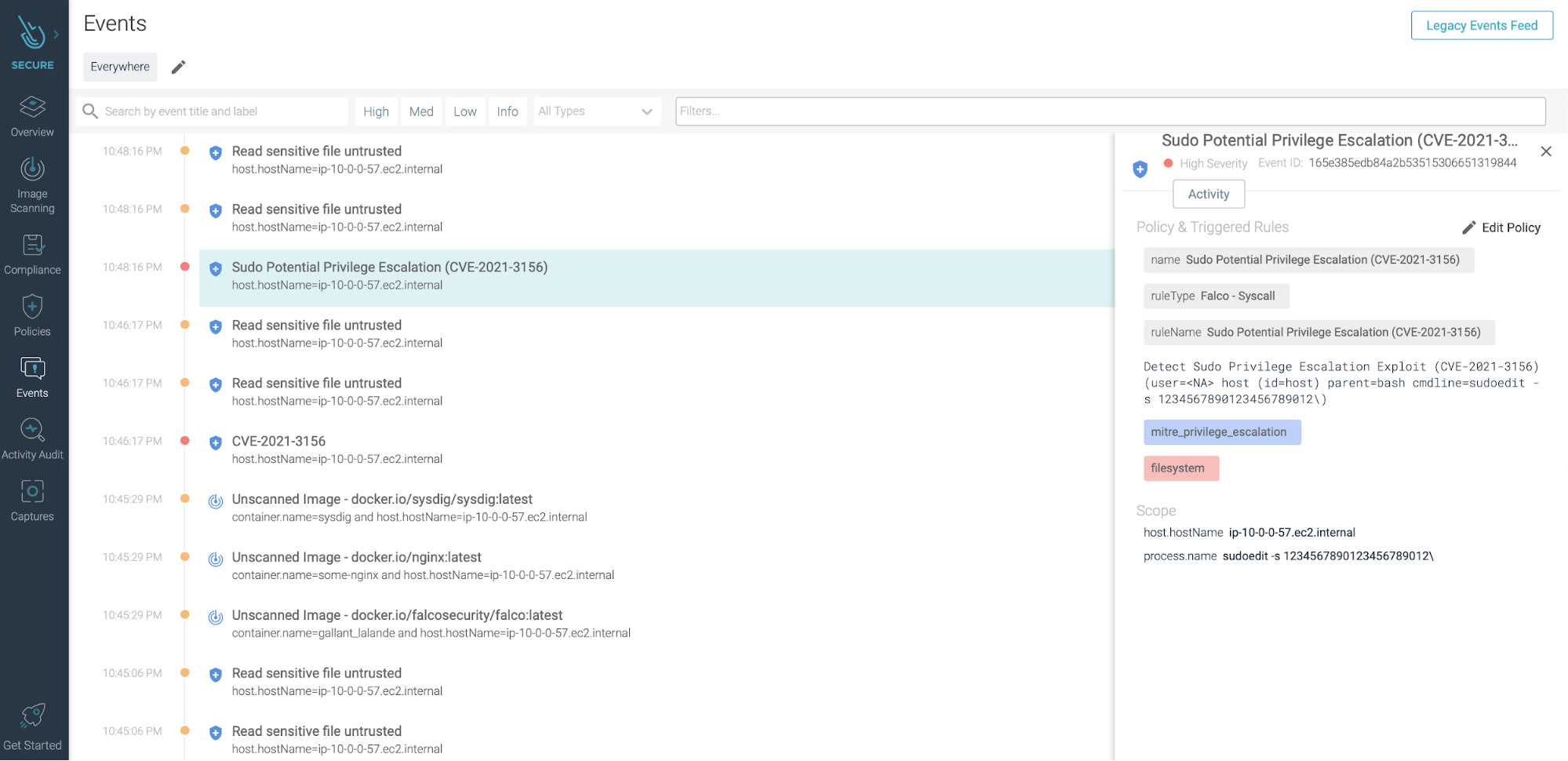
In addition, Sysdig Secure will allow you to:
- Block threats by extending Falco’s detection capabilities with response.
- Ease the burden of creating and updating runtime Falco policies with automated profiling, a flexible policy editor and centralized management.
- Embed security across the DevOps process with image scanning, forensics/incident response and audit, in addition to security monitoring.
- Validate compliance using out-of-the-box checks and runtime policies that map to compliance standards.
So using Sysdig Secure, you can easily detect sudo packages affected by the vulnerability CVE-2021-3156, block any new container affected in your CI/CD pipeline or registry before a new deployment and react to exploitation attempts of this vulnerability across already running containers in production blocking the malicious containers in your Kubernetes cluster.
Conclusions
The CVE-2021-3156 vulnerability allows malicious users, that already have local access to a host, to escalate its privileges and to run any command as root using a bug code available in sudo.
Falco allows users to filter and detect this kind of activity. By writing a custom rule to match the exploit behaviour pattern, and then alert regarding the malicious activity across our hosts and containers.
Sysdig Secure takes this functionality a step further, being able to react to these attacks, block them, and report on any affected running containers with the sudo vulnerability.


